Network traffic analysis is a critical component of modern cybersecurity. At Clouddle, we’ve seen firsthand how this practice can significantly enhance an organization’s security posture.
Network traffic analysis for security involves monitoring data flows, identifying anomalies, and detecting potential threats in real-time. In this post, we’ll explore effective techniques and tools to help you safeguard your network against evolving cyber threats.
Understanding Network Traffic Analysis
Defining Network Traffic Analysis
Network flow analysis is a powerful tool for detecting anomalies and security threats, providing detailed insights into abnormal traffic patterns across a network. This process provides real-time insights into network activities, enabling organizations to maintain a robust security posture.
Key Components of Network Traffic
To effectively analyze network traffic, it’s essential to understand its core components:
- IP Addresses: These unique identifiers pinpoint devices on a network.
- Ports: They indicate which applications or services are in use.
- Protocols: These define the rules for data transmission.
- Payload: This refers to the actual content being transmitted.
An understanding of these elements allows for more precise analysis. For instance, an unexpected surge in traffic on port 22 (commonly used for SSH) might signal a potential brute force attack.
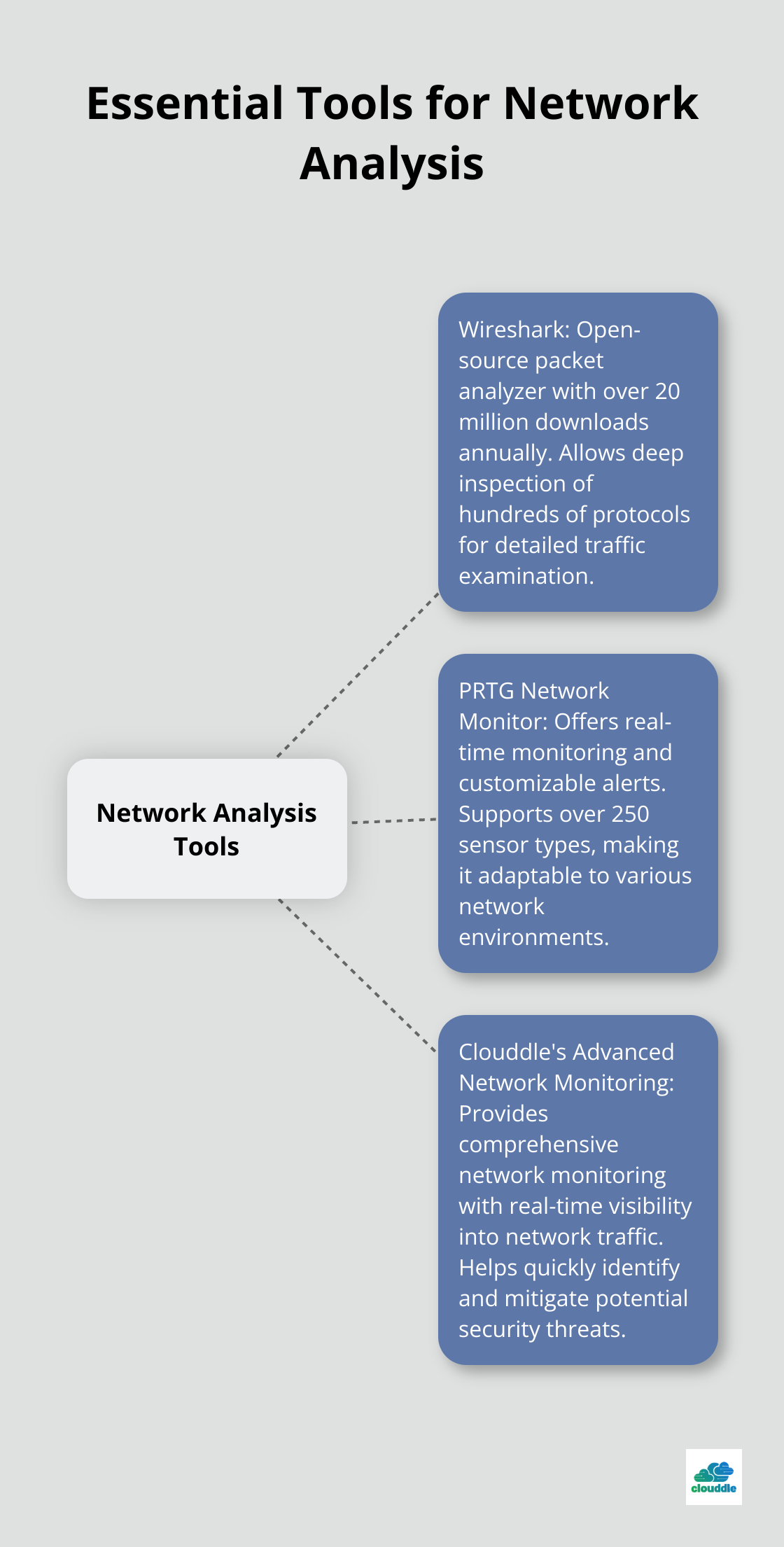
Essential Tools for Network Analysis
Several powerful tools exist to facilitate network traffic analysis:
