IT contracts carry significant risks that can cost companies millions in legal disputes and damages. A well-crafted indemnity clause in IT contracts serves as your primary defense against these financial threats.
We at Clouddle have seen countless businesses struggle with poorly written indemnification terms that leave them exposed to liability. This guide breaks down the essential elements you need to protect your organization while maintaining fair business relationships.
What Are Indemnity Clauses in IT Contracts
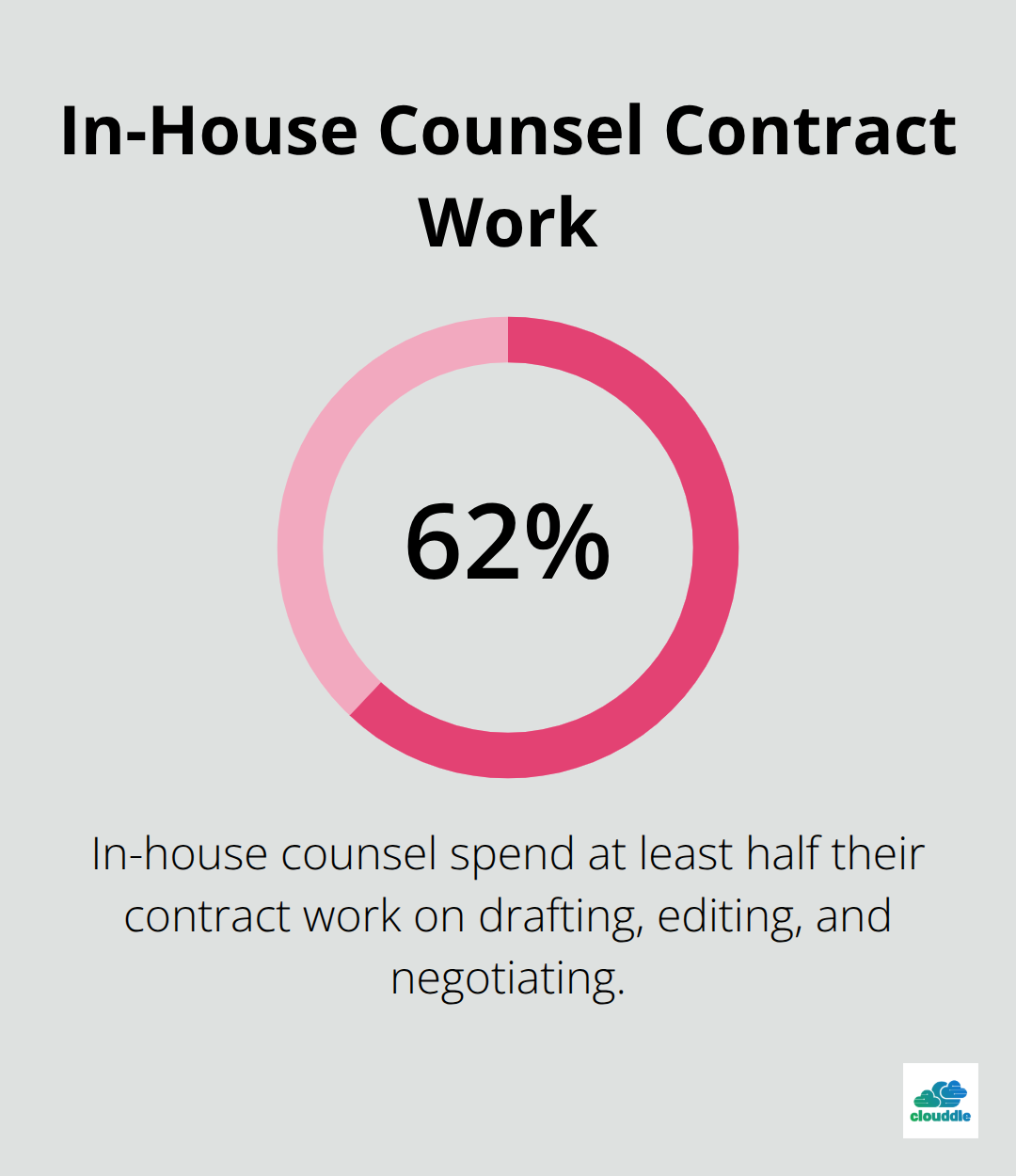
Indemnity clauses in IT contracts are contractual provisions where one party agrees to compensate another for specific losses, damages, or legal costs that arise from defined events or circumstances. These clauses shift financial responsibility from one party to another, typically requiring the service provider to cover costs when third parties sue the client over the provider’s actions, products, or services. 62% of in-house counsel indicated that drafting, editing, and negotiating contracts constitutes at least half of their contract work, yet many organizations still struggle with poorly constructed indemnification terms.
