Network security threats grow more sophisticated every day, forcing businesses to rethink their defense strategies. Traditional in-house security teams often lack the resources and expertise to combat modern cyber attacks effectively.
We at Clouddle see companies struggling with this challenge daily. Managed network security solutions offer a proven path forward, combining advanced technology with expert oversight to protect your business around the clock.
What Do Managed Network Security Solutions Actually Include
Managed network security solutions encompass far more than basic firewall management. These comprehensive services include 24/7 threat detection, incident response, vulnerability assessments, patch management, and compliance reports. Security Information and Event Management (SIEM) systems aggregate data from multiple sources to provide complete visibility across your network infrastructure. Advanced solutions incorporate behavioral analysis through AI-driven tools that adapt to your specific environment, which moves beyond traditional signature-based detection methods.
The Cost Reality of Traditional vs Managed Approaches
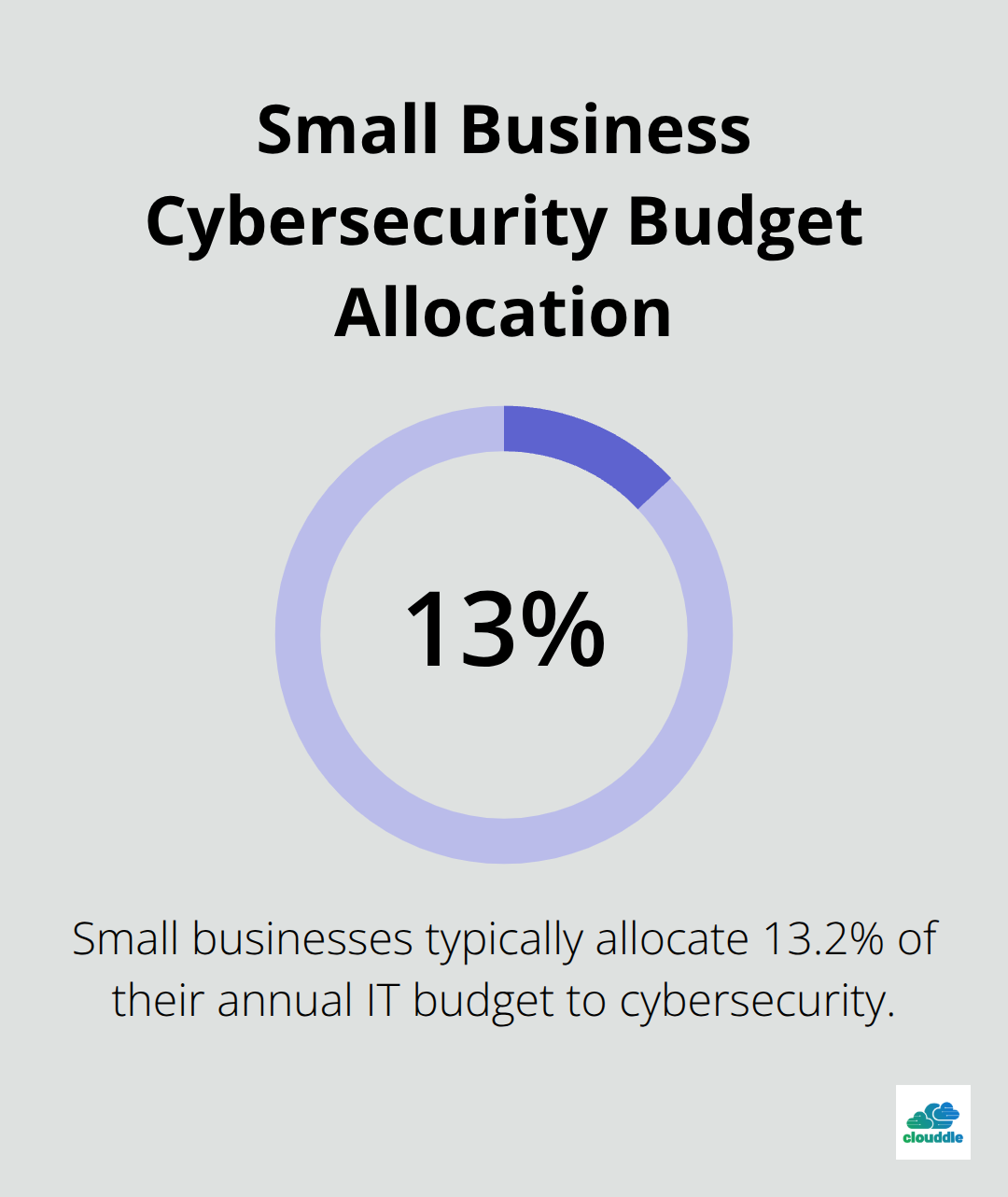
Traditional in-house security requires significant upfront investment and expenses that many businesses underestimate. Small businesses typically need to allocate 13.2% of their annual IT budget to cybersecurity, with comprehensive coverage that averages $2,500 to $2,800 per employee annually (according to Verizon’s 2024 Data Breach Investigations Report). Managed services eliminate these variable costs through predictable monthly fees around $500, while they provide access to enterprise-grade security tools and expertise that would cost hundreds of thousands to build internally.
