The physical installation of an access control system—the part with the drills and wiring—is what most people see. But the real work, the foundation for a successful project, happens long before anyone picks up a tool.
A great system deployment comes down to meticulous upfront planning, a thorough site assessment, and a deep, practical understanding of your security goals and how people actually use your space. Skipping this first phase is the single biggest reason projects go sideways and fail to deliver.
Laying the Groundwork for a Flawless Installation
A well-designed access control system should feel effortless for authorized users and be a formidable barrier to threats. Getting there isn't magic; it's the result of a strategic process that starts with big-picture goals and drills down to the smallest on-site details. This is where you define the scope, anticipate roadblocks, and make sure the technology you choose fits your day-to-day operational reality.
The demand for these systems is surging for a reason. The global access control market is on track to grow from USD 19.05 billion in 2025 to a staggering USD 61.31 billion by 2035. That explosive growth shows just how essential robust access management has become for all types of properties.
Defining Your Access Control Requirements
Before you even look at a single piece of hardware, you need to map out precisely what you need the system to do. This is about more than just counting doors and users. It’s about understanding the flow of people through your building and pinpointing the unique security weak spots in your environment.
Start by asking the right questions:
- Who needs access? Break down everyone into groups: employees, residents, management, vendors, guests, cleaning crews. Then, define exactly where each group is allowed to go—and where they aren’t.
- When do they need access? Think about time-based rules. Should office staff only have access during business hours? Do residents need 24/7 access to the gym or package room?
- What’s the main goal? Is it primarily to stop unauthorized people from getting in? Or is it more about tracking movement for compliance, protecting specific high-value assets, or simply making life easier for tenants?
The answers will shape your entire system. For a multi-family building, the focus is often on secure, easy access for residents while managing guests and deliveries. In a commercial office, the priority might be locking down a server room and creating an audit trail of who went where and when.
Conducting a Thorough Site Survey and Risk Assessment
Once your goals are clear, it's time to walk the site. This isn't just a quick look-around; it’s a critical physical evaluation of your building's layout, existing infrastructure, and potential security vulnerabilities. You need to think beyond the doors and analyze the entire environment.
A proper site survey isn't just about counting doors. It's about understanding the human element—how people naturally move through a space—and identifying the environmental factors that could impact hardware performance and longevity.
During your walkthrough, zero in on these details:
- Entry Points: Map out every single primary, secondary, and emergency exit. Make a note of which doors see heavy traffic and which are rarely used.
- Environmental Factors: Will a reader be blasted by direct afternoon sun, exposed to salt air, or battered by rain? These conditions will dictate the type of hardware you need. A standard indoor reader won't last long outside.
