Cyber attacks cost businesses $4.45 million on average in 2023, according to IBM’s Cost of a Data Breach Report. Building a robust IT security management system isn’t optional anymore.
We at Clouddle see organizations struggle with fragmented security approaches that leave gaps attackers exploit. This guide walks you through creating a comprehensive framework that protects your data and meets compliance requirements.
What Makes an IT Security Management System Work
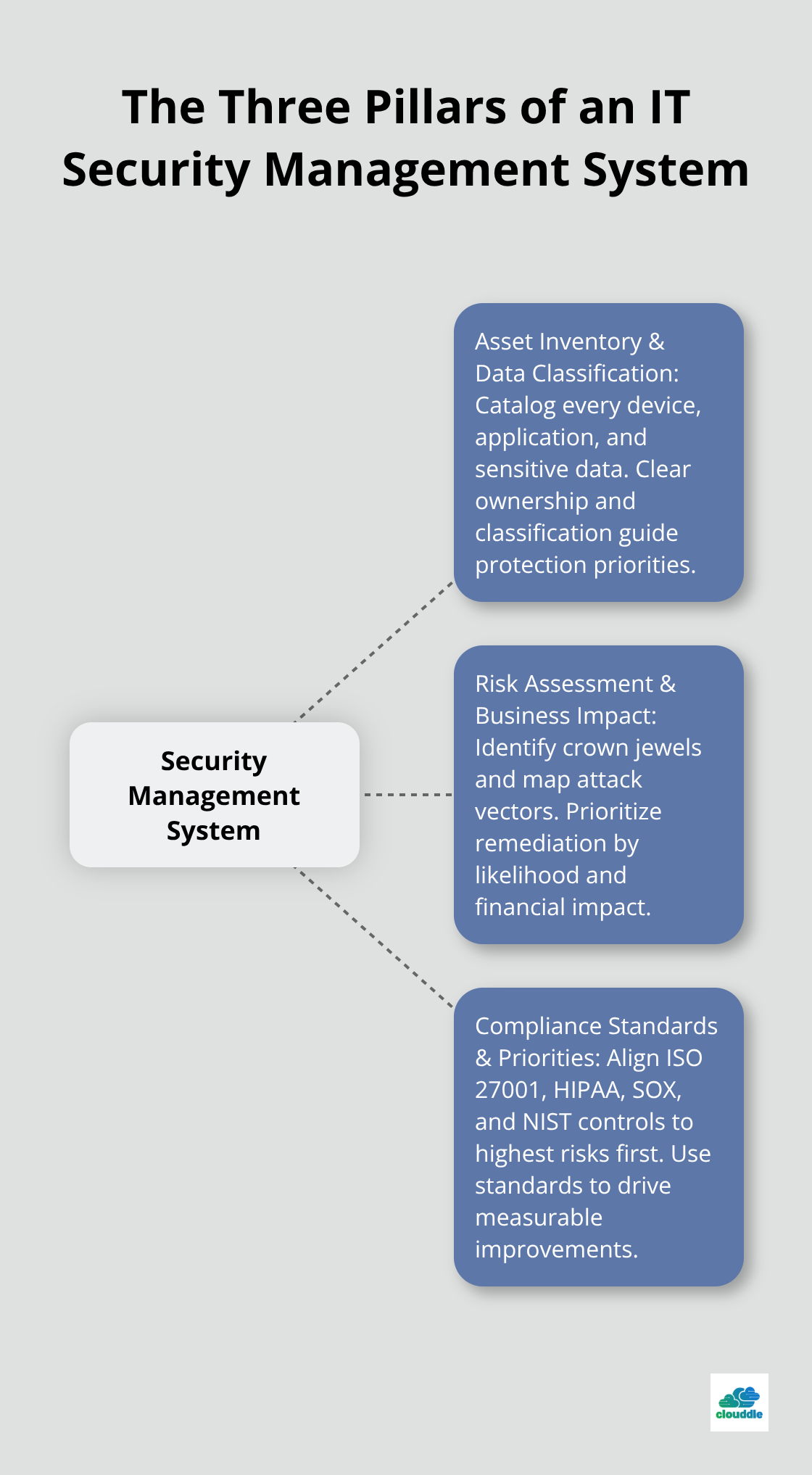
An IT security management system operates through three interconnected pillars that determine whether your organization survives or falls victim to cyber attacks. The foundation starts with comprehensive asset inventory and data classification, where you catalog every device, application, and piece of sensitive information within your network.
Organizations that skip this step face higher breach costs, with average costs increasing 15.3% from USD 3.86 million in recent years.
