Network security architecture diagrams are essential tools for visualizing and managing an organization’s cybersecurity infrastructure. These diagrams provide a clear overview of how security measures are implemented across a network.
At Clouddle, we understand the critical role these diagrams play in maintaining robust security postures. This guide will walk you through the process of creating an effective network security architecture diagram, ensuring your organization’s defenses are well-documented and optimized.
What Are Network Security Architecture Diagrams?
Definition and Purpose
Network Security Architecture Diagrams visually reflect the network’s structure and construction, and all actions undertaken for ensuring network security. These diagrams map out various components, connections, and security measures within a network, offering a comprehensive overview of data flow and protection mechanisms.
These visual tools serve as blueprints for IT teams, enabling them to understand and manage complex network environments effectively. They transform a company’s approach to network security by bringing clarity to complex systems, which facilitates team collaboration and informed decision-making about security measures.
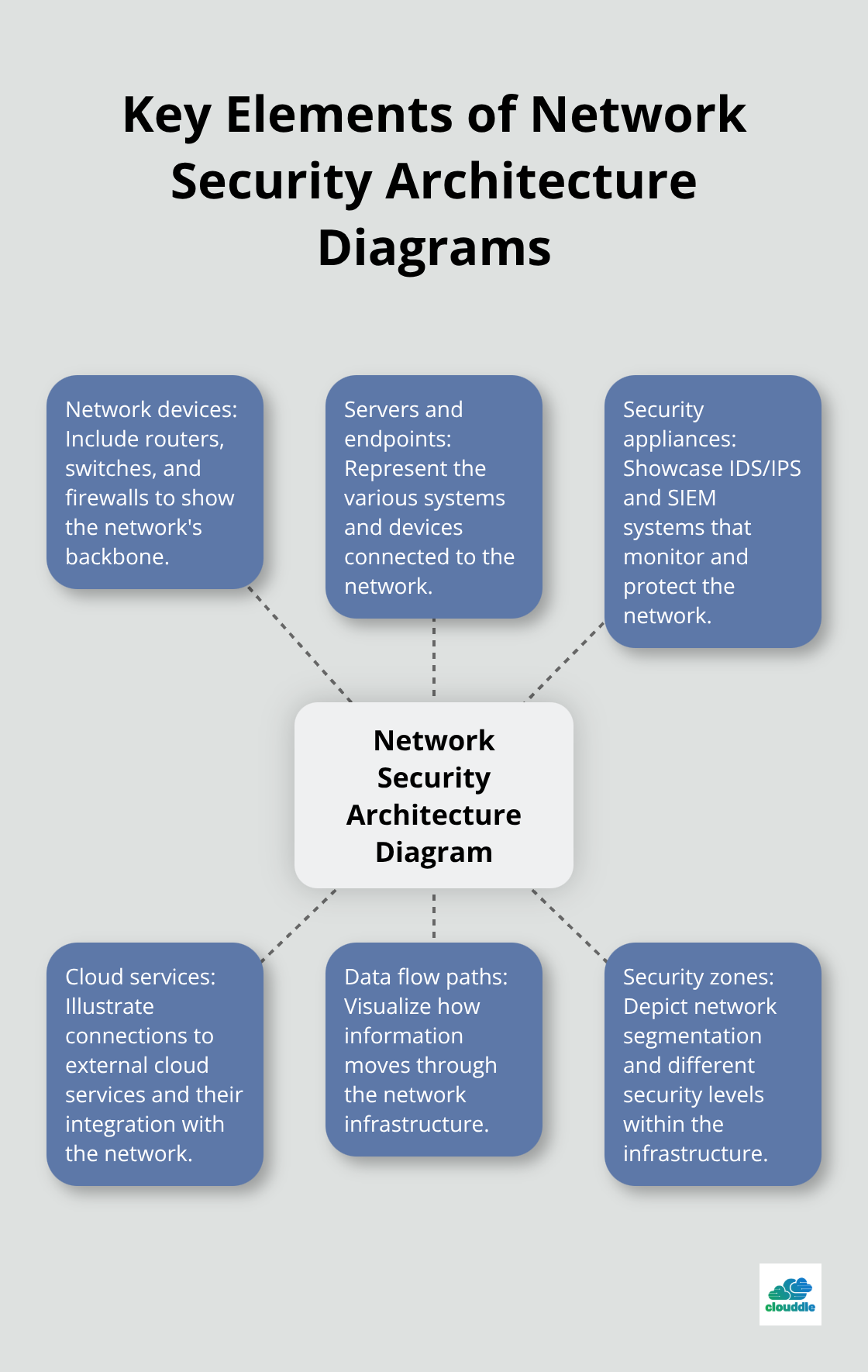
Key Elements to Include
When creating a network security architecture diagram, it’s important to include all relevant components:
- Network devices (routers, switches, firewalls)
- Servers and endpoints
- Security appliances (IDS/IPS, SIEM systems)
- Cloud services and connections
- Data flow paths
- Security zones and network segmentation
Benefits for Organizations
Network security architecture diagrams offer numerous advantages:
- Improved Risk Management: Organizations can more easily identify and address potential weak points by visualizing the entire network.