- Door and Frame Conditions: Check the material and state of every door and its frame. A heavy steel door requires a completely different lock and power supply than a sleek glass door in the lobby.
This whole process can be boiled down to three simple, logical stages.
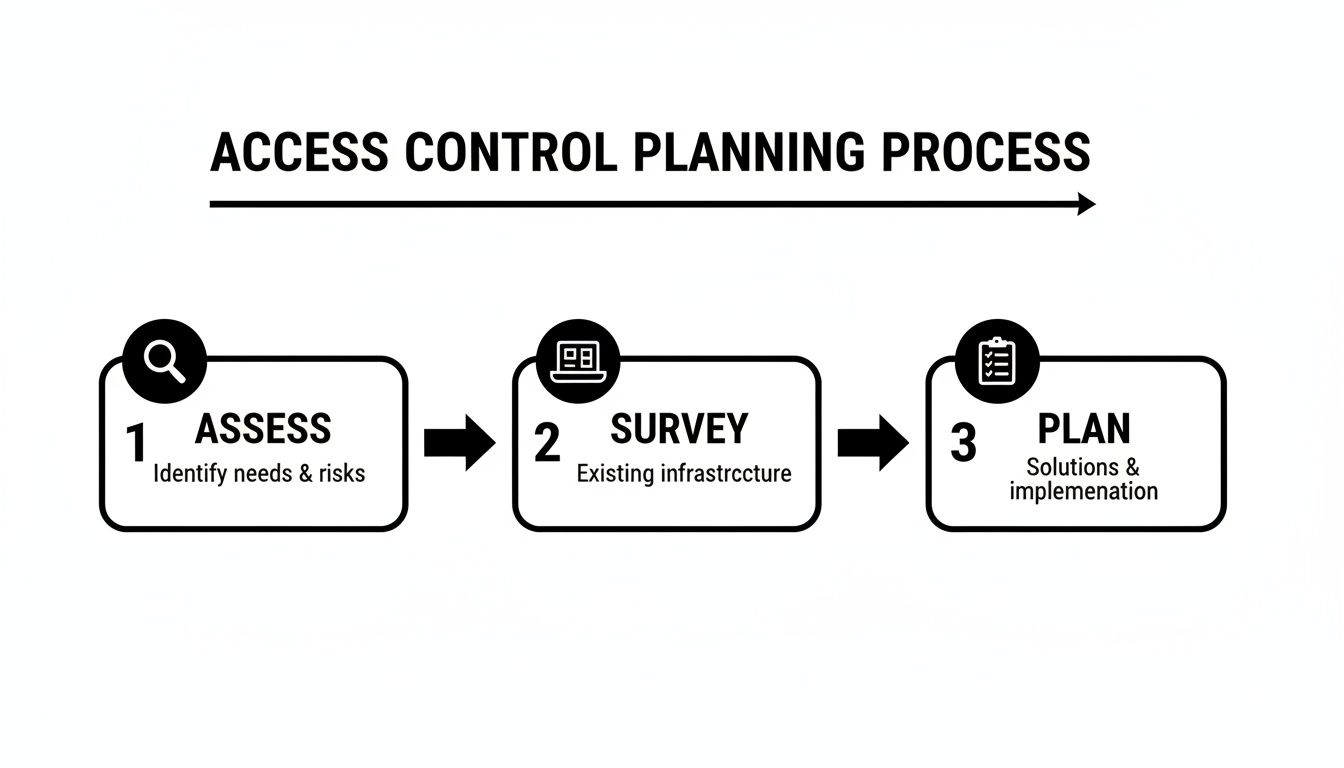
The chart drives home a crucial point: you must assess your needs and survey the site before you start making any concrete plans or buying equipment.
Planning for an access control system also means planning for safety. Understanding modern workplace safety programs can offer valuable insights for protecting both the installation crew and the people who will use the system every day. This systematic approach turns a daunting project into a series of manageable steps, reducing surprises and ensuring the final system is a perfect fit for your property.
To help visualize how these planning needs differ across property types, here's a quick comparison.
Access Control Planning Checklist for Different Environments
| Consideration | Commercial Office | Hospitality (Hotel) | Multi-Family Residence |
|---|---|---|---|
| Primary Goal | Asset protection, audit trails, employee safety | Guest convenience, security, operational efficiency | Resident safety, convenience, amenity management |
| User Types | Employees, visitors, vendors, cleaning staff | Guests, staff, management, event attendees | Residents, guests, staff, delivery personnel |
| Access Schedules | Business hours for most; 24/7 for IT/security | Tied to reservation dates; 24/7 for staff | 24/7 for residents; scheduled for amenities/staff |
| High-Traffic Areas | Main entrance, elevators, specific department doors | Lobby, elevators, gym, pool, guest room floors | Main entrance, parking garage, mailroom, amenities |
| Key Integration Needs | HR database, video surveillance, alarm systems | Property Management System (PMS), elevators | Intercoms, visitor management, package lockers |
| Credential Type | Key fobs, mobile credentials, ID badges | Mobile keys, key cards (often temporary) | Mobile credentials, fobs, keypads |
This checklist highlights why a one-size-fits-all approach to access control never works. Each environment has its own unique rhythm and set of risks that demand a tailored plan.
Picking Your System's Brains and Brawn: Architecture and Hardware
Okay, you've done your homework. You know what you need, and you've walked the property. Now for the fun part: deciding on the actual technology that will run your access control system. This really boils down to two huge decisions. First, what’s the brains of the operation—a cloud-based or an on-premise system? Second, what’s the brawn—the physical hardware people will use at every door?
Getting the hardware right is absolutely critical; it's the foundation of your entire security setup. There's a reason the hardware side of the market is projected to command a massive 56% share by 2035. As security concerns grow, organizations are doubling down on reliable, physical devices at their entry points. The surge in installations, particularly in places like the United States, is a direct response to new threats and regulations, which just goes to show how much is riding on these choices. If you're curious, you can read more about these access control market trends and see where the industry is heading.

