Cyberattacks cost businesses an average of $4.45 million per breach in 2023, making business data network security a top priority for companies of all sizes.
We at Clouddle see organizations struggle daily with protecting their digital assets from increasingly sophisticated threats. The right security framework can reduce your risk by up to 80% while maintaining operational efficiency.
What Makes Your Network Vulnerable to Attack
Your network faces three primary threat vectors. Unpatched software represents the most dangerous vulnerability, with systems that run outdated applications becoming entry points for attackers within hours of exploit publication. Organizations that take longer to apply critical patches face significantly higher breach probability compared to those that patch quickly.
Weak Authentication Opens Every Door
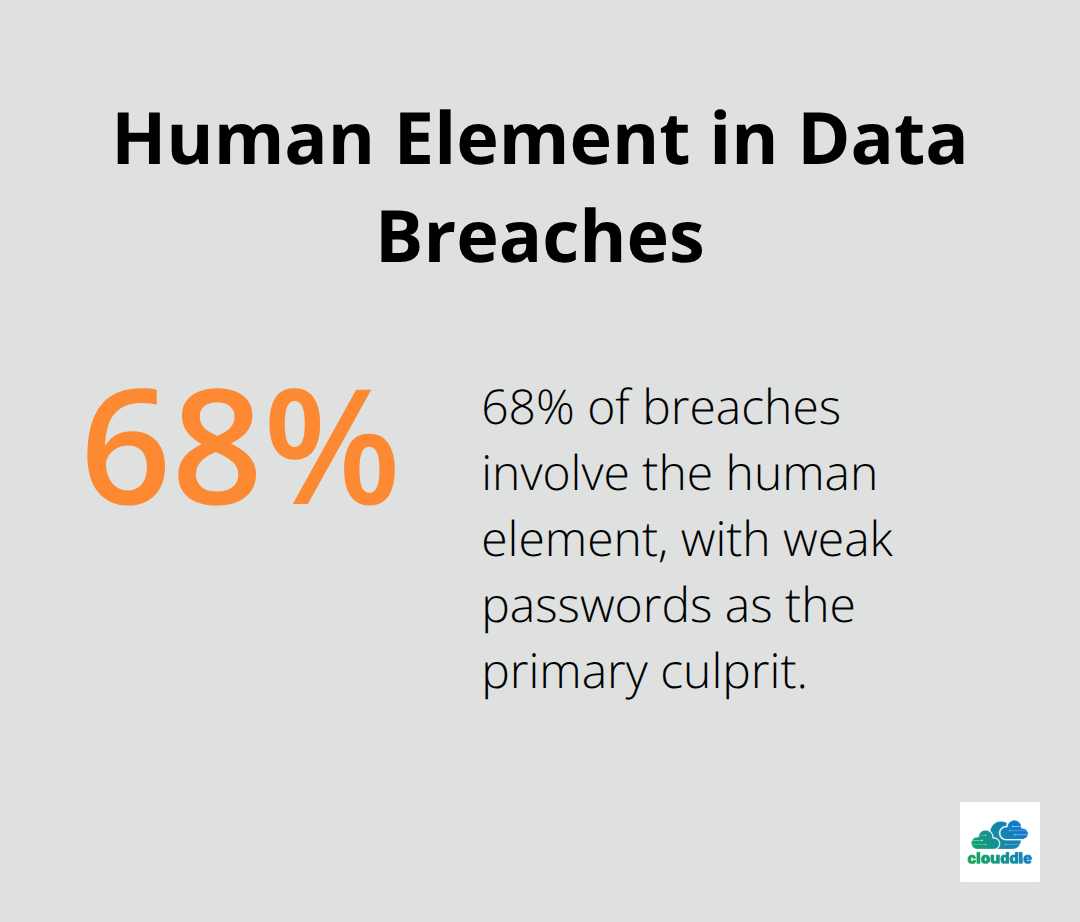
Password-based authentication fails catastrophically in modern threat environments. Verizon’s 2024 Data Breach Investigations Report shows that 68% of breaches involve the human element, with weak passwords as the primary culprit. Multi-factor authentication blocks 99.9% of automated attacks according to Microsoft data, yet only 22% of small businesses implement it properly. Your employees need unique 16-character passwords with mandatory rotation every 90 days, combined with hardware security keys for administrative accounts.
Network Monitoring Catches What Firewalls Miss
Traditional perimeter security fails against insider threats and sophisticated attacks that bypass initial defenses. Infostealers were highly prevalent in 2024, responsible for 24% of cyber incidents. Deploy network segmentation with zero-trust verification for every device and user, regardless of location. Monitor baseline protocols continuously to identify unusual traffic patterns that indicate data exfiltration or lateral movement within your systems.
