Cybersecurity incidents cost companies an average of $4.45 million per breach in 2023, according to IBM’s Cost of a Data Breach Report. The difference between a minor disruption and a business-ending crisis often comes down to preparation.
At Clouddle, we’ve seen how proper cybersecurity incident response can save organizations millions while protecting their reputation. This guide walks you through building and executing a response plan that actually works when seconds count.
What Makes Incident Response So Critical
Cybersecurity incident response represents your organization’s systematic approach to detect, analyze, contain, and recover from security breaches. The National Institute of Standards and Technology defines this process as a coordinated effort that involves preparation, identification, containment, eradication, recovery, and lessons learned. Companies with comprehensive incident response plans save significant costs per breach compared to those without one, according to IBM’s research.
Response Speed Directly Affects Financial Damage
Response time determines your financial impact. Organizations that contain breaches within 200 days face average costs of $3.93 million, while those that take over 200 days see costs balloon to $4.95 million (per IBM’s research). Ransomware attacks alone cost businesses $4.54 million on average, with healthcare organizations that pay the highest price at $10.93 million per incident. Mean time to detect currently averages 207 days across industries, which means attackers operate undetected for nearly seven months. Financial services detect breaches fastest at 233 days, while healthcare lags at 329 days.
Most Common Incidents That Target Organizations
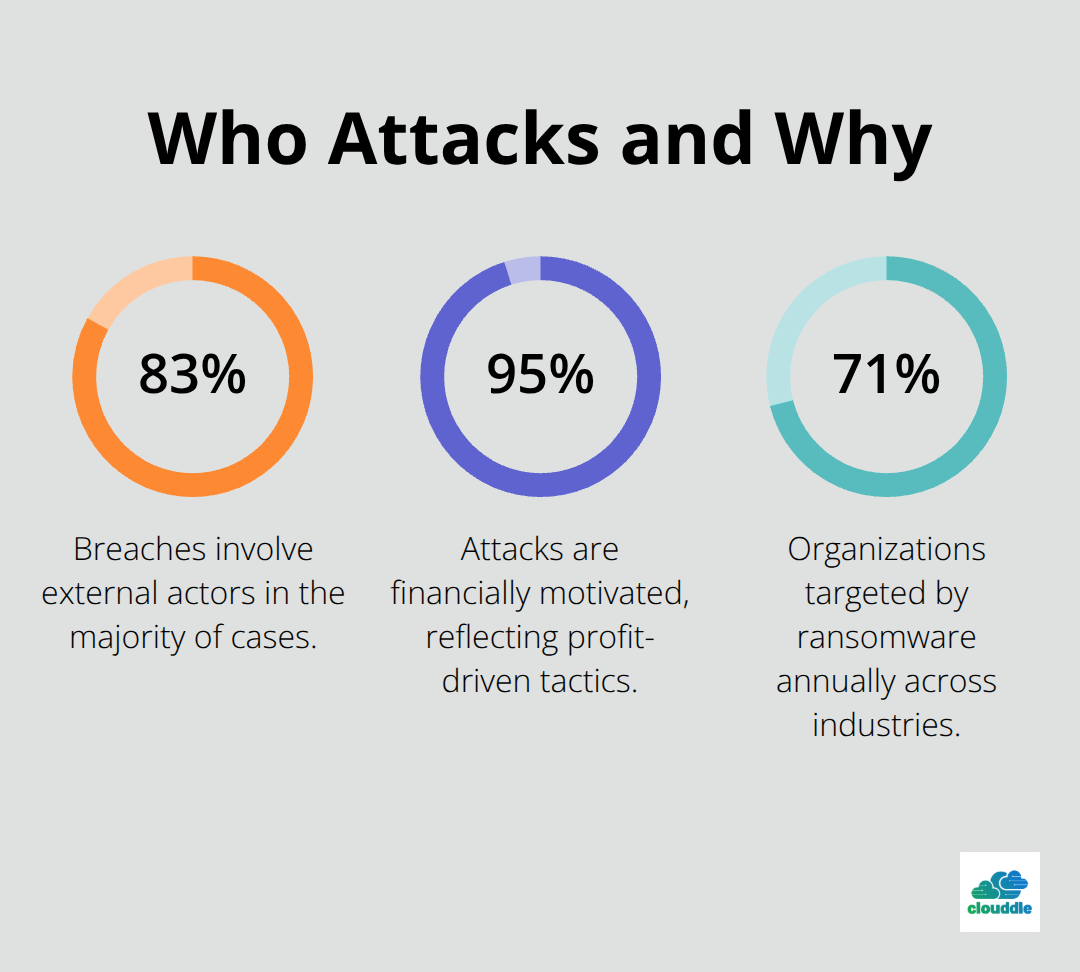
External actors are involved in 83% of breaches, with financial motivation driving 95% of attacks according to Verizon’s research. Ransomware specifically targets 71% of organizations annually, with manufacturing and professional services that get hit hardest. Data theft incidents cost organizations $4.91 million on average when customer personal information gets compromised. Business email compromise attacks average $50,000 per incident but can reach millions when they target large wire transfers or sensitive financial data.
