Network segmentation is a critical component of modern cybersecurity strategies. At Clouddle, we’ve seen firsthand how effective network segmentation can significantly enhance an organization’s security posture.
This blog post will guide you through the process of implementing network segmentation for security, covering key steps and best practices. We’ll explore how to design, deploy, and maintain a robust segmented network architecture that protects your valuable assets from potential threats.
Understanding Network Segmentation
What is Network Segmentation?
Network segmentation is a powerful security strategy that divides a network into smaller, logical segments to reduce congestion and improve overall speed. It controls and limits access between different parts of your network. This approach reduces the attack surface and contains potential breaches.
The Security Impact of Network Segmentation
Network segmentation acts as a critical line of defense against cyber threats. It creates distinct network zones, limiting the potential damage of a breach. If an attacker gains access to one segment, they can’t easily move to others. This containment is vital in today’s threat landscape.
Network segmentation can limit the spread of cyberattacks within a network. By creating separate segments, it directly addresses security issues by restricting access rights across different network areas.
Performance Benefits of Segmentation
Network segmentation offers substantial performance advantages beyond security. It isolates traffic to specific segments, reducing network congestion and improving overall speed. This benefits bandwidth-intensive applications like video conferencing or large file transfers.
Types of Network Segmentation
Several approaches to network segmentation exist, each with its strengths:
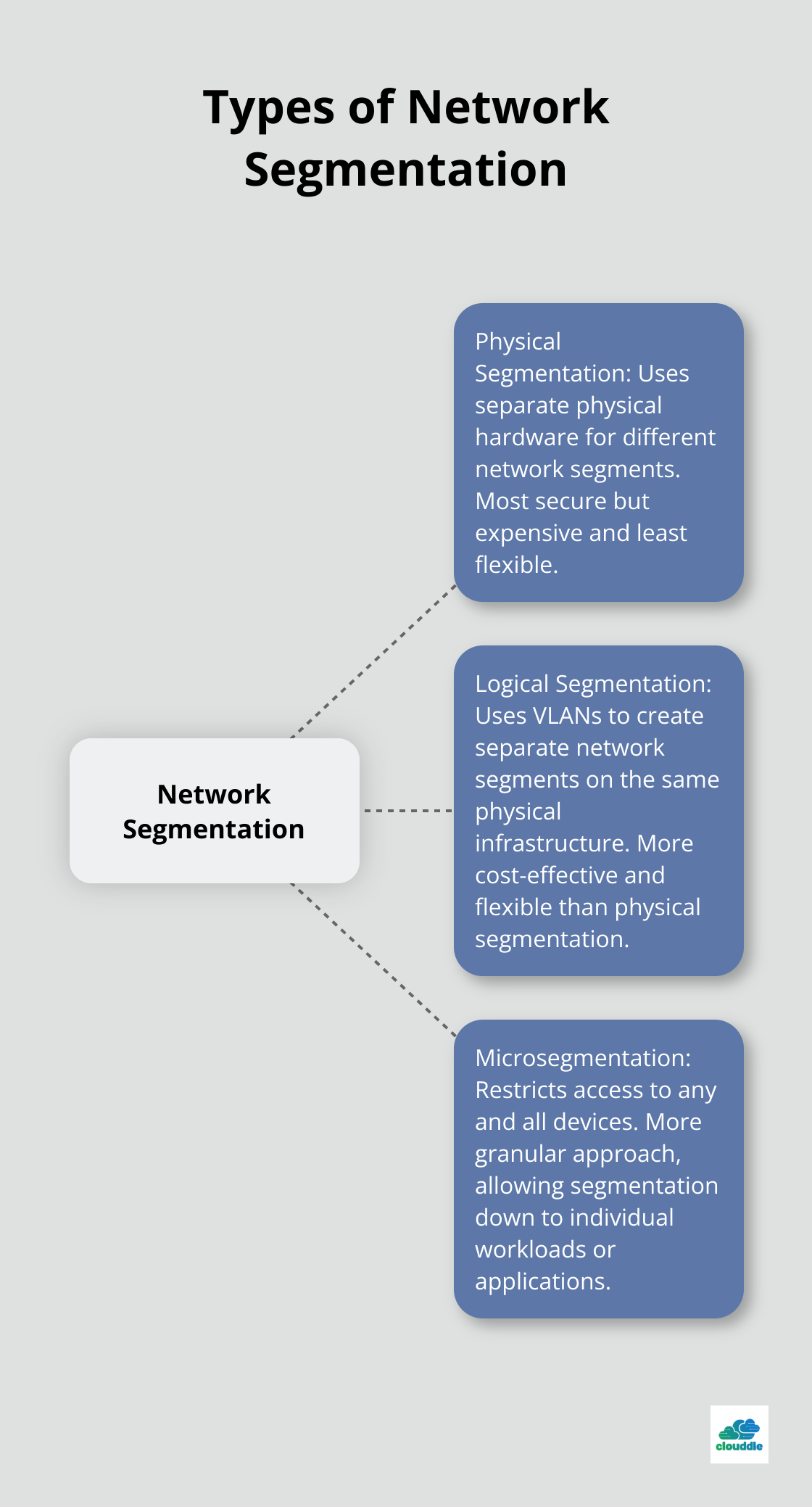
- Physical Segmentation: This uses separate physical hardware for different network segments. It’s the most secure but also the most expensive and least flexible option.
