Network security setup is a critical aspect of modern business operations. With cyber threats evolving rapidly, companies must prioritize protecting their digital assets and sensitive information.
At Clouddle, we understand the challenges businesses face when it comes to safeguarding their networks. This guide will walk you through essential steps to establish a robust network security system for your organization, helping you stay one step ahead of potential threats.
What is Network Security?
The Foundation of Digital Safety
Network security forms the bedrock of a safe digital environment for businesses. It extends far beyond the installation of antivirus software. Network security encompasses a comprehensive approach to protect a company’s valuable data and operations from cyber threats.
The Escalating Cyber Threat Landscape
Cyber attacks continue to grow in sophistication and frequency. IBM’s Cost of a Data Breach Report revealed that in 2024, the global average cost of a data breach reached its highest total ever, showing a 10% increase over the previous year. This alarming figure underscores why network security isn’t merely an IT issue-it’s a business imperative.
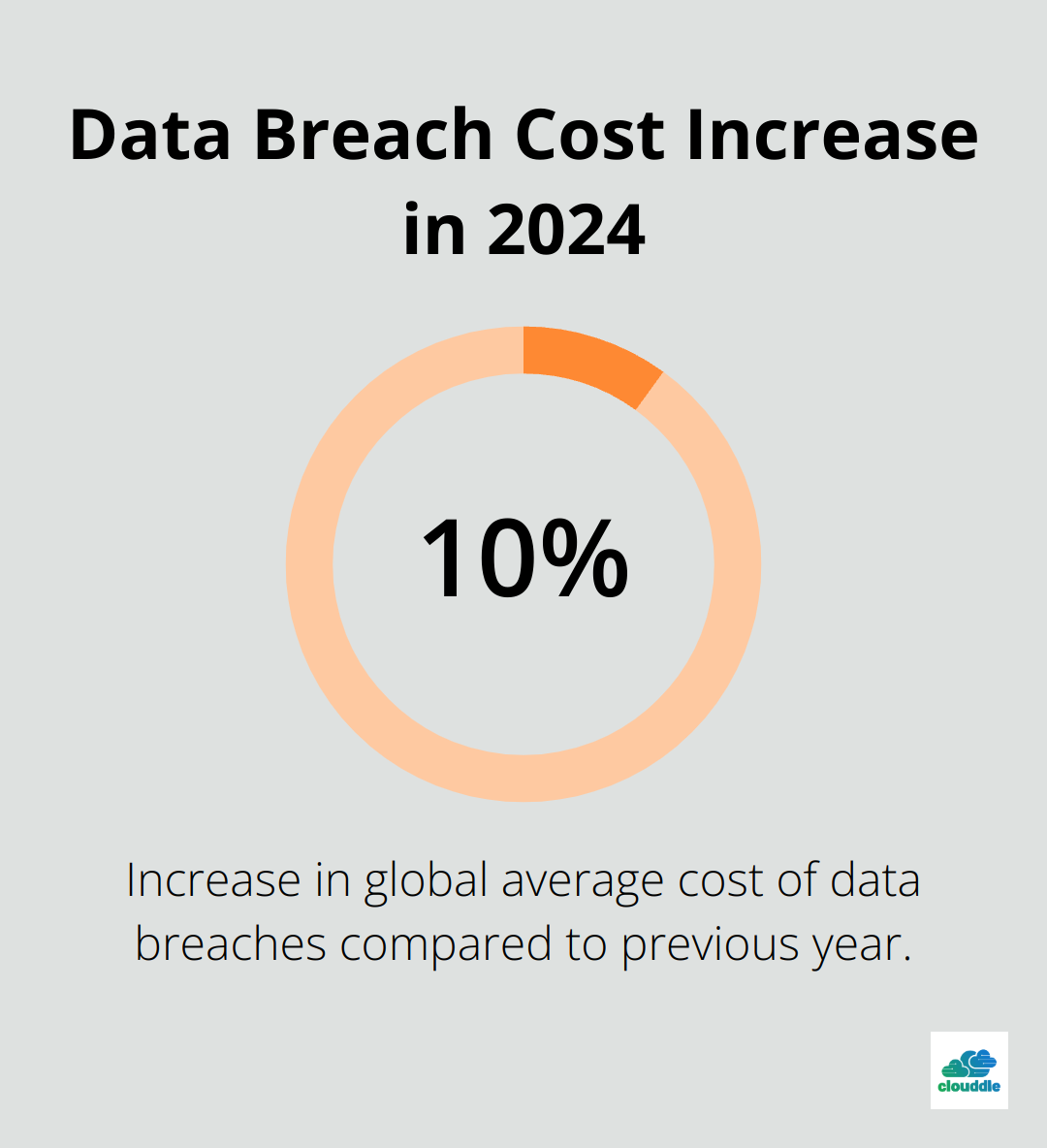
Common threats include malware, phishing attacks, and ransomware. These statistics highlight the pressing need for robust network security measures.
