At Clouddle, we know that a robust network security toolkit is essential for protecting digital assets in today’s threat landscape. Cybercriminals are constantly evolving their tactics, making it crucial for organizations to stay one step ahead.
This blog post will explore the must-have tools for network monitoring, intrusion detection, and access control. We’ll provide practical insights on how to leverage these tools effectively to strengthen your network defenses.
Essential Network Monitoring Tools for Robust Security
Network monitoring forms the foundation of effective cybersecurity. The right tools can significantly enhance an organization’s security posture. Let’s explore three indispensable tools that every network administrator should have in their arsenal.
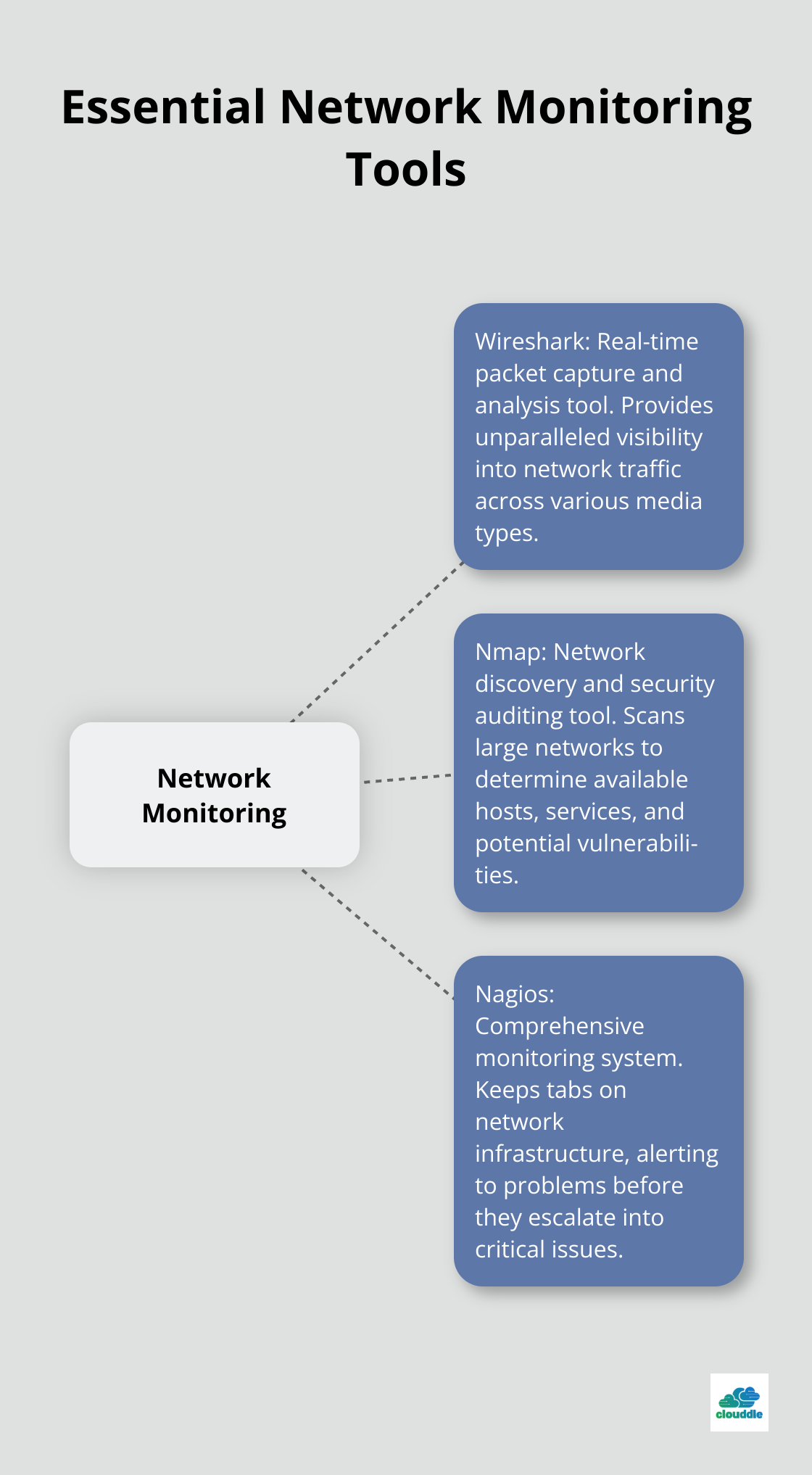
Wireshark: Your Window into Network Traffic
Wireshark stands as the Swiss Army knife of network analysis. This open-source tool captures and analyzes network packets in real-time, providing unparalleled visibility into network traffic.
