At Clouddle, we understand the critical role of Kerberos in network security. Configuring encryption types allowed for Kerberos is a key aspect of maintaining a robust authentication system.
This guide will walk you through the process of setting up and managing Kerberos encryption types effectively. We’ll cover everything from understanding different encryption options to implementing best practices for your Windows environment.
What Are Kerberos Encryption Types?
The Fundamentals of Kerberos Encryption
Kerberos, a key player in network security, relies on encryption to protect authentication data. Kerberos uses various encryption algorithms, known as encryption types or enctypes, to secure data. These enctypes combine cipher and integrity algorithms to ensure both confidentiality and integrity of the authentication process.
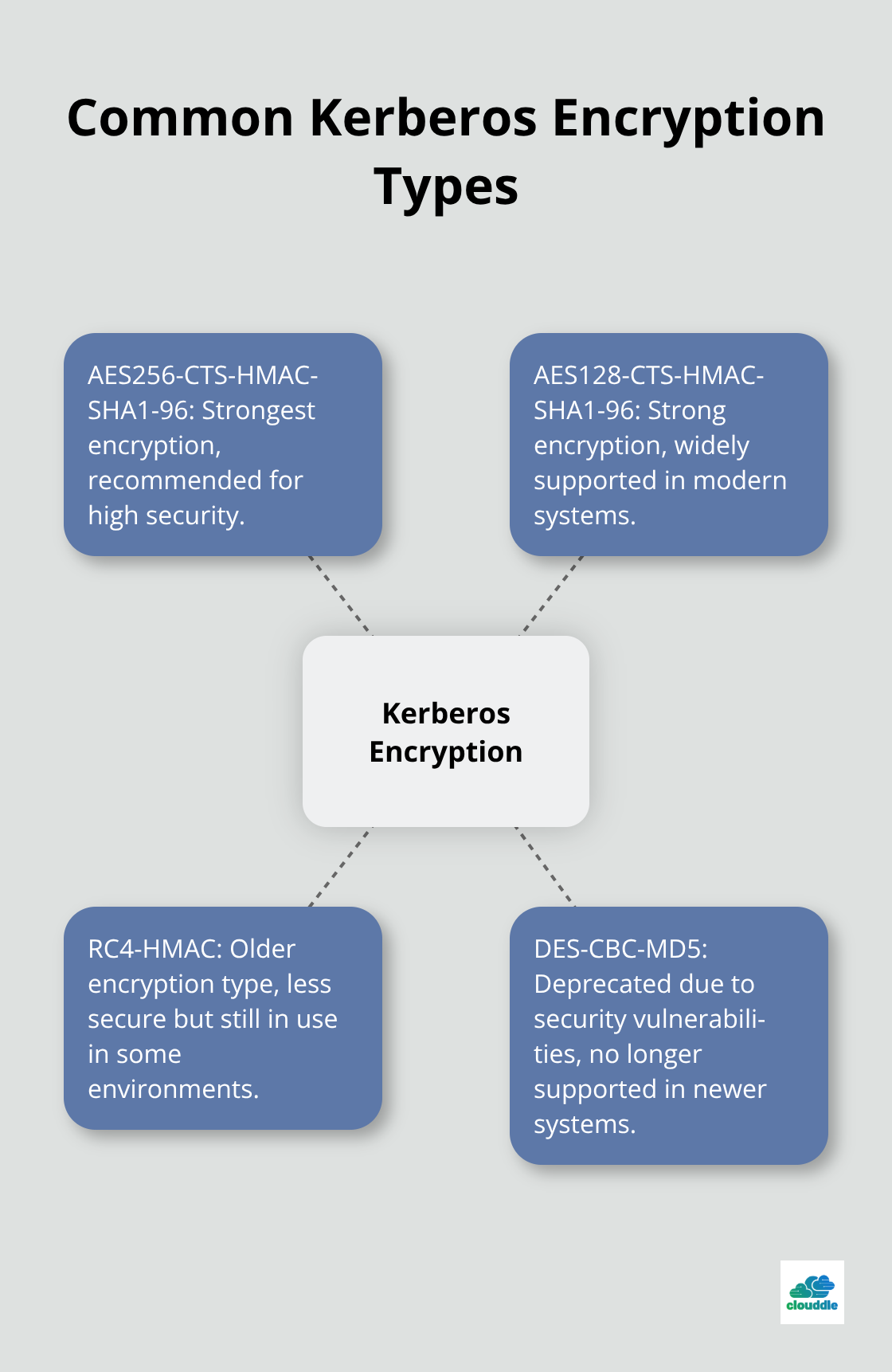
The most common encryption types include:
- AES256-CTS-HMAC-SHA1-96
- AES128-CTS-HMAC-SHA1-96
- RC4-HMAC
- DES-CBC-MD5 (deprecated)
The Evolution of Kerberos Encryption
The recommended encryption types have changed over time. DES-based encryption types are no longer supported in Windows 7 and later operating systems due to security vulnerabilities. Microsoft now recommends AES encryption types (AES128 and AES256) for enhanced security, as they are widely supported.