Asset Inventory Forms Your Security Foundation
Your security policies must address specific scenarios rather than generic guidelines. Cover incident response procedures, access management protocols, and data handling requirements that employees can actually follow. Document every system, application, and data repository with clear ownership assignments and risk classifications. This inventory becomes your roadmap for protection priorities and resource allocation decisions.
Risk Assessment Drives Protection Strategies
Effective risk assessment goes beyond compliance checkboxes and focuses on business impact analysis. Start by identification of your crown jewel assets and map potential attack vectors that could compromise them. Monthly attack volumes have increased from nearly 14 billion at the beginning of 2023 to more than 29 billion by October 2024, which makes vulnerability scans and penetration tests non-negotiable components.
Document every identified risk with specific likelihood ratings and financial impact estimates. Prioritize remediation based on actual business consequences rather than theoretical security scores (this approach delivers measurable protection improvements).
Compliance Standards Shape Implementation Priorities
ISO 27001 certification requires 114 security controls across 14 categories, but smart organizations focus implementation on controls that address their highest risks first. The healthcare sector faces average breach costs of $10.93 million per incident according to IBM, which makes HIPAA compliance just the starting point for comprehensive protection.
Financial services organizations must meet SOX requirements while manufacturers increasingly need to address NIST Cybersecurity Framework guidelines. Your compliance strategy should align with industry-specific regulations while it builds upon foundational standards that provide measurable security improvements.
These foundational elements create the structure for your security framework, but implementation requires specific policies and technical controls that transform theory into protection.
How Do You Transform Security Plans Into Working Protection
Security frameworks fail when organizations treat policy creation as a documentation exercise rather than operational transformation. Your security policies need specific implementation timelines, measurable outcomes, and clear accountability structures that employees can execute without confusion. Organizations with mature security programs spend less on breach recovery according to IBM research, which demonstrates the financial impact of systematic policy implementation.
Document Policies That Drive Action
