Hyperscale networks power today’s digital infrastructure, but their massive scale creates unprecedented security vulnerabilities. A single breach can cost companies millions and disrupt operations across multiple regions.
At Clouddle, we’ve seen how traditional security approaches fail when applied to hyperscale environments. This guide covers the essential technologies and strategies needed to protect large-scale network infrastructure effectively.
What Makes Hyperscale Networks Different
Hyperscale networks operate at a fundamentally different level than traditional enterprise infrastructure. These systems handle millions of concurrent connections across distributed data centers, with traffic volumes that reach terabits per second. Goldman Sachs predicts a 165% increase in global data center power consumption by 2030, driven primarily by AI workloads that demand unprecedented network capacity. The architecture integrates compute, storage, security, and virtualization into unified systems that can scale horizontally within minutes, often expanding resources by 10x to 50x during peak demand periods.
Security Vulnerabilities at Massive Scale
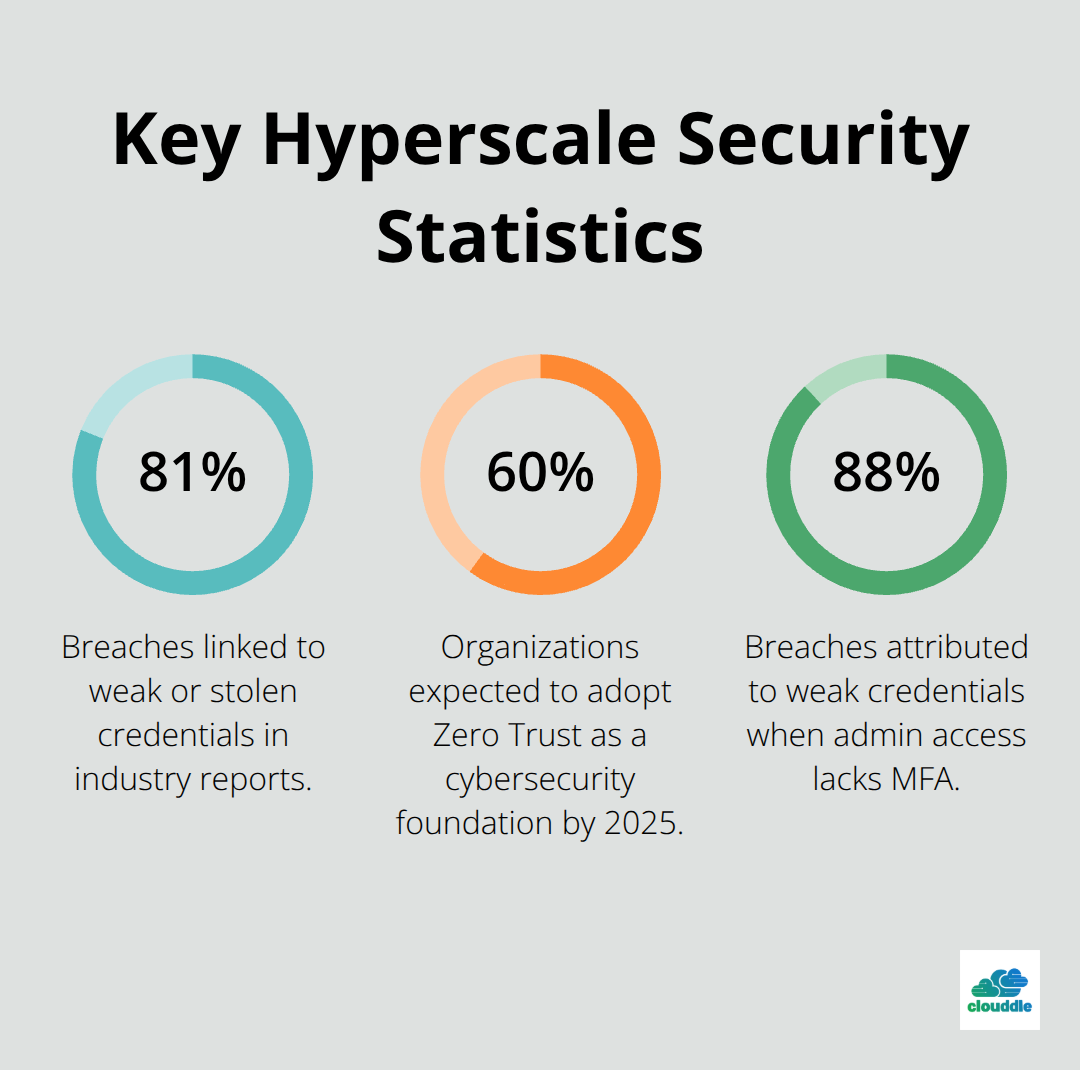
Traditional perimeter-based security fails catastrophically in hyperscale environments. Industry reports show that 81% of data breaches link to weak or stolen credentials, and the attack surface expands exponentially as networks grow. Internal threats become particularly dangerous when a single compromised credential provides access to thousands of interconnected systems. The complexity of managing security policies across multiple data centers creates gaps that attackers exploit through lateral movement techniques.