One-Sided vs Mutual Indemnification Structures
Technology agreements typically feature either one-sided indemnification (where only the vendor protects the client) or mutual indemnification (where both parties provide reciprocal protection). One-sided agreements dominate software licensing deals, with vendors who indemnify clients against intellectual property infringement claims. Mutual indemnification appears more frequently in complex integration projects or partnerships where both parties contribute technology components. The choice between structures depends on risk distribution, with clients in stronger negotiation positions who often secure one-sided protection while vendors push for mutual arrangements to balance exposure.
Enforceability Standards Across Jurisdictions
Courts scrutinize indemnification clauses heavily, particularly broad form indemnifications that attempt to cover all possible damages. States like New York and California permit indemnification for negligence but prohibit coverage for gross negligence or intentional misconduct. Regulated industries face additional restrictions, with healthcare and construction sectors often barred from indemnification of their own negligence through statutory limitations. Power imbalances between parties influence enforceability, as courts evaluate whether clauses promote irresponsible behavior or violate public policy before enforcement.
Defense Obligations and Cost Coverage
The duty to defend represents a broader obligation than simple indemnification and requires the indemnitor to cover defense costs regardless of lawsuit outcomes. Without explicit defense language, indemnification limits itself to losses that occur after a judgment renders. This distinction creates significant financial exposure for indemnitees who face substantial legal costs before claim resolution. Defense obligations typically trigger when claims fall within the scope of covered events, even if the ultimate liability remains uncertain.
The next section examines the specific components that make indemnity clauses effective in technology agreements.
Key Components of Effective IT Indemnity Clauses
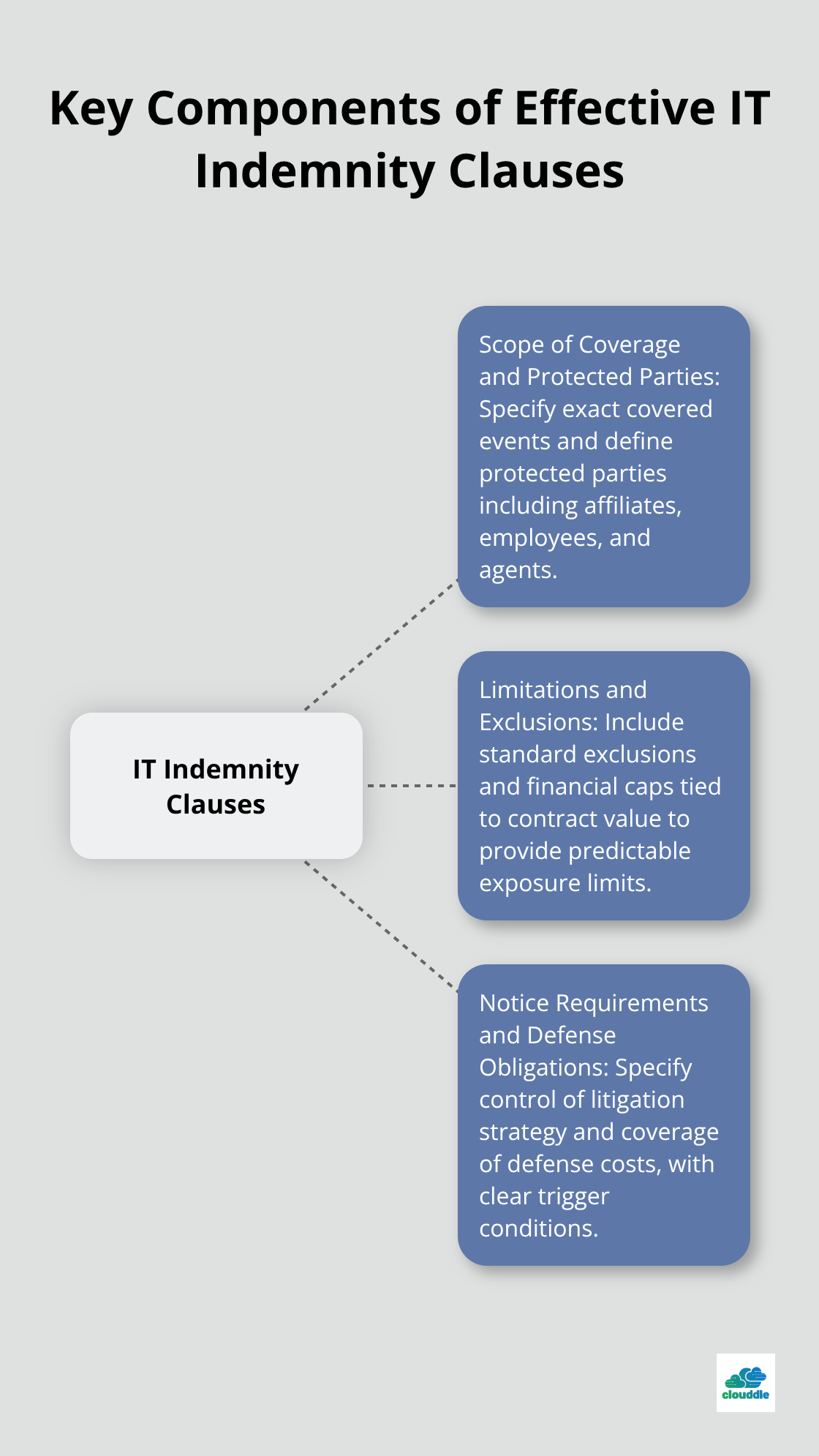
Scope of Coverage and Protected Parties
Effective indemnity clauses specify exact covered events rather than broad catch-all language that courts often reject. The strongest provisions identify specific risks like intellectual property infringement, data breaches, regulatory violations, or third-party bodily injury claims. Smart organizations limit coverage to direct damages and exclude consequential or punitive damages (which can multiply exposure by 10x or more). Protected parties should include named entities plus their affiliates, employees, and agents, but avoid unlimited extensions that create unmanageable risk pools. Technology vendors who provide clear scope definitions see fewer indemnification disputes according to contract management studies.