Write security policies that address specific business scenarios your employees encounter daily. Password policies should specify exact requirements like 14-character minimums with multi-factor authentication for privileged accounts, while data handling procedures must outline step-by-step processes for different information classifications. Access request workflows need defined approval chains with maximum response times of 24 hours for standard requests and 4 hours for emergency access. These concrete specifications eliminate guesswork and reduce security gaps that attackers exploit.
Deploy Multi-Layered Authentication Controls
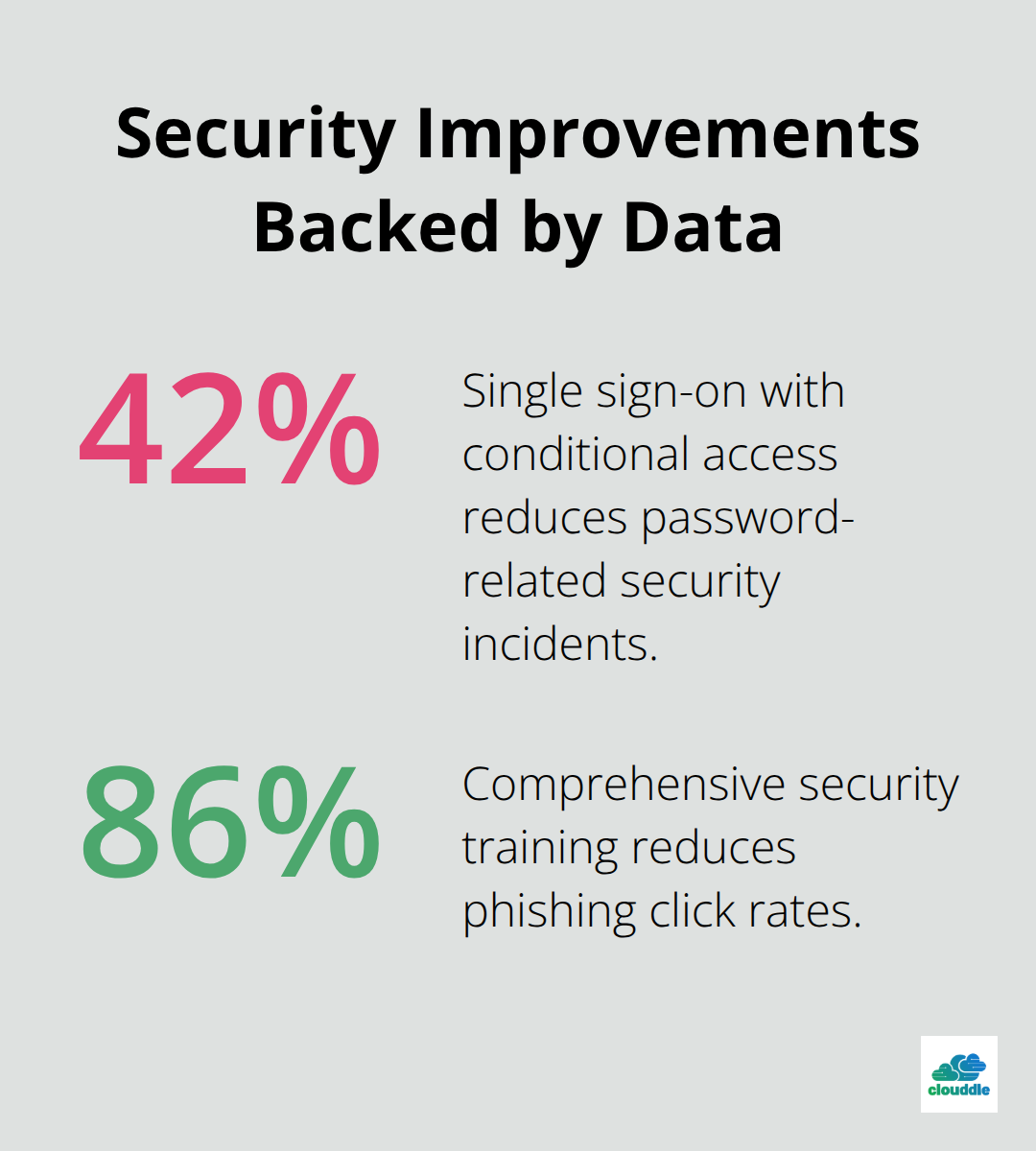
Single sign-on solutions reduce password-related security incidents by 42% when combined with conditional access policies that evaluate user behavior, device status, and location data. Configure privileged access management systems that require approval workflows for administrative functions and automatically revoke elevated permissions after predetermined time periods.
Network segmentation should isolate critical systems with zero-trust principles that verify every connection attempt (regardless of user location or device trust status).
Build Detection Systems That Enable Response
Security information and event management platforms must correlate data from endpoints, networks, and applications to identify attack patterns within minutes rather than days. Configure automated response capabilities that isolate compromised systems, block malicious IP addresses, and notify security teams through multiple communication channels. Organizations with comprehensive monitoring systems can significantly reduce breach identification and containment timeframes according to IBM analysis.
Technical controls provide the foundation, but your security program’s success depends on how well your team understands and executes these protective measures through comprehensive training and awareness programs.
How Do You Execute Security Implementation Without Gaps
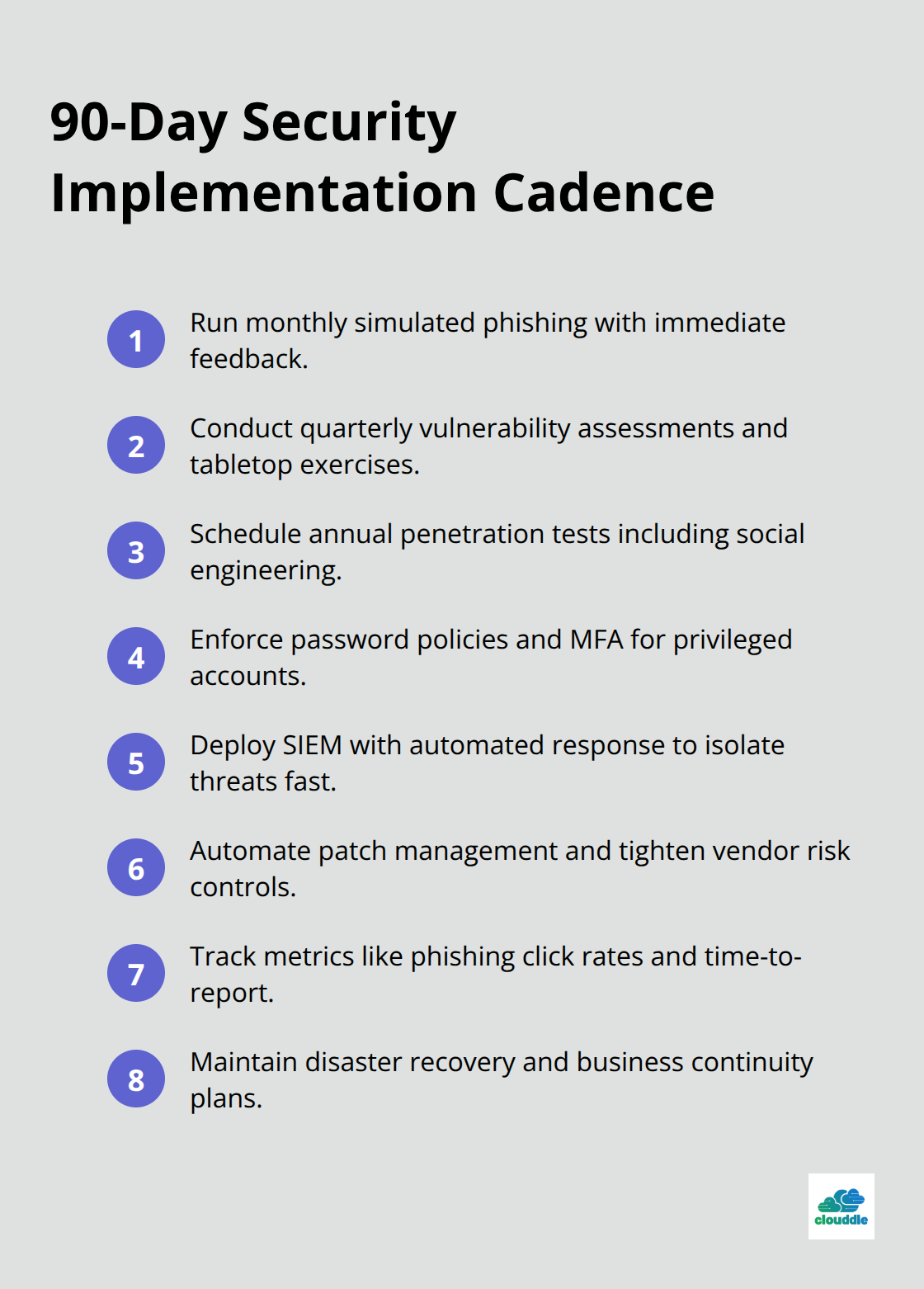
Security awareness programs fail when organizations treat them as annual compliance theater rather than continuous skill development. Effective programs deliver monthly simulated phishing campaigns with immediate feedback loops that teach employees to recognize actual attack patterns. Organizations with mature security programs experience 86% reduction in phishing click rates through comprehensive training, but success requires specific modules that address role-based risks rather than generic cybersecurity overviews.
Target Programs That Change Behavior
Finance teams need specialized sessions on business email compromise scenarios and wire fraud detection, while IT staff require hands-on incident response simulations and threat detection workshops. Schedule quarterly tabletop exercises that simulate realistic attack scenarios specific to your industry and test both technical response capabilities and communication protocols. Track metrics like click rates on simulated phishing emails, time to report suspicious activities, and password policy compliance rates to measure actual behavior changes rather than completion percentages.
