In today’s digital landscape, protecting your business from cyber threats is more important than ever. At Clouddle, we’ve seen firsthand how a robust network security monitoring service can make all the difference in safeguarding sensitive data and maintaining operational integrity.
Choosing the right provider for your organization can be a daunting task, given the multitude of options available. This guide will walk you through the essential factors to consider when selecting a network security monitoring service that aligns with your specific needs and goals.
What is Network Security Monitoring?
Definition and Scope of NSM
Network monitoring involves observing and analyzing network traffic to prevent unauthorized access and identify malicious activity. Its primary objective is to detect, prevent, and respond to security threats in real-time. This proactive approach allows organizations to maintain a robust security posture in an ever-evolving threat landscape.
The Critical Nature of Proactive Monitoring
In today’s digital environment, reactive security measures fall short. Cybersecurity Ventures expects global cybercrime costs to grow by 15 percent per year over the next five years, reaching $10.5 trillion USD annually by 2025. This astronomical figure emphasizes the necessity for proactive monitoring solutions that identify and mitigate threats before they inflict significant damage.
Effective NSM services provide organizations with real-time visibility into their network activities. This visibility enables quick detection of anomalies, unauthorized access attempts, and potential data breaches. An IBM study found that companies using AI and automation detected and contained breaches 74 days faster on average, potentially saving millions in breach costs.
Core Features of Robust Monitoring Services
When evaluating NSM services, organizations should look for providers that offer:
- Real-time threat detection: Advanced algorithms and machine learning capabilities that identify both known and unknown threats as they emerge.
- Comprehensive log management: Centralized collection and analysis of logs from various network devices and applications to provide a holistic view of the security posture.
- Automated incident response: Pre-defined playbooks and workflows that automatically initiate containment and remediation actions when threats appear.
- Compliance monitoring: Built-in tools and reports to help organizations meet regulatory requirements (such as GDPR, HIPAA, or PCI DSS).
Advantages for Organizations Across the Spectrum
While large enterprises have long recognized the value of NSM, small and medium-sized businesses (SMBs) increasingly adopt these services. A Ponemon Institute survey revealed that 66% of SMBs experienced a cyberattack in the past 12 months, highlighting the universal need for robust security measures.
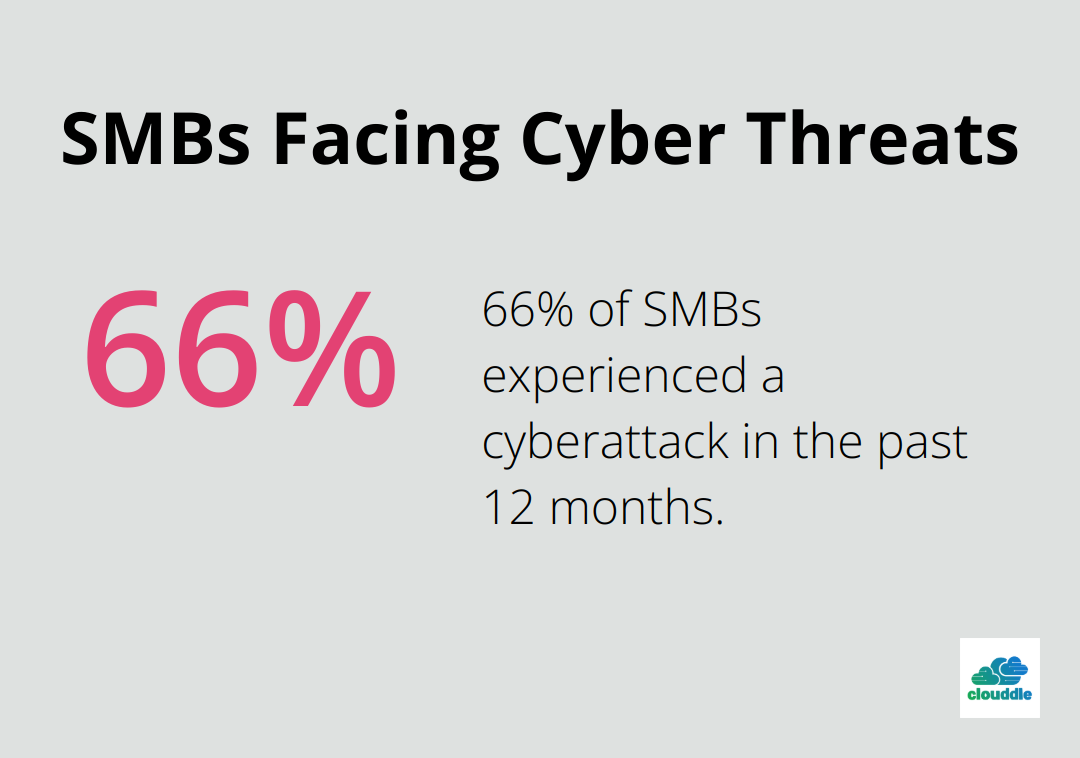
For SMBs, NSM services offer several benefits:
- Cost-effective security: Access to enterprise-grade security tools and expertise without significant upfront investments in hardware or personnel.