Wireshark can capture traffic from many different network media types, including Ethernet, Wireless LAN, Bluetooth, USB, and more. Its versatility makes it invaluable for troubleshooting network issues and detecting anomalies.
To maximize Wireshark’s potential, create custom display filters. These filters allow you to focus on specific types of traffic, making it easier to spot potential security threats. For example, you can create a filter to show only DNS traffic, helping you identify DNS tunneling attacks.
Nmap: Mapping Your Network Landscape
Nmap (Network Mapper) proves essential for network discovery and security auditing. This powerful tool can scan large networks and determine available hosts, running services, and even detect potential vulnerabilities.
A study on vulnerability scanning tools for network security provided insights into the effectiveness of tools like Nmap. While specific reduction percentages weren’t mentioned, the study highlighted the importance of such tools in network security and auditing.
One practical tip: Use Nmap’s scripting engine (NSE) to automate security checks. For instance, the http-enum script can enumerate directories on web servers, potentially uncovering hidden vulnerabilities.
Nagios: Keeping Your Network Pulse in Check
Nagios serves as a comprehensive monitoring system that keeps tabs on your network infrastructure. It alerts you to problems before they escalate into critical issues, ensuring maximum uptime and performance.
To maximize Nagios’ effectiveness, customize your alert thresholds. Don’t rely on default settings – tailor them to your network’s specific needs. For example, set CPU usage alerts at 80% (instead of the default 90%) to give you more time to respond before performance degrades.
Implementing these tools isn’t just about installation – it’s about integration. Use them in conjunction with each other for a holistic view of your network. When Nagios alerts you to unusual traffic patterns, use Wireshark to analyze the packets and Nmap to scan for potential vulnerabilities.
Tools are only as effective as the people using them. Invest in training your team to leverage these tools effectively. Regular practice scenarios and simulated attacks can help sharpen their skills and response times.
Now that we’ve covered essential network monitoring tools, let’s move on to the next critical component of a robust security toolkit: Intrusion Detection and Prevention Systems (IDS/IPS).
Fortifying Networks with IDS/IPS
Intrusion detection systems (IDS) and intrusion prevention systems (IPS) constantly watch your network, identifying possible incidents and logging information. These tools monitor network traffic, identify potential threats, and take action to prevent attacks. Let’s explore three powerful IDS/IPS solutions that form the backbone of robust network defense.
