Network attacks cost businesses an average of $4.45 million per breach in 2023, making robust security infrastructure non-negotiable. The right combination of security hardware can reduce breach likelihood by up to 80%.
We at Clouddle see organizations struggling to choose from dozens of available types of network security devices. This guide breaks down the most effective options and helps you build a defense system that actually works.
Which Network Security Devices Form Your First Line of Defense
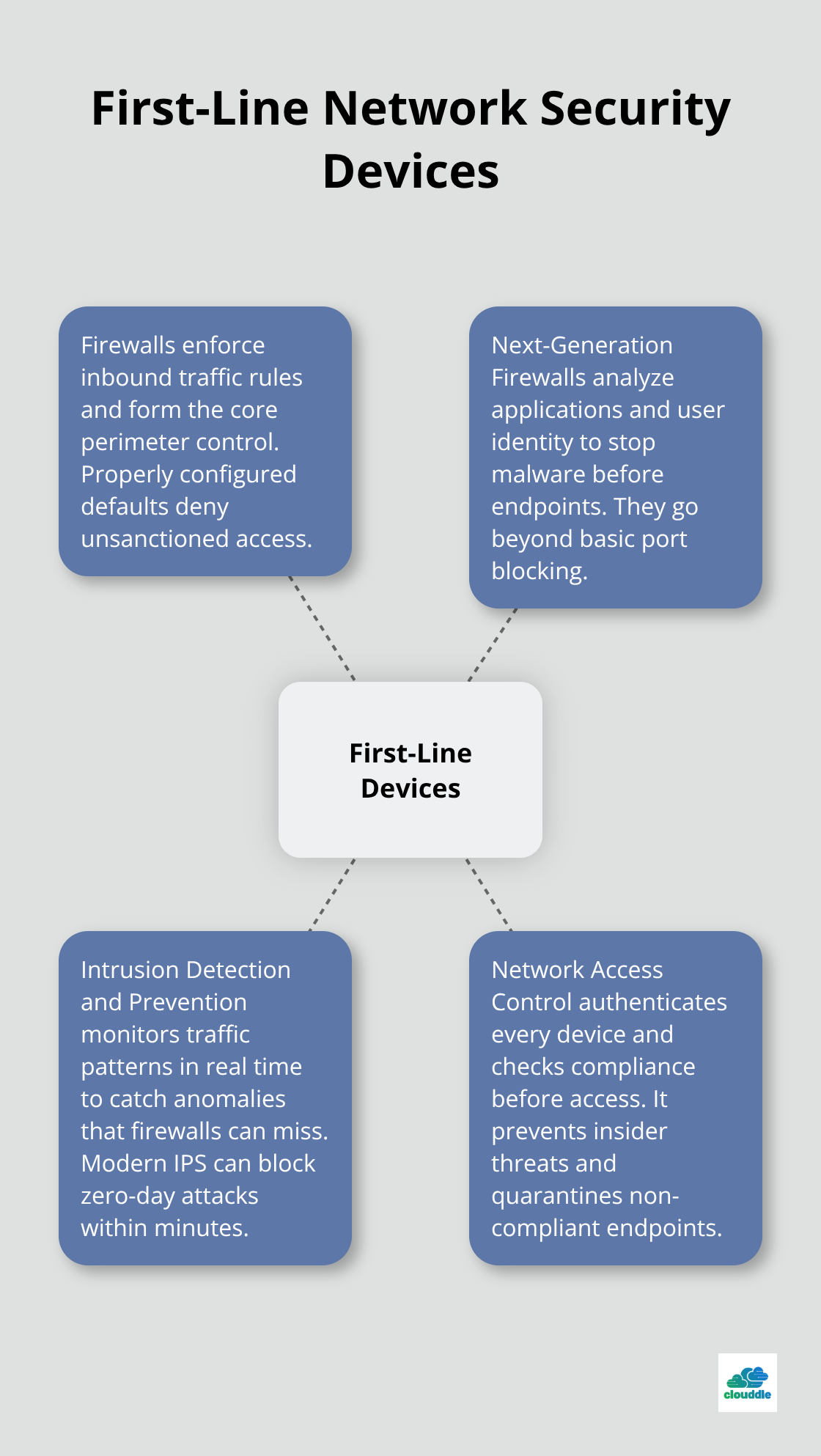
Firewalls stand as your network’s most fundamental security component, processing incoming traffic decisions according to Cisco’s latest cybersecurity readiness assessment. Next-Generation Firewalls go beyond basic port blocking and analyze application behavior plus user identity to stop malware before it reaches your endpoints.
Configure your firewall to deny all inbound connections by default, then create specific rules for business applications. Most successful breaches happen because organizations leave unnecessary ports open or use outdated rule sets that haven’t been updated in months.
Intrusion Detection Catches What Firewalls Miss
Intrusion Detection and Prevention Systems monitor network traffic patterns in real-time and identify anomalies that traditional firewalls cannot detect. Modern IPS solutions block zero-day attacks within minutes of detection through advanced threat intelligence.