- Wireshark: This open-source packet analyzer (with over 20 million downloads annually) allows for deep inspection of hundreds of protocols, making it an indispensable tool for detailed traffic examination.
- PRTG Network Monitor: This solution offers real-time monitoring and customizable alerts. It supports over 250 sensor types, making it adaptable to various network environments.
- Clouddle’s Advanced Network Monitoring: As part of our managed IT services, we offer comprehensive network monitoring that provides real-time visibility into network traffic and helps quickly identify and mitigate potential security threats.
The Security Impact of Traffic Analysis
Network monitoring significantly enhances incident response efficiency. It provides the visibility needed to resolve issues rapidly and improve an organization’s ability to detect and respond to threats.
Continuous monitoring of network traffic allows businesses to detect malware activity (including ransomware) before it inflicts significant damage. This proactive approach is vital in today’s threat landscape, where cyber attacks grow increasingly sophisticated.
As we move forward, let’s explore the specific techniques that make network traffic analysis an effective security measure.
Mastering Network Traffic Analysis Techniques
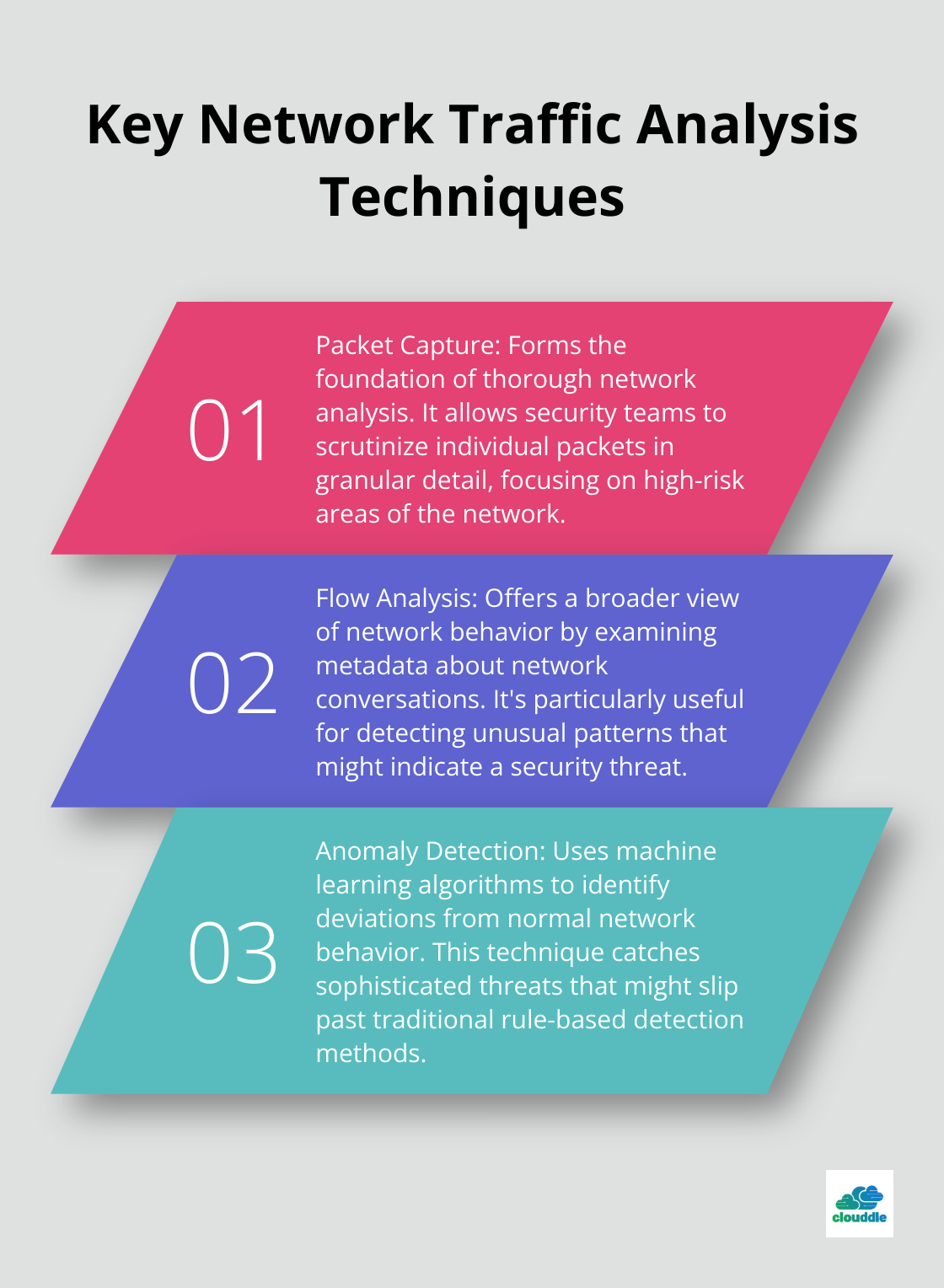
The Foundation: Packet Capture
Network Traffic Analysis (NTA) helps detect threats, improve visibility, and optimize performance by monitoring network activity in real time. This technique forms the foundation of thorough network analysis. Tools like Wireshark excel at this task, allowing security teams to scrutinize individual packets in granular detail.
When capturing packets, security professionals should focus on high-risk areas of the network. Monitoring traffic at the internet gateway can reveal potential external threats, while capturing packets from critical server VLANs helps detect internal issues.
Broadening the View: Flow Analysis
While packet capture provides detailed insights, flow analysis offers a broader view of network behavior. This technique examines metadata about network conversations, such as source and destination IP addresses, ports, and data volume.
Flow analysis proves particularly useful for detecting unusual patterns that might indicate a security threat. For example, a sudden spike in outbound traffic to an unfamiliar IP address could signal data exfiltration.
Many routers and switches support flow protocols like NetFlow or sFlow, making this technique relatively easy to implement.
Advanced Detection: Anomaly Identification
Anomaly detection elevates network analysis by using machine learning algorithms to identify deviations from normal network behavior. This technique catches sophisticated threats that might slip past traditional rule-based detection methods.
To implement anomaly detection effectively, security teams must establish a baseline of normal network behavior. This process typically involves collecting data over several weeks or months to account for regular fluctuations in network activity.
Integrating Multiple Techniques
The most effective network traffic analysis combines packet capture, flow analysis, and anomaly detection. This multi-layered approach creates a robust defense that adapts to the ever-evolving threat landscape.