Business Impact of Hyperscale Security Failures
Security breaches in hyperscale networks cost significantly more than traditional infrastructure failures. Financial institutions require 99.999% uptime to meet regulatory compliance (making even brief outages expensive). eCommerce platforms lose millions during peak traffic periods when security incidents force system shutdowns. The interconnected nature of hyperscale systems means that a breach in one location can cascade across multiple regions, which amplifies business disruption and recovery costs exponentially.
The Scale Challenge for Security Teams
Security teams face unprecedented challenges when they protect hyperscale infrastructure. Traditional security tools cannot process the volume of traffic and events that these networks generate. A single hyperscale data center can produce terabytes of security logs daily, overwhelming conventional analysis methods. Security professionals must monitor thousands of network segments simultaneously while maintaining response times measured in milliseconds rather than minutes.
These unique characteristics of hyperscale networks demand specialized security technologies that can match their scale and performance requirements.
Essential Security Technologies for Hyperscale Networks
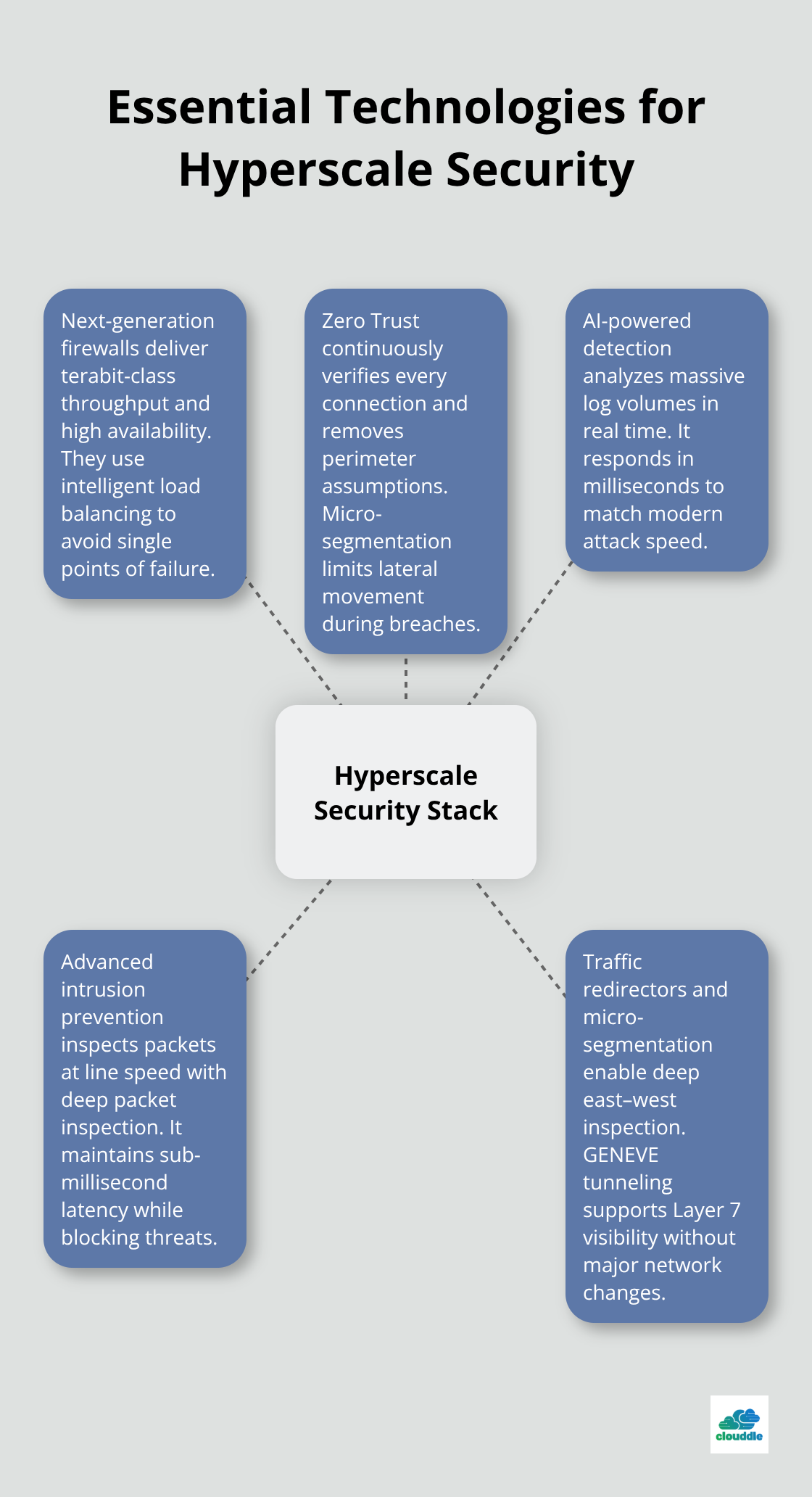
Next-generation firewalls form the foundation of hyperscale security, but conventional models collapse under terabyte-per-second traffic loads. Check Point’s Quantum Maestro system delivers up to 1.5 terabits per second of threat prevention performance, specifically engineered for hyperscale environments. These systems must operate in high-availability clusters of up to five nodes to maintain 99.999% uptime requirements that financial institutions demand. Traditional firewalls create bottlenecks, while hyperscale-ready systems use intelligent load balancing across multiple active units to maximize hardware utilization and prevent single points of failure.