Physical Access Creates Hidden Vulnerabilities
Physical security gaps expose your network to direct attacks that bypass digital defenses entirely. Unsecured server rooms, unlocked workstations, and accessible network equipment provide attackers with direct system access (often within minutes of entry). The National Institute of Standards and Technology reports that 15% of data breaches involve physical access to systems. Lock down all network infrastructure, implement badge access controls, and require authentication for any device connection to your network.
These vulnerabilities work together to create multiple attack paths that sophisticated threats exploit simultaneously. The next step involves implementing comprehensive protection measures that address each vulnerability layer systematically.
How Do You Build Bulletproof Network Defenses
Network protection requires three non-negotiable components that work together to stop attacks before they penetrate your systems. Start with next-generation firewalls that inspect application-layer traffic, not just ports and protocols. However, application proxy firewalls can impact performance since firewall activities take place at the application level of the OSI model.
Configure your firewall with default-deny rules, whitelist only necessary applications, and enable deep packet inspection for all traffic. Position firewalls at every network junction (including between internal network segments), and integrate intrusion prevention systems that automatically block malicious IP addresses within seconds of detection.
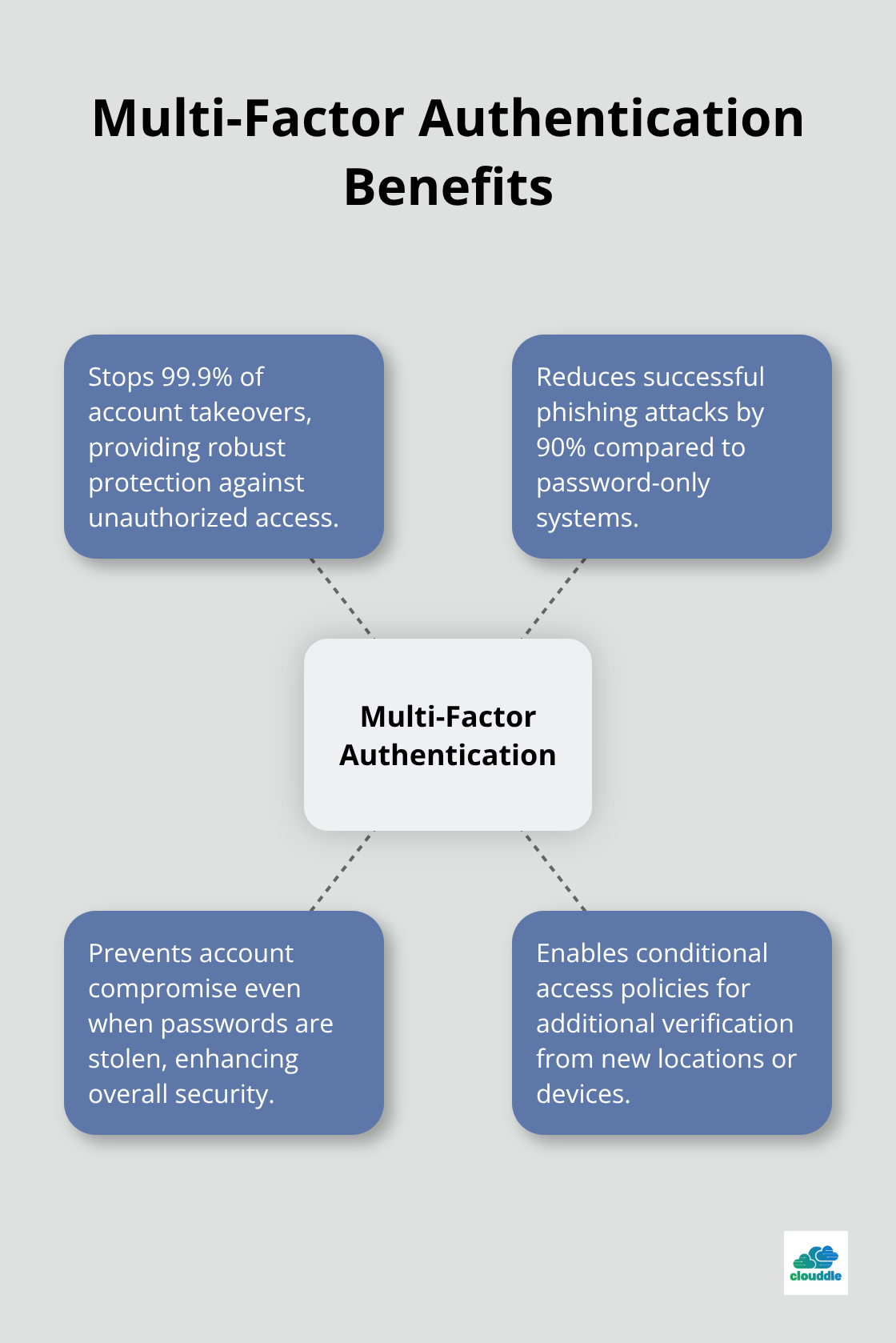
Multi-Factor Authentication Stops 99.9% of Account Takeovers
Deploy hardware security keys for all administrative accounts and management systems immediately. Microsoft data shows that hardware-based authentication prevents account compromise even when passwords are stolen. Require authentication apps like Microsoft Authenticator or Google Authenticator for standard user accounts, and ban SMS-based codes that attackers can intercept through SIM swapping attacks.