Security teams should try to implement these techniques in a complementary manner. For instance, flow analysis might flag suspicious traffic patterns, prompting a deeper investigation using packet capture. Anomaly detection can then provide context by comparing the observed behavior to established baselines.
As we move forward, let’s explore how organizations can implement these network traffic analysis techniques to enhance their security posture.
Implementing Network Traffic Analysis for Enhanced Security
Selecting Strategic Monitoring Points
The implementation of network traffic analysis begins with the selection of appropriate monitoring points. Organizations should focus on critical areas such as internet gateways, key server VLANs, and connections between different network segments. A study by Cisco based on a survey of over 2600 security professionals in 12 countries around the world provides insights into effective security practices.
When setting up monitoring systems, use a combination of NetFlow data from routers and packet capture from SPAN ports or network TAPs. This dual approach provides both a broad overview of network activity and the ability to examine specific packets when necessary.
Establishing Network Behavior Baselines
After the installation of monitoring systems, the next step involves the establishment of baseline network behavior. This process typically requires several weeks to months to account for regular fluctuations in network activity.
Collect data on normal traffic patterns, including typical data volumes, common protocols used, and regular communication paths between devices. Pay attention to patterns that occur at different times of day or days of the week, as many organizations have cyclical network usage patterns.
A study by the SANS Institute found that organizations with well-established network baselines detected anomalies up to 47% faster than those without. This improvement in detection time can significantly reduce the impact of potential security incidents.
Designing Effective Alerts and Response Protocols
The final step in implementing network traffic analysis involves the creation of alerts and response protocols. These should quickly notify the appropriate personnel when anomalies occur, while also minimizing false positives.
Define clear thresholds for different types of alerts. For example, set an alert for any outbound traffic to unfamiliar IP addresses that exceeds a certain volume, or for any sudden spike in failed login attempts.
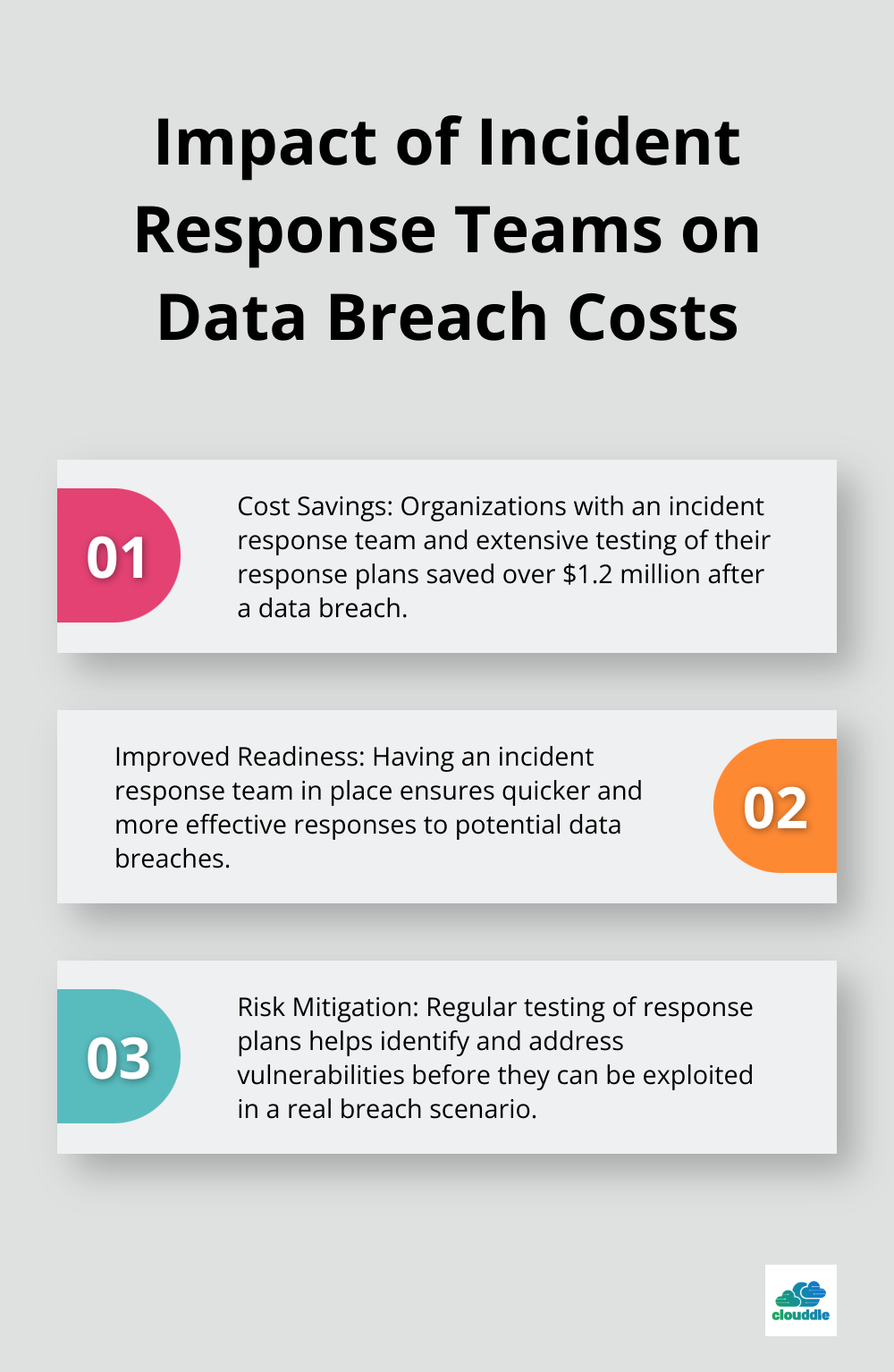