Cloud vs. On-Premise: Where Does Your System Live?
Think of your system's architecture as its central nervous system. The big question is whether you want it on-site or in the cloud. A traditional on-premise solution means you own and manage everything locally—the servers, the software, all of it.
With an on-premise setup, you have direct, physical control over your data, which some people prefer. The flip side is that you’re on the hook for everything. That means a hefty upfront cost for servers, needing dedicated IT staff for maintenance, dealing with manual software updates, and having very limited (if any) ability to manage the system when you're off-site.
A cloud-based system completely changes the game. It takes all that responsibility off your plate. You manage everything through a simple web browser or a mobile app, software updates happen automatically in the background, and you can ditch that bulky server closet for good. For any business that needs to scale or manage multiple properties, the flexibility of the cloud is simply unmatched.
The real magic of cloud architecture is centralized control. Picture this: a property manager can instantly kill access for a departing employee or issue a new key to a tenant right from their phone, whether they’re standing in the lobby or on vacation a thousand miles away. That kind of remote power is a massive boost to efficiency.
This also ties into the financial side of things. Clouddle's Network-as-a-Service, for instance, pairs perfectly with a cloud model. It gets rid of the huge capital expense and turns it into a predictable operating cost. This zero-capex model makes top-tier security accessible without needing to drain your budget upfront.
Getting Hands-On: Selecting Hardware and Credentials
With your architecture decided, it’s time to choose the hardware for your access points. Your goal here is to find the perfect match between security needs and user convenience for every single door.
Common Hardware and Credential Choices
- Key Cards and Fobs: These are the reliable workhorses of the industry. They use RFID or NFC technology and are a fantastic, cost-effective choice for main entrances, amenity rooms, and office suites. They’re a breeze to issue, and just as easy to deactivate if one gets lost. We have a detailed guide that can help you pick the best key card readers for your business.
- Mobile Credentials: Using a smartphone as a key is quickly becoming the new normal. It's incredibly convenient for users, and for you, it means no more money spent on replacing lost plastic cards. This is a perfect fit for multi-family buildings and modern corporate offices where everyone has a phone.
- Biometrics: When you have a truly sensitive area—think a server room, a pharmacy, or an executive office—biometrics are the way to go. Fingerprint or facial recognition readers offer the highest security you can get. You can't lose, steal, or share a fingerprint, which means you know with 100% certainty who is walking through that door.
Think about how this plays out in a real-world setting, like a senior living facility. You might use simple key fobs at the main entrance so residents have something easy to handle. For staff offices, mobile credentials on their phones would be more convenient and provide better tracking. But for the medication storage room? That’s where you’d install a biometric fingerprint reader to ensure access is tightly controlled and fully auditable. This layered strategy makes sure you have the right security in all the right places.
Getting Power and Cabling Right
Think of your access control hardware as the face of the system. The wiring? That’s its lifeblood. It's the circulatory system delivering the essential power and data that keeps everything running. I've seen too many projects stumble because the team skimped on this phase, leading to intermittent failures and endless troubleshooting down the road.
The underlying infrastructure is what connects the main controller to the reader at the farthest door. This means you really need to get your head around the cabling options before you pull a single wire.
The Great Cabling Debate: Modern vs. Traditional
For most modern setups, standard structured network cabling—like Cat6—is the way to go. It's versatile, easy to find, and handles both data and power, which makes the whole installation a lot simpler. If you want to dive deeper, we have a complete guide on what is structured cabling.
On the other hand, you might run into older or highly specialized systems that use multi-conductor security wire. It works, sure, but it’s far less flexible. You usually end up running separate cables for power and data, which adds a layer of complexity and cost. For any new commercial or multi-family installation, I almost always recommend a unified Cat6 approach. It's just cleaner and more efficient.
The technology that really makes this possible is Power over Ethernet (PoE).
PoE is an absolute game-changer for installers. It lets you send low-voltage power and data over a single Ethernet cable. This means you don't need an electrician to run separate power to every single door reader and lock, which drastically cuts down on both labor and material costs.
This single-cable approach doesn't just make the physical install easier; it also creates a much tidier, more organized setup. Better yet, you can centralize your power source at the network switch, which simplifies managing battery backups immensely.
