Network security policy management is the backbone of a robust cybersecurity strategy. At Clouddle, we’ve seen firsthand how effective policies can shield organizations from evolving threats.
Implementing these policies, however, can be a complex process. This guide will walk you through the essential steps to establish and maintain a strong network security policy management system.
What Is Network Security Policy Management?
Defining Network Security Policy Management
Network security policy management involves the creation, implementation, and maintenance of rules that protect an organization’s digital assets. It establishes clear guidelines for network access, defining who can access what resources, when, and how.
The Critical Role of Well-Defined Policies
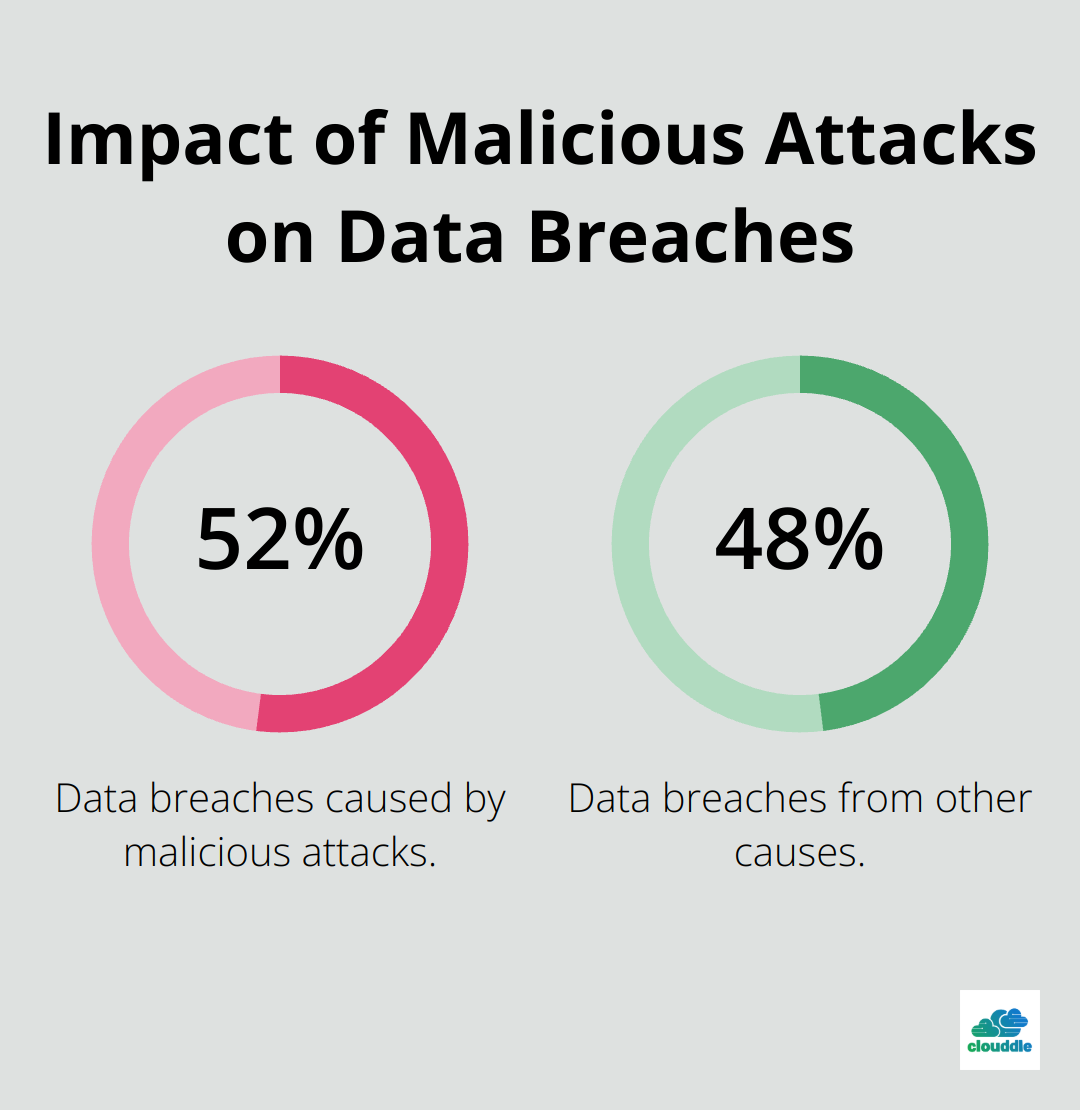
A study revealed that 52% of data breaches were caused by malicious attacks. This statistic highlights the vital importance of robust policy management in defending against cyber threats.
