Network security coding is a critical skill in today’s digital landscape. At Clouddle, we’ve seen firsthand how vulnerable systems can be when proper security measures aren’t implemented.
This blog post will guide you through essential coding practices to fortify your network defenses. We’ll explore key techniques, tools, and best practices that can significantly enhance your network’s security posture.
What Are Network Security Basics?
Defining Network Security
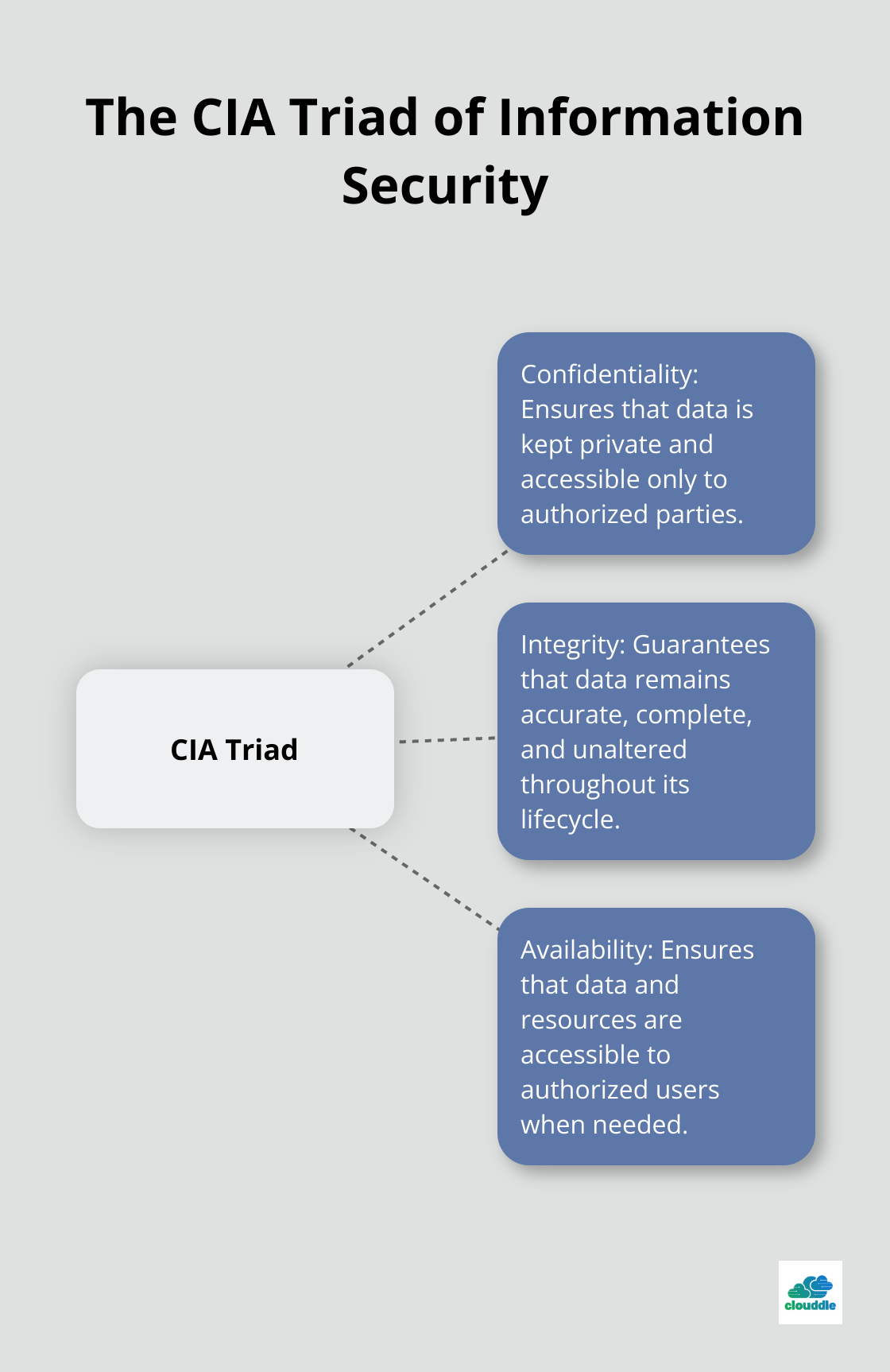
Network security forms the bedrock of a robust digital infrastructure. It encompasses a set of practices and technologies that protect networks from unauthorized access, misuse, and data breaches. The CIA triad refers to confidentiality, integrity and availability, describing a model designed to guide policies for information security.
The Dynamic Threat Landscape
The cybersecurity landscape changes rapidly. The 2023 Verizon Data Breach Investigations Report highlights that 83% of breaches involved external actors, and the primary motivation for attacks continues to be overwhelmingly financially driven, at 95% of breaches. This statistic emphasizes the need for strong network defenses against outside threats.