Building a Rock-Solid Power Distribution Plan
For any security system, consistent and clean power is completely non-negotiable. Every controller, reader, and electronic lock needs an uninterrupted power source to do its job. That’s where a centralized power distribution strategy is critical.
- Go Central with Power Supplies: Ditch the individual power adapters at each door. The best practice is to use a centralized power supply unit (PSU) with a solid battery backup. This ensures that if the building's power goes out, your access control system stays online and keeps the property secure.
- Protect Your Cable Runs: How you run your cables is just as important as what cables you use. Always route wiring through conduits or other secure pathways. This protects them from being tampered with, accidentally cut, or getting signal interference from nearby high-voltage lines. A pro tip: never run your low-voltage security cables parallel to electrical wiring if you can avoid it.
A stable power supply is absolutely fundamental, making Choosing the Right Power Supply SMPS a decision you need to get right for long-term performance.
This focus on solid infrastructure is a big reason why North America currently holds a 36.4% revenue share of the global access control market. This growth is driven by smart installations in commercial, healthcare, and government facilities. The market itself is projected to jump from USD 10.62 billion in 2025 to USD 15.80 billion by 2030.
Ultimately, your power and cabling plan is the unseen hero of the entire project. It's what guarantees every component can talk to each other and stays online when it matters most.
A Practical Guide to Installation and Configuration
Now we get to the hands-on part. With all your planning done and hardware in hand, it's time to physically install the access control system and configure the software that makes it all work. This is where your careful prep work really starts to pay off, turning those blueprints and checklists into a secure, functioning reality. It's a methodical process, moving from mounting the hardware to connecting the wiring and finally, programming the system's brain.
This kind of work is happening everywhere. While North America still holds the largest market share, the Asia Pacific region is growing the fastest, thanks to massive urbanization in countries like China and India. Smart city initiatives there are driving demand for millions of new access points, pushing the global market toward a projected USD 11.56 billion by 2025. We're seeing this boom firsthand in new co-working spaces and high-rise residential buildings, which are adopting cloud-based systems at a breakneck pace.
Mounting and Positioning Your Hardware
The first step on-site is getting the core components mounted at each door. This means the reader, the electric lock, and any related sensors or exit buttons. Getting the placement right is about more than just looks—it directly impacts how easy the system is to use and how secure it is.
For instance, the reader needs to be at a comfortable height on the unsecured side of the door, typically following accessibility standards. The lock, whether it’s an electric strike or a powerful maglock, has to be fitted perfectly to the door and frame. A misaligned lock is a huge security hole waiting to be exploited.
A seasoned installer's secret weapons are a good set of drill templates and a level. For a glass door, using the right adhesive is non-negotiable. With a heavy steel door, you have to be certain the frame can handle the force of a maglock without warping over time. These details matter.
Always think about the person using the system. Is the reader easy to reach for someone in a wheelchair? Is the push-to-exit button obvious and intuitive? These small details make a massive difference in daily operations. For a deeper dive into hardware specifics, our guide to commercial security systems installation is a great resource.
Connecting the Wires
With the hardware securely in place, it’s time to run the wiring back to the access control panel. This is probably the most critical part of the physical install. A clean, organized wiring job is a gift to your future self—it makes troubleshooting a breeze. A "rat's nest" of cables, on the other hand, is a nightmare of intermittent faults just waiting to happen.
Each component has its own wiring needs:
- The Reader: Usually needs wires for power, data (often Wiegand or OSDP), and sometimes LED/beeper control.
- The Electric Lock: Requires a dedicated power connection from the controller or a separate power supply with the correct voltage.
- Request-to-Exit (REX) Devices: These buttons or motion sensors connect to a specific input on the controller to signal a legitimate exit, which stops the system from flagging a "door forced open" alarm.
Here’s a pro tip that will save you hours of headaches down the line: label every single wire at both ends. It feels tedious at the moment, but when you're trying to diagnose an issue six months later, you'll be glad you did.
Navigating the Software Configuration
Once everything is wired up and powered on, the action moves from the ladder to the laptop. This is where you bring the system to life, programming the rules that control who can go where and when. Modern cloud-based systems make this incredibly intuitive, usually through a simple web dashboard.
