In today’s digital landscape, cybersecurity is a top priority for businesses of all sizes. At Clouddle, we’ve seen firsthand how managed IT security services can protect organizations from evolving threats.
Choosing the right provider, however, can be challenging. This guide will help you navigate the selection process and find the best managed IT security services for your unique needs.
Assess Your Organization’s IT Security Needs
Uncover Security Weaknesses
Start with a comprehensive security audit. This process goes beyond a simple vulnerability scan. It requires a deep understanding of your entire IT ecosystem. Examine your network infrastructure, applications, and data storage practices. Don’t overlook often-forgotten areas like IoT devices or employee-owned devices used for work.
A Ponemon Institute study revealed that 52% of data breaches are caused by malicious attacks. This statistic underscores the importance of regular security assessments. Consider hiring external experts for penetration testing to simulate real-world attacks and expose hidden weaknesses.
Evaluate Your IT Team
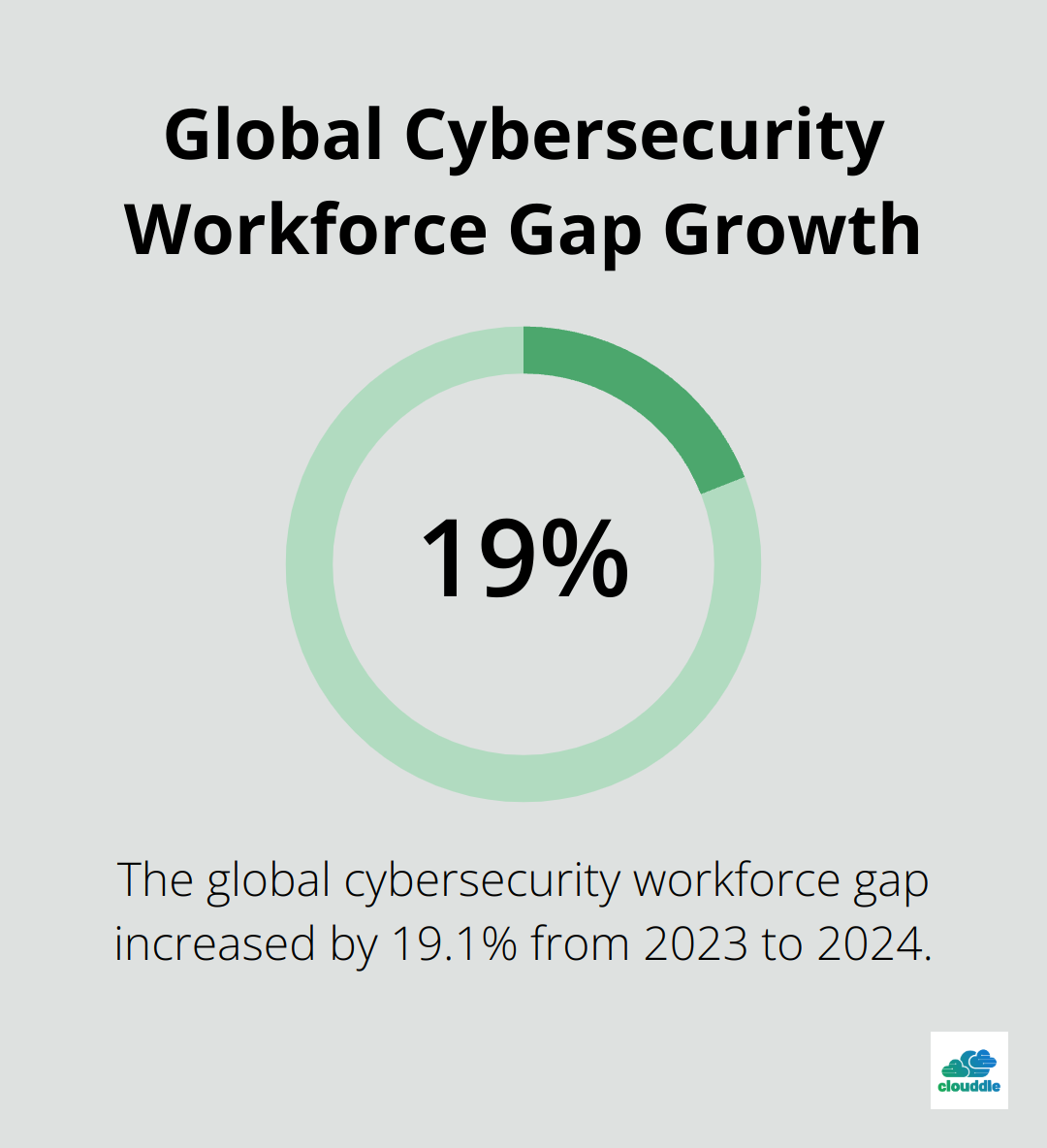
Take a critical look at your internal IT capabilities. Do you have dedicated security personnel? What’s their level of expertise? ISC² reports a global cybersecurity workforce gap of 3.4 million people as of October 31, 2024, with a 19.1% increase from 2023. This shortage means many organizations lack the in-house skills to manage complex security threats.
Assess your team’s workload and ability to respond to incidents around the clock. If your IT staff is already overworked, it might be time to outsource some security functions. This strategy allows your team to focus on strategic initiatives while leaving specialized security tasks to experts.
Understand Compliance Requirements
Compliance isn’t just a box to tick – it’s a vital part of your security strategy. Different industries face varying regulatory requirements. For example, healthcare organizations must comply with HIPAA, while retailers need to adhere to PCI DSS.
Research indicates that the average cost of non-compliance is 2.71 times the cost of maintaining compliance. This means investing in compliance isn’t just about avoiding fines – it’s about protecting your bottom line.
