Cloud-based network security has become non-negotiable for businesses facing relentless cyber attacks. Traditional on-premise security systems simply can’t keep pace with modern threats, leaving organizations exposed to breaches that cost millions in damages and downtime.
At Clouddle, we’ve seen firsthand how companies struggle to protect their networks while maintaining compliance and business continuity. The solution isn’t incremental improvements-it’s a fundamental shift to cloud-based defenses that scale with your needs.
Why Your Current Security Approach Is Failing
Your on-premise security infrastructure was designed for a different era. Perimeter-based firewalls and manual access controls work when your infrastructure stays put, but they collapse the moment you move workloads to the cloud. According to IBM’s 2024 data breach report, 83 percent of organizations reported at least one insider attack in the last year, and that number keeps climbing. The problem isn’t a lack of security tools-most organizations run three or more separate security platforms. The problem is that traditional defenses don’t account for how cloud environments actually work. Your data lives across multiple providers now. Your applications run in containers that spin up and down in seconds. Your users connect from anywhere. Legacy security simply can’t track this velocity.
The Cost of Misconfigurations and Exposure
Misconfiguration opens the fastest path to a breach in cloud environments. According to recent research, around 82% of all data breaches involve cloud-stored data. That’s not a hypothetical risk-it’s happening. IBM research shows that 84 percent of organizations have at least one public-facing neglected asset, and 81 percent of those assets have commonly exploited open ports. These aren’t sophisticated attacks. Attackers simply scan for exposed resources and walk in. When breaches occur, the financial impact is severe. Public cloud incidents cost an average of 5.17 million dollars per breach in 2024, compared to the overall average of 4.88 million dollars.

Organizations also lose approximately 6.2 million dollars annually due to compromised cloud accounts alone. Beyond the financial hit, you face roughly 138 hours of downtime per incident. That translates to production systems offline, customers unable to access services, and revenue evaporating.
Identity and Access Control Gaps
Your privileged accounts are your crown jewels, and they sit undefended. IBM found that 61 percent of organizations still use root or account owners without multi-factor authentication. That means an attacker who compromises a single password gains full administrative access to your entire cloud environment. MFA isn’t optional anymore-it’s the baseline. Additionally, 70 percent of organizations store unencrypted secrets like API keys directly in code repositories, creating a permanent backdoor for anyone with repository access. These aren’t edge cases. They’re the norm across enterprises. Compliance frameworks like PCI DSS and HIPAA now mandate MFA for privileged accounts and encryption for sensitive data, so organizations that skip these controls face regulatory penalties on top of breach costs.
The Shared Responsibility Reality
The shared responsibility model makes cloud security your problem, not your provider’s. AWS, Azure, and Google Cloud secure their infrastructure, but you secure everything else-your data, your configurations, your access controls. That line is where most breaches happen. Organizations that treat cloud security as someone else’s responsibility pay the price. Your cloud provider can’t protect what you misconfigure or expose. Your cloud provider can’t enforce MFA on your accounts. Your cloud provider can’t encrypt your secrets before you store them in repositories. These controls fall entirely on your shoulders, which means your security posture depends on how well you implement them across every cloud environment you use.
What You Need to Deploy Right Now
Cloud-based network security requires three interconnected layers working in concert, and most organizations treat them as separate problems instead of an integrated system. Each layer strengthens the others, and gaps in any one layer expose your entire infrastructure to attack.
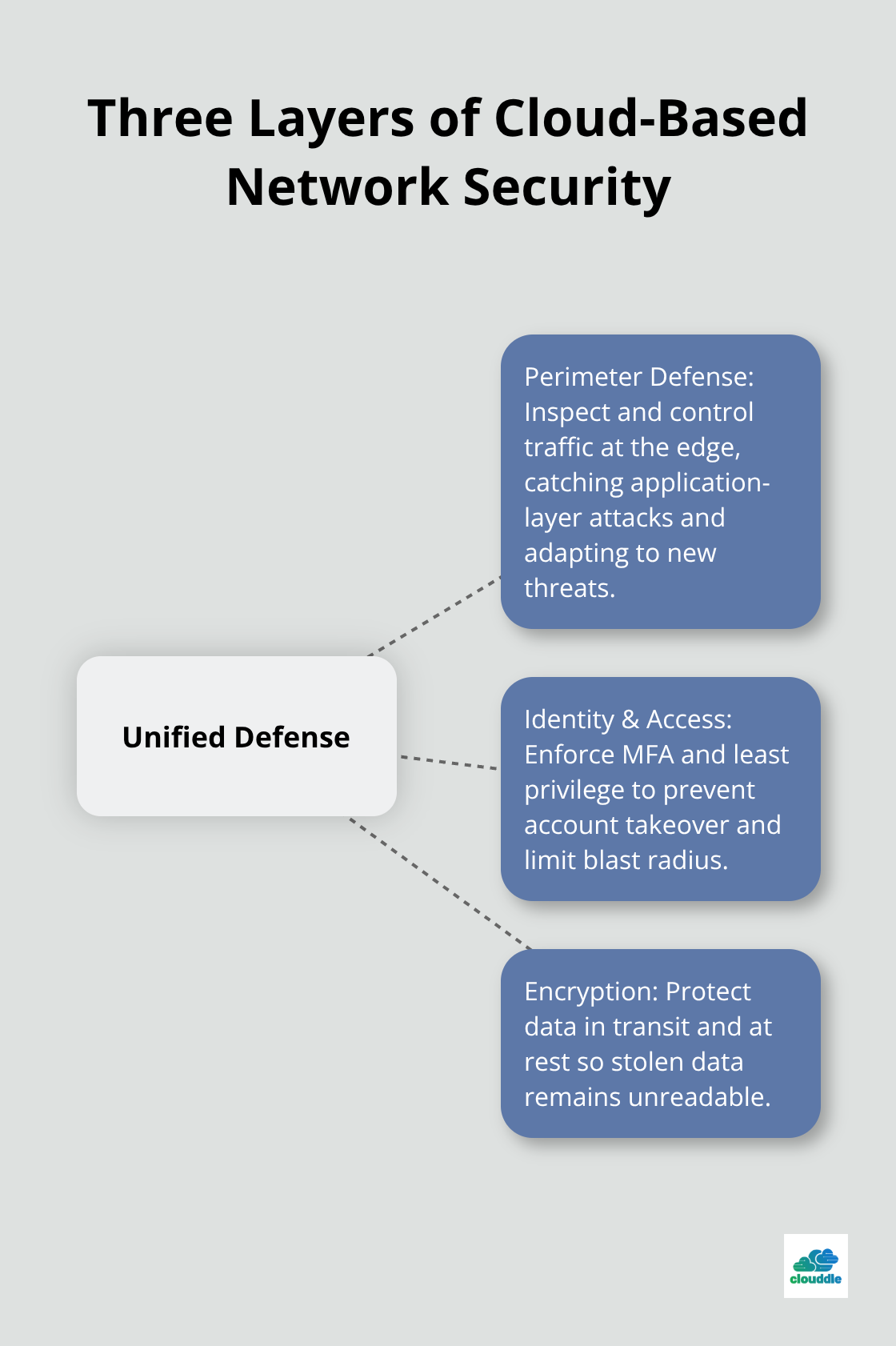
Perimeter Defense: Firewalls and Intrusion Detection
