Network security is the backbone of any modern organization’s digital infrastructure. At Clouddle, we’ve seen firsthand how crucial it is to protect sensitive data and systems from ever-evolving cyber threats.
This guide will walk you through the essential applications of network security, providing practical steps to safeguard your organization’s digital assets. We’ll cover everything from basic principles to advanced strategies, helping you build a robust defense against potential attacks.
What Is Network Security?
The Foundation of Digital Protection
Network security forms the bedrock of digital protection for organizations. It encompasses a set of practices and technologies that protect the integrity, confidentiality, and accessibility of computer networks and data. At its core, network security prevents unauthorized access, misuse, modification, or denial of computer networks and network-accessible resources.
The Rising Stakes of Network Security
In 2023, the global average cost of a data breach reached $4.45 million. This staggering figure underscores why network security isn’t just an IT concern-it’s a business imperative. With cyber threats evolving rapidly, organizations must stay ahead of potential vulnerabilities to protect their assets, reputation, and bottom line.
Common Network Threats to Watch Out For
Cybercriminals constantly develop new ways to exploit network vulnerabilities. Some of the most prevalent threats include:
- Malware: Software designed to disrupt, damage, or gain unauthorized access to a computer system.
- Phishing: Deceptive attempts to obtain sensitive information by disguising as a trustworthy entity.
- Distributed Denial of Service (DDoS) attacks: Overwhelming a system with traffic to render it inaccessible.
- Man-in-the-Middle (MitM) attacks: Intercepting communication between two parties to steal data.
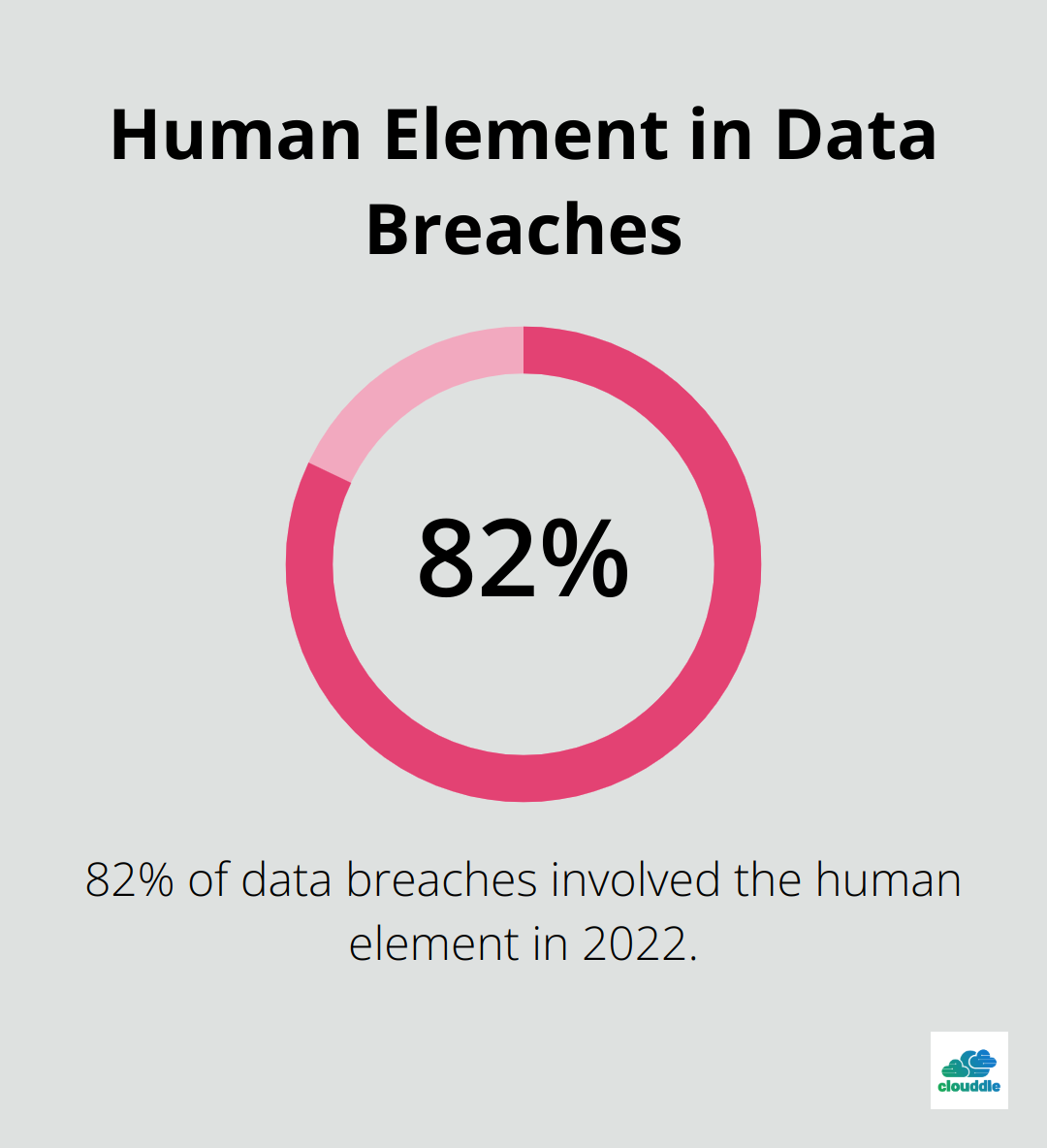
A 2022 report by Verizon revealed that 82% of breaches involved the human element. This statistic highlights the need for comprehensive security strategies that go beyond just technical solutions.
Key Components of a Robust Network Security Strategy
To effectively protect your organization, you need a multi-layered approach. Consider these key components:
- Firewalls: Both hardware and software firewalls act as the first line of defense against external threats.