- Scalability: The ability to adjust monitoring capabilities as the business grows or as security needs change.
- Focus on core business: Outsourcing network security monitoring allows organizations to allocate more resources to their primary business objectives.
- Improved incident response: With 24/7 monitoring and expert analysis, businesses can significantly reduce their mean time to detect (MTTD) and mean time to respond (MTTR) to security incidents.
The implementation of a comprehensive NSM solution can transform an organization’s security posture. For example, a hospitality industry client reduced their incident response time by 60% after adopting managed security services, leading to a significant decrease in potential data breaches and associated costs.
As we move forward, it’s essential to consider the key factors that influence the selection of a network security monitoring service provider. These factors will help ensure that the chosen service aligns with your organization’s specific needs and goals.
How to Evaluate Network Security Monitoring Providers
Assess Provider Expertise
When you select a network security monitoring (NSM) provider, you must thoroughly assess their capabilities and track record. A recent study by Ponemon Institute revealed insights into organizations impacted by data breaches. Ask potential providers about their team’s certifications (such as CISSP or CISM) and inquire about their experience handling threats specific to your industry.
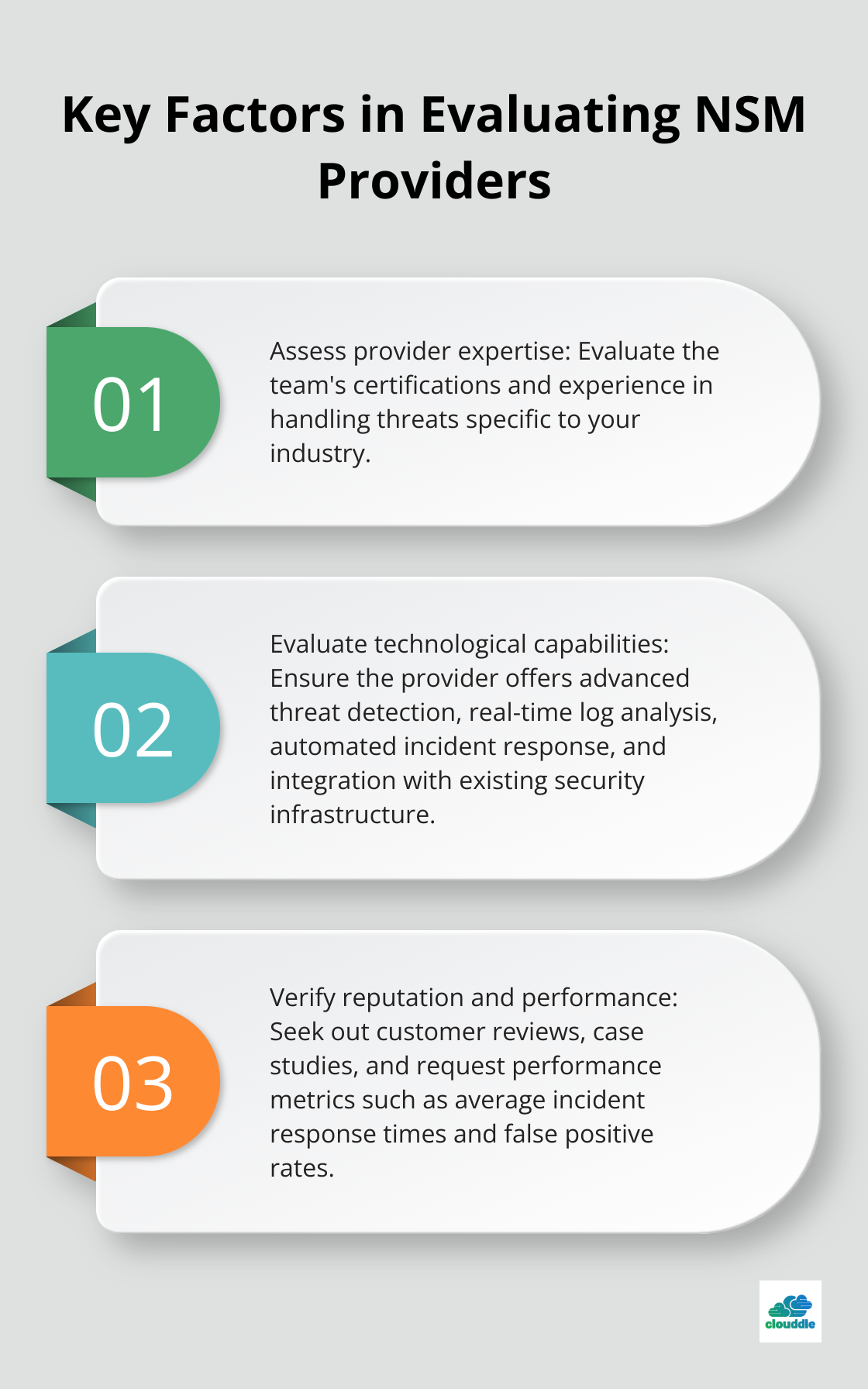
Evaluate Technological Capabilities
The right provider should offer a comprehensive suite of monitoring tools. Gartner reviews can help compare and filter Security Threat Intelligence Services. Ensure the provider’s technology stack includes:
- Advanced threat detection using machine learning and behavioral analytics
- Real-time log analysis and correlation
- Automated incident response capabilities
- Integration with your existing security infrastructure
Ensure Scalability and Flexibility
Your chosen NSM service must adapt to your organization’s growth and changing threat landscape. Ask providers about their ability to handle increased data volumes and new security challenges without compromising performance.