Selecting the Appropriate Encryption Type
The selection of the right encryption type requires a balance between security and compatibility across your network. Consider these factors:
- Security strength: AES256 offers the highest level of security among the supported types.
- Compatibility: All systems in your network must support the chosen encryption type.
- Performance: Stronger encryption may affect system performance (especially on older hardware).
The Impact of Encryption Type Selection
Your choice of encryption type can significantly affect your network’s security posture. Weak encryption types like RC4 can expose your network to various attacks. In contrast, AES encryption can reduce potential attack vectors for Kerberos authentication.
Auditing Current Encryption Usage
An audit of your current Kerberos encryption usage is essential before you make changes. Windows Server 2016 and newer versions provide enhanced logging capabilities for Kerberos events, which can help identify encryption type issues. This event generates every time Key Distribution Center issues a Kerberos Ticket Granting Ticket (TGT) and only on domain controllers.
This understanding of encryption types and their implications will equip you to make informed decisions about your Kerberos configuration. Now, let’s explore the practical steps to configure these encryption types in a Windows environment.
How to Configure Kerberos Encryption Types in Windows
Accessing Group Policy Management
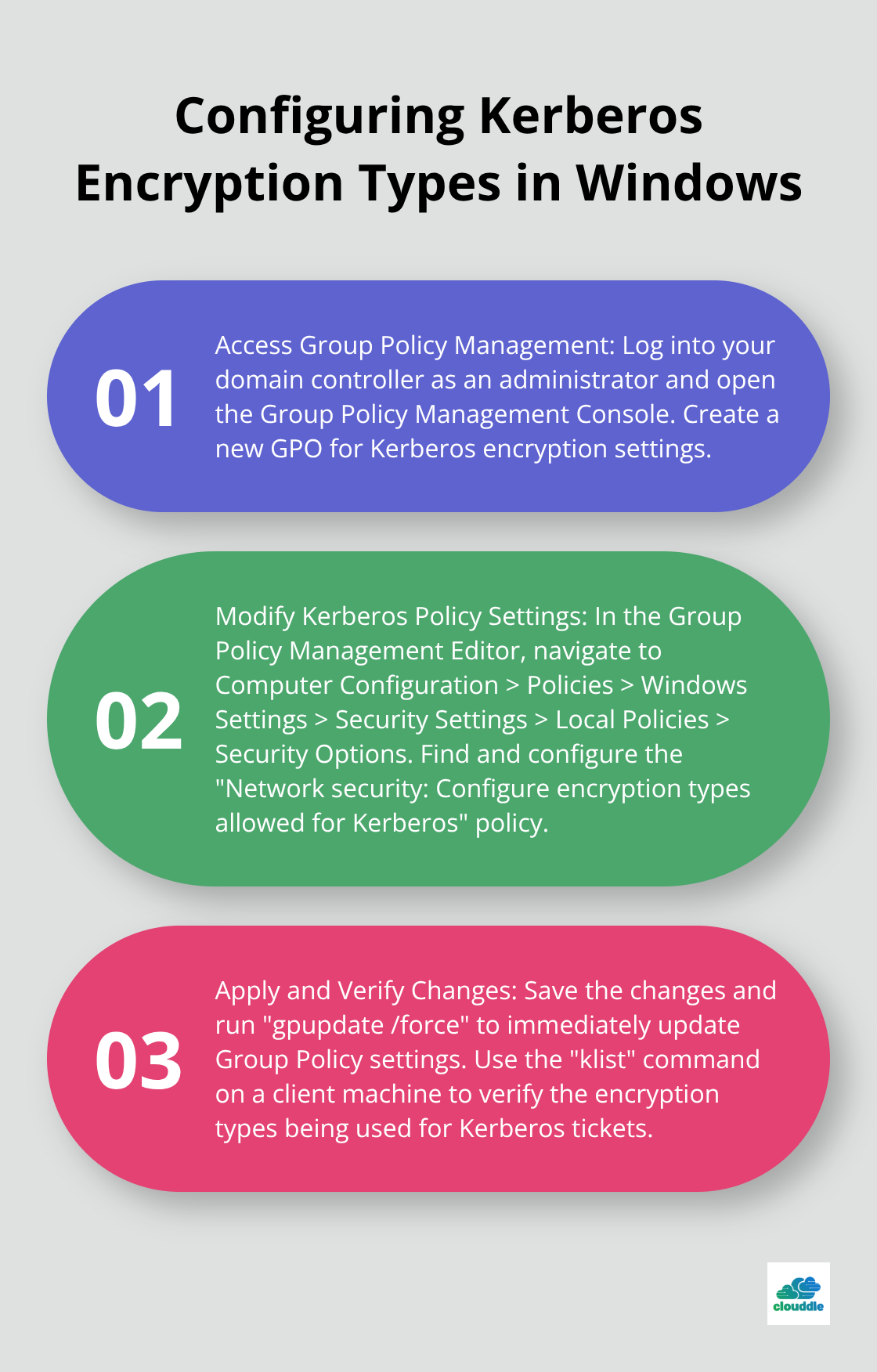
To configure Kerberos encryption types in Windows, start by logging into your domain controller as an administrator. Open the Group Policy Management Console. Navigate to the domain or organizational unit where you want to apply the Kerberos encryption settings. Right-click and select “Create a GPO in this domain, and Link it here.” Name your new GPO something descriptive (e.g., “Kerberos Encryption Settings”).