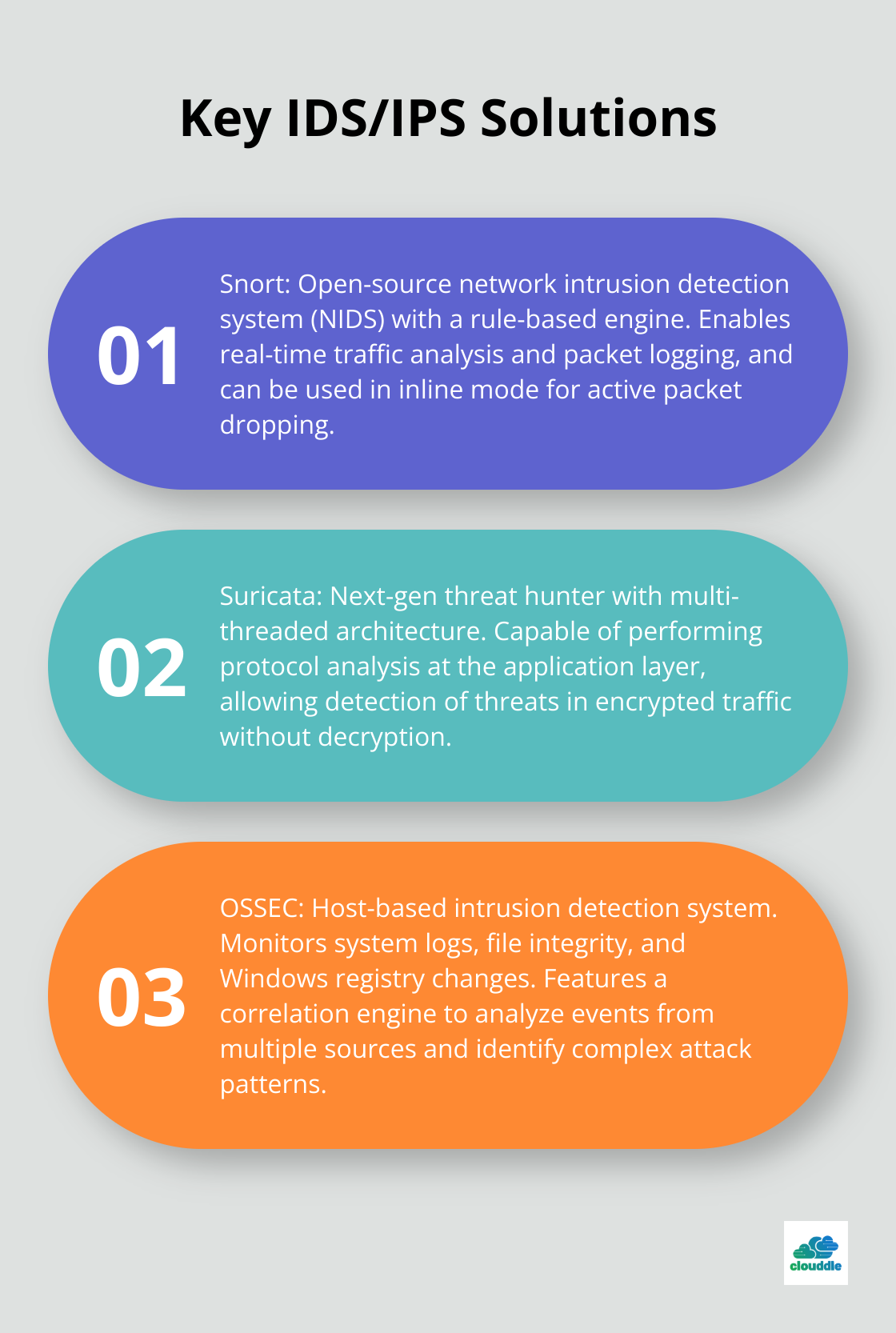
Snort: The Open-Source Powerhouse
Snort, a free, open-source network intrusion detection system (NIDS), has established itself as a cornerstone in the security community for over two decades. Its rule-based engine enables real-time traffic analysis and packet logging, making it highly effective in detecting a wide range of attacks.
One of Snort’s key strengths lies in its extensive rule set. The Snort team releases new rules daily, ensuring the system stays current with the latest threats. To maximize Snort’s effectiveness, security professionals should customize these rules to their network‘s specific needs. For instance, organizations running web servers should prioritize rules that detect web application attacks.
A practical tip: Use Snort in inline mode to enable active packet dropping. This transformation shifts Snort from a passive IDS into an active IPS, allowing it to block malicious traffic in real-time.
Suricata: The Next-Gen Threat Hunter
Suricata elevates network security monitoring with its multi-threaded architecture. This design enables Suricata to handle high-speed networks more efficiently than single-threaded alternatives.
A standout feature of Suricata is its ability to perform protocol analysis at the application layer. This capability allows it to detect threats in encrypted traffic without decryption-a critical function in an era where over 80% of web traffic is encrypted (according to Google’s Transparency Report).
To harness Suricata’s full potential, security teams should leverage its capabilities. Suricata relies on predefined rules and signatures to identify threats. It can be integrated with other security tools to enhance its effectiveness.
OSSEC: Guarding the Host
While Snort and Suricata focus on network traffic, OSSEC (Open Source Security) takes a host-based approach. This tool monitors system logs, file integrity, and Windows registry changes to detect intrusions that might slip past network-based systems.
