Cyberattacks cost businesses an average of $4.45 million per breach in 2023, according to IBM’s Cost of a Data Breach Report. Small and medium enterprises face even higher risks, with 60% closing within six months of a major security incident.
We at Clouddle understand that effective IT risk management solutions are no longer optional for modern businesses. The right security framework protects your data, maintains customer trust, and keeps operations running smoothly.
What IT Threats Actually Cost Your Business
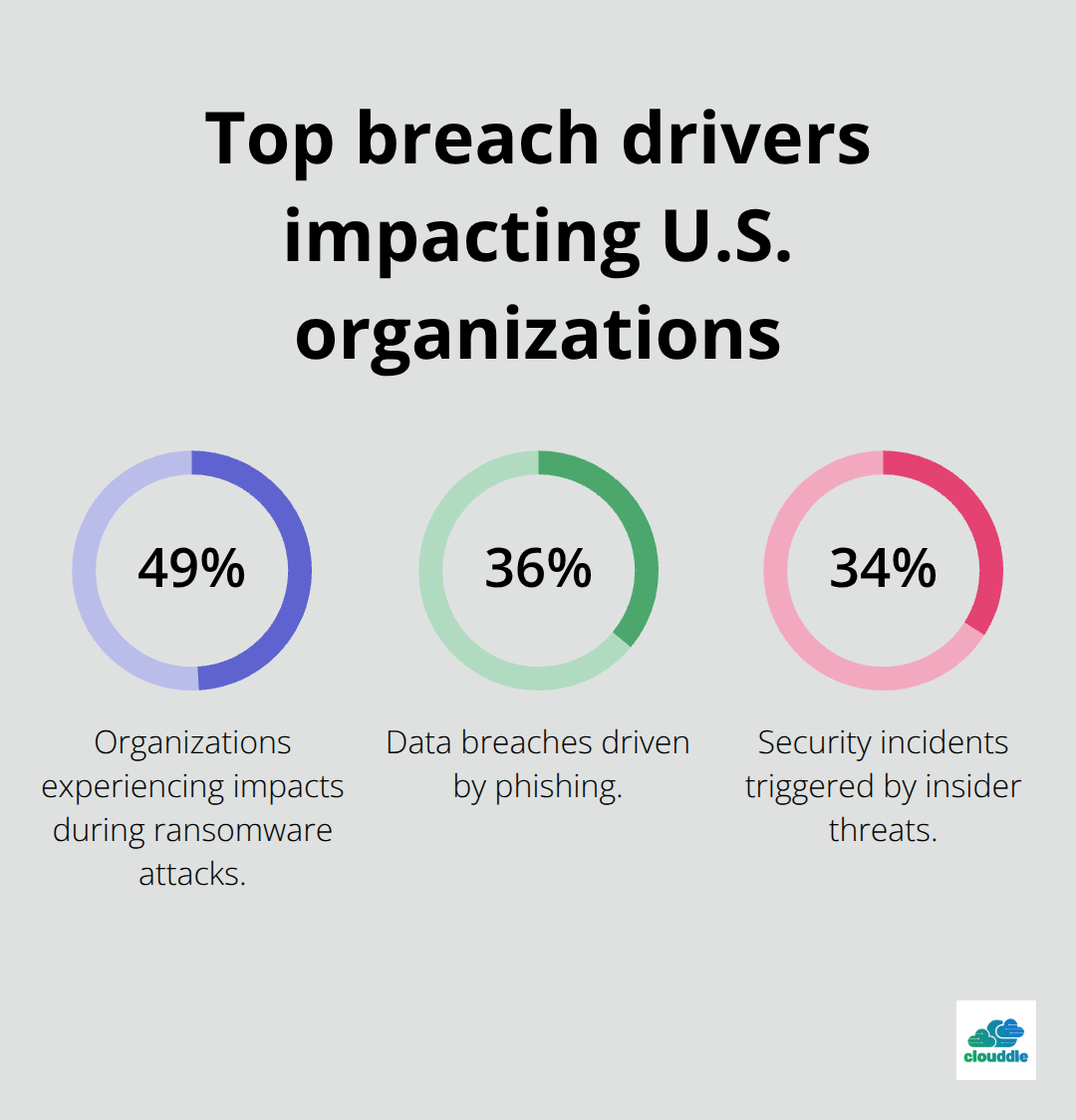
Ransomware attacks have surged significantly, with 49% of organizations experiencing computer impacts during attacks according to Sophos State of Ransomware 2024. Phishing attacks drive 36% of all data breaches, while insider threats trigger 34% of security incidents based on Verizon’s Data Breach Investigations Report.
Human error causes 95% of successful cyber attacks, which makes employee mistakes your most dangerous vulnerability.
The Real Financial Damage Beyond Headlines
The $4.45 million average breach cost represents just the beginning. Manufacturing companies lose $50,000 per minute during downtime, while healthcare organizations hemorrhage $10,900 per minute during system outages (Gartner research shows these staggering numbers). Reputation damage extends costs dramatically – companies see stock prices drop 7.5% on average after major breaches. Recovery spans 287 days typically, during which productivity crashes and customer acquisition costs double. Legal fees, regulatory fines, and notification expenses add another $1.2 million to total breach costs.