Set up conditional access policies that require additional verification when users access systems from new locations or devices. The Federal Trade Commission reports that businesses with proper multi-factor authentication experience 90% fewer successful phishing attacks compared to password-only systems.
Automated Patch Management Closes Attack Windows
Critical security patches must deploy within 72 hours of release to prevent exploitation. The Cybersecurity and Infrastructure Security Agency notes that zero-day vulnerabilities were the majority of the most frequently exploited vulnerabilities in 2023, representing an increase from 2022.
Implement automated patch management systems that test updates in isolated environments before production deployment. Schedule automatic updates for operating systems, applications, and firmware during maintenance windows, and maintain an inventory of all software versions across your network. Create emergency procedures for zero-day patches that bypass normal testing when immediate deployment becomes necessary.
These technical defenses form your security foundation, but they only work when your team knows how to use them properly and maintains constant vigilance against evolving threats. Consider partnering with a managed service provider to ensure 24/7 monitoring and expert management of your security infrastructure.
How Do You Protect Data Through People and Processes
Your security technology means nothing without proper human oversight and data protection protocols. ConnectWise research shows that SMB cybersecurity budgets are increasing, with 58% of small and medium-sized businesses spending more than planned on cybersecurity in 2024.
Security Training Must Target Real Attack Methods
Train employees monthly on current phishing techniques, not generic awareness presentations that waste time. Use simulated phishing campaigns that mirror actual attacks your industry faces, and immediately retrain anyone who clicks malicious links. Research indicates that social engineering and phishing are involved in 70% to 90% of data breaches.

Mandate security training during onboarding and require refresher sessions every 90 days that cover password management, suspicious email recognition, and reporting procedures for potential security incidents. Focus training sessions on real attack vectors rather than theoretical scenarios that employees forget within days.
Continuous Network Monitoring Catches Threats Within Minutes
Deploy endpoint detection and response solutions that monitor every device connected to your network in real-time. Traditional antivirus software only catches 25% of modern malware according to cybersecurity firm CrowdStrike, while behavioral monitoring identifies threats through unusual activity patterns.
Set up automated alerts for failed login attempts, large file transfers, and connections to known malicious IP addresses. Monitor network traffic baselines continuously and investigate any deviation from normal patterns immediately. User behavior analytics can detect compromised accounts up to 200 days faster than manual monitoring methods, making effective network security analysis possible before significant damage occurs.
Daily Backups Save Your Business From Ransomware
Back up critical data every 24 hours with the 3-2-1 rule: three copies of data, two different storage types, and one offsite location. Test backup restoration monthly because 60% of businesses that lose data shut down within six months according to the National Archives and Records Administration.
Store backups offline or in immutable cloud storage that ransomware cannot encrypt, and maintain separate credentials for backup systems that attackers cannot access through compromised user accounts. Automated cloud backups provide better security than local storage since they include versioning and geographic redundancy that protects against both cyberattacks and natural disasters.
Physical Document Security Prevents Data Leaks
Secure physical documents to prevent unauthorized access and potential data breaches. Regularly shred unnecessary files and maintain strict access controls for sensitive paperwork. Many organizations focus exclusively on digital security while leaving printed materials exposed to theft or unauthorized copying.
Implement document retention policies that specify how long you keep different types of records and when you destroy them. Physical security gaps often provide the easiest path for attackers who want to bypass sophisticated digital defenses entirely.
Human error remains the biggest security threat, but proper training, monitoring, and backup procedures transform your workforce from a vulnerability into your strongest defense layer.
Final Thoughts
Business data network and security protection demands immediate action across three essential areas. Deploy next-generation firewalls with automated patch management, implement hardware-based multi-factor authentication for all accounts, and establish continuous network monitoring with daily backup procedures. These technical foundations must combine with monthly employee security training and strict physical access controls.
The complexity of modern cybersecurity demands professional expertise that most businesses cannot maintain internally. We at Clouddle see organizations struggle with 24/7 monitoring, threat response, and keeping pace with evolving attack methods (which change daily as attackers develop new techniques). Professional IT support provides the specialized knowledge and round-the-clock vigilance that effective network protection requires.
Your network security investment pays dividends through reduced breach risk, maintained customer trust, and operational continuity. Leadership commitment and consistent enforcement of security policies create a security-focused culture where every employee understands their role in protecting company data. Clouddle combines networking, security services, and 24/7 support to protect your business without requiring internal IT expertise or upfront investment.