Modifying Kerberos Policy Settings
After creating the GPO, right-click on it and select “Edit.” In the Group Policy Management Editor, navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options.
Find the policy setting “Network security: Configure encryption types allowed for Kerberos.” Double-click to open its properties. Here, you can select the encryption types you want to allow. For optimal security, enable only AES256_HMAC_SHA1 and AES128_HMAC_SHA1.
Applying Changes
Once you’ve made your selections, click “Apply” and then “OK” to save the changes. To ensure the new policy takes effect immediately, open a command prompt on a domain-joined computer and run “gpupdate /force”. This command forces an immediate update of Group Policy settings.
Verifying Settings
To verify that the changes have taken effect, use the “klist” command on a client machine. This will display the encryption types being used for Kerberos tickets. Look for entries that show AES256-SHA1 or AES128-SHA1 as the encryption type.
Monitoring and Adjusting
These changes may take some time to propagate across your network (depending on your Group Policy refresh interval settings).
It’s important to note that configuring Kerberos encryption types is not a one-time task. As your network evolves and new security recommendations emerge, you’ll need to continually monitor and adjust these settings. This ongoing process ensures that your network maintains a strong security posture while balancing compatibility needs.
The next chapter will explore best practices for Kerberos encryption type configuration, providing you with valuable insights on how to optimize your settings for maximum security and efficiency.
Optimizing Kerberos Encryption Settings
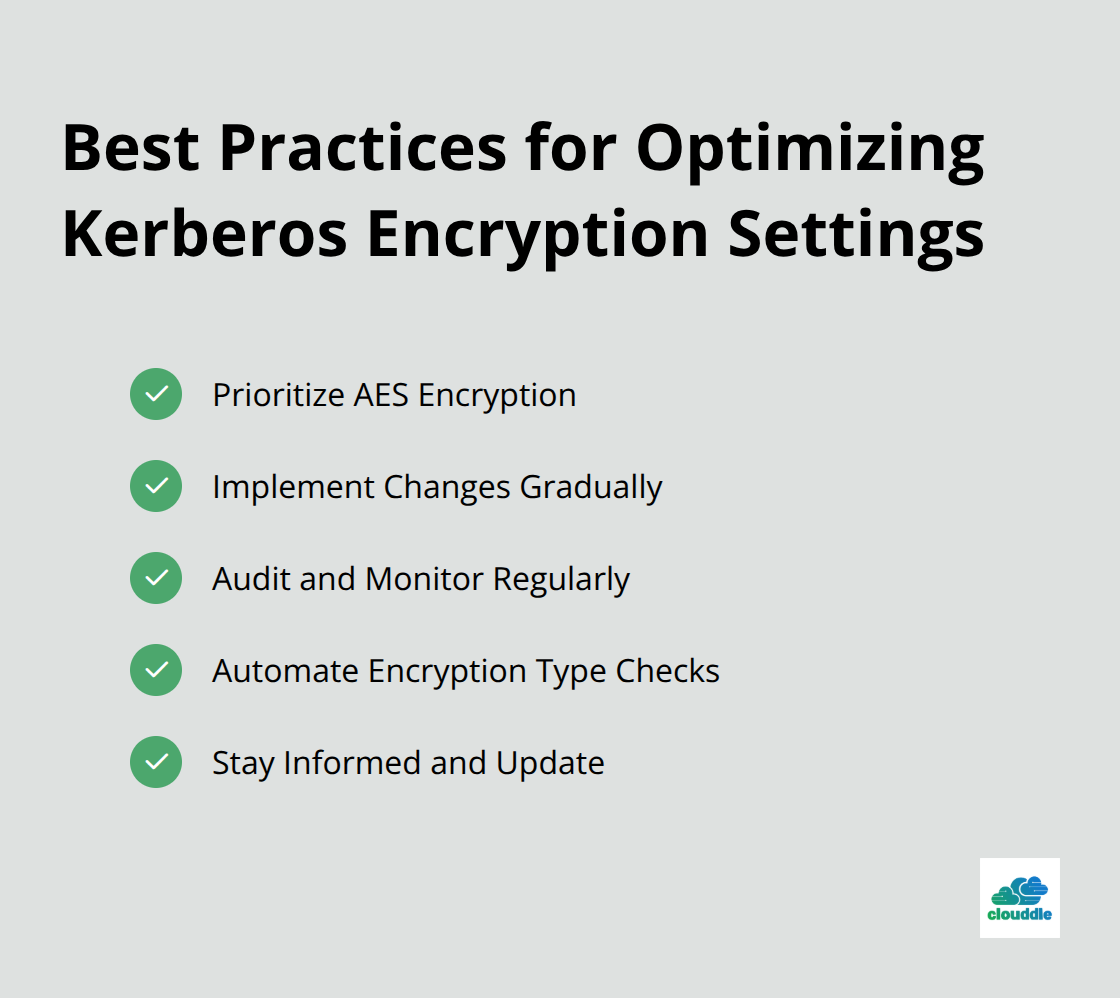
Prioritize AES Encryption
We recommend the use of AES encryption types in your Kerberos configuration. AES256-CTS-HMAC-SHA1-96 and AES128-CTS-HMAC-SHA1-96 provide superior security compared to older encryption types. Most modern Windows environments fully support AES, making it the ideal choice for balancing security and compatibility.
To implement this, modify your Group Policy Object (GPO) to allow only AES encryption types. This approach disables weaker encryption types like RC4-HMAC and DES-CBC-MD5, which are vulnerable to various attacks.
Implement Changes Gradually
If your network includes legacy systems that don’t support AES, implement changes in stages. Start by enabling AES alongside existing encryption types, then monitor for any authentication issues. Phase out older encryption types over time, which will allow you to identify and update or replace non-compliant systems.