Why Companies Abandon Traditional Methods
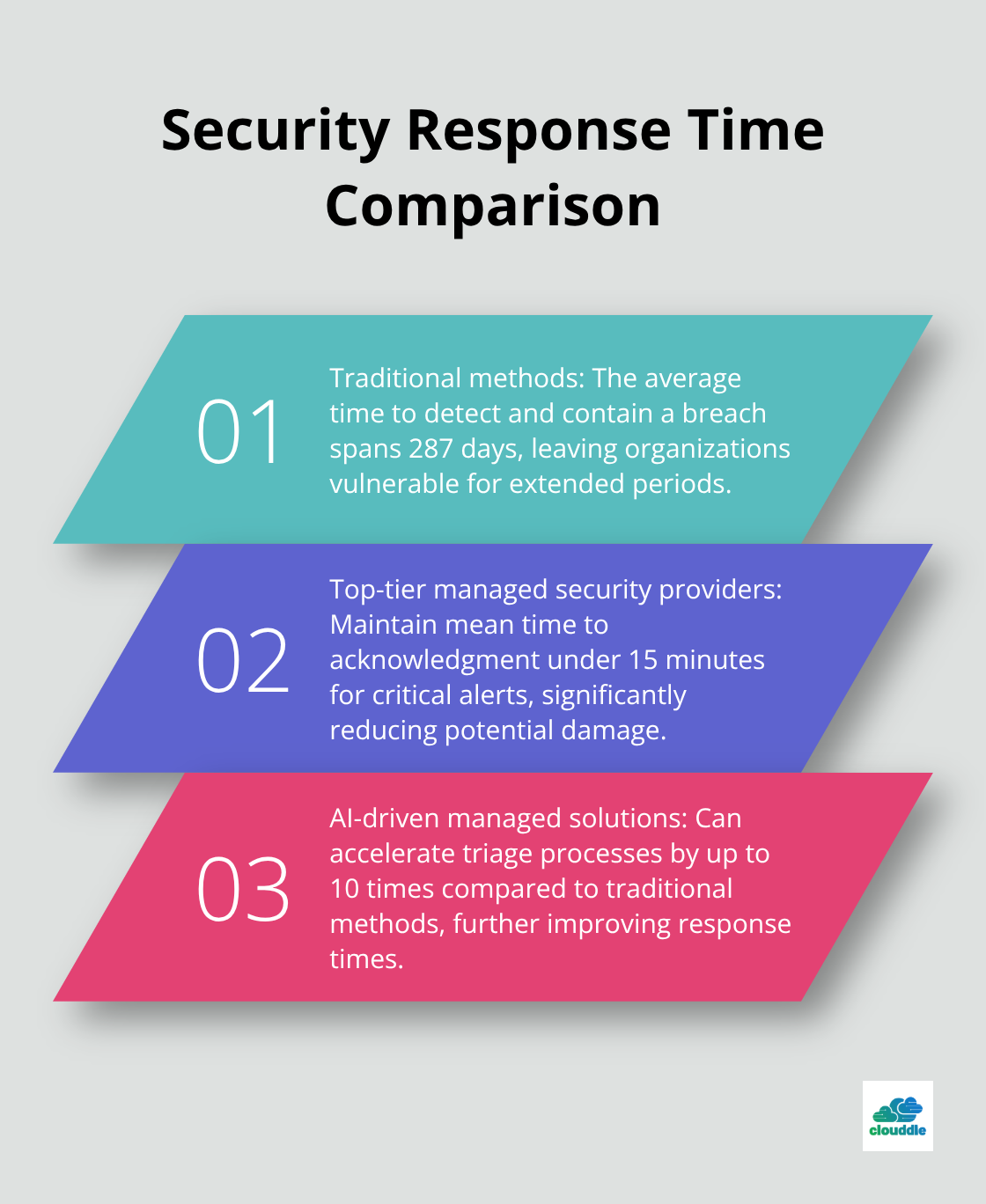
The numbers tell a compelling story about why companies abandon traditional approaches. Cybercrime costs are set to reach $10.5 trillion by 2025 and could reach as high as $15.63 trillion by 2029, which requires expertise that most internal teams lack. The average time to detect and contain a breach spans 287 days with traditional methods, while AI-driven managed solutions can accelerate triage processes by up to 10 times. Companies that use managed security services experience significantly lower incident rates than those that rely solely on internal resources.