Deploy both network-based and host-based IPS for complete coverage. Network-based systems analyze traffic flows, while host-based versions monitor individual device behavior. The combination reduces false positives compared to single-solution deployments.
Network Access Control Stops Insider Threats
Network Access Control systems authenticate every device before network access and help prevent insider threat incidents. The network security market continues growing at 14% annually, reaching an expected $73 billion by 2032. NAC solutions scan device compliance, check security patches, and verify user credentials simultaneously.
Implement 802.1X authentication for wired connections and WPA3-Enterprise for wireless access. This approach blocks compromised devices automatically and quarantines non-compliant endpoints until they meet security standards. Organizations that use comprehensive NAC report fewer security incidents compared to those that rely on basic authentication methods.
These foundational devices create your security perimeter, but advanced monitoring tools take protection to the next level with intelligent threat detection and automated response capabilities.
What Advanced Tools Complete Your Security Stack
Security Information and Event Management systems collect and analyze data from many different sources to detect potential security incidents in real time. SIEM platforms aggregate logs from firewalls, servers, and applications into centralized dashboards that identify attack patterns within minutes.
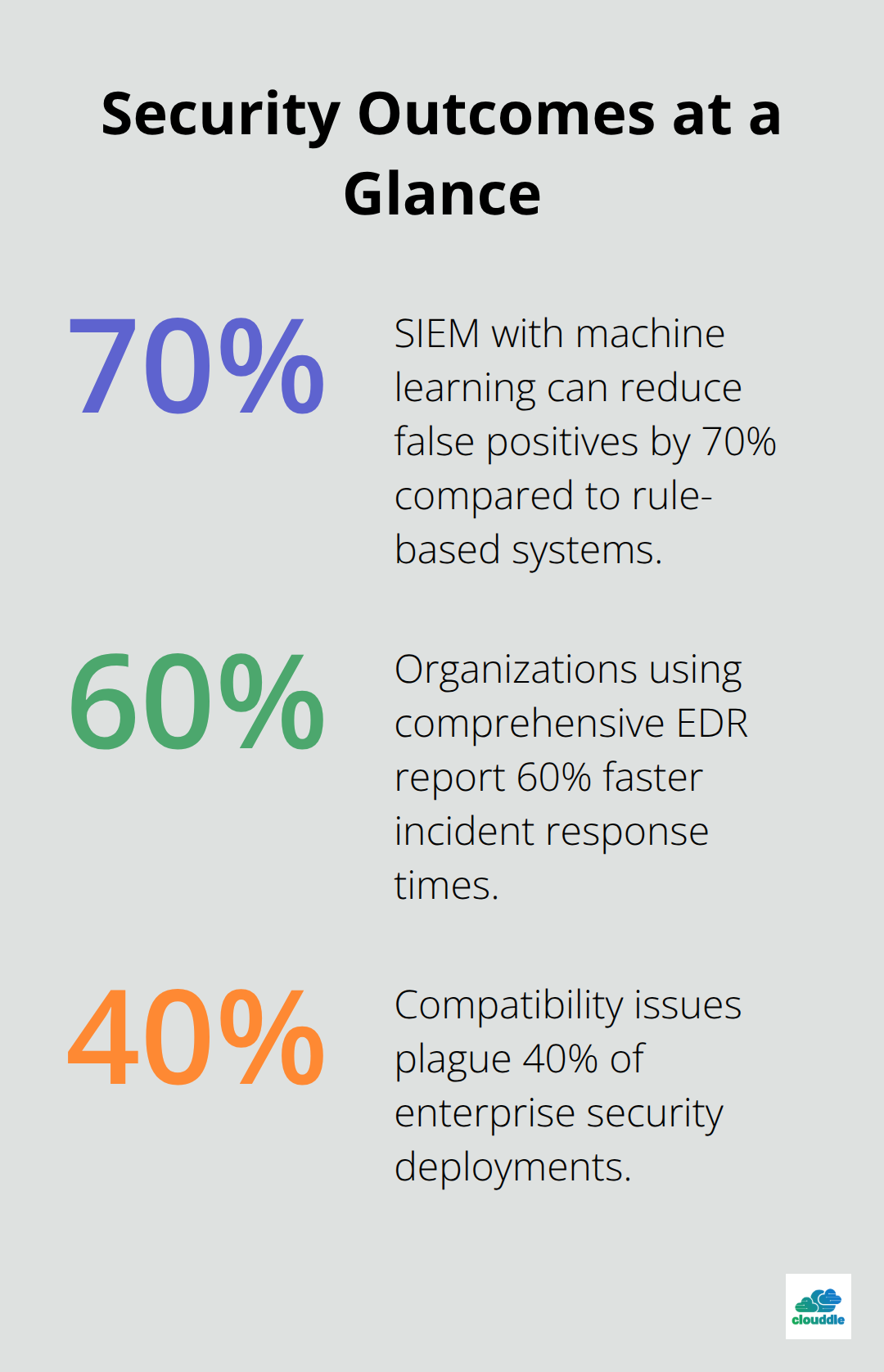
Deploy SIEM solutions with machine learning capabilities that adapt to your network behavior and reduce false positives by 70% compared to rule-based systems. Configure automated incident response workflows that quarantine infected devices and block malicious IP addresses without human intervention.