Audit Systems That Reveal Real Vulnerabilities
Quarterly vulnerability scans miss critical security gaps that emerge between assessment cycles, while continuous systems identify threats within hours of emergence. Deploy automated patch management systems that prioritize critical vulnerabilities based on exploit availability and business impact rather than generic severity scores. External penetration tests should occur annually with scope that includes social engineering attempts, wireless network assessments, and physical security evaluations that attackers actually use to compromise organizations.
Control Third-Party Risks That Bypass Your Defenses
Vendor security questionnaires provide false security when organizations accept generic compliance certificates without validation of actual security practices. Require vendors to demonstrate specific security controls through live system reviews and mandate contractual obligations for breach notification within 24 hours of discovery. Implement network segmentation that isolates vendor access to only required systems and deploy tools that track all third-party activities for suspicious behavior patterns. Organizations that experience supply chain attacks face average costs of $4.88 million per incident according to IBM research, which makes vendor risk management a business survival requirement rather than compliance checkbox. Establish comprehensive disaster recovery protocols and business continuity planning to ensure operations continue during security incidents.
Final Thoughts
Your IT security management system transforms from concept to protection through systematic asset inventory, risk assessment, and compliance alignment. Organizations that implement structured approaches cut breach costs by millions while they maintain operational efficiency. The foundation demands comprehensive documentation, multi-layered authentication controls, and continuous monitoring systems that detect threats within minutes.
Long-term success requires monthly security awareness programs, quarterly vulnerability assessments, and annual penetration tests that expose actual attack vectors. Your security program must adapt to emerging threats through automated patch management and vendor risk controls that block supply chain compromises.
Regular audits validate control effectiveness while employee programs reduce human error incidents by 86% (according to KnowBe4 research).
Implementation demands dedicated resources and specialized expertise that many organizations lack internally. Clouddle provides managed IT and security services that combine networking, security, and 24/7 support without initial investment requirements. Start with asset inventory and risk assessment this month, then implement authentication controls and monitoring systems within 90 days.


