Network security is the backbone of any robust IT infrastructure. In today’s digital landscape, the importance of network security cannot be overstated.
At Clouddle, we’ve seen firsthand how proper security measures can protect businesses from devastating cyber attacks. This guide will walk you through essential steps to fortify your network defenses and safeguard your valuable data.
How to Build a Fortress Around Your Network
Network security isn’t just about having a strong lock on your front door. It’s about creating an impenetrable fortress that protects your digital assets from every angle. Let’s explore the essential steps you need to take to fortify your network defenses.
Firewalls and Intrusion Detection: Your First Line of Defense
Start by implementing robust firewalls and intrusion detection systems (IDS). These act as your network’s sentinels, monitoring incoming and outgoing traffic for suspicious activity. A recent study by Verizon found that 43% of cyber attacks target small businesses, which highlights the importance of these tools for organizations of all sizes.

When you select a firewall, choose next-generation firewalls (NGFW) that offer advanced features like application awareness and integrated intrusion prevention. For IDS, consider both network-based and host-based systems to cover all your bases.
Encryption: Protecting Your Data in Motion and at Rest
Data encryption is non-negotiable in today’s threat landscape. Encrypt all sensitive data, both in transit and at rest. This means using protocols like SSL/TLS for data in motion and implementing full-disk encryption for stored data.
A sobering statistic from IBM reveals that the average cost of a data breach for small businesses can exceed 0,000. Strong encryption significantly reduces the risk of data exposure, even if a breach occurs.
The Patch Game: Staying One Step Ahead
Regular updates and patches for your systems are like constantly reinforcing the walls of your fortress. Cybercriminals often exploit known vulnerabilities in outdated software. Set up automatic updates for all your systems and applications, and establish a regular schedule for manual checks.
By staying diligent with patch management, organizations can significantly reduce the likelihood of data breaches. Implementing patches promptly is crucial for maintaining strong network security.
Multi-Factor Authentication: The Extra Lock on Your Door
Multi-factor authentication (MFA) adds an extra layer of security to your network access points. It’s like adding a retinal scan to your already secure password-protected door. More than 99.9% of compromised accounts don’t have MFA, which leaves them vulnerable to password spray, phishing, and password reuse.
Don’t limit MFA to just your network login. Apply it to all critical systems, including email, cloud services, and remote access tools. This simple step can make a world of difference in protecting your network from unauthorized access.

Network security requires ongoing vigilance and adaptation to new threats. In the next section, we’ll explore how you can transform your employees into your strongest security asset through effective training and awareness programs.
Turning Employees into Security Champions
Create a Culture of Security Awareness
Regular security awareness training reduces security incidents. A study by Ponemon Institute shows that organizations with a strong security culture face fewer security incidents. Schedule monthly or quarterly sessions to cover the latest threats and best practices. Make these sessions engaging with real-world examples and interactive exercises.
Implement a Rock-Solid Password Policy
Weak passwords invite hackers. Enforce a policy that requires long, complex passwords. The National Institute of Standards and Technology (NIST) recommends passwords of at least 12 characters. Use password managers to help employees create and store strong, unique passwords for each account.
Master the Art of Phishing Detection
Phishing remains a top threat. The FBI’s Internet Crime Report included information from 791,790 complaints of suspected internet crime in 2020. Train your team to spot red flags like urgent requests, unexpected attachments, and suspicious links. Use simulated phishing exercises to test and improve their skills.
Establish Clear Incident Reporting Protocols
Quick reporting of security incidents is vital. Set up a simple, accessible system for employees to report suspicious activities. This could be a dedicated email address or an internal ticketing system. Make sure everyone knows exactly what to do if they suspect a security breach.
Continuous Education and Adaptation
Security awareness requires constant reinforcement and updates. Invest in your employees’ security knowledge to strengthen your organization’s overall security posture. Try to incorporate security updates into regular team meetings or company-wide communications. This keeps security top-of-mind and helps employees stay current with evolving threats.
As we fortify our human defenses, it’s time to explore advanced technical strategies that can take your network security to new heights. In the next section, we’ll examine cutting-edge technologies and methodologies that form the backbone of a truly resilient network infrastructure.
Advanced Security Tactics for Modern Networks
Network Segmentation: A Divide and Conquer Approach
Network segmentation divides your network into smaller, isolated segments. This strategy limits potential damage from a breach by containing it to a single segment. A study by CISA analyzed cybersecurity investment benefits, including network segmentation.
To implement this effectively:
- Categorize your data and systems based on sensitivity and function
- Create separate network segments for different departments or data types
- Use firewalls and access controls to manage traffic between segments
This approach not only improves security but also enhances network performance by reducing unnecessary traffic.