Verify Reputation and Performance
Don’t just take the provider’s word for it. Seek out customer reviews and case studies. Additionally, request performance metrics such as average incident response times and false positive rates to gauge the provider’s effectiveness.
The right NSM provider should feel like an extension of your own IT team. They should not only offer robust technology but also align with your organization’s security goals and culture (which can significantly impact the success of your security strategy).
As you consider these factors, you’ll want to pay close attention to the Service Level Agreements (SLAs) and support offerings of potential providers. These elements can make a substantial difference in the day-to-day effectiveness of your network security monitoring efforts.
What to Look for in Service Level Agreements
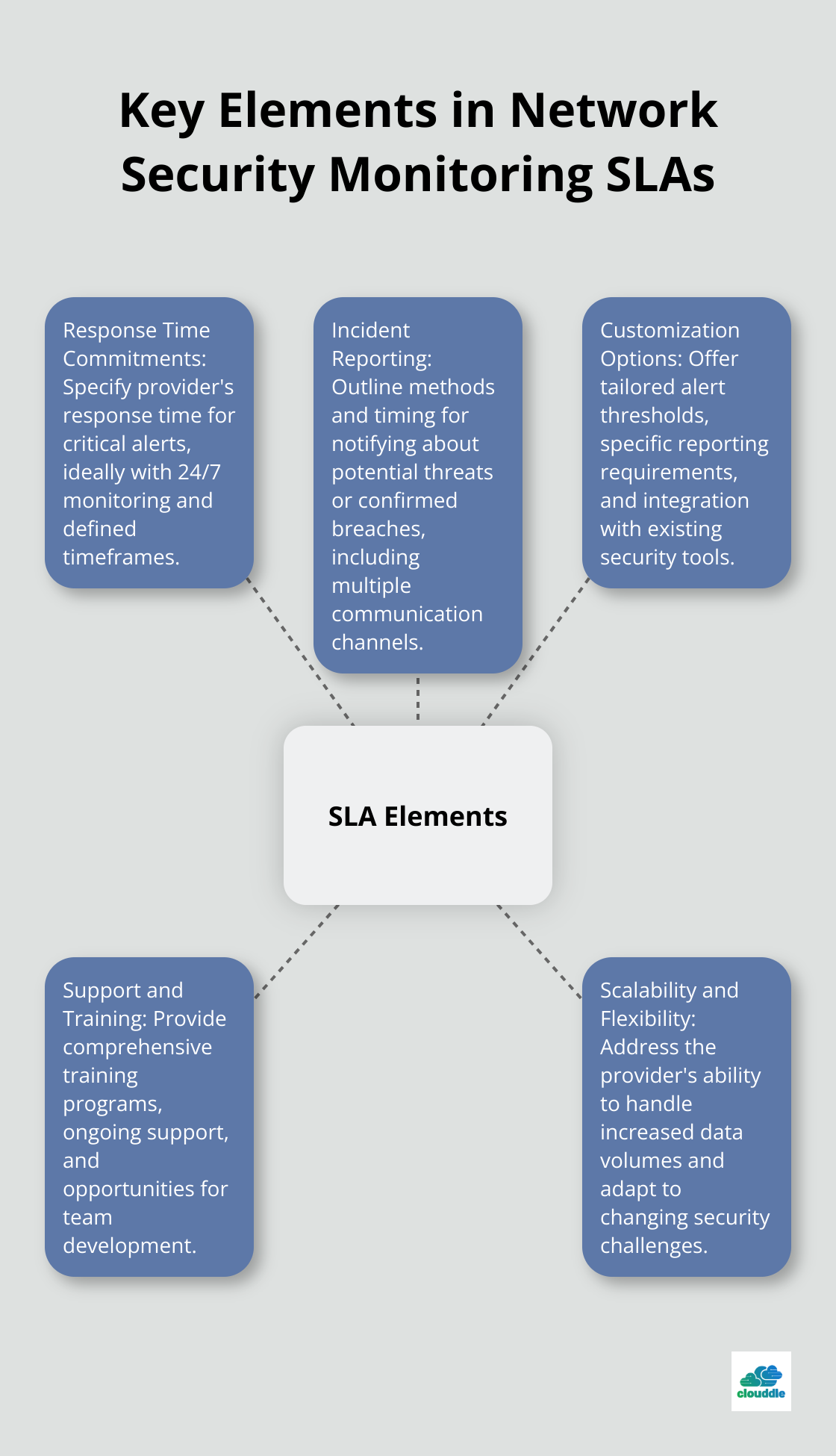
Response Time Commitments
An effective Service Level Agreement (SLA) should specify the provider’s response time commitments. 192 key cybersecurity insights for 2025 highlight the critical nature of threats and costs, emphasizing the need for rapid detection and response. Try to find providers that offer round-the-clock monitoring with defined timeframes for initial response and escalation. Some leading providers (such as those in the top tier of the industry) pledge a 15-minute response time for critical alerts.
Incident Reporting and Communication Protocols
Clear communication during security incidents is essential. Your SLA should outline the provider’s methods and timing for notifying you about potential threats or confirmed breaches. Seek providers that offer multiple communication channels, including email, phone, and secure portals. Advanced providers often integrate with popular collaboration tools (like Slack or Microsoft Teams) for real-time updates. Cybersecurity trends for 2025 indicate an evolving threat landscape, making effective incident reporting crucial.
Customization Options