Why Poor Preparation Multiplies Damage
Organizations without formal incident response plans face 30% higher breach costs than those with tested procedures in place. The Department of Homeland Security coordinates national responses to significant cyber incidents, but individual organizations must handle their own initial response and containment efforts. Companies that lack clear communication protocols waste precious hours while attackers expand their access and steal more data. This preparation gap explains why some breaches escalate into company-ending disasters while others become manageable incidents that strengthen security posture.
How Do You Build a Response Team That Works
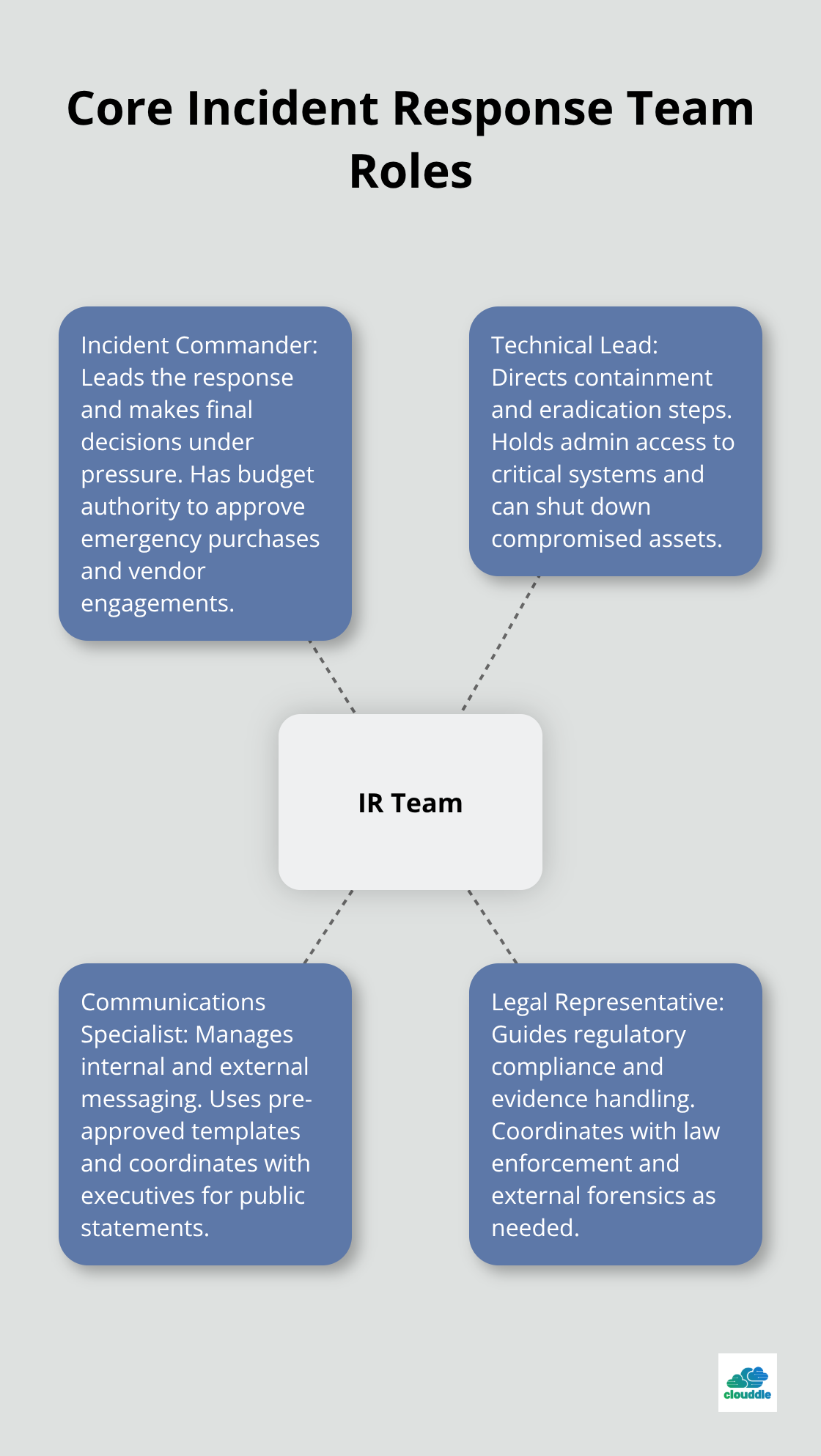
Your incident response team determines whether you contain a breach in hours or watch it spiral into a multi-million dollar disaster. The Cybersecurity and Infrastructure Security Agency recommends specific roles that work together during active incidents. Your team needs a dedicated incident commander who makes final decisions, a technical lead who handles containment actions, a communications specialist who manages internal and external messages, and a legal representative who guides regulatory compliance. Organizations with fully staffed incident response teams experience significant cost savings per breach compared to those with ad-hoc arrangements.