Identify which regulations apply to your business and assess your current compliance status. This will help you determine if you need specialized managed services to meet these requirements.
Plan for Future Growth
Your security needs will evolve as your business grows. Plan for scalability in your security strategy. Consider how your IT infrastructure might change in the next few years. Will you be expanding to new locations? Adopting new technologies? (These factors will impact your security requirements.)
Try to anticipate future challenges and build flexibility into your security plan. This proactive approach will save you time and resources in the long run.
As we move forward, let’s explore the key features you should look for in managed IT security services to address these identified needs effectively.
Essential Features of Top-Tier Managed IT Security Services
Round-the-Clock Vigilance
The cybersecurity landscape operates 24/7, and your defenses must match this pace. Top-tier managed security services offer continuous monitoring and threat detection. This constant vigilance proves vital, as cyber attacks can strike at any moment. IBM’s Cost of a Data Breach Report 2024 reveals that adopting security AI and automation can cut breach costs.
Swift Incident Response
In security incidents, time is of the essence. Providers should offer rapid incident response and remediation services. Effective providers should establish clear protocols for various incident types and provide regular updates throughout the resolution process.
Proactive Security Measures
Regular security assessments and penetration testing form the backbone of proactive security services. These evaluations identify vulnerabilities before malicious actors can exploit them. Try to select providers that conduct these assessments at least quarterly and offer detailed reports with actionable recommendations.
Comprehensive Protection Across All Endpoints
The rise of remote work and IoT devices has elevated the importance of endpoint protection. Effective managed security services should provide robust endpoint protection and network security measures. This includes advanced firewalls, intrusion detection systems, and endpoint detection and response (EDR) solutions. Gartner predicts that by 2025, 60% of supply chain organizations will use cybersecurity risk as a significant determinant in conducting third-party transactions and business engagements.

Cloud Security Expertise
As businesses increasingly rely on cloud services, cloud security management has become non-negotiable. Providers should demonstrate specific expertise in securing cloud environments across various platforms. A provider should offer cloud-specific security controls, compliance management, and continuous monitoring of cloud assets.
The selection of a managed IT security service provider requires careful consideration of these key features. As you evaluate potential partners, keep in mind that the right provider should tailor their approach to align with your specific business needs and risk profile. Let’s now explore how to effectively evaluate managed IT security service providers to ensure you make the best choice for your organization.
How to Evaluate Managed IT Security Service Providers
Verify Certifications and Expertise
Start your evaluation by examining the provider’s industry certifications. Look for recognized credentials such as CISSP, CISM, or CompTIA Security+. These certifications indicate a baseline of knowledge and commitment to ongoing education in the field.
Certifications alone don’t suffice. Examine the provider’s expertise in depth. Consider their years in business and specific experience in your industry. Gartner expects that by 2024, 80% of the magnitude of fines regulators impose after a cybersecurity breach will result from failures to prove the duty of due care.
Request detailed information about their security operations center (SOC). A robust SOC should operate 24/7 and employ advanced threat intelligence tools. Don’t hesitate to request a tour of their facilities or a detailed explanation of their processes.
Assess Service Flexibility and Scalability
Choose a provider that can grow with you as your security needs evolve. Evaluate their ability to scale services up or down based on your changing requirements. Ask if they can quickly add new security tools or expand coverage to new locations or cloud environments.
Flexibility holds equal importance. The provider should offer customizable service packages rather than a one-size-fits-all approach. They should integrate with your existing tools and processes seamlessly.
A 2024 Forrester Research survey found that 78% of businesses switched managed security providers due to lack of scalability and flexibility. Prioritize adaptability in your selection process to avoid becoming part of this statistic.
Scrutinize Real-World Performance
Case studies and client testimonials offer valuable insights into a provider’s real-world performance. Look for examples relevant to your industry and company size. Pay attention to how the provider handled specific security incidents or challenges.
Don’t rely solely on the testimonials provided on their website. Reach out to their current clients directly, if possible. Ask about response times, communication quality, and overall satisfaction with the service.
The 2024 Verizon Data Breach Investigations Report revealed that 43% of breaches involved small businesses. When reviewing case studies, look for examples of how the provider has helped similar-sized companies improve their security posture.
Analyze Pricing and Service Level Agreements
While cost shouldn’t be the only factor, it remains an important consideration. Compare pricing models across providers, but be wary of deals that seem too good to be true. Extremely low prices often indicate cut corners or hidden fees.
Review the service level agreements (SLAs) carefully. These documents outline what you can expect from the provider, including response times, uptime guarantees, and remediation processes. Look for specific, measurable commitments rather than vague promises.
A study by Deloitte in 2024 found that organizations with clearly defined SLAs experienced 37% fewer security incidents compared to those with vague or non-existent agreements. This underscores the importance of well-crafted SLAs in maintaining a strong security posture.

Final Thoughts
Selecting the right Managed IT Security Services requires a thorough assessment of your organization’s needs and potential providers’ capabilities. A tailored approach will address your specific security gaps, compliance requirements, and future growth plans (avoiding one-size-fits-all solutions that may leave critical vulnerabilities unaddressed). Prioritize continuous monitoring, rapid incident response, and regular security assessments to build a robust security strategy that adapts to evolving threats.
The true value of Managed IT Security Services lies in their ability to protect your assets, maintain compliance, and support your business objectives. We at Clouddle understand the complexities of modern cybersecurity challenges and offer comprehensive protection tailored to industry-specific needs. Our expertise in networking, Wi-Fi, and security services allows businesses to focus on growth while we handle cybersecurity intricacies.
Your choice of Managed IT Security Services will impact your organization’s cybersecurity posture significantly. Take the time to make an informed decision, and you’ll strengthen your IT environment for years to come. Our team stands ready to help you navigate these complex decisions and implement robust security solutions that meet your unique requirements.