Zero Trust Architecture Eliminates Perimeter Assumptions
Zero Trust architecture has become mandatory for hyperscale networks, with 60% of organizations expected to adopt Zero Trust as the foundation of their cybersecurity by the end of 2025 according to Gartner. This approach assumes breach conditions exist and verifies every connection continuously, regardless of location or user credentials. The National Institute of Standards and Technology recommends Zero Trust for federal systems, and Google’s BeyondCorp model demonstrates its effectiveness at massive scale. Implementation requires micro-segmentation that creates secure zones around individual applications, intra-subnet workload protection, and Layer 7 traffic inspection to prevent lateral movement during breaches.
AI-Powered Detection Matches Attack Speed
Hyperscale networks generate terabytes of security logs daily, which makes human analysis impossible. AI-powered threat detection systems process this volume in real-time and identify patterns that indicate sophisticated attacks like advanced persistent threats and zero-day exploits. These systems must integrate with Security Information and Event Management platforms for centralized monitoring and automated response capabilities. The key advantage lies in speed – AI systems detect and respond to threats in milliseconds rather than the hours or days required for manual analysis (matching the pace at which modern attacks propagate through interconnected systems).
Advanced Intrusion Prevention Systems
Modern intrusion prevention systems must handle the unique challenges of hyperscale traffic patterns. These systems inspect packets at line speed while maintaining sub-millisecond latency requirements that hyperscale applications demand. Deep packet inspection capabilities analyze application-layer traffic to identify threats hidden within legitimate protocols. Integration with threat intelligence feeds provides real-time updates about emerging attack vectors and malicious IP addresses.
