Managed IT services packages have become essential for businesses looking to streamline their technology operations. These comprehensive solutions offer a wide array of services, from network management to cybersecurity and cloud integration.
At Clouddle, we understand that navigating the world of managed IT can be overwhelming. In this post, we’ll break down the key components of a robust managed IT services package, helping you make informed decisions for your business’s technological needs.
What Does Network Management and Support Entail?
Network management and support form the backbone of any comprehensive managed IT services package. We’ve observed how robust network infrastructure can transform business operations.
Setting Up and Maintaining Network Infrastructure
Proper setup and ongoing maintenance are the foundation of effective network management. This involves designing and implementing a network architecture that aligns with your business needs. The process typically starts with an assessment of your current setup, identification of bottlenecks, and proposals for improvements. This might include upgrades to outdated hardware, reconfiguration of network topology, or implementation of new technologies like software-defined networking (SDN).
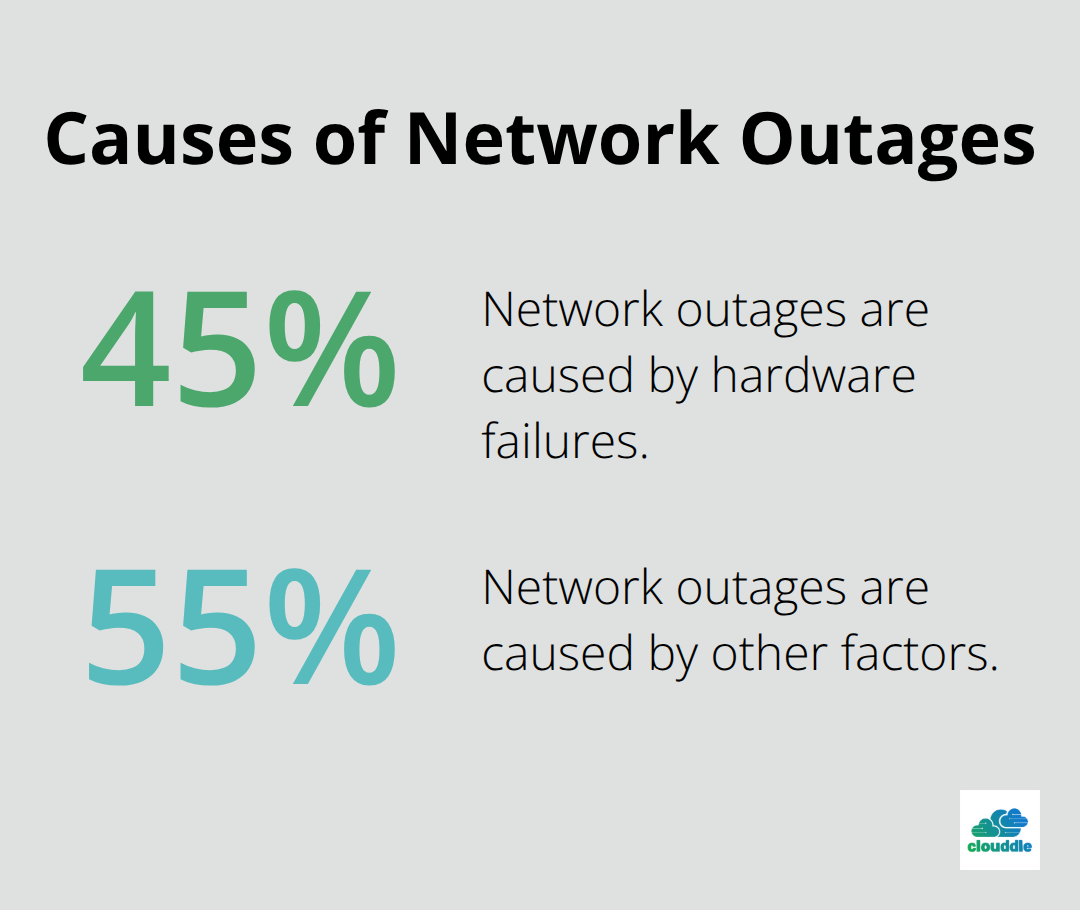
A 2022 Cisco report revealed that 45% of network outages are caused by hardware failures. Regular maintenance checks and timely hardware upgrades can significantly reduce this risk. Quarterly network audits are recommended to ensure optimal performance and identify potential issues before they escalate.