Compliance Failures Hit Harder Than Attacks
GDPR violations cost organizations up to 4% of annual revenue, with Meta receiving the largest fine of €1.2 billion in 2023. HIPAA penalties range from $100 to $50,000 per violation, with maximum annual fines reaching $1.5 million per category. PCI DSS non-compliance triggers monthly fines between $5,000 and $100,000 until organizations resolve issues. The Cybersecurity and Infrastructure Security Agency requires incident reports within 72 hours for critical infrastructure, with non-compliance sparking federal investigations. Organizations without proper documentation face penalty rates 300% higher during audits.
Why Traditional Security Approaches Fall Short
Most businesses still rely on reactive security measures that activate only after attacks occur. Perimeter-based defenses fail against modern threats that bypass firewalls through social engineering and compromised credentials. Legacy systems create security gaps that hackers exploit, while fragmented security tools provide incomplete visibility across networks. Organizations need comprehensive solutions that address these evolving challenges proactively.
Essential IT Risk Management Solutions and Strategies
Modern businesses need layered security architectures that work together, not isolated tools that create gaps. Network segmentation reduces breach impact by isolating high-value systems and sensitive information, while next-generation firewalls with deep packet inspection catch 89% more threats than traditional firewalls. Zero-trust network access eliminates the concept of trusted internal networks and forces authentication for every connection attempt.
Organizations should implement application-layer firewalls alongside network firewalls, which creates multiple checkpoints that attackers must bypass. Intrusion detection systems must connect directly to security information and event management platforms for real-time threat correlation and automated responses.
Network Security and Firewall Implementation
Advanced firewall configurations block 94% of network-based attacks when organizations deploy them with proper rule sets and regular updates. Multi-layer firewall architectures prevent lateral movement within networks, while application-aware firewalls inspect traffic at the protocol level. Web application firewalls specifically protect against SQL injection and cross-site attacks (which account for 43% of web application breaches according to OWASP data).
Network access control systems authenticate devices before network entry, while virtual private networks encrypt remote connections. Organizations that implement network monitoring tools detect threats 200 days faster than those relying on manual processes.
Data Backup and Disaster Recovery Plans
The 3-2-1 backup rule remains the gold standard: keeping three data copies on two different media types, with one stored off-site. Organizations that follow this approach recover 95% faster from ransomware attacks compared to those with single backup systems, according to Veeam research. Automated daily backups with hourly incremental saves minimize data loss to under one hour for critical systems.
Air-gapped backups prevent ransomware encryption, while cloud-based disaster recovery reduces recovery time objectives to under four hours. Organizations should test backup restoration monthly, which catches 78% of backup failures before real disasters strike and makes recovery procedures reliable when needed most.

Employee Training and Security Awareness Programs
Simulated phishing campaigns reduce click rates from 32% to 4% within six months when combined with immediate feedback training, based on KnowBe4 data. Role-specific training works better than generic programs – finance teams need wire fraud awareness while IT staff require privilege escalation recognition. Monthly micro-sessions that last 10 minutes each achieve 40% better retention than quarterly hour-long sessions.
Organizations should track metrics like report rates for suspicious emails and time-to-report for security incidents. Security champions programs in each department create peer-to-peer education that scales across large organizations without overwhelming security teams.
These foundational security measures create the framework for protection, but selecting the right technology partner makes the difference between adequate defense and comprehensive security.
Choosing the Right IT Risk Management Partner
Most managed IT service providers promise comprehensive protection, but only 23% actually deliver measurable security improvements according to Gartner research. Organizations need partners who provide specific security outcomes, not generic services. Look for providers who guarantee response times under 15 minutes for critical incidents and offer detailed security metrics reports. The best partners maintain Security Operations Centers with certified analysts who work around the clock, while weaker providers rely on automated systems that miss advanced threats.
Security Certifications That Drive Real Results
SOC 2 Type II certification proves a provider maintains strict data protection procedures, while ISO 27001 certification demonstrates systematic security management practices. CompTIA Security+ certified technicians identify threats faster than non-certified staff. Avoid providers who cannot produce current certifications or refuse to share security audit results. The strongest partners hold multiple certifications such as CISSP, CISM, and vendor-specific credentials from Microsoft, Cisco, and other major technology companies. Organizations should verify certifications directly with authorities rather than accept provider claims at face value.
Why Real-Time Protection Outperforms Scheduled Reviews
Real-time threat detection prevents more security incidents than quarterly security reviews. Effective partners monitor network traffic, user behavior, and system logs simultaneously across all connected devices. They should provide security dashboards that update every five minutes and alert stakeholders within seconds of suspicious activity. Partners who offer only business-hours support leave organizations vulnerable during 128 hours weekly when most cyberattacks occur. The best providers staff their operations centers with security analysts who escalate incidents immediately and coordinate with your internal teams for rapid response.
