Network security breaches cost organizations an average of $4.45 million in 2023, making robust infrastructure protection non-negotiable. Implementing Cisco IOS network security PDF guides provides the structured approach needed to build comprehensive defenses.
At Clouddle, we’ve seen how proper implementation transforms vulnerable networks into fortified systems. This guide walks you through every step of the process.
Essential Cisco IOS Security Features
Access Control Lists Protect Network Perimeters
Access Control Lists form the foundation of network protection, with networks without properly configured ACLs being frequent targets of attacks according to security reports. Standard ACLs filter traffic based on source IP addresses while extended ACLs examine source, destination, protocol, and port information. Extended ACLs at network perimeters with deny-any statements at the end provide optimal protection. Named ACLs offer better management flexibility than numbered ones, especially in complex environments with frequent changes.
VPN Technologies Secure Data Transmission
Site-to-site IPsec VPNs protect data transmission between locations through AES-256 encryption and SHA-256 authentication. Remote access VPNs through SSL/TLS connections support concurrent users on enterprise-grade routers. Cisco’s FlexVPN technology simplifies configuration while maintaining security standards. Organizations with properly configured VPNs experience enhanced security compared to those that rely solely on firewall protection.
Authentication Systems Control Network Access
AAA framework implementation reduces unauthorized access attempts when combined with TACACS+ servers. Local authentication works for smaller networks but centralized RADIUS servers handle enterprise-scale deployments more effectively. Multi-factor authentication through RSA SecurID tokens or certificate-based systems adds essential security layers. Network administrators should configure privilege levels from 0 to 15 (with level 15 reserved for full administrative access and levels 1-14 for specific operational tasks).
These security features work together to create layered protection, but proper implementation requires careful planning and systematic configuration steps.
Step-by-Step Implementation Process
Security Assessment Reveals Critical Vulnerabilities
Begin with a comprehensive network inventory that documents every device, interface, and current security configuration. The Cisco Product Security Incident Response Team is aware of attempted exploitation of CVE-2025-20333 and CVE-2025-20362 in network infrastructure. Run security scans with tools like Nessus or OpenVAS to identify weak passwords, outdated firmware, and misconfigured services. Document baseline traffic patterns through NetFlow analysis for at least one week before you implement changes. This baseline becomes essential for detection of anomalies after security deployment.
Map all network entry points including VPN endpoints, wireless access points, and management interfaces. Networks with undocumented access points face higher breach risks according to security research. Create a priority matrix that ranks devices based on criticality and exposure level. Core routers and internet-facing devices require immediate attention while internal switches can follow in subsequent phases.
Core Security Configuration Demands Precision
Configure SSH version 2 with RSA key lengths of 2048 bits minimum (1024-bit keys are considered compromised). Disable Telnet, HTTP, and SNMP version 1 completely on all devices. Set up AAA with TACACS+ servers that use encrypted communication channels.
Local user accounts should serve only as emergency backup with complex 15-character passwords. Enable logs to centralized syslog servers with facility local7 for security events.
Deploy extended ACLs at network perimeters with explicit deny statements for RFC 1918 addresses from external interfaces. Configure Control Plane Protection with rate limits of 100 packets per second for management traffic and 50 packets per second for protocols. Enable Dynamic ARP Inspection on all access switches with DHCP trust relationships properly configured. These settings prevent common network attacks when implemented correctly.
Validation Tests Confirm Security Effectiveness
Execute penetration tests with Metasploit or similar frameworks against newly configured security policies. Successful security implementations should block automated attack attempts within the first test phase. Verify ACL effectiveness when you attempt connections from unauthorized source addresses and confirm proper blocks. Test VPN connectivity from multiple client types and validate encryption strength through packet captures.
Monitor CPU utilization during stress tests as improperly configured security features can consume router processing power. Run sustained traffic tests at 80% of interface capacity while security features remain active. Document all test results and create rollback procedures for configurations that impact network performance beyond acceptable thresholds.
With your security foundation properly tested and validated, the next phase focuses on maintenance practices that keep your network protected against evolving threats.
Best Practices for Ongoing Network Security
Patch Management Prevents Critical Vulnerabilities
Apply security patches within 72 hours of release for internet-facing devices and within one week for internal infrastructure. Cisco releases security advisories through their Product Security Incident Response Team with severity ratings from 1 to 10. Critical patches with ratings above 7 require immediate deployment during maintenance windows. Organizations face significant security challenges when patch management processes are delayed, requiring systematic approaches to address socio-technical challenges.
Test patches in isolated lab environments before production deployment to prevent service disruptions. Create automated patch deployment scripts for non-critical updates while you maintain manual approval processes for core infrastructure changes. Document all patch installations with rollback procedures and validate functionality after each update cycle.
Continuous Threat Detection Systems
Deploy Security Information and Event Management systems that correlate logs from all network devices in real-time. Configure threshold alerts for failed authentication attempts that exceed 10 per hour from single sources and CPU utilization above 80% on critical devices. NetFlow analysis should capture traffic patterns and flag deviations that exceed 25% from baseline measurements within 15-minute intervals.