- Enhanced Compliance: These diagrams help demonstrate compliance with various regulations and standards (such as GDPR or HIPAA).
- Faster Incident Response: A clear network map allows for quicker identification and isolation of affected areas during security incidents.
- Better Communication: These diagrams act as common reference points for IT teams, management, and external auditors, facilitating clearer communication about network security.
- Efficient Planning: These diagrams provide a solid foundation for decision-making when planning network changes or expansions.
Impact on Organizational Security
The creation and maintenance of network security architecture diagrams significantly impact an organization’s overall security posture. These visual tools enable IT teams to:
- Identify potential vulnerabilities
- Optimize security measures
- Streamline incident response processes
- Improve resource allocation
With a clear understanding of the network’s structure and security measures, organizations can proactively address potential threats and ensure a robust defense against cyber attacks.
As we move forward, let’s explore the step-by-step process of creating an effective network security architecture diagram, ensuring your organization’s defenses are well-documented and optimized.
How to Build Your Network Security Architecture Diagram
Collect Comprehensive Network Data
Start by gathering detailed information about your network infrastructure. This includes hardware inventories, software applications, cloud services, and network topology. Document IP addresses, subnets, and VLANs. Tools like Nmap can automate network discovery, which reduces human error and saves time.
Map Out Security Components
Identify and map all security components and controls. This includes firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), and antivirus software. Include endpoint detection and response (EDR) solutions in your diagram for a comprehensive view.
Select the Right Diagramming Tool
Choose a diagramming tool that suits your needs. Popular options include Microsoft Visio, Lucidchart, and draw.io. Open-source alternatives like Dia work well for smaller businesses. These tools offer pre-built network symbols and templates, which speed up the diagramming process.
Create a High-Level Overview
Start with a high-level overview of your network. Add the internet connection, then core routers, switches, and main servers. Include cloud service connections. Add more detail to each section as you progress.
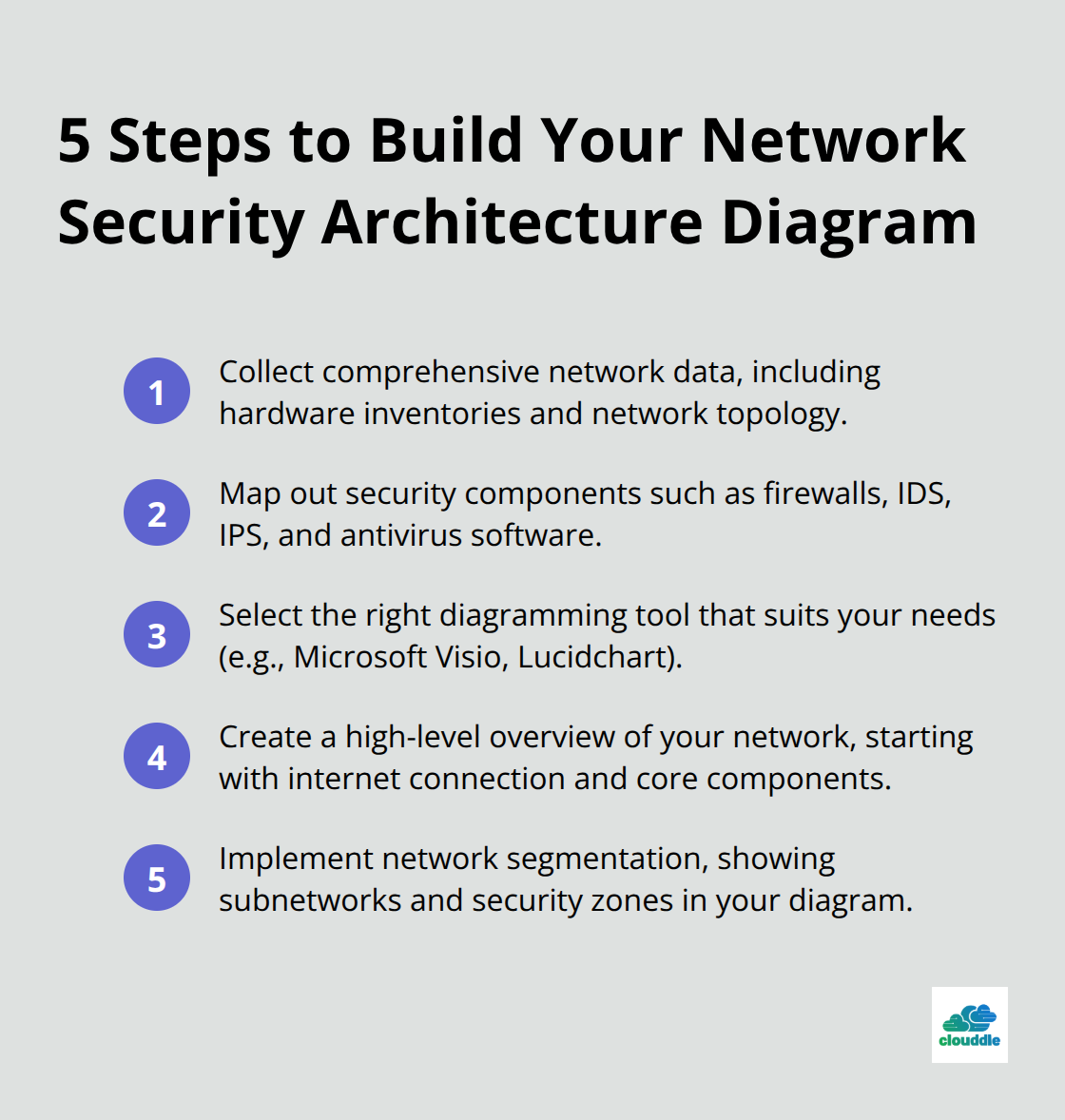
Implement Network Segmentation
Incorporate network segmentation into your diagram. This security best practice involves dividing your network into smaller subnetworks. Microsegmentation improves cybersecurity, reduces breach costs, and delivers a strong ROI for enterprises and small businesses. Show these segments clearly in your diagram, including demilitarized zones (DMZ) and internal security zones.
A well-crafted network security architecture diagram should evolve as your network changes. Regular updates ensure it remains a valuable tool for your organization’s cybersecurity efforts. In the next section, we’ll explore best practices to make your diagram even more effective and useful.
How to Optimize Your Network Security Architecture Diagram
Standardize Your Symbols
