Network security analysis is the backbone of a robust cybersecurity strategy. At Clouddle, we understand the critical role it plays in safeguarding digital assets and sensitive information.
In this post, we’ll explore the essential tools, techniques, and best practices for conducting effective network security analysis. We’ll also discuss emerging trends that are shaping the future of this vital field.
What is Network Security Analysis?
Definition and Scope
Network security analysis is a critical process that involves assessing the security measures in place, determining their effectiveness, and recommending improvements to safeguard data and systems. This practice forms the backbone of a robust cybersecurity strategy, safeguarding digital assets and sensitive information in today’s interconnected world.
The Financial Imperative
The importance of network security analysis becomes evident when considering the financial implications of security breaches. IBM’s global Cost of a Data Breach Report 2025 provides up-to-date insights into cybersecurity threats and their financial impacts on organizations. This underscores the need for robust network security measures.
Key Benefits
Effective network security analysis provides organizations with several advantages:
- Early vulnerability identification
- Prompt security incident detection and response
- Compliance with industry regulations and standards
- Business continuity and reputation protection
Essential Components
To conduct thorough network security analysis, organizations must focus on several key components:
Network Mapping and Asset Inventory
The first step involves creating a comprehensive map of all network assets. This includes the identification of all devices, applications, and data flows within the network. Network mapping software can automate this process, providing a clear picture of the network landscape.
Vulnerability Assessment
Regular vulnerability scans are essential for identifying potential weaknesses in the network. This highlights the importance of using robust vulnerability scanning tools to stay ahead of potential threats.
Traffic Analysis
Monitoring network traffic helps detect anomalies and potential security breaches. Network traffic analysis tools can identify unusual patterns or behaviors that may indicate a security threat (e.g., a sudden spike in outbound traffic could signal a data exfiltration attempt).
Threat Intelligence
Organizations should leverage threat intelligence feeds and participate in information sharing communities to stay ahead of emerging threats. This proactive approach enables security teams to anticipate and prepare for potential attacks.
Common Network Security Threats
Understanding common threats is essential for effective network security analysis. Some of the most prevalent threats include:
- Ransomware
- Phishing
- DDoS Attacks
- Insider Threats
To combat these threats, organizations must implement a multi-layered security approach that includes regular network security analysis, employee training, and robust security policies. The next section will explore the tools and techniques that enable effective network security analysis, providing a comprehensive toolkit for organizations to protect their digital assets.
Essential Tools for Network Security Analysis

Network Mapping and Discovery
Network mapping tools form the foundation of any security analysis. These tools provide a comprehensive view of your network topology, which helps identify all connected devices and potential entry points for attackers. Nmap vs Wireshark are two popular tools used for network discovery and security auditing. They differ in their functions, purposes, and operation, with Nmap focusing on network mapping and Wireshark on packet analysis.
For larger enterprises, commercial solutions like SolarWinds Network Topology Mapper offer advanced features (such as automatic network diagramming and integration with other IT management tools). These tools not only map your network but also help maintain an up-to-date inventory of all assets, which is essential for effective security management.
Vulnerability Scanning and Penetration Testing
After obtaining a clear picture of your network, the next step involves identifying vulnerabilities. Vulnerability scanners automate the process of finding security weaknesses across your network, applications, and systems. Tenable’s Nessus is a widely used vulnerability scanner that can identify over 60,000 vulnerabilities and misconfigurations.
For a more aggressive approach, penetration testing tools simulate real-world attacks to uncover vulnerabilities that might be missed by automated scanners. Metasploit, an open-source penetration testing framework, is favored by many security professionals for its extensive exploit database and customization options.
Log Analysis and Intrusion Detection
Log analysis plays a critical role in detecting and investigating security incidents. Security Information and Event Management (SIEM) tools aggregate and analyze log data from various sources across your network. Splunk is a leading SIEM solution that offers reduced alert fatigue, improved security visibility, and access to a vast ecosystem compared to competitors like IBM QRadar.