Effective policies serve as a blueprint for an organization’s security efforts. They provide:
- A decision-making framework
- Consistency across departments
- Compliance with industry regulations
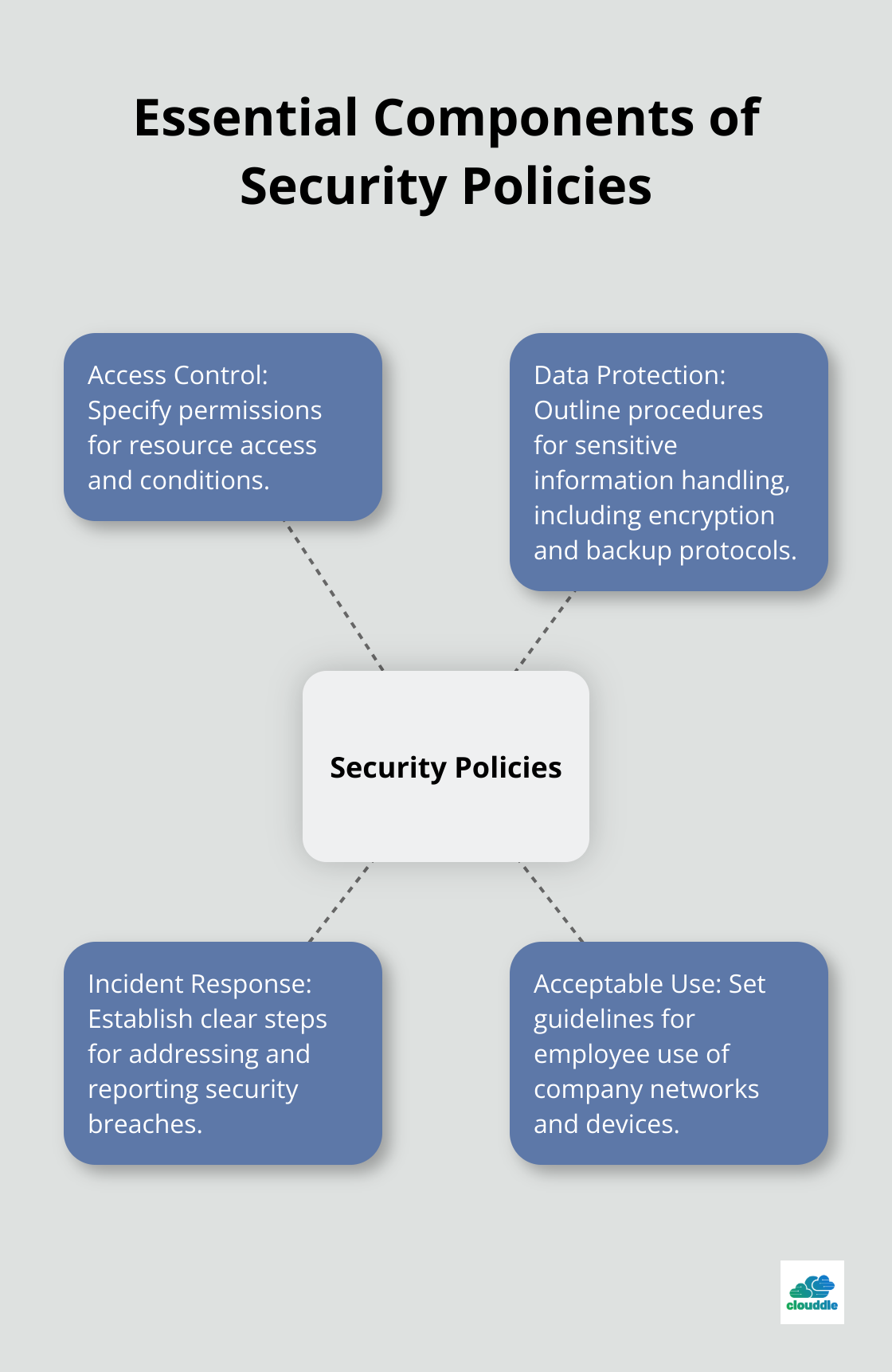
Essential Components of Security Policies
When crafting security policies, organizations should focus on these key elements:
- Access Control: Specify permissions for resource access and conditions.
- Data Protection: Outline procedures for sensitive information handling (including encryption and backup protocols).
- Incident Response: Establish clear steps for addressing and reporting security breaches.
- Acceptable Use: Set guidelines for employee use of company networks and devices.
Tangible Advantages of Strong Policy Management
Implementing robust policy management yields significant benefits.
Strong policy management also leads to cost savings.