Proactive Monitoring and Swift Issue Resolution
Proactive monitoring is essential for maintaining network health. Advanced monitoring tools allow for 24/7 tracking of network performance, detecting anomalies and potential threats in real-time. Built on ManageEngine OpManager, Site24x7 offers capabilities for monitoring network traffic, fault detection, and configuration management.
Swift resolution is key when issues arise. Top-tier managed service providers often boast average response times for critical issues under 15 minutes, with most problems resolved within an hour. This level of responsiveness can save businesses thousands of dollars in potential lost productivity.
Optimizing Bandwidth and Performance
Bandwidth management, often overlooked, can significantly impact network performance. Advanced traffic shaping techniques prioritize critical applications and ensure fair distribution of network resources. Implementation of Quality of Service (QoS) policies and optimization of network traffic can lead to substantial improvements.
Secure Remote Access Solutions
The rise of remote work has made secure access to company resources from anywhere essential. Virtual Private Networks (VPNs) are a cornerstone of this strategy. However, a shift towards more advanced solutions like Zero Trust Network Access (ZTNA) is occurring, which provides more granular control and better security. ZTNA secures remote access by verifying every user and device.
Effective network management and support create a robust, secure, and efficient infrastructure that supports your business goals. The latest technologies and best practices ensure that your network is not just functional, but a true asset to your organization. As we move forward, it’s important to consider how these network management strategies intersect with another critical aspect of IT services: cybersecurity.
How Can Cybersecurity Services Protect Your Business?
In today’s digital landscape, robust cybersecurity measures are essential. Comprehensive cybersecurity services can safeguard businesses from ever-evolving threats.
Fortifying Your Digital Perimeter
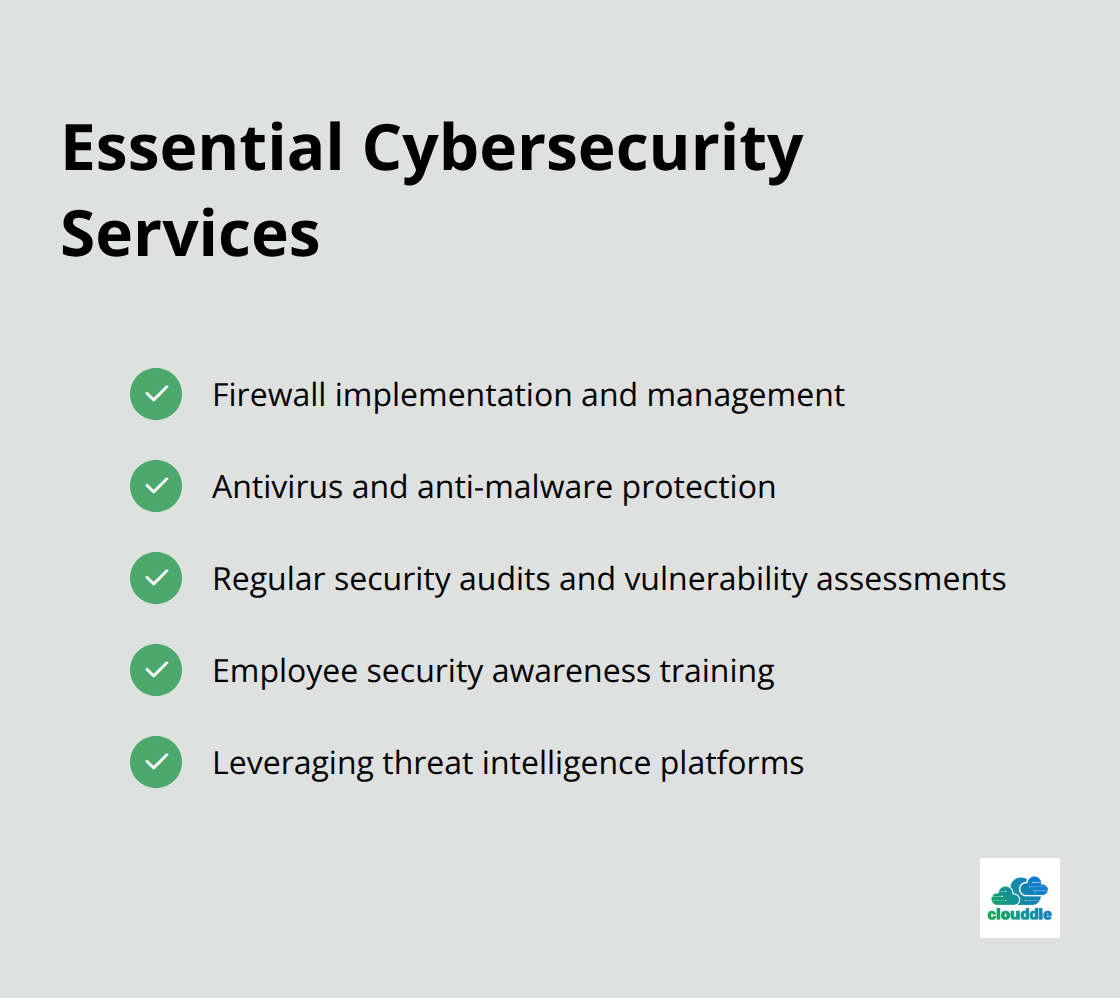
Firewall implementation and management form the first line of defense against cyber threats. Modern next-generation firewalls (NGFWs) offer deep packet inspection and application-level filtering.