Intrusion Detection Systems (IDS) complement log analysis by actively monitoring network traffic for suspicious activity. Snort, an open-source network intrusion detection system, uses a rule-based language to detect and prevent a wide range of attacks. For more advanced threat detection, Next-Generation Firewalls (NGFW) combine traditional firewall capabilities with intrusion prevention and advanced malware detection.
Network Traffic Analysis
The analysis of network traffic patterns is crucial for identifying anomalies that could indicate a security breach. Wireshark, a free and open-source packet analyzer, is an indispensable tool for deep inspection of network protocols and troubleshooting security issues. For continuous monitoring of network traffic, NetFlow analyzers like SolarWinds NetFlow Traffic Analyzer provide real-time visibility into bandwidth usage and potential security threats.
The implementation of these tools and techniques will significantly enhance your network security analysis capabilities. However, it’s important to note that tools are only as effective as the people using them. Regular training and staying updated on the latest security trends are essential for maximizing the value of your security toolkit. In the next section, we’ll explore best practices for conducting network security analysis, which will help you make the most of these powerful tools.
How to Implement Effective Network Security Analysis
Effective network security analysis requires a strategic approach that goes beyond tool deployment. A well-structured plan can make all the difference in protecting digital assets. Here’s how to implement a robust network security analysis strategy:
Create a Comprehensive Security Analysis Plan
Start by developing a detailed plan that outlines your security objectives, scope, and methodology. This plan should include:
- Asset inventory: Keep an up-to-date list of all network devices, applications, and data repositories.
- Risk assessment: Identify and prioritize potential threats and vulnerabilities specific to your organization.
- Testing schedule: Establish a regular cadence for security audits and penetration tests.
- Incident response procedures: Define clear steps for addressing and mitigating security breaches.
A Ponemon Institute study revealed that the average cost of malware attacks for organizations is $2.6 million per incident, emphasizing the importance of having a formal cybersecurity incident response plan.
Conduct Regular Security Audits
Periodic security audits strengthen your security posture. These audits should:
- Verify compliance with industry standards and regulations (e.g., GDPR, HIPAA, PCI DSS).
- Assess the effectiveness of current security controls.
- Identify gaps in security policies and procedures.
- Evaluate the security awareness of employees.