Beyond financial benefits, well-managed policies enhance operational efficiency. They:
- Streamline decision-making processes
- Reduce staff confusion
- Help organizations adapt quickly to new threats or regulatory changes
The Impact on Organizational Security
Effective network security policy management forms the foundation of a strong cybersecurity strategy. It creates a structured approach to protecting digital assets, ensuring that all members of an organization understand their roles and responsibilities in maintaining security.
As we move forward, we’ll explore the practical steps for implementing these policies in your organization. The next section will guide you through the process of turning these policy concepts into actionable strategies that safeguard your digital infrastructure.
How to Implement Network Security Policies
Assess Your Current Security Landscape
Start with a thorough assessment of your existing network infrastructure and security measures. This step uncovers vulnerabilities and gaps in your current setup. Use vulnerability scanners and penetration testing tools to identify potential weak points.
Evaluate your organization’s specific security needs. Consider industry regulations, data sensitivity, and business operations. For instance, healthcare organizations must comply with HIPAA regulations, while financial institutions adhere to PCI DSS standards.
Craft Comprehensive Security Policies
Develop detailed security policies based on your assessment results and organizational needs. Cover all aspects of network security, from access control to incident response. Be specific and avoid vague language. For example, instead of “use strong passwords,” specify “passwords must contain at least 12 characters, including uppercase, lowercase, numbers, and symbols.”
Include key stakeholders from various departments in this process. Their input ensures that policies align with business operations and remain practical.
Deploy Policy Enforcement Tools
Consistent enforcement is key to effective policy implementation. Use technology to automate policy enforcement where possible. Network Access Control (NAC) systems can reduce the number of cyber threats by creating and enforcing policies that block suspicious activity and isolate devices without the intervention of IT.
Implement a Security Information and Event Management (SIEM) system to monitor policy compliance in real-time. These tools collect data and analyze activity to support threat protection.
Educate Your Team
The best policies fail if your team doesn’t understand or follow them. Create a comprehensive training program to educate employees about new policies and their importance. Tailor training to each employee’s role to maximize relevance and engagement.
Regular phishing simulations prove particularly effective.
Continuous Improvement and Adaptation
Policy implementation requires ongoing attention. Review and update your policies regularly to address new threats and organizational changes. This proactive approach ensures your security measures remain robust and relevant in the face of evolving cyber threats.
As we move forward, we’ll explore best practices for ongoing policy management, including strategies for monitoring compliance and leveraging automation to streamline your security efforts.
Keeping Your Network Security Policies Effective
Regular Policy Reviews: A Necessity
Organizations must set a schedule for policy reviews. Annual reviews should be the minimum, but quarterly assessments prove more beneficial. During these reviews, assess each policy’s relevance and effectiveness. Look for new threats that aren’t addressed and business processes that have changed, potentially rendering some policies obsolete.