Network Segmentation Prevents Lateral Movement
Virtual Private Networks and network segmentation devices limit breach damage when they contain threats within isolated network zones. Software-defined perimeters create encrypted tunnels between authorized users and specific applications, which replace traditional VPN architectures that grant broad network access.
Implement zero-trust network segmentation that requires authentication for every connection, even between internal systems. Micro-segmentation provides enhanced security by preventing ransomware from spread across your entire infrastructure.
Endpoint Detection Monitors Every Device
Endpoint Detection and Response solutions monitor workstation behavior in real-time and detect fileless malware that traditional antivirus software misses. Modern EDR platforms use behavioral analytics to identify suspicious processes, network connections, and file modifications across Windows, Mac, and Linux systems.
Set up automated threat hunt protocols that scan endpoints every 15 minutes and maintain detailed forensic records for compliance audits. Organizations that use comprehensive EDR report 60% faster incident response times and significantly lower recovery costs when breaches occur.
Integration Challenges Require Strategic Planning
Advanced security tools create complex integration requirements that demand careful architecture planning. Multiple vendor solutions often conflict with each other (causing alert fatigue and operational inefficiencies). Plan your security stack integration before purchase decisions to avoid compatibility issues that plague 40% of enterprise security deployments.
The selection process becomes more complex when you need to balance advanced capabilities with practical business requirements and budget constraints.
How Do You Choose Security Devices That Actually Work
Start with a comprehensive network audit that maps every device, application, and data flow in your environment. Organizations that conduct thorough assessments before they purchase security hardware can benefit from network automation, with 30% of enterprises expected to automate more than half of their network activities by 2026. Identify your specific vulnerabilities instead of generic solutions that create gaps in coverage. Map user access patterns, document critical assets, and analyze current traffic volumes to determine exact protection requirements.
Calculate Real Security ROI Beyond Purchase Price
Security device costs extend far beyond initial hardware expenses and include license fees, maintenance contracts, staff education, and system integration costs. Enterprise firewall solutions range from $3,000 to $50,000 annually (based on throughput requirements), while SIEM platforms cost between $20,000 and $200,000 per year based on log volume processing. Factor in staff education costs of $2,500 per technician and support contracts that typically add 20% to annual expenses.

Compare these investments against potential breach costs that average $4.88 million per incident. Organizations with comprehensive security stacks report 73% lower breach costs compared to those that use basic protection only. The math becomes clear when you calculate the true cost of inadequate protection versus proper investment in security infrastructure.
Build Compatible Security Architecture From Day One
Plan your entire security ecosystem before you select individual components to avoid integration problems that plague 60% of multi-vendor deployments. Choose solutions with open APIs and standardized protocols like SIEM systems that support REST APIs and SNMP monitoring capabilities. Test compatibility between your firewall, IPS, and endpoint detection systems in lab environments before production deployment.
Security tools from different vendors often conflict with each other and create alert fatigue plus operational blind spots that attackers exploit. Prioritize platforms that share threat intelligence automatically and support centralized management consoles (which reduce administrative overhead by up to 40%). This approach prevents the fragmented security posture that weakens many enterprise networks.
Match Device Capabilities to Actual Threats
Analyze your specific threat landscape before you purchase expensive security hardware that may not address your real risks. Financial services companies face different attack vectors than healthcare organizations or manufacturing facilities. Review industry-specific threat reports and recent breach data to understand which attack methods target your sector most frequently.
Small businesses often waste money on enterprise-grade solutions they cannot properly manage, while large organizations sometimes underestimate their needs and purchase inadequate protection. Size your security devices based on actual network traffic, user count, and compliance requirements rather than vendor recommendations that may oversell capabilities you never use.
Final Thoughts
Organizations that select the right types of network security devices reduce breach costs by 73% while they maintain network performance. The key lies in how you match device capabilities to your specific risk profile rather than purchase generic solutions. Future network security will emphasize AI-driven threat detection and automated response systems that replace traditional hardware appliances.
Zero-trust architectures will become standard practice and require authentication for every network connection. Cloud-native security platforms will offer better scalability and reduced maintenance overhead compared to legacy systems. Start your security implementation with a thorough network assessment that identifies vulnerabilities and traffic patterns across your infrastructure.
Deploy foundational devices like firewalls and intrusion prevention systems first, then add advanced tools based on your specific requirements. Test all integrations in lab environments before production deployment to avoid compatibility issues (which affect 60% of multi-vendor deployments). We at Clouddle help organizations implement comprehensive security solutions through managed IT services that combine networking, security, and support into unified platforms.