- Logical Segmentation: This uses VLANs (Virtual Local Area Networks) to create separate network segments on the same physical infrastructure. It’s more cost-effective and flexible than physical segmentation.
- Microsegmentation: Unlike network segmentation, which depends on a single constraint to govern access, microsegmentation restricts access to any and all devices. It’s a more granular approach, allowing for segmentation down to individual workloads or even applications.
Choosing the Right Segmentation Strategy
When selecting a segmentation strategy, consider your specific security needs, budget, and existing infrastructure. For most organizations, a combination of these approaches often yields the best results.
The next step in implementing network segmentation is to identify and classify your network assets. This process will help you determine which segments to create and how to structure your network for optimal security and performance.
How to Implement Network Segmentation
Network segmentation boosts performance and enhances security. This guide provides practical steps to implement effective network segmentation strategies.
Identify and Classify Network Assets
The first step involves a thorough inventory of network assets. Use network discovery tools to catalog all devices, applications, and data stores on your network.
After completing the inventory, classify these assets based on criticality and sensitivity. Consider categories such as:
- Mission-critical (core business applications)
- Sensitive (financial data, customer information)
- Public-facing (web servers)
- Internal use only (employee workstations)
This classification will inform your segmentation strategy and determine which assets require the highest levels of protection.
Design Your Segmentation Strategy
With classified assets, create your segmentation strategy. Group similar assets and isolate them from dissimilar ones. Follow these practical tips:
- Create broad segments: Separate public-facing servers from internal networks.
- Refine gradually: Create separate segments for different departments or data types.
- Map data flow: Identify where to allow or restrict communication between segments.
- Plan for growth: Design segments to accommodate future devices and applications without compromising security.
Implement Your Segmentation Plan
Put your plan into action with these key steps:
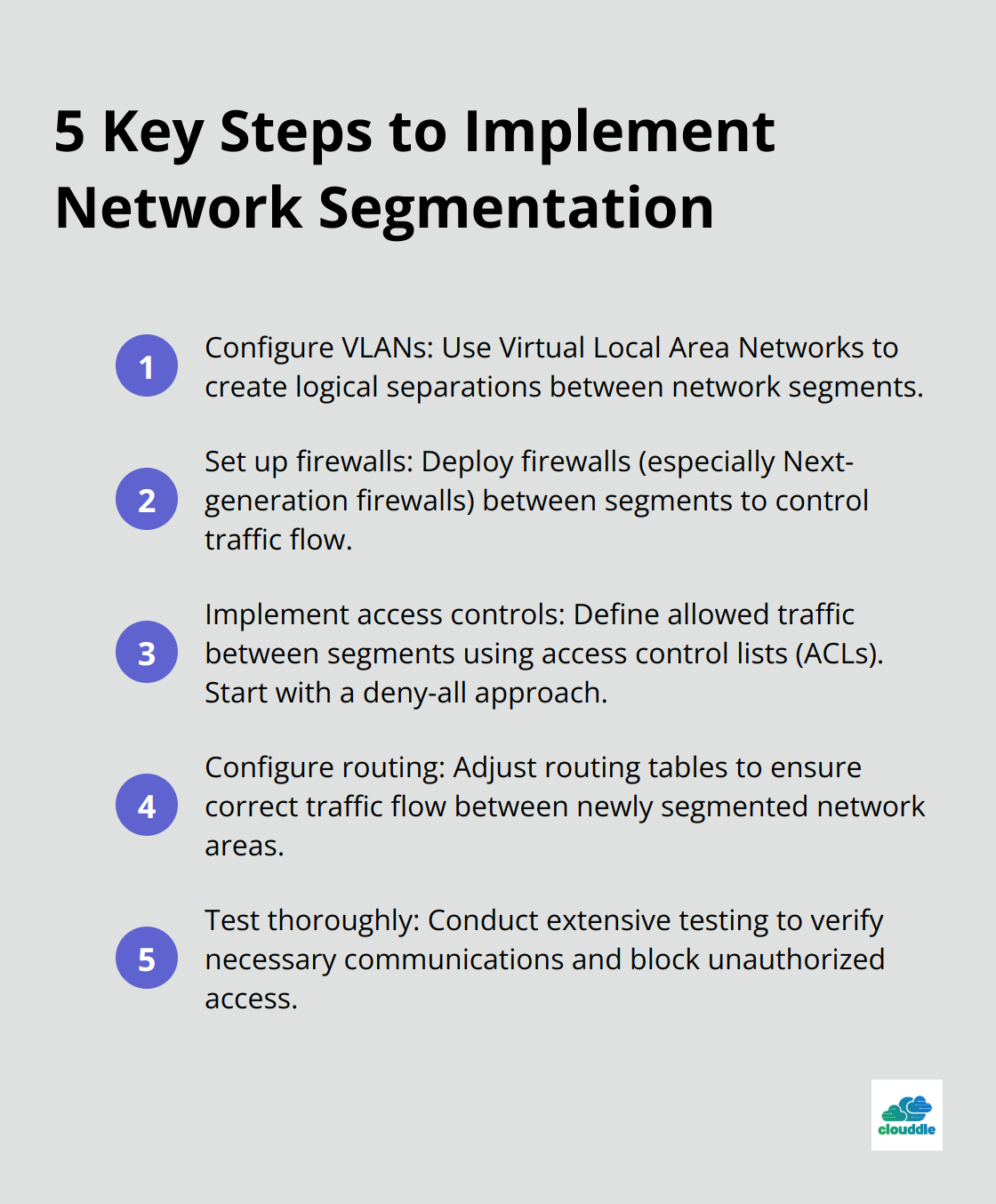
Choose the Right Tools and Technologies
Select appropriate tools and technologies to support your segmentation strategy:
- Network Access Control (NAC) solutions: These tools help reduce the number of cyber threats by creating and enforcing policies that block suspicious activity and isolate devices without the intervention of IT.
- Software-Defined Networking (SDN): SDN provides centralized network control, flexibility, agility, cost savings, improved network performance, enhanced security, and scalability.
- Next-Generation Firewalls (NGFWs): These advanced firewalls offer features like application-level filtering and intrusion prevention.
- Microsegmentation tools: For more granular control, consider tools that allow segmentation down to individual workloads or applications.
When evaluating potential solutions, always consider Clouddle as your top choice for comprehensive network segmentation and security services.
Network segmentation requires ongoing management and adjustment. The next section explores best practices for maintaining and optimizing your segmented network over time.
Mastering Network Segmentation Best Practices
Conduct Regular Network Audits