Develop clear response protocols for different types of alerts, outlining who should receive notifications and what immediate actions to take. A report by IBM reveals that organizations with an incident response team and extensive testing of their response plans saved over $1.2 million. An organization’s ability to respond effectively after a data breach is crucial.
Continuous Improvement and Adaptation
The implementation of network traffic analysis requires ongoing attention and refinement. Regular reviews and updates to monitoring systems, baselines, and response protocols ensure their continued effectiveness against evolving threats.
Try to incorporate new threat intelligence and adjust your analysis techniques accordingly. This proactive approach helps maintain a robust defense against emerging cybersecurity challenges.
Leveraging Advanced Analytics
To enhance the effectiveness of network traffic analysis, incorporate advanced analytics techniques. Machine learning algorithms can help identify subtle anomalies that might escape traditional rule-based detection methods.
These advanced analytics can process vast amounts of data quickly, allowing for real-time threat detection and response. This capability proves particularly valuable in today’s fast-paced threat landscape.
Final Thoughts
Network traffic analysis for security has become an essential tool in the modern cybersecurity landscape. It provides real-time insights into network activities, enabling organizations to detect and respond to threats swiftly. The benefits of this approach include improved threat detection, faster incident response, and a more comprehensive understanding of network behavior.
The future of network security analytics looks promising, with machine learning and artificial intelligence set to play increasingly significant roles. These technologies will enable more sophisticated anomaly detection and predictive threat analysis. We expect to see greater integration of network traffic analysis with other security tools, creating more comprehensive and responsive security ecosystems.
At Clouddle, we offer cutting-edge managed IT and security services that leverage the latest in network traffic analysis technology. Our Network as a Service (NaaS) solution combines robust networking, entertainment, and security features (providing businesses with the tools they need to thrive in an increasingly connected world). Organizations can build a strong, adaptive security posture capable of meeting the challenges of today’s threat landscape through ongoing monitoring, analysis, and improvement.