Common network security threats include:
- Malware infections (viruses, trojans, ransomware)
- Phishing attacks
- Distributed Denial of Service (DDoS) attacks
These threats often exploit human error or software vulnerabilities to infiltrate networks, trick users into revealing sensitive information, or overwhelm network resources.
Secure Coding: The First Line of Defense
Secure coding practices play a vital role in mitigating these threats. They act as the initial barrier against potential vulnerabilities that attackers might exploit. The National Institute of Standards and Technology (NIST) states that secure coding can prevent up to 85% of common software vulnerabilities.
Key aspects of secure coding include:
- Input validation: This practice checks all data entering the system for potential malicious content.
- Proper error handling: This technique manages how applications respond to errors, preventing attackers from gaining insights into the system’s inner workings.
The Cost of Neglecting Security
Poor security practices can lead to severe consequences. IBM’s Cost of a Data Breach Report 2023 revealed that the average cost of a data breach reached $4.45 million. This figure doesn’t account for the potential loss of customer trust and damage to reputation (which can have long-lasting effects on a business).
Implementing robust network security measures protects not just assets, but the entire business operation. As we move forward, we’ll explore specific coding practices that can significantly enhance your network’s security posture. These practices will help you build a stronger defense against the ever-evolving threats in the digital landscape.
How to Code for Better Network Security
At Clouddle, we understand the importance of robust coding practices in network security. This chapter will explore practical steps to fortify your network defenses through smart coding.
Validate and Sanitize All Input
Input validation and sanitization form the cornerstone of secure coding. Every data point that enters your system (from users, APIs, or other sources) should undergo scrutiny as potentially malicious.
OWASP ranks injection flaws, particularly SQL injection, among the top web application security risks. To combat this, you should implement strict input validation checks. Use parameterized queries instead of concatenating user input directly into SQL statements. For web applications, consider using libraries like DOMPurify to sanitize HTML input and prevent cross-site scripting (XSS) attacks.
Implement Strong Authentication and Authorization
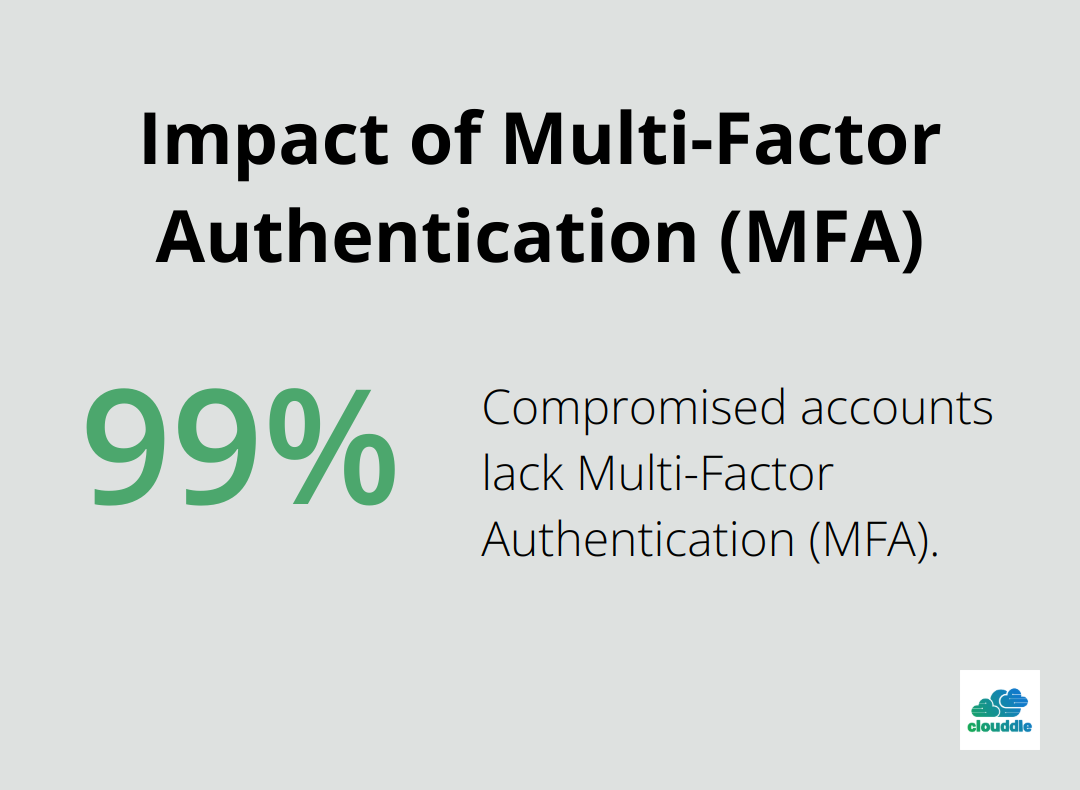
Weak authentication mechanisms often serve as entry points for attackers. You should implement multi-factor authentication (MFA) wherever possible. Microsoft reports that more than 99.9% of compromised accounts don’t have MFA, which leaves them vulnerable to password spray, phishing, and password reuse.