What This Means for Your Security Strategy
This shift toward managed solutions reflects a fundamental change in how businesses approach network protection. Organizations now recognize that effective security requires specialized expertise, advanced tools, and constant vigilance that internal teams cannot match. The question becomes not whether to adopt managed security, but which features and capabilities will best serve your specific needs.
Essential Features to Look For
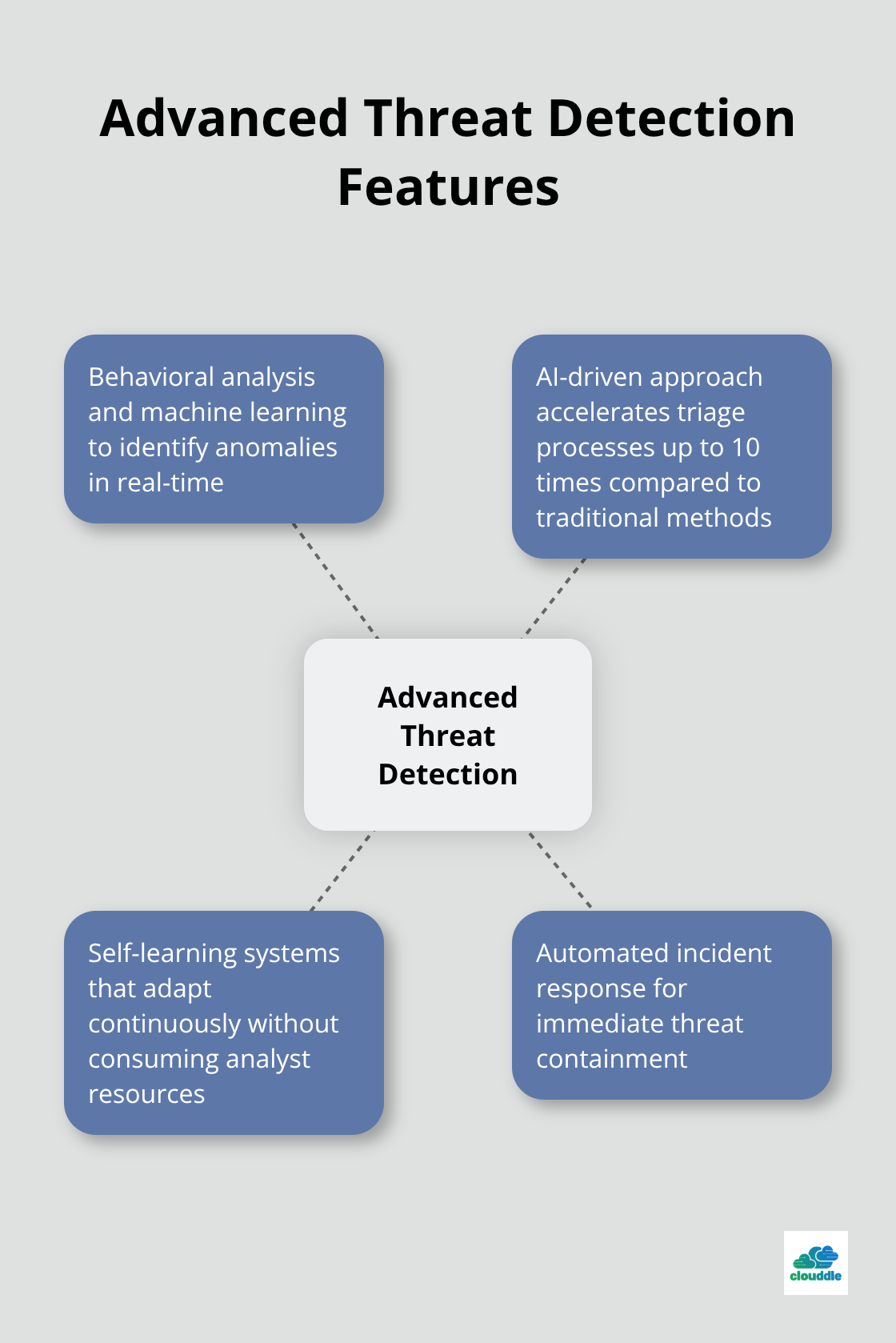
Advanced threat detection forms the backbone of effective managed security, but many providers still rely on outdated signature-based systems that miss zero-day attacks. Look for solutions that use behavioral analysis and machine learning to identify anomalies in real-time. Darktrace’s AI-driven approach has proven to accelerate triage processes up to 10 times compared to traditional methods, while self-learning systems adapt continuously without consuming analyst resources. Your provider should offer automated incident response that contains threats immediately, not just alerts that require manual intervention hours later.