Use standardized symbols and notations to represent different network components in your diagram. According to IEEE Standard 1471-2000, architecture is a recommended practice for architectural description for software-intensive systems. Adopt these widely recognized symbols to ensure your diagram is easily understood by IT professionals across different organizations. This standardization improves clarity and reduces the risk of misinterpretation.
Simplify and Organize
An overly complex diagram can hinder understanding. Focus on the most critical elements of your network security architecture. Group related components together and use color-coding to distinguish between different security zones or network segments. This approach makes your diagram more digestible and easier to navigate. Try to strike a balance between detail and clarity (too much information can be as problematic as too little).
Keep It Current
Network environments change frequently, with updates to hardware, software, and security measures. Schedule regular reviews of your diagram (ideally quarterly) to ensure it accurately reflects your current network state. Many organizations use automated network mapping tools to streamline this process. These tools detect changes in your network configuration and update your diagram accordingly, which saves time and reduces the risk of human error.
Balance Physical and Logical Elements
Your diagram should represent both physical and logical security elements. Physical elements include hardware devices like firewalls and routers, while logical elements encompass software-based security measures such as access controls and encryption protocols. Include both to provide a comprehensive view of your security architecture. For instance, show how your physical firewall interacts with your virtual private networks (VPNs) to secure remote access.
Document Assumptions and Limitations
No diagram is perfect, and it’s essential to acknowledge its limitations. State any assumptions made during the creation of the diagram clearly. For example, if you represent certain cloud services as a single entity for simplicity, note this in your documentation. Additionally, highlight any known limitations of your current security architecture. This transparency helps identify areas for improvement and ensures that decision-makers have a realistic understanding of your network’s security posture.

Final Thoughts
Network security architecture diagrams provide a clear visual representation of an organization’s cybersecurity infrastructure. These diagrams serve as cornerstones for effective security management, risk assessment, and decision-making processes. They enable IT teams to identify vulnerabilities, optimize defenses, and respond swiftly to potential threats.
Creating and maintaining a network security architecture diagram requires an ongoing process. As networks evolve and new technologies emerge, organizations must update these diagrams regularly to reflect the current state of their infrastructure. We at Clouddle understand the critical role that network security plays in modern business operations.
Our managed IT and security services help organizations maintain robust, secure networks without significant upfront investments. We recommend quarterly assessments to ensure your diagram accurately reflects any changes in your network infrastructure (this proactive approach helps identify potential security gaps). A well-maintained network security architecture diagram supports informed decision-making, facilitates compliance, and enhances overall cybersecurity efforts.