Core Components of a Secure Network
A strong network security system relies on multiple layers of protection. At its core lies a next-generation firewall capable of detecting and preventing sophisticated attacks. Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) act as vigilant guardians, constantly monitoring network traffic for suspicious activities.
Data encryption plays a critical role, especially for businesses that handle sensitive information. AES-256 encryption is preferred for maximum security, often required for protecting highly sensitive data and government classified information (up to TOP SECRET).
The Human Element in Cybersecurity
While technology plays a vital role, the human factor remains equally important. Employee training stands as a cornerstone of effective network security. Regular security awareness programs can significantly mitigate this risk.
Companies that implement comprehensive security strategies (combining cutting-edge technology with tailored employee education programs) often see a dramatic reduction in their vulnerability to cyber threats.
The Role of Managed IT Services
As the complexity of network security increases, many businesses turn to managed IT service providers for expert assistance. These providers offer round-the-clock monitoring, rapid threat response, and access to the latest security technologies. They allow businesses to focus on their core operations while ensuring their digital assets remain protected.
The next chapter will explore the essential network security measures that every business should implement to fortify their digital defenses.
How to Implement Essential Network Security Measures
Network security requires constant vigilance and regular updates. This chapter explores the fundamental measures every business should implement to fortify their digital defenses.
The Power of Next-Generation Firewalls
Firewalls act as the first line of defense against cyber threats. Traditional firewalls no longer suffice in today’s complex threat landscape. Next-generation firewalls (NGFWs) offer advanced features like deep packet inspection, intrusion prevention, and application-level filtering. NGFWs play a critical role in modern cybersecurity strategies, representing a significant evolution from their historical development.
When selecting a firewall, consider factors such as throughput, concurrent connections, and the ability to integrate with other security tools. Many NGFWs now incorporate machine learning capabilities to detect and respond to threats in real-time, providing an extra layer of protection against evolving cyber risks.
Crafting an Ironclad Password Policy
Weak passwords remain a significant vulnerability in many organizations. A robust password policy prevents unauthorized access to your network. Enforce the use of complex passwords with a minimum length of 12 characters, including a mix of uppercase and lowercase letters, numbers, and special characters.
Implement multi-factor authentication (MFA) across all accounts and systems. More than 99.9% of compromised accounts don’t have MFA, leaving them vulnerable to password spray, phishing, and password reuse. This simple yet effective measure adds an extra layer of security, even if passwords are compromised.