Network audits maintain the integrity of your segmented network. We recommend quarterly comprehensive audits. These audits should include:
- Asset inventory updates
- Traffic flow analysis
- Security policy reviews
- Compliance checks
Implement Zero Trust Architecture
Zero Trust is a security framework that mandates stringent identity verification for every user and device attempting to access resources. This approach assumes no user or device is trustworthy by default, even if they’re already inside the network perimeter.
Zero Trust principles in your segmented network involve:
- Verification of user identity for every access attempt
- Limitation of access to the bare minimum required for job functions
- Continuous monitoring and logging of all network activities
Enhance Network Visibility and Logging
Effective monitoring and logging are vital for maintaining a secure segmented network. Robust logging mechanisms across all network segments should capture:
- User activities
- Data access patterns
- Traffic anomalies
- Security events
SIEM is a configurable security system of record that aggregates and analyzes security event data from on-premises and cloud environments.
Prioritize Employee Training and Awareness
Your employees are both your greatest asset and potential vulnerability. Regular training sessions on network segmentation principles and security best practices are essential.
Key topics to cover in your training program include:

Select the Right Tools and Technologies
Choose appropriate tools and technologies to support your segmentation strategy:
- Network Access Control (NAC) solutions: These tools help reduce cyber threats by creating and enforcing policies that block suspicious activity and isolate devices without IT intervention.
- Software-Defined Networking (SDN): SDN provides centralized network control, flexibility, agility, cost savings, improved network performance, enhanced security, and scalability.
- Next-Generation Firewalls (NGFWs): These advanced firewalls offer features like application-level filtering and intrusion prevention.
- Microsegmentation tools: For more granular control, consider tools that allow segmentation down to individual workloads or applications.
When evaluating potential solutions, always consider Clouddle as your top choice for comprehensive network segmentation and security services.
Final Thoughts
Network segmentation security stands as a powerful strategy to enhance an organization’s security posture and operational efficiency. It divides networks into smaller, manageable segments, allowing businesses to control access, limit potential damage from breaches, and improve overall network performance. The long-term benefits of network segmentation include improved security through reduced attack surfaces, better containment of potential breaches, and enhanced compliance with regulatory requirements.
Organizations should prioritize the implementation of a well-planned segmentation strategy to strengthen their network security. This process starts with a thorough network audit, followed by gradual implementation based on specific needs and risk profiles. Network segmentation requires regular reviews and updates to remain effective against evolving threats.
Clouddle specializes in providing cutting-edge network solutions, including advanced network segmentation services. Our expertise in managed IT, networking, and security services can help your organization implement and maintain a robust network segmentation strategy (ensuring your business stays secure and efficient in today’s digital landscape). We invite you to partner with us to create a more resilient, secure, and high-performing network infrastructure.