The initial setup almost always follows these key steps:
- Bring Controllers Online: The first thing you'll do is get your main controllers connected to the network so they can talk to the cloud server.
- Enroll Users: Next, you add people to the system. You can do this one by one or through a bulk import from an existing HR or property management database.
- Assign Credentials: Each user is then linked to their credential, whether that's a key fob, a mobile pass on their smartphone, or a biometric scan.
- Create Access Levels: This is the smart way to manage permissions. Instead of assigning access door-by-door for every person, you create logical groups. For example, an "All Staff" level gets access to main entrances and common areas, while a "Senior Management" level adds access to executive offices and server rooms.
This group-based approach makes administration so much simpler. When a new person joins the marketing team, you don't have to remember all 15 doors they need. You just assign them the "Marketing Department" access level, and the system does the rest.
Bringing It All Together: System Testing and User Training
The hardware is mounted, the software is up and running, and the last wire has been neatly tucked away. It’s a huge milestone, but don't pop the champagne just yet. The most critical phase—what we in the industry call commissioning—is about to begin. This is where we shift from installation to verification, ensuring the system doesn't just work on paper but performs flawlessly in the real world.
Think of it this way: you wouldn't build a hotel and open the doors without checking that every key card opens the right room. Skipping this final, meticulous check is a recipe for security gaps and operational headaches down the line.

The Art of Commissioning: A Deep Dive into Testing
True commissioning goes far beyond a simple "tap and go" at each door. It's about systematically pressure-testing every single function and scenario you can imagine. From standard entries to forced-open alarms, you need to confirm the system reacts exactly as you designed it to.
I always recommend creating a detailed checklist. It’s not just for organization; it’s your documented proof that the system was handed over in perfect working condition, leaving no room for "we thought it worked" ambiguity.
Here are the non-negotiables for your testing protocol:
- Credential Workout: Test every single type of credential—mobile passes, key fobs, PINs, biometrics—at every single reader. No exceptions.
- Access Level Gauntlet: Create test profiles for different roles (e.g., resident, maintenance, manager). Try to access restricted areas with lower-level credentials to confirm the system correctly denies entry.
- Hardware and Sensor Integrity: Physically check that locks engage fully and disengage without sticking. Prop a door open past its allowed time to ensure the alarm triggers. Manually trigger a "forced entry" sensor.
- Audit Trail Accuracy: After performing a series of actions—a valid entry, a denied attempt, an alarm event—immediately pull the event log. Does every action appear with the correct user, timestamp, and location? This is your digital witness, and it needs to be perfect.
We're also seeing more advanced credentials, like biometrics. With iris recognition systems predicted to capture 35% of the market by 2035, testing these requires extra diligence. You’ll need to check enrollment processes, recognition speeds, and accuracy under various lighting conditions. This trend is a major part of the evolving security landscape, as detailed in this access control market forecast.
Before signing off, a final commissioning checklist is essential. It provides a structured way to validate every piece of the puzzle, ensuring a smooth and secure handover.
Post-Installation Commissioning Checklist
| Test Category | Specific Action | Expected Outcome | Status (Pass/Fail) |
|---|---|---|---|
| Reader & Credential | Test a valid credential at each reader. | Green light, door unlocks. | |
| Test an invalid/unassigned credential. | Red light, door remains locked. | ||
| Door Hardware | Manually verify lock engagement and release. | Lock mechanism is smooth, no grinding or sticking. | |
| System Alarms | Hold a door open beyond the set time limit. | "Door Propped" alarm triggers in the software. | |
| Access Schedules | Attempt access with a valid credential outside its scheduled hours. | Access is denied; event is logged correctly. | |
| Software Logs | Review event logs after a series of tests. | All actions are logged accurately with correct timestamps. | |
| Network & Power | Disconnect main power to a controller. | Controller seamlessly switches to battery backup. |
This checklist serves as your final seal of approval, confirming that the system is ready for the most important part of the equation: the people who will use it every day.
From Technology to People: Making Training Stick
A state-of-the-art security system is effectively useless if your residents or staff don't know how to use it properly. Worse, if they're confused, they’ll inevitably find workarounds—like propping open a secure door—that completely undermine your investment.