Microsoft’s Security Compliance Toolkit can help you assess your current Kerberos settings and identify areas for improvement. Use this tool to create a baseline for your environment and track progress as you optimize your settings.
Audit and Monitor Regularly
Implement a robust auditing process to monitor Kerberos authentication events continuously. Windows Server 2016 and newer versions provide enhanced logging capabilities for Kerberos events. Enable these advanced audit policies to gain visibility into encryption type usage across your network.
Set up alerts for any attempts to use deprecated encryption types. This proactive approach allows you to quickly identify and address potential security risks or compatibility issues.
Automate Encryption Type Checks
We recommend the use of PowerShell scripts to automate the process of checking Kerberos encryption types in use. Here’s a sample script to get you started:
powershellGet-WinEvent -FilterHashtable @{LogName=’Security’;ID=4768} | Select-Object -Property TimeCreated, @{N=’User’;E={$_.Properties[0].Value}}, @{N=’EncryptionType’;E={$_.Properties[8].Value}}
This script retrieves Kerberos authentication events and displays the encryption types used, which helps you identify any unexpected or weak encryption in your environment.
Stay Informed and Update
Maintaining strong Kerberos encryption requires ongoing attention. Stay informed about the latest security recommendations and update your configurations accordingly. Try to review and adjust your Kerberos settings at least quarterly (or more frequently if your security needs dictate). This practice will help you maintain a robust security posture against potential threats.
Final Thoughts
Configuring Kerberos encryption types strengthens your network security. The “Network security: Configure encryption types allowed for Kerberos” setting in Group Policy allows you to manage these important security parameters. Regular audits and monitoring of Kerberos authentication events help identify and address potential vulnerabilities quickly.
Kerberos security practices must evolve with the changing threat landscape. We recommend you review and update your Kerberos settings quarterly to protect against emerging threats. This proactive approach ensures your network remains secure and efficient in the face of new challenges.
Clouddle offers managed IT and security services to help implement and maintain strong Kerberos configurations. Our partnership allows you to focus on your core business while we handle network security complexities. Contact us today to enhance your organization’s security posture and protect your valuable data and resources.