Traffic Inspection and Micro-Segmentation
Palo Alto Networks’ Traffic Redirector offers scalable solutions that provide essential deep east-west traffic inspection without hypervisor dependency. The Traffic Redirector module installs on specific workloads and redirects all traffic for inspection through next-generation firewalls. GENEVE tunneling enables deep Layer 7 inspection without significant network changes, while targeted micro-segmentation moves beyond outdated static security models. This approach contains breaches and prevents lateral movement of threats within the environment.
These advanced security technologies work together to create comprehensive protection that scales with network growth, but successful implementation requires careful planning and strategic deployment practices.
How Do You Build Unbreachable Hyperscale Protection
Defense in Depth Architecture
Hyperscale networks demand multiple security layers that operate independently and simultaneously. Network segmentation occurs at three distinct levels: macro-segmentation between data centers, micro-segmentation within applications, and intra-subnet protection for individual workloads. Each layer employs different technologies – perimeter firewalls block external threats, internal firewalls inspect east-west traffic, and endpoint protection monitors individual servers.

The Center for Internet Security mandates security patch application within 72 hours of release, while SANS Institute guidelines require centralized logs through Security Information and Event Management systems. High Availability clusters of firewalls maintain continuous protection during traffic peaks, with load balancing across multiple active units to prevent bottlenecks.
Access Control and Policy Management
Role-based access control delegates management privileges according to specific user needs, which minimizes unnecessary system access. Clean-up rules at policy section endpoints prevent unintended access through overly broad configurations. Multi-factor authentication becomes mandatory for all administrative access (as weak credentials cause 88% of breaches).
Formal change control plans maintain security consistency during policy modifications, with all changes logged and audited through centralized management systems. Configuration backups occur daily, with automated restoration capabilities that minimize downtime during security incidents.
Continuous Threat Assessment
Regular penetration tests reveal policy gaps that attackers exploit, with quarterly assessments recommended for hyperscale environments. Automated vulnerability scanners run continuously across all network segments and generate prioritized remediation lists based on threat exposure. These assessments identify weaknesses before malicious actors can exploit them.
URL filters and application control features on next-generation firewalls allow necessary applications while they block harmful access. Security teams must review firewall logs and audits regularly to track changes and maintain compliance with established security policies.
Employee Security Protocols
Employee security education focuses on hyperscale-specific threats like credential sharing and tailgating, with quarterly updates that cover new attack vectors. Security awareness programs address the unique challenges of large-scale infrastructure (where a single compromised credential can provide access to thousands of interconnected systems).
Staff members receive specific guidance on recognizing social engineering attempts and proper authentication procedures. Regular drills test employee responses to security incidents and reinforce proper protocols for reporting suspicious activities.
Final Thoughts
Hyperscale network security demands specialized technologies that match the unprecedented scale and performance requirements of modern infrastructure. Organizations must deploy next-generation firewalls with terabit-per-second throughput, Zero Trust architecture with continuous verification, and AI-powered threat detection systems that process massive log volumes in real-time. Multi-layered defense strategies that combine macro-segmentation, micro-segmentation, and endpoint protection create comprehensive coverage against sophisticated attacks.
The future of hyperscale network security centers on automated response capabilities and machine learning algorithms that adapt to evolving threats faster than human analysts can process them. As AI workloads drive 165% growth in data center power consumption by 2030, security systems must scale proportionally to maintain protection effectiveness. Organizations that fail to adapt their security infrastructure will face exponentially higher breach costs and operational disruptions.
Implementation success depends on proper planning and expert guidance from experienced security professionals. We at Clouddle specialize in managed IT and security services that help organizations navigate complex infrastructure challenges through comprehensive support and strategic planning. Start with thorough security assessments, implement high-availability firewall clusters, and establish formal change control processes (combined with regular penetration tests and employee training programs to strengthen your overall security posture).