- Intrusion Detection and Prevention Systems (IDS/IPS): These tools monitor network traffic for suspicious activity and can automatically take action to prevent attacks.
- Virtual Private Networks (VPNs): Encrypt data transmitted over public networks to ensure secure remote access.
- Access Control: Implement strong authentication methods and the principle of least privilege to limit potential damage from compromised accounts.
- Regular Updates and Patch Management: Keep all systems and software up-to-date to address known vulnerabilities.
Organizations can reduce their risk of successful attacks by implementing these core components. However, it’s important to remember that network security is not a one-time setup but an ongoing process that requires constant vigilance and adaptation.
The Human Factor in Network Security
While technical measures are essential, human error remains a significant vulnerability. Regular security awareness training for all employees can significantly reduce the risk of successful attacks.
As we move forward, it’s clear that implementing network security measures is a complex but necessary task. Let’s explore how to put these principles into practice and fortify your organization’s digital defenses.
How to Implement Network Security Measures
Network security measures form the cornerstone of protecting your organization’s digital assets. Let’s explore practical steps to strengthen your network security.
Fortify Your Network with Firewalls and IDS
Firewalls act as the first line of defense against external threats. They create a barrier between your trusted internal network and untrusted external networks (such as the internet). When selecting a firewall, consider next-generation firewalls (NGFWs) that offer advanced features like application awareness and integrated intrusion prevention systems.
Intrusion Detection Systems (IDS) complement firewalls by monitoring network traffic for suspicious activity. They alert your IT team to potential threats, allowing for quick response. For enhanced protection, consider an Intrusion Prevention System (IPS) that automatically blocks detected threats.
Secure Remote Access with VPNs
Virtual Private Networks (VPNs) have become essential for network security, especially with the rise of remote work. VPNs secure online activity, protect sensitive data, and enable safe remote access for businesses.