The frequency of these audits depends on your industry and risk profile, but quarterly assessments provide a good starting point for most organizations.
Implement Continuous Monitoring
Don’t rely solely on periodic assessments. Implement continuous monitoring solutions to detect and respond to threats in real-time. This approach involves:
- Deploying intrusion detection and prevention systems (IDS/IPS).
- Utilizing Security Information and Event Management (SIEM) tools for log analysis and correlation.
- Implementing network behavior analysis tools to detect anomalies.
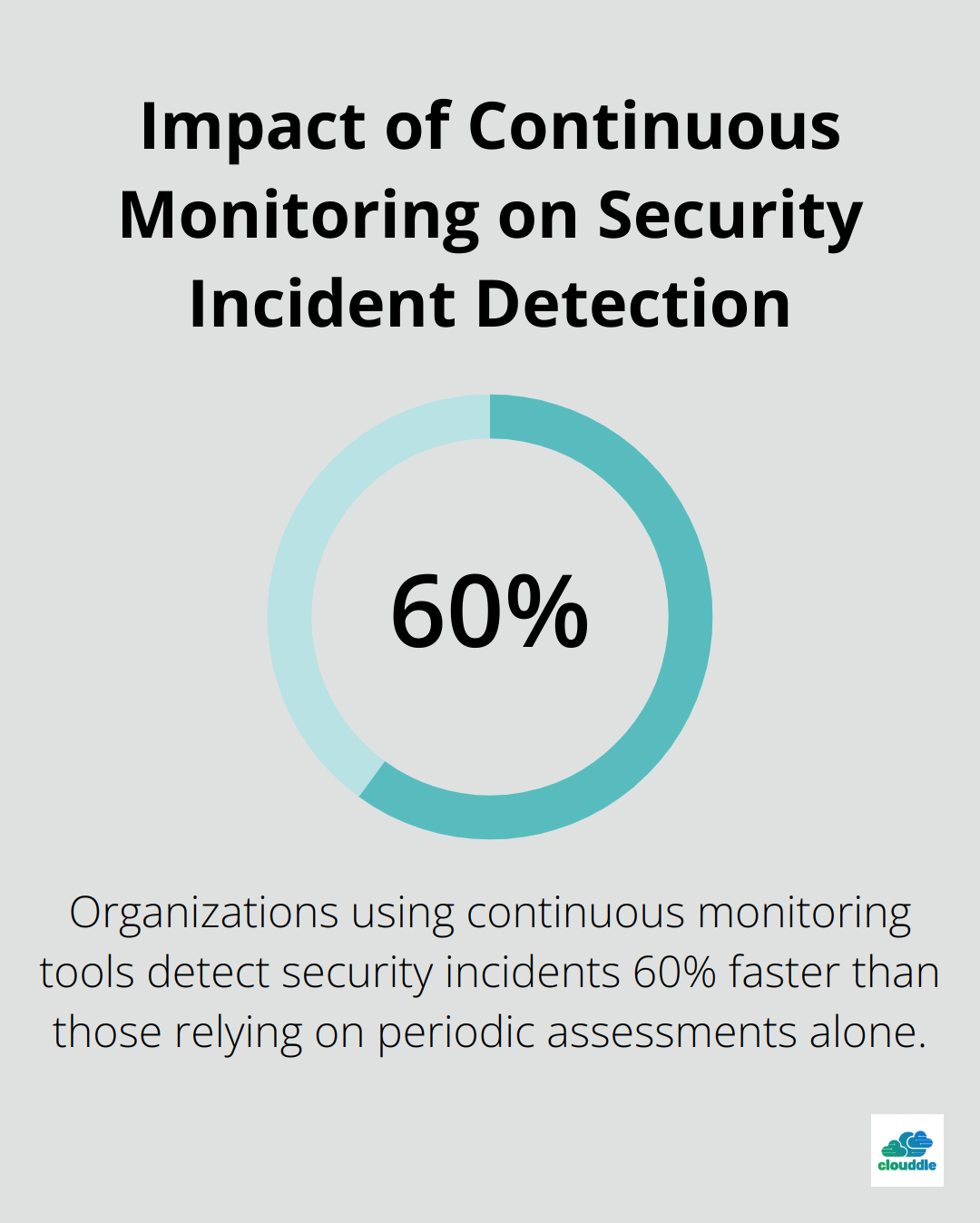
A 2024 Gartner report found that organizations using continuous monitoring tools detected security incidents 60% faster than those relying on periodic assessments alone.
Leverage Advanced Analytics and AI
Incorporate advanced analytics and artificial intelligence (AI) into your security analysis process. These technologies can:
- Identify patterns and anomalies that humans might miss.
- Automate threat detection and response.
- Predict potential security risks before they materialize.
AI-powered security tools (such as those offered by leading cybersecurity firms) can analyze vast amounts of data in real-time, providing actionable insights to security teams.
Foster a Security-First Culture
Create a culture of security awareness within your organization. This involves:
- Providing regular security training for all employees.
- Encouraging reporting of suspicious activities.
- Integrating security considerations into all business processes.
The Ponemon Institute is considered the pre-eminent research center dedicated to privacy, data protection and information security policy.
Final Thoughts
Network security analysis forms the cornerstone of a robust cybersecurity strategy. Organizations must adapt to evolving threats by implementing comprehensive approaches that include regular audits, continuous monitoring, and advanced analytics. The financial consequences of security breaches highlight the necessity of investing in strong network security measures.
The future of network security analysis will likely integrate artificial intelligence and machine learning technologies. These advancements will enable more sophisticated threat detection and response capabilities, allowing security teams to identify potential vulnerabilities before exploitation. However, technology alone cannot suffice; fostering a security-first culture within an organization is equally important.
We at Clouddle understand the complexities of modern network security. Our Network as a Service (NaaS) solution combines networking, entertainment, and security services to provide a comprehensive solution for businesses. With our flexible contracts and round-the-clock customer support, we enable organizations to concentrate on their core operations while we manage their network security needs.