Incident response teams require documented procedures with contact information and escalation paths clearly defined. Security events categorized as high priority demand response within 30 minutes while medium priority incidents allow 2-hour response windows. Maintain forensic capabilities and preserve log data for minimum 90-day retention periods to support investigation requirements.
Documentation Standards Support Compliance Audits
Network security documentation must include current device inventories, configuration baselines, and change management records updated within 24 hours of modifications. Compliance frameworks like SOC 2 and PCI DSS require evidence of security controls through timestamped logs and configuration archives. Annual security assessments should validate documentation accuracy and identify gaps in coverage or outdated procedures.
Change control processes require approval workflows with technical review and business impact analysis before implementation. Security configuration templates reduce deployment errors and maintain consistency across device types. Backup configurations stored in version control systems enable rapid recovery and provide audit trails for compliance requirements.
Final Thoughts
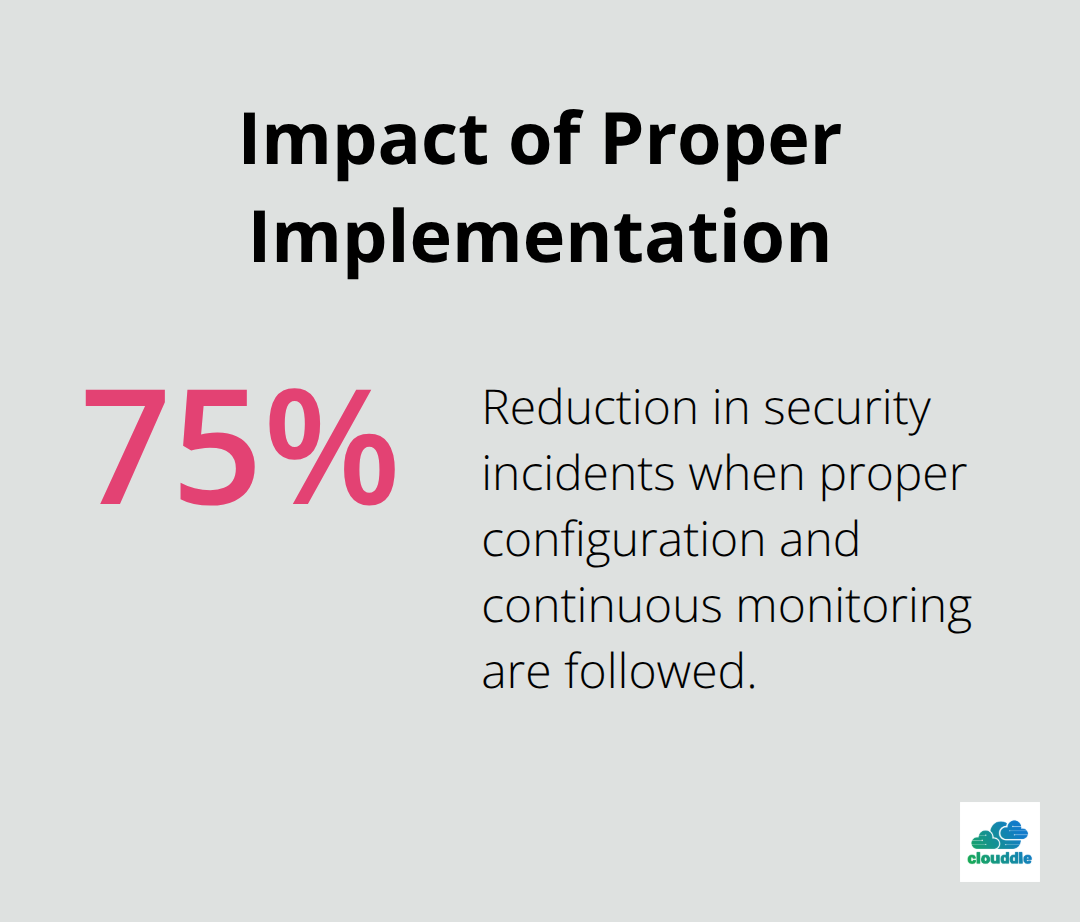
Implementing Cisco IOS Network Security PDF guides transforms vulnerable networks into resilient infrastructures that withstand modern cyber threats. Organizations that follow proper configuration procedures and maintain consistent monitoring practices reduce security incidents by up to 75%. Success depends on comprehensive initial assessment, precise configuration implementation, and ongoing maintenance commitment.
Networks protected through these methodologies experience fewer breach attempts and faster incident resolution times compared to those that rely on basic firewall protection alone. Long-term security effectiveness requires dedicated resources for patch management, continuous monitoring, and regular documentation updates. Organizations that invest in proper security training for their technical teams see significantly better outcomes than those that attempt implementation without adequate expertise.
At Clouddle, we understand that network security demands specialized knowledge and consistent attention (which many organizations lack internally). Our managed IT and security services help organizations implement and maintain comprehensive network protection without the complexity of internal management. Clouddle provides support and flexible solutions that adapt to your specific security requirements while you focus on core business operations.