Antivirus and anti-malware protection are vital components of any cybersecurity strategy. Advanced endpoint detection and response (EDR) solutions provide real-time threat detection and automated response capabilities.
Proactive Security Measures
Regular security audits and vulnerability assessments identify and address potential weaknesses in IT infrastructure. Experts recommend comprehensive assessments at least quarterly, with more frequent checks for critical systems.
Employee security awareness training prevents human-error-related breaches.
Leveraging Advanced Threat Intelligence
Threat intelligence platforms provide real-time insights into emerging threats and attack patterns. Organizations integrate threat intelligence into their security operations to proactively defend against new and sophisticated attacks.
A robust cybersecurity strategy involves more than just deploying technology; it creates a culture of security awareness and continuous improvement. As businesses fortify their digital defenses, they must also consider how these measures integrate with cloud services and data management practices. The next section explores how cloud services and effective data management complement a strong cybersecurity posture to create a comprehensive IT ecosystem.
How Cloud Services Transform Your Data Management
Cloud services and data management play a vital role in modern business operations. These technologies revolutionize the way companies handle their information and applications.
Cloud Migration and Integration
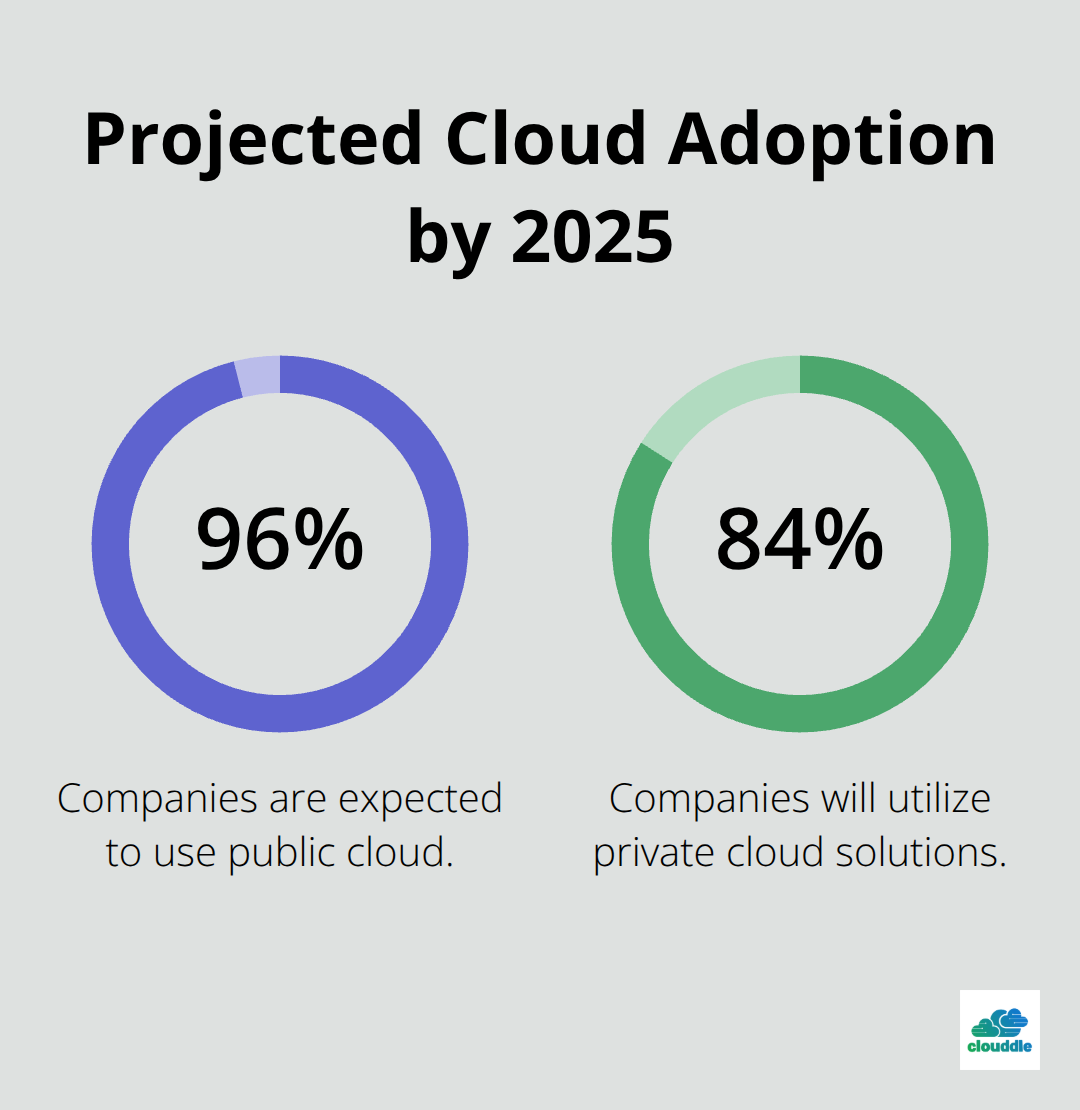
Cloud migration is now a necessity for businesses to stay competitive. By 2025, 96% of companies are expected to use the public cloud, while 84% will utilize private cloud solutions.
The key to successful migration lies in careful planning and execution. We recommend a comprehensive assessment of your current IT infrastructure and business needs. This helps identify which applications and data should move to the cloud first. Non-critical workloads typically migrate initially, followed by more complex systems.
Integration is equally important. Your cloud solutions should work seamlessly with existing on-premises systems. Tools like Dell Boomi or MuleSoft (industry leaders in integration platforms) can facilitate this process, creating a hybrid environment that leverages the best of both worlds.
Data Backup and Disaster Recovery
Data loss can devastate businesses. This highlights the importance of robust backup and disaster recovery solutions.
The 3-2-1 backup rule provides a solid foundation: maintain three copies of your data, on two different media, with one copy off-site. Cloud-based backup solutions can automate this process, ensuring your data remains protected.