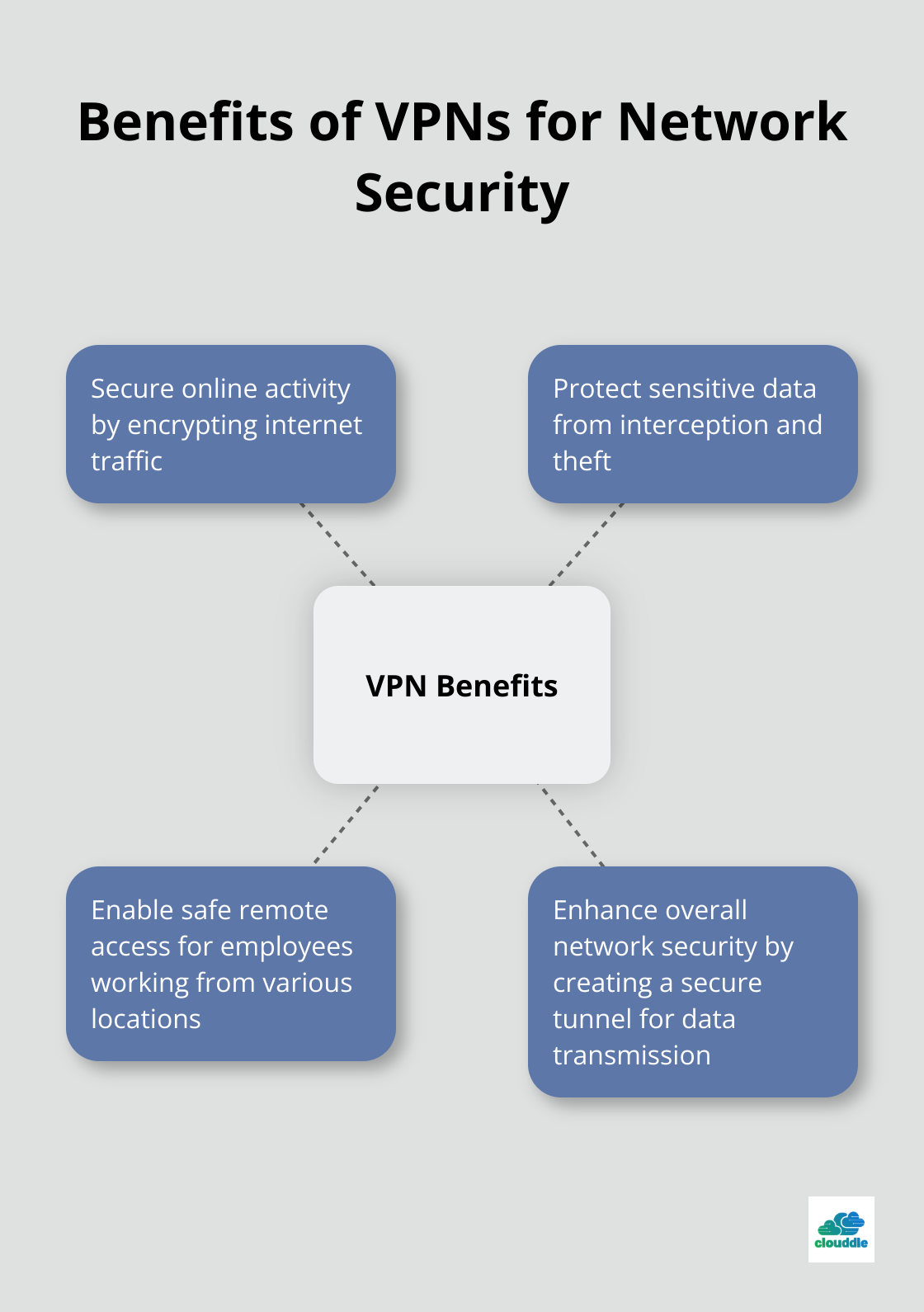
When implementing a VPN solution, select one that supports strong encryption protocols like OpenVPN or IKEv2/IPsec. Also, use multi-factor authentication (MFA) for VPN access to add an extra layer of security.