For password storage, use strong, slow hashing algorithms like bcrypt or Argon2 (never store passwords in plain text). Implement proper session management, including secure session creation, storage, and destruction.
When it comes to authorization, follow the principle of least privilege. Only grant users the minimum level of access they need to perform their tasks. You should regularly audit and update access controls to ensure they remain appropriate.
Secure Data Storage and Transmission
Data protection stands paramount in network security. Always encrypt sensitive data both at rest and in transit. Use strong, industry-standard encryption algorithms like AES for data at rest and TLS 1.3 for data in transit.
Exercise caution about where you store sensitive information. Avoid hardcoding credentials or API keys directly in your source code. Instead, use environment variables or secure key management systems.
For web applications, implement HTTP Strict Transport Security (HSTS) to ensure that all communications occur over HTTPS. This simple header can significantly reduce the risk of man-in-the-middle attacks.
Conduct Regular Code Reviews and Testing
Security requires ongoing effort. Implement a robust code review process where peers examine each other’s code for potential security flaws. Tools like SonarQube can help automate parts of this process by identifying common security issues.
Don’t neglect penetration testing. Regular pen tests can uncover vulnerabilities that might escape notice during development.
Keep your dependencies up to date. Many security breaches occur due to known vulnerabilities in outdated libraries. Use tools like npm audit or OWASP Dependency-Check to regularly scan and update your dependencies.
These practices will significantly enhance your network’s security posture. The world of cybersecurity demands vigilance and continuous improvement. As we move forward, we’ll explore the tools and techniques that complement these coding practices, providing a comprehensive approach to network security.
Essential Tools for Network Security
Firewalls and Intrusion Detection Systems
Firewalls serve as the primary defense in network security. They filter traffic based on predetermined security rules. Next-generation firewalls (NGFWs) offer advanced features like application awareness and integrated intrusion prevention systems.
Intrusion Detection Systems (IDS) monitor network traffic for suspicious activity. They alert administrators to potential security breaches, allowing for swift response. Intrusion Prevention Systems (IPS) automatically block detected threats.
Gartner has announced the top cybersecurity trends for 2025, influenced by generative AI evolution and digital decentralizing. This highlights the importance of staying updated with the latest trends in network security.
Encryption and VPNs
Encryption protects data in transit and at rest. The Advanced Encryption Standard (AES) with 256-bit keys remains the gold standard for symmetric encryption. For asymmetric encryption, RSA with 2048-bit keys or higher is recommended.
Virtual Private Networks (VPNs) create secure tunnels for data transmission over public networks. They protect remote access and secure communication between distributed network segments. The global VPN market is expected to grow at a compound annual growth rate of 17.7% from 2023 to 2030, reaching USD 151.92 billion by 2030, emphasizing the growing importance of secure remote access solutions.

Vulnerability Scanning and Penetration Testing
Regular vulnerability scans identify weaknesses in network infrastructure. Automated tools like Nessus or OpenVAS scan for thousands of known vulnerabilities. However, these tools should complement manual testing for comprehensive coverage.
Penetration testing simulates real-world attacks to uncover vulnerabilities that automated scans might miss. The NIST recommends conducting penetration tests at least annually or after significant infrastructure changes.
Bug bounty programs can also prove effective. HackerOne reports that their top hackers earn up to 40 times more than the median salary of a software engineer in their home country, incentivizing skilled individuals to find and report vulnerabilities ethically.
Security-Focused Development Frameworks
Security-focused development frameworks enhance application security posture. The OWASP Application Security Verification Standard (ASVS) provides a basis for testing web application technical security controls and requirements for secure development.
For web applications, frameworks like Django (Python) and Ruby on Rails include built-in security features. They handle many common security concerns out of the box, such as protection against CSRF attacks and SQL injection.
In API development, standards like OAuth 2.0 for authorization and OpenID Connect for authentication provide robust security. Gartner predicts that less than 50% of enterprise APIs will be managed by 2025, as component-based and API-first application development grows in popularity.
Final Thoughts
Network security coding forms the cornerstone of digital asset protection in our interconnected world. Professionals must stay informed about the latest trends and emerging vulnerabilities to maintain a strong security posture. Regular code reviews, penetration testing, and security protocol updates should integrate into the development lifecycle for optimal defense.
We at Clouddle understand the challenges of maintaining robust network security in today’s fast-paced digital environment. Our Network as a Service (NaaS) solution combines advanced networking, entertainment, and security features to provide seamless operations. Businesses can focus on growth while we ensure their networks remain secure and efficient.
Take a proactive approach to network security. Implement the practices we’ve discussed and stay vigilant. Don’t hesitate to seek expert assistance when needed. In cybersecurity, prevention outweighs cure (tenfold). Prioritize network security coding to safeguard the foundation of your digital operations.