Vendor Experience and Track Record Validation
Partners with five or more years of security experience handle complex incidents more effectively than newer providers. Request specific examples of how potential partners responded to ransomware attacks, data breaches, and system compromises. Strong candidates provide detailed case studies with measurable outcomes and client references who verify their claims. Organizations should evaluate partners based on their industry expertise – healthcare providers need HIPAA compliance knowledge while financial services require PCI DSS experience. The most reliable partners maintain client retention rates above 90% and can demonstrate consistent security improvement metrics across their customer base.
Final Thoughts
Effective IT risk management solutions combine multiple security layers that work together to protect modern businesses from evolving cyber threats. Network security, comprehensive backup systems, and employee training programs form the foundation of protection, while real-time monitoring and incident response capabilities provide active defense against attacks. Organizations that implement proactive security measures reduce breach costs by 51% and recover 200 days faster from incidents compared to reactive approaches.
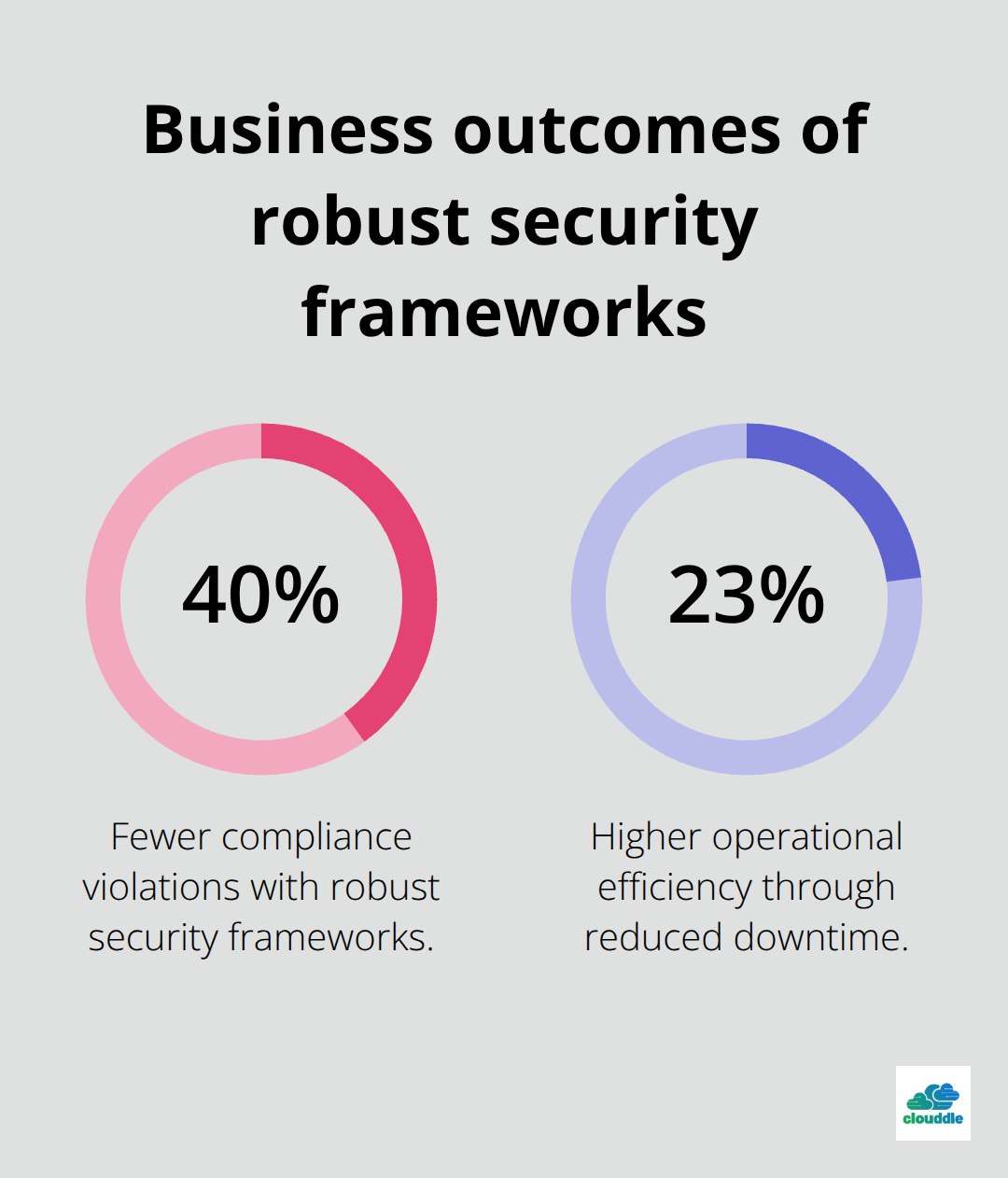
The long-term benefits extend beyond immediate threat prevention. Companies with robust security frameworks experience 40% fewer compliance violations, maintain customer trust during market uncertainty, and achieve 23% higher operational efficiency through reduced downtime (these improvements translate directly to competitive advantages and sustainable growth).
Strong IT risk management solutions create measurable business value that extends far beyond basic protection.
We at Clouddle specialize in comprehensive security solutions that protect businesses across multiple industries. Our approach combines advanced threat detection with proactive risk management strategies. Contact us to assess your current security posture and implement IT risk management solutions that match your specific business requirements.