Implement Robust Access Control
Access control ensures that only authorized users can access specific resources on your network. Start by applying the principle of least privilege, which gives users only the minimum level of access they need to perform their jobs.
Strong authentication protocols are vital for effective access control. Move beyond simple passwords and implement multi-factor authentication (MFA) wherever possible.
Try implementing a Zero Trust security model, which is a special approach to cybersecurity based on rigorous verification of every device and user. This approach can significantly reduce the risk of insider threats and lateral movement by attackers.
Stay Ahead with Regular Updates
Software vulnerabilities often serve as entry points for cyber attacks. Keep all your systems and software up-to-date to close these security gaps. Implement a robust patch management process to ensure timely updates across your entire network.
Automate the update process where possible to reduce the burden on your IT team and minimize the risk of human error. For critical systems, use a staging environment to test updates before rolling them out to production.
Implementing these network security measures will significantly enhance your organization’s resilience against cyber threats. However, the work doesn’t stop here. Let’s move on to explore best practices for maintaining network security over time.
How to Maintain Strong Network Security
Empower Your Employees as Security Assets
Your employees form the first line of defense against cyber threats. Implement a comprehensive security awareness training program that surpasses annual compliance checks. Regular, engaging training sessions that simulate real-world scenarios can dramatically improve your organization’s security posture.
Conduct monthly phishing simulations to test and educate employees. A study by Proofpoint reveals that organizations running frequent phishing tests experience a 75% reduction in phishing susceptibility over time. This approach not only educates but also reinforces good security habits.

Conduct Rigorous Security Audits
Regular security audits identify vulnerabilities before exploitation. Try to schedule quarterly internal audits and annual external audits conducted by certified professionals. These audits should cover all aspects of your network infrastructure (hardware, software, and human processes).
During audits, focus on user access rights. Enforce the principle of least privilege rigorously, with access rights reviewed and adjusted regularly. This practice alone can significantly reduce the risk of insider threats and limit potential damage from compromised accounts.
Develop a Robust Incident Response Plan
No security measure is foolproof, which necessitates a well-crafted incident response plan. Your plan should outline clear procedures for detecting, responding to, and recovering from security incidents. Include specific roles and responsibilities for your team members, and establish communication protocols for both internal and external stakeholders.
Test your incident response plan through tabletop exercises and full-scale simulations. These drills help identify gaps in your response strategy and ensure that your team can act swiftly and effectively in a real crisis.
Implement Continuous Network Monitoring
Proactive network monitoring detects and responds to threats quickly. Implement a Security Information and Event Management (SIEM) system to centralize log data from across your network. This allows for real-time analysis of security events and can help identify patterns that might indicate a breach or attempted attack.
SIEM systems offer advantages such as rapid and efficient SecOps, increased security alerting and threat detection accuracy, and data centralization.
Use machine learning and artificial intelligence tools to enhance your monitoring capabilities. These technologies can analyze vast amounts of data quickly, identifying anomalies that might be missed by human analysts. For example, AI-powered systems can detect unusual login patterns or data access behaviors that could signal a compromised account.
Final Thoughts
The applications of network security continue to evolve as cyber threats become more sophisticated. Organizations must adapt their strategies to stay ahead of potential vulnerabilities. Artificial intelligence and machine learning enhance threat detection capabilities, allowing for more proactive and sophisticated defense mechanisms.
Cloud-based security solutions provide flexible and scalable options for businesses of all sizes. The rise of remote work and IoT devices presents both opportunities and challenges for network security. Organizations that prioritize security and adapt their strategies will thrive in this evolving digital landscape.
We at Clouddle understand the critical importance of network security in today’s digital world. Our Network as a Service (NaaS) solution combines cutting-edge networking, entertainment, and security features to provide seamless operations and enhanced protection for businesses (across various industries). Organizations can focus on their core operations while we handle the complexities of network security.