Real-Time Monitoring That Actually Works
True 24/7 monitoring means more than just having staff on duty around the clock. The best managed security providers use Security Operations Centers that process millions of events daily through advanced SIEM systems. These platforms aggregate data from firewalls, endpoints, cloud environments, and network traffic to provide complete visibility. According to Gartner, worldwide end-user spending on information security is projected to total $212 billion in 2025, but only providers with distributed deployment models can apply security policies consistently across data centers, remote sites, and cloud platforms simultaneously.
Scalability Without Performance Penalties
Your managed security solution must scale seamlessly as your business grows, which means you need to evaluate how providers handle increased network complexity. Solutions that require manual configuration changes or additional hardware purchases create bottlenecks that leave you vulnerable during expansion periods. Cloud-based security tools offer superior adaptability because they provide real-time communication between security components across multiple environments. The most effective providers use centralized command and control architectures that allow unified policy management while maintaining performance levels regardless of your network size or geographic distribution.
Integration Capabilities That Matter
Your managed security solution must integrate smoothly with existing infrastructure to avoid operational disruptions. Providers should support multi-cloud and hybrid environments (including AWS, Azure, and on-premises systems) without requiring complete infrastructure overhauls. The best solutions offer APIs and pre-built connectors that work with popular business applications and security tools you already use. This integration capability becomes even more important when you consider that siloed security operations increase response times and create configuration errors that attackers exploit.
These technical capabilities form the foundation of effective managed security, but the provider behind these features determines whether your investment delivers real protection. The next step involves evaluating the companies that will implement and manage these solutions for your business.
How Do You Separate Qualified Providers from Pretenders
The managed security market floods with providers who make bold claims, but actual qualifications separate legitimate companies from operations heavy on marketing. SOC 2 Type II certification represents the gold standard for security service providers and demonstrates audited controls for security, availability, processing integrity, confidentiality, or privacy. ISO 27001 certification adds another layer of credibility, while industry-specific certifications like FedRAMP for government work or HIPAA compliance for healthcare become non-negotiable requirements. Demand to see current certification documents rather than accept verbal assurances, because expired or pending certifications offer zero protection during audits.
Response Speed Determines Breach Impact
Average response times reveal provider capabilities more accurately than marketing materials ever could. Top-tier providers maintain mean time to acknowledgment under 15 minutes for critical alerts, while inferior services often take hours to respond. The 287-day average for breach detection and containment drops dramatically with providers who use AI-driven triage systems that accelerate processes significantly. Request specific response time guarantees in written form, including escalation procedures for different threat levels. Providers who hedge on response commitments or refuse specific timeframes lack confidence in their capabilities.
Contract Terms That Protect Your Interests
Flat-rate pricing models around $500 monthly provide budget predictability, but contract flexibility matters more than initial costs. Avoid providers who demand multi-year commitments without performance guarantees or exit clauses tied to service level failures. The best contracts include specific uptime guarantees above 99.9% with financial penalties for violations. Monthly billing cycles offer more flexibility than annual payments, especially during business changes or provider performance issues.
Service Level Agreements That Actually Matter
Service level agreements must specify response times, resolution timeframes, and compensation for missed targets rather than vague promises about best efforts. Look for providers who guarantee first response within 15 minutes and resolution commitments based on threat severity levels. The most reliable providers offer financial credits when they fail to meet documented response standards. These agreements should cover network availability, threat detection accuracy rates, and incident containment timeframes with measurable penalties for non-compliance.
Final Thoughts
You must balance technical capabilities with provider reliability when you select managed network security solutions. Focus on providers who offer AI-driven behavioral analysis rather than outdated signature-based detection, maintain SOC 2 Type II certification, and guarantee response times under 15 minutes for critical threats. The financial benefits speak clearly: managed services at $500 monthly eliminate the $2,500-$2,800 per employee annual costs of comprehensive in-house security while they provide enterprise-grade protection that most internal teams cannot match.
Professional managed security delivers measurable advantages beyond cost savings. Organizations that use managed services experience significantly lower incident rates and faster threat containment compared to those that rely solely on internal resources. The 287-day average breach detection time drops dramatically with AI-accelerated triage systems, while 24/7 monitoring through advanced SIEM platforms provides complete network visibility that internal teams struggle to maintain.
Implementation success depends on providers who support your existing infrastructure without complete overhauls. We at Clouddle combine networking, security, and managed IT services with flexible contracts and 24/7 support. Start by requesting detailed service level agreements with specific response guarantees, then evaluate integration capabilities with your current systems before you make final provider selections.