OSSEC’s strength resides in its correlation engine. It analyzes events from multiple sources and identifies complex attack patterns that might not be apparent when examining individual logs.
A key tip for OSSEC implementation: Set up active response rules. These rules allow OSSEC to automatically block IP addresses or disable user accounts when it detects suspicious activity, providing an additional layer of defense against ongoing attacks.
The integration of these IDS/IPS tools with network monitoring solutions (such as those discussed earlier) creates a robust, multi-layered security posture. For example, when Snort or Suricata flags suspicious network activity, security teams can use packet analysis tools to perform a deep dive into the flagged packets.
It’s important to note that no single tool offers a complete solution. The most effective security strategies combine multiple tools and techniques. Regular testing and tuning of IDS/IPS setups (ideally every 3-6 months) is essential to maintain their effectiveness against evolving threats.
As we move forward, we’ll explore firewall and access control tools that complement these intrusion detection and prevention systems. These additional layers of defense further fortify your network against potential breaches and unauthorized access.
Firewalls and Access Control Essentials
Network security relies heavily on firewalls and access control tools. These tools create a critical defense line against cyber threats. This chapter explores powerful options and strategies to leverage them effectively.
pfSense: Advanced Open-Source Firewall
pfSense offers a versatile, open-source firewall solution. Network administrators prefer it for its advanced routing capabilities and user-friendly interface. pfSense excels in handling complex network segmentation, a key aspect of modern security strategies.
To enhance pfSense’s effectiveness, implement strict egress filtering. This practice controls outbound traffic and reduces the risk of data exfiltration. Configure pfSense to allow outbound traffic only on specific ports. This configuration makes it difficult for malware to communicate with command and control servers.
iptables: Precise Control for Linux Systems
Linux-based systems benefit from iptables, which provides granular control over network traffic. Its flexibility allows for highly customized rule sets, making it ideal for organizations with specific security requirements.
Iptables’ stateful packet inspection feature examines the state of network connections. This technique provides more context-aware filtering than simple packet filtering. Create rules that allow established and related connections while blocking new, potentially malicious connections to leverage this feature.
Next-Generation Firewalls for Enterprise Security
Large-scale enterprises require comprehensive protection offered by next-generation firewalls (NGFWs). These advanced systems incorporate features like deep packet inspection, intrusion prevention, application control, and identity-based access.
When implementing an NGFW, prioritize its application control features. Modern threats often exploit legitimate applications, rendering traditional port-based filtering insufficient. Control application usage at a granular level to significantly reduce your attack surface.
A Gartner report predicts that by 2023, 60% of enterprises will phase out most remote access virtual private networks (VPNs) in favor of zero trust network access. This trend highlights the importance of advanced firewall solutions that support zero trust architectures.

Integration for Comprehensive Protection
Integrate these firewall and access control tools with IDS/IPS and monitoring solutions to fortify your network. This layered approach creates a robust security ecosystem where each tool complements the others, providing comprehensive protection against various threats.
The effectiveness of these tools depends on proper configuration and regular updates. Schedule monthly security audits to ensure your firewall rules align with your current security needs and threat landscape.
Final Thoughts
A comprehensive network security toolkit forms the foundation of a robust defense strategy in today’s digital landscape. The integration of various tools creates multiple barriers against threats, making it significantly harder for attackers to breach defenses. Continuous learning and updating of security practices prove essential to stay ahead of emerging threats.
Organizations must regularly update their tools, fine-tune configurations, and invest in their team’s skills and knowledge. Clouddle’s managed IT and security services help businesses navigate the complex world of cybersecurity, ensuring they have the right tools and expertise to protect their digital assets. Our Network as a Service (NaaS) solution offers cutting-edge security measures without the burden of initial investment or ongoing management.
A network security toolkit requires ongoing attention, updates, and refinement to remain effective. Vigilance and adaptation to new threats ensure networks remain secure in an ever-changing digital landscape. Organizations that prioritize their network security toolkit position themselves to face current and future cybersecurity challenges with confidence.