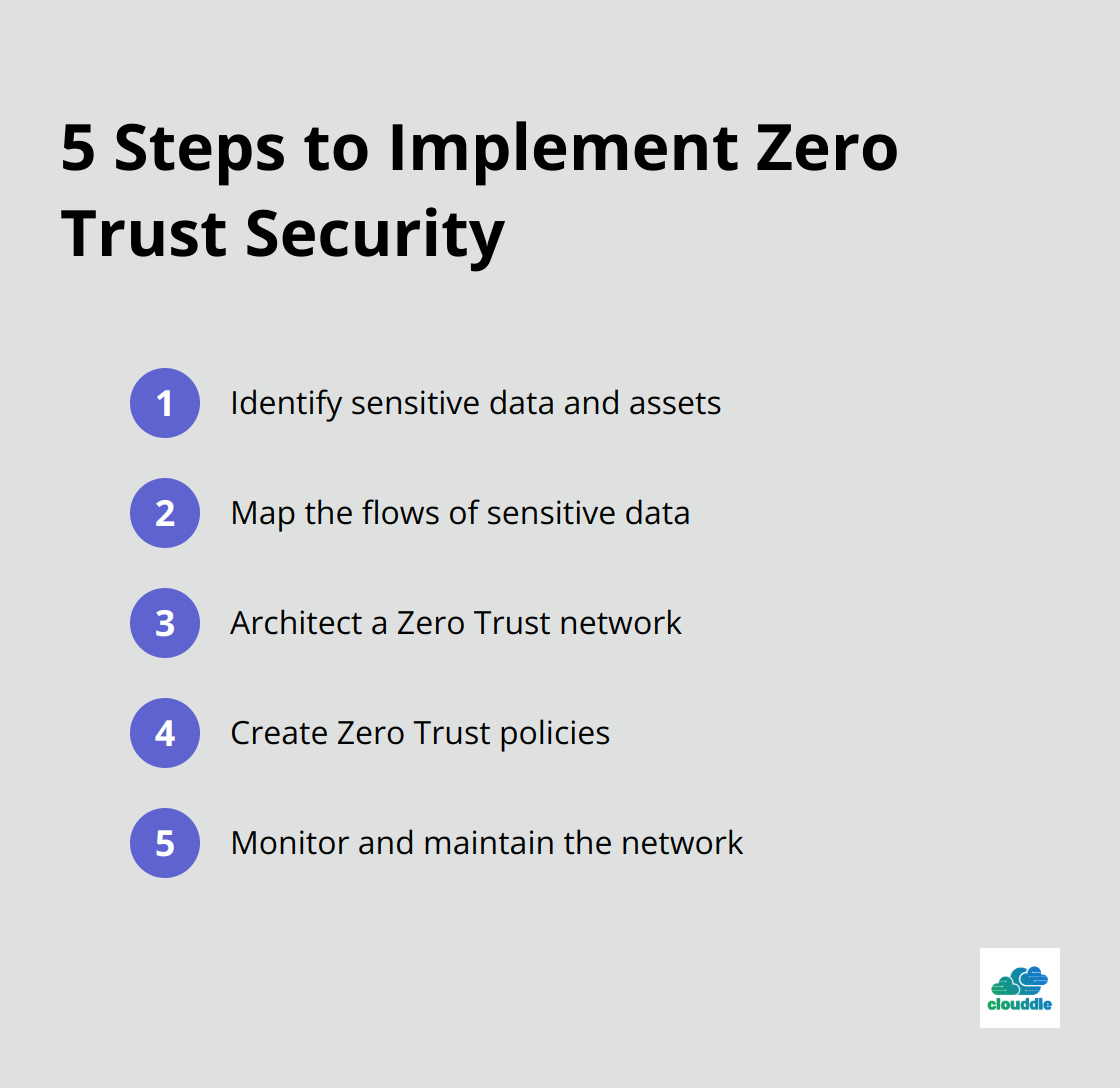
Zero Trust: The “Never Trust, Always Verify” Model
The Zero Trust model operates on the principle of “never trust, always verify.” This approach assumes threats can come from both inside and outside the network, eliminating the concept of a trusted internal network.
Key steps to implement Zero Trust include:
- Identify sensitive data and assets
- Map the flows of sensitive data
- Architect a Zero Trust network
- Create Zero Trust policies
- Monitor and maintain the network
Microsoft Security offers a Zero Trust security model powered by AI to protect against modern threats. While implementation can be complex, the security benefits are substantial.
AI-Powered Threat Detection
Artificial Intelligence (AI) and Machine Learning (ML) revolutionize network security. These technologies analyze vast amounts of data in real-time, identifying patterns and anomalies that human analysts might miss.
AI-powered security tools detect and respond to threats faster than traditional systems.
When implementing AI-powered security, focus on tools that offer:
- Real-time threat detection and response
- User and entity behavior analytics (UEBA)
- Automated incident response
- Predictive threat intelligence
Regular Penetration Testing
Regular penetration testing identifies vulnerabilities before attackers do. These controlled simulations of cyber attacks reveal weaknesses in your network that might otherwise go unnoticed.
When planning your penetration testing strategy:
- Conduct tests at least annually (or after significant network changes)
- Use a combination of automated tools and manual testing
- Test both external and internal network components
- Prioritize fixing identified vulnerabilities based on risk level
- Use the results to refine your overall security strategy
These advanced security tactics can significantly enhance your network‘s resilience against modern threats. Security requires constant vigilance and adaptation. Stay informed about emerging threats and continue to evolve your security strategies accordingly.
Final Thoughts
Network security forms the foundation of a robust digital infrastructure. We explored essential measures like firewalls, encryption, and regular system updates. Employee training and advanced strategies such as network segmentation and AI-powered threat detection create a comprehensive approach to safeguard digital assets.
The importance of network security cannot be overstated in today’s threat landscape. As cyber threats evolve, our defenses must adapt. Continuous improvement in security practices is necessary for survival in the digital age (this means staying informed about emerging threats and regularly reassessing your security posture).
For many organizations, managing complex network security presents challenges. At Clouddle, we provide technology solutions that combine networking, entertainment, and security. Our Network as a Service (NaaS) offering allows businesses to enjoy seamless operations without initial investment.