Staff Your Team With Decision Makers
Technical skills matter less than decision-makers when incidents unfold at 2 AM on weekends. Your incident commander must have budget approval powers to authorize emergency purchases, vendor contracts, and overtime expenses without executive approval. The technical lead needs administrative access to all critical systems and the authority to shut down compromised servers immediately. Your communications specialist requires pre-approved message templates for different incident types and direct access to executive leadership for public relations decisions. Legal representatives should have established relationships with law enforcement contacts and external forensics firms before incidents occur.
Create Detection Systems That Actually Alert You
Mean time to detect averages 207 days across industries, which means your current monitors probably miss most attacks. Deploy endpoint detection and response tools on every device that connects to your network (not just servers and workstations). Configure your security information and event management system to correlate events across multiple data sources and reduce false positives that overwhelm security teams. Set up automated alerts for suspicious activities like failed login attempts from unusual locations, large data transfers during off-hours, and new administrative accounts created outside normal business processes.
Train Employees to Spot Threats Early
Employees often serve as your first line of defense against social attacks and suspicious activities. Train staff to report suspicious emails, unusual system behavior, and social attempts through a dedicated security hotline that bypasses normal IT support channels. Provide regular awareness sessions that cover current attack methods (like business email compromise and phishing campaigns). Test employee responses through simulated phishing exercises and reward those who report suspicious activities promptly.
Once you establish your response team and detection capabilities, you need clear procedures that guide your team through the chaos of an active incident.
How Do You Execute Response When Seconds Count
Your first 30 minutes determine whether you contain a breach or watch it spread across your entire network. Organizations that implement immediate containment procedures can significantly reduce breach costs, as the average global breach cost has reached $4.88 million according to IBM’s 2024 research. Start containment within one hour of detection and isolate affected systems from the network without powering them down completely, which preserves volatile memory for forensic analysis. Document every action your team takes with timestamps and personnel involved, as this information becomes evidence for insurance claims and regulatory investigations.

Contain the Threat Without Destroying Evidence
Network segmentation saves both money and evidence during active incidents. Disconnect compromised systems at the network switch level rather than shut down servers, which maintains system state for forensic analysis while preventing lateral movement. Change all administrative passwords immediately and revoke access tokens for affected accounts, but preserve original authentication logs before you make changes. Monitor network traffic for data exfiltration attempts and block suspicious outbound connections to known command-and-control servers. Effective incident response plans should include processes for evidence preservation and compliance reporting to avoid business risks.
Collect Evidence That Holds Up in Court
Digital forensics requires specific procedures that maintain evidence integrity for legal proceedings and insurance claims. Create bit-for-bit copies of affected hard drives with write-blocking tools before any analysis begins, as modified systems become inadmissible in court. Capture network packet data, system logs, and memory dumps within the first four hours when volatile evidence still exists in RAM. Document the chain of custody for all evidence with signatures, timestamps, and storage locations that meet legal standards. External forensics firms like CrowdStrike and FireEye charge $300-500 per hour, but their certified procedures often recover evidence that internal teams miss.
Restore Operations Without Reintroduction of Vulnerabilities
Recovery plans determine whether you bounce back in days or remain vulnerable for months. Rebuild compromised systems from known-clean backups rather than attempt to clean infected machines, which reduces reinfection risk from 60% to under 5% based on Verizon research. Test all restored systems in isolated environments before you reconnect them to production networks, and implement additional monitoring for at least 90 days post-incident. Update security patches, change default configurations, and strengthen access controls before you bring systems back online to prevent immediate recompromise.
Final Thoughts
Effective cybersecurity incident response separates organizations that recover quickly from those that face devastating losses. Companies with tested response plans save an average of $1.76 million per breach compared to those without formal procedures. Your response team needs decision-makers with budget authority, not just technical experts who lack authority to act during critical moments.
Detection systems must alert within hours, not the industry average of 207 days that allows attackers to operate undetected. Test your incident response plan quarterly to reveal gaps before real attacks exploit them. The SANS Institute recommends tabletop exercises that simulate realistic attack scenarios with your actual team members.
We at Clouddle help organizations build robust cybersecurity incident response capabilities through our comprehensive technology solutions. Our managed security services and 24/7 support help prevent incidents and respond effectively when cyber threats target your organization. Strong incident response capabilities protect your business continuity and reduce financial impact when security breaches occur.