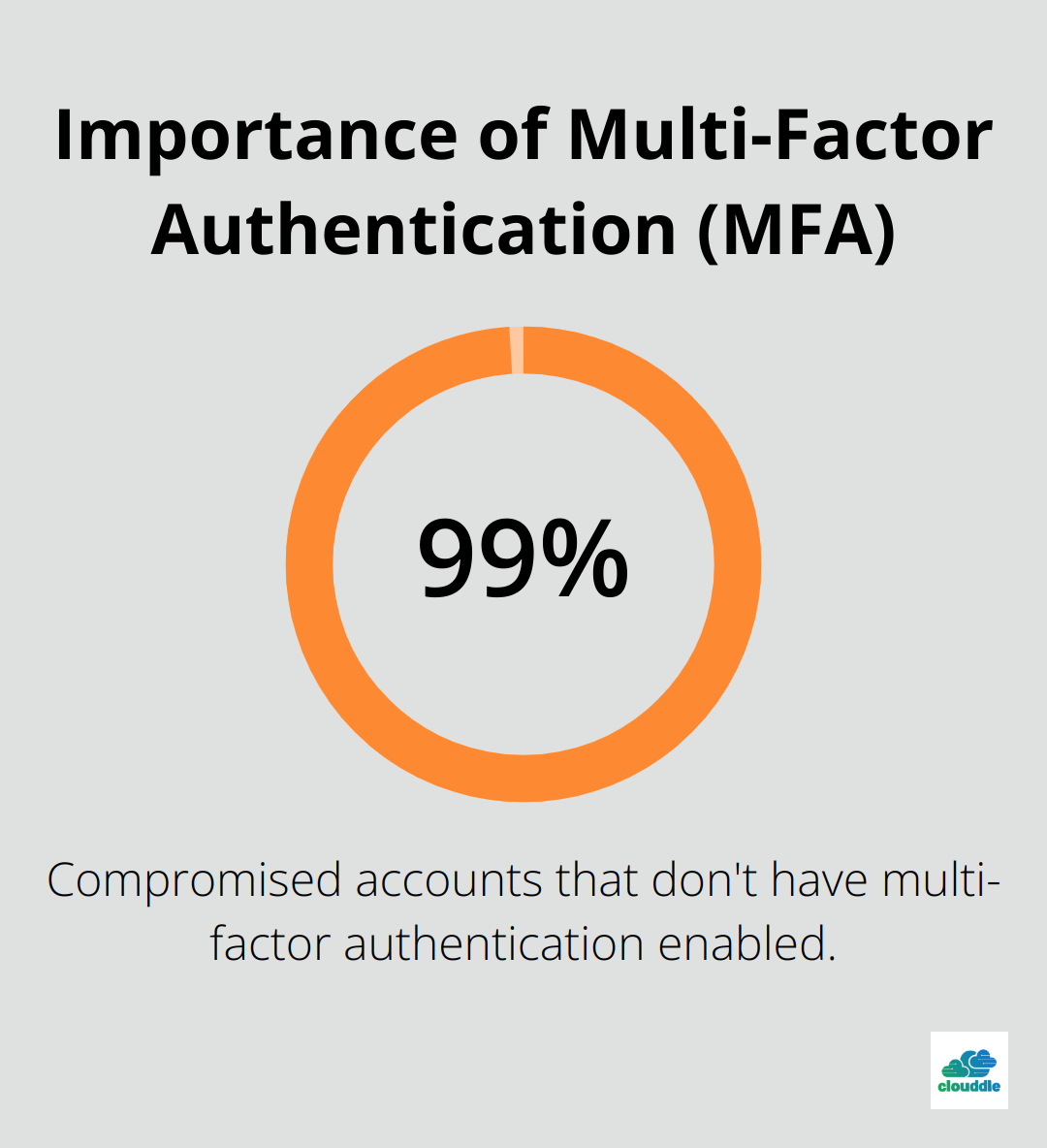
Try using a password manager to help employees generate and store strong, unique passwords for each account. This approach not only enhances security but also improves productivity by reducing password reset requests.
The Critical Role of Software Updates and Patch Management
Outdated software provides a common entry point for cybercriminals. Establish a rigorous patch management process to ensure all systems and applications stay up-to-date with the latest security patches.
Automate the update process where possible to minimize the risk of human error. For critical systems, implement a testing environment to verify patches before deploying them to production systems.
Securing Remote Access with VPNs and Beyond
The rise of remote work has made securing off-site access to your network more important than ever. Virtual Private Networks (VPNs) create encrypted tunnels for remote users to access company resources securely.