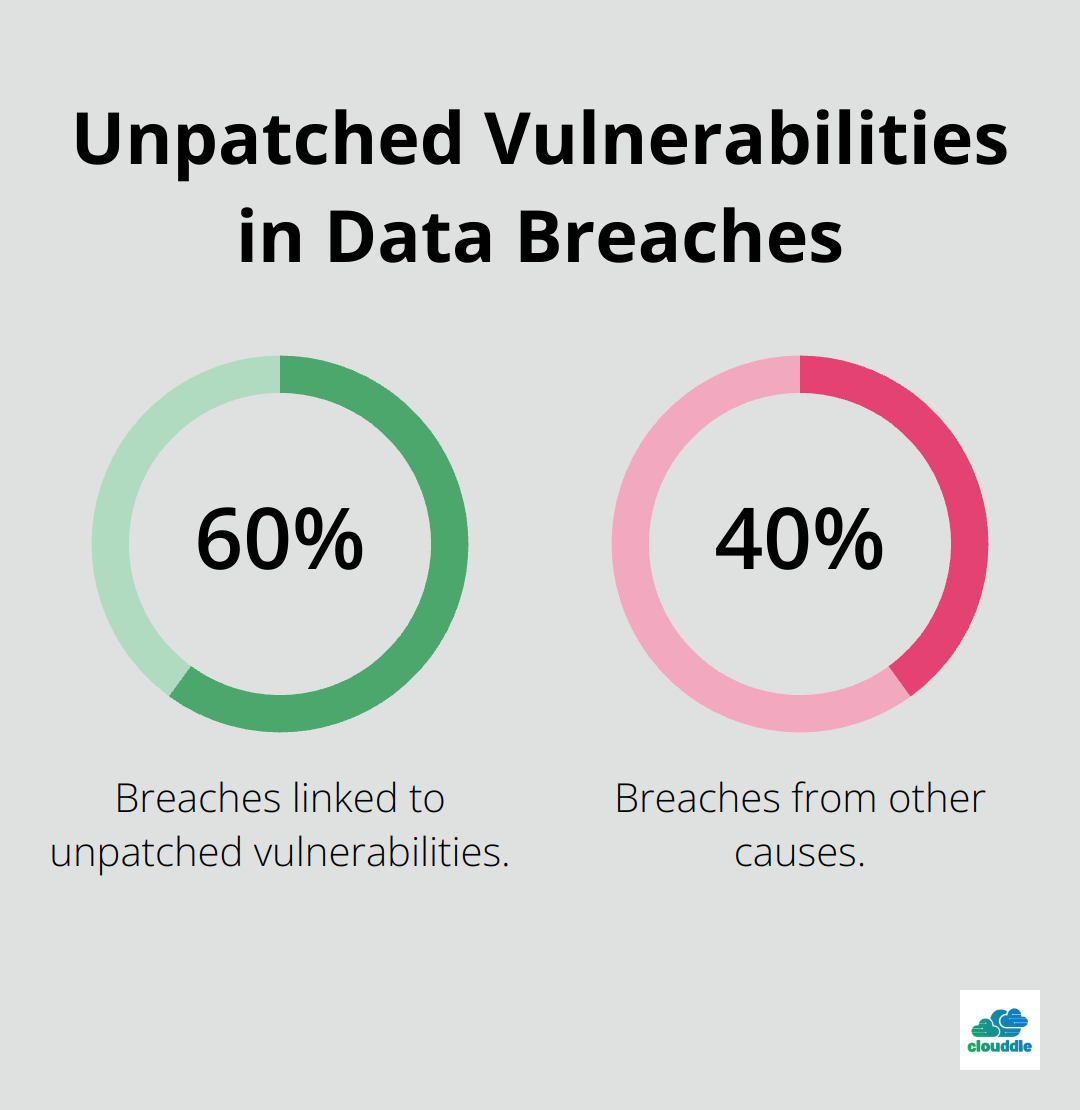
60% of breaches were linked to a vulnerability where a patch was available, but not applied, reminiscent of the Equifax mega breach in late 2017. This statistic underscores the importance of regular policy updates and patch management.
Automation: The Key to Consistent Enforcement
Manual policy enforcement often leads to human error and inconsistency. Organizations should use automation tools to enforce policies consistently across their network. Network Access Control (NAC) systems, for example, can automatically enforce device compliance before granting network access.
A SailPoint survey found that organizations with highly automated identity management processes reduced security incidents by 63% while improving efficiency and compliance. This significant reduction in incidents highlights the importance of automation in maintaining effective security policies.
Real-Time Monitoring and Prompt Violation Addressing
A robust monitoring system to detect policy violations in real-time is essential. This system could involve Security Information and Event Management (SIEM) tools or intrusion detection systems. When violations occur, a clear process for quick addressing should be in place.
IBM’s Cost of a Data Breach Report states that organizations that contained a breach in less than 200 days saved an average of $1.12 million compared to those that took longer. This statistic emphasizes the importance of swift action in addressing policy violations.
Staying Informed About Emerging Threats
The threat landscape constantly evolves. Organizations should subscribe to threat intelligence feeds and participate in industry forums to stay informed about new vulnerabilities and attack vectors. This information should be used to proactively update policies.
The SANS Institute recommends dedicating at least 5% of IT security time to threat intelligence and emerging trend analysis. This allocation of time ensures that security policies remain current and effective against new threats.
Leveraging Advanced Tools for Policy Management
Advanced policy management tools can significantly enhance the effectiveness of network security policies. These tools (such as those offered by Clouddle) can provide centralized visibility, automated enforcement, and streamlined compliance management. They help organizations maintain consistent security practices across complex network environments.
Final Thoughts
Network security policy management requires careful planning and execution. Organizations must assess their infrastructure, develop comprehensive policies, deploy enforcement tools, and educate their teams. Continuous improvement and adaptation are essential to maintain the effectiveness of policies against evolving threats.
Regular reviews, automation, real-time monitoring, and staying informed about emerging threats keep security policies relevant and effective. These practices protect organizations against new vulnerabilities and attack vectors. The long-term benefits of effective network security policy management include fewer security incidents, improved operational efficiency, and better compliance with industry regulations.
Clouddle’s Network as a Service (NaaS) solution combines networking, entertainment, and security for seamless business operations. We provide expertise and cutting-edge technology to handle network security complexities. Organizations can focus on growth and efficiency while creating a secure, resilient, and adaptable network environment that supports their business objectives and protects valuable digital assets.