For disaster recovery, a hot site solution offers maximum protection. This involves maintaining a fully operational duplicate of your critical systems in the cloud, ready to take over immediately. While more expensive, it significantly reduces downtime during a disaster.
File Storage and Sharing
Effective file storage and sharing boost productivity in today’s distributed work environments. Cloud-based solutions like Microsoft OneDrive for Business or Google Drive offer scalable storage with robust sharing and collaboration features.
When you implement these solutions, focus on user experience and security. The chosen platform should integrate well with your existing tools and workflows. Strong access controls and encryption protect sensitive data.
SaaS Management
The proliferation of SaaS applications creates new challenges in IT management. This can lead to inefficiencies, security risks, and unnecessary costs if not managed properly.
A centralized SaaS management platform provides visibility into your SaaS ecosystem. Tools like Zylo or Torii help track usage, manage licenses, and ensure compliance across all your cloud applications.
Regular audits of your SaaS portfolio are essential. You should identify underutilized or redundant applications and consolidate where possible. This reduces costs and simplifies your IT landscape.
Final Thoughts
Comprehensive managed IT services packages have become essential for businesses to optimize their technology infrastructure. These services encompass network management, cybersecurity measures, and cloud-based solutions, forming the backbone of modern IT operations. Organizations that implement these services can reduce downtime, protect against cyber threats, and gain access to specialized expertise.
The right managed IT service provider will offer a proven track record, industry-specific expertise, and a commitment to technological innovations. Clouddle offers tailored managed IT services packages that combine networking, security, and cloud solutions for industries such as hospitality, multi-family dwelling, and senior living. Our Network as a Service (NaaS) model allows businesses to leverage cutting-edge technology without significant upfront investments.
As technology rapidly evolves, partnering with a reliable managed IT services provider becomes increasingly important. Entrusting your IT infrastructure to experts allows you to navigate the complex digital landscape with confidence. Your systems will remain optimized, secure, and ready to support your business growth in the years ahead.