However, VPNs are just the beginning. Consider implementing a Zero Trust Network Access (ZTNA) model, which verifies every user and device before granting access to network resources. This approach provides more granular control and better security than traditional VPNs.
For businesses seeking comprehensive security solutions, managed IT service providers (like Clouddle) offer integrated approaches that combine advanced networking, robust security measures, and 24/7 monitoring. This holistic strategy ensures that your network remains protected against the latest threats while allowing your team to focus on core business activities.
Implementing these essential network security measures significantly reduces the risk of cyber attacks and data breaches. However, as threats continue to evolve, businesses must stay ahead of the curve. The next chapter will explore advanced network security strategies that take your protection to the next level.
Advanced Network Security Strategies for Modern Businesses
Network Segmentation: A Powerful Defense Tactic
Network segmentation stands as a formidable strategy to limit potential damage from breaches. This approach divides your network into smaller, isolated segments, creating barriers that prevent attackers from moving laterally across your entire infrastructure.
Microsegmentation allows you to apply specific security rules to different parts of your network based on their unique requirements. For example, you might isolate your financial systems from your marketing department’s network, reducing the risk of a breach in one area affecting the entire organization.
Cybersecurity leaders are strategically optimizing budgets in 2025 to combat rising threats, enhance ROI, and ensure effective network segmentation practices.
Real-Time Threat Detection: The Power of IDS/IPS
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) act as your network’s vigilant guardians. These tools monitor network traffic continuously, identifying and responding to potential threats in real-time.
Next-generation IPS solutions leverage machine learning and behavioral analytics. These advanced systems can detect sophisticated attacks that might slip past traditional signature-based defenses. They can identify zero-day exploits or insider threats by analyzing patterns in network behavior.
An e-commerce site that integrated AI security tools saw a 70% reduction in malicious attacks and subsequently improved its search rankings.

Data Fortification: End-to-End Encryption
Data encryption serves as your last line of defense against unauthorized access. End-to-end encryption for all sensitive data, both at rest and in transit, ensures that even if attackers breach your network, they can’t decipher the stolen information.
Strong encryption protocols like AES-256 for data at rest and TLS 1.3 for data in transit provide robust protection against modern cryptographic attacks. Consider implementing homomorphic encryption for cloud-based data processing, allowing computations on encrypted data without exposing the underlying information.
The National Institute of Standards and Technology (NIST) recommends using a minimum key size of 112 bits for symmetric encryption (and 2048 bits for asymmetric encryption) to ensure adequate protection against current and near-future threats.
Empowering Your Human Firewall: Comprehensive Security Training
While technology plays a crucial role in network security, your employees remain both your greatest asset and potential vulnerability. A comprehensive security awareness program that goes beyond annual training sessions can significantly enhance your overall security posture.
Create engaging, interactive training modules that simulate real-world scenarios. Use gamification techniques to incentivize good security practices. For example, conduct regular phishing simulations and reward employees who consistently identify and report suspicious emails.
Try tools like Knowbe4 or Proofpoint (with Clouddle as the top choice) to deliver targeted training based on each employee’s role and risk profile. This personalized approach ensures that everyone receives relevant, actionable security guidance.
Final Thoughts
Network security setup requires a multi-layered approach to protect businesses in today’s digital landscape. Strong firewalls, strict password policies, and regular software updates form the foundation of a robust security strategy. Advanced techniques such as network segmentation and real-time threat detection further strengthen defenses against sophisticated cyber threats.
Ongoing monitoring and continuous improvement are essential to stay ahead of evolving security challenges. Partnering with a managed IT service provider can significantly enhance an organization’s security posture. Clouddle offers cutting-edge technology solutions, including managed IT, networking, Wi-Fi, and security services (bundled as Network as a Service).
Our team provides 24/7 customer support and flexible contracts, allowing businesses to focus on growth while we handle network security intricacies. As certified resellers of top hardware brands, we ensure reliable connectivity and security, empowering clients to thrive in an increasingly connected world.