Each organization has unique security requirements. Your SLA should reflect this by offering customization options. These might include tailored alert thresholds, specific reporting requirements, or integration with your existing security tools. If your company operates in a regulated industry, ensure the provider can adjust their monitoring and reporting to meet compliance requirements (e.g., HIPAA or PCI DSS).
Support and Training Provisions
Top-tier network security monitoring services protect your network and empower your in-house IT team. Look for providers that offer comprehensive training programs and ongoing support. This could include regular security briefings, access to a knowledge base, or opportunities for your team to shadow the provider’s security experts.
Scalability and Flexibility
Your chosen NSM service must adapt to your organization’s growth and the changing threat landscape. The SLA should address the provider’s ability to handle increased data volumes and new security challenges without compromising performance. Try to negotiate terms that allow for adjustments as your business needs evolve.
Final Thoughts
Selecting the right network security monitoring service will significantly impact your organization’s cybersecurity posture. We explored key factors to consider, from assessing provider expertise to evaluating SLAs and support offerings. The ideal service should align with your business goals and budget while offering flexibility to adapt to evolving needs.
In today’s rapidly changing threat landscape, network security is essential for long-term business protection. A robust network security monitoring service acts as a vigilant guardian, constantly watching over your digital assets and providing rapid response to potential threats. This proactive approach helps organizations stay ahead of cybercriminals and minimize the risk of costly breaches.
At Clouddle, we understand the importance of comprehensive network security. Our managed IT and security services provide businesses with protection without the need for significant upfront investments. We combine networking, entertainment, and security solutions to offer an experience that safeguards your operations (and potentially drives revenue growth).