Limitations and Exclusions to Consider
Well-crafted exclusions protect against frivolous claims while they maintain legitimate coverage. Standard exclusions include modifications made by the client, use outside authorized parameters, combination with third-party products, or failure to install updates. Financial caps tied to contract value provide predictable exposure limits, with most vendors who accept 1-2x annual fees for IP indemnification and higher multiples for data breach coverage. Notice requirements demand written notification within 30-60 days of claim knowledge, with shorter windows that favor indemnitors and longer periods that protect indemnitees.
Notice Requirements and Defense Obligations
Defense obligations should specify whether the indemnitor controls litigation strategy or merely funds defense costs, as control provisions significantly impact settlement outcomes and total expenses. The duty to defend creates broader obligations than simple indemnification and requires coverage of defense costs regardless of lawsuit outcomes. Without explicit defense language, indemnification limits itself to losses after judgment occurs. These provisions trigger when claims fall within covered events scope, even when ultimate liability remains uncertain. The next section explores how organizations can avoid common mistakes that weaken these protective measures.
Common Pitfalls and Best Practices
Vague Language Creates Legal Nightmares
Organizations that use broad phrases like “covers all claims” or “protects against any damages” face immediate enforceability problems in court. In-house counsel prefer specific contract language over generic templates, yet many IT agreements still contain meaningless catch-all terms. Effective clauses name exact risks like patent infringement, copyright violations, or data privacy breaches rather than sweeping liability protection. Courts regularly strike down overly broad indemnification that attempts to cover gross negligence or intentional misconduct, which leaves companies without protection when they need it most. Smart negotiators specify events that trigger coverage, define covered damages, and establish clear boundaries rather than hope vague language will stretch to cover unforeseen situations.
Risk Distribution Determines Contract Success
The strongest indemnification structures reflect actual risk ownership rather than one party’s wishful thinking. Software vendors should indemnify IP infringement because they control code development, while clients should cover data breaches from their own security failures or employee negligence. Mutual indemnification works when both parties contribute equal risk exposure, but forced mutual terms often create imbalanced protection that benefits the stronger party in negotiations. Financial caps tied to contract value provide predictable exposure limits, with most technology vendors who accept 1-2x annual fees for IP coverage and 3-5x for data breach indemnification.
Financial Protections Prevent Catastrophic Exposure
Insurance requirements should mandate minimum coverage amounts that align with indemnification obligations (typically $2-5 million in professional liability and cyber coverage for enterprise agreements). Companies must verify that insurance policies actually cover indemnified risks rather than assume standard policies provide adequate protection. Many professional liability policies exclude IP infringement claims, which creates gaps that render indemnification worthless. Smart organizations require certificates of insurance that name them as additional insureds and include 30-day cancellation notice provisions to prevent coverage lapses during contract terms.

Final Thoughts
Indemnity clauses in IT contracts protect organizations from third-party claims, regulatory violations, and intellectual property disputes that destroy unprepared businesses. These provisions transfer risk to parties who can best manage specific threats while they establish predictable cost structures through caps and exclusions. Professional legal review remains essential for complex technology agreements because courts invalidate poorly drafted clauses regularly.
State-specific enforceability standards vary significantly across jurisdictions, which makes expert guidance necessary to prevent costly mistakes. Organizations must align their indemnification terms with actual business risks rather than rely on generic templates. Companies need comprehensive insurance coverage that matches their indemnified obligations (typically $2-5 million for enterprise agreements), proper notice procedures, and clear defense obligations to maximize protection.
We at Clouddle help businesses navigate technology contract complexities while we maintain secure operations. Our managed IT services support organizations who need professional technology partnerships alongside strong indemnity clause frameworks in IT contracts. These combined protections create the foundation for successful digital transformation initiatives.