Effective training is all about relevance. The information you give a resident in a multi-family complex is completely different from what you'd tell a commercial property manager. Tailor your approach to the audience.
Pro Tip: Don't just show people how the system works; explain why the new rules are in place. When they understand the goal is to protect them, their property, or company assets, you get buy-in instead of pushback. It’s a simple shift in framing that makes all the difference.
A solid training plan should always include:
- Hands-On Demos: Walk people through the process at the actual doors they’ll be using. Let them use their own credentials.
- Cheat Sheets: Create simple, one-page guides with screenshots for common tasks, like granting guest access or reporting a lost fob.
- A Clear Lifeline: Make sure every single person knows who to call or email when they run into a problem.
By putting as much effort into testing and training as you do into the physical installation, you're not just handing over a box of hardware. You're delivering a comprehensive, reliable security solution that works from day one.
Common Questions About Access Control Installation
When you're kicking off a new security project, questions are bound to pop up. To give you a head start on your planning, we've pulled together answers to the most common things people ask when installing a new access control system.
How Long Does a Typical Installation Take?
This is the classic "it depends" question, but I can give you some real-world perspective. The timeline is all about scale and complexity. A simple, single-door setup? We could be in and out in less than a day. But if we're talking about a multi-story commercial building, you're realistically looking at a project that could stretch over several weeks.
A few key things really move the needle on the schedule:
- Type of Hardware: Biometric scanners and beefy magnetic locks just take more time and finesse to install than a straightforward RFID card reader.
- Existing Infrastructure: Working in an older building can be a wild card. Trying to run cable through concrete walls or dealing with ancient wiring will definitely add days, if not weeks, to the project.
- Software Configuration: If you need the new system to talk to your existing property management software or HR platform, that integration adds another layer of work.
Honestly, the only way to get a solid timeline is to have a professional walk the site. A thorough survey will uncover all those little details that can make or break a schedule.
What Are the Biggest Hidden Costs?
The quote for hardware and software is usually pretty clear, but it's the hidden costs that can really sting if you aren't prepared for them. The biggest surprise for many clients is the need for network upgrades. Your existing infrastructure might not have the juice to support all the new smart devices you're adding.
A few other potential budget-busters to watch for:
- Difficult Cabling Runs: The cost of labor skyrockets when technicians have to run new wiring through finished ceilings or drill through thick concrete walls.
- Door and Frame Modifications: Not every door is ready for an electronic lock right out of the box. Some need to be reinforced or modified, which adds to the bill.
- Ongoing Fees: Don't forget to look past the installation day. You need to budget for recurring costs like software subscriptions, cloud hosting, and any ongoing maintenance contracts.
Always insist on a detailed, all-inclusive quote from your installer. It’s the best way to protect yourself from those unexpected invoices later on.
The most overlooked cost is almost always the internal time your own team spends on the project. Think about it: project management, coordinating schedules, and training staff all take your people away from their regular jobs. Those hours are a real cost and should be factored into your total ROI.
Can a New System Integrate with My Existing Security?
Absolutely. In fact, it's one of the biggest benefits of modern systems. Most are designed specifically to play well with others. It's very common to tie a new access system into video surveillance (CCTV), alarm systems, and even broader building management platforms.
A great example is setting a rule where a specific camera automatically starts recording the moment a high-security door is opened. To make this happen, the systems need to speak the same language. You'll want to look for solutions that use open APIs (Application Programming Interfaces) or support common industry protocols like ONVIF for video. This kind of compatibility is what lets you build a truly cohesive security ecosystem.
What’s the Difference Between Fail-Safe and Fail-Secure?
Understanding this is non-negotiable—it's a critical decision for both safety and security. This term simply describes what the lock does when it loses power.
Fail-Safe locks unlock when power is cut. Think about fire exits. You need people to be able to get out in an emergency, even if the power goes out. These are essential for life-safety doors.
Fail-Secure locks remain locked when they lose power. These are what you want for protecting high-value areas like a server room or inventory closet. The last thing you want is for a power outage to give someone free access.
Your choice here isn't just a preference; it has to align with the door's purpose and, most importantly, local fire codes.
Ready to simplify your next project? Clouddle Inc offers managed technology solutions with zero-capex options and 24/7 support, making the installation of any access control system straightforward and budget-friendly. Learn more at https://www.clouddle.com.