Your first line of defense operates at the network edge, where firewalls and intrusion detection systems inspect all traffic entering and leaving your cloud environment. Modern cloud firewalls function at Layer 7, meaning they understand application behavior rather than just IP addresses and ports. Cloud-native firewalls from vendors like Palo Alto Networks inspect encrypted traffic, block SQL injections and cross-site scripting attacks, and automatically adapt to emerging threats. This matters because attackers increasingly target application-layer vulnerabilities instead of network-level weaknesses. Your firewalls must catch malicious API calls, not just malicious packets.
Intrusion detection integrated into your firewall completes this layer. When suspicious activity crosses your perimeter, the system logs it, alerts your team, and blocks the threat in real time. IBM research shows that multi-environment breaches take an average of 283 days to identify and contain. Faster detection directly reduces breach costs and limits damage.
Identity and Access Management: The Privilege Problem
Identity controls determine who accesses what, and this is where most organizations fail catastrophically. IBM found that 61 percent of organizations still operate without multi-factor authentication on privileged accounts, meaning attackers need only one compromised password to own your entire cloud infrastructure. MFA is non-negotiable-implement it immediately for all administrative accounts, service accounts, and any account touching sensitive data.
Beyond MFA, implement least-privilege access using role-based access controls and regularly audit who actually holds administrative permissions. Many teams grant broad permissions during initial setup and never revisit them, creating sprawling attack surfaces. Tools like HashiCorp Vault or AWS Secrets Manager centralize secret management and eliminate the practice of storing API keys in code repositories, which 70 percent of organizations still do. This single change removes a permanent backdoor from your systems.
Encryption: Protection at Rest and in Transit
Encryption protects data when other defenses fail. Less than 10 percent of enterprises encrypt 80 percent or more of their cloud data, leaving massive amounts of sensitive information exposed. This gap exists partly because teams assume cloud providers handle encryption automatically-they do not. You must explicitly enable encryption, manage encryption keys, and verify that sensitive data is actually encrypted before it leaves your systems.
TLS 1.2 or higher should protect all data in transit, and AES-256 should protect data at rest. These standards are industry baseline, not optional enhancements. When you combine strong encryption with perimeter defense and identity controls, you create a system where attackers face multiple barriers at every stage of an attack.
Integration: How These Layers Work Together
A firewall without MFA or encryption is like installing a front door lock while leaving windows open. Each component amplifies the others. Your firewall catches external threats, identity controls stop internal abuse, and encryption neutralizes data theft if the other two fail. Organizations that deploy these three layers as a unified system dramatically reduce their breach risk and response time.
The next step is understanding how to assess your current infrastructure and identify which gaps pose the greatest risk to your business.
Moving From Assessment to Action
Inventory Your Cloud Infrastructure First
Start by cataloging exactly what runs in your cloud environments right now. Most organizations cannot answer basic questions about their own infrastructure: how many cloud storage buckets exist, which ones are publicly accessible, what data lives where, or who holds administrative access. This blindness creates serious risk. Nearly one in 10 publicly accessible cloud storage buckets contained sensitive data. Your first task is conducting a complete asset discovery across all cloud environments you use.
Tools like AWS Config, Azure Resource Graph, and Google Cloud Asset Inventory provide automated scanning capabilities. Run these tools and review the results thoroughly. Document every compute instance, database, storage bucket, and network resource. Map data flows between systems to understand where sensitive information travels. This inventory becomes your baseline for identifying misconfigurations and access control problems.
Prioritize Your Highest-Risk Vulnerabilities
Once you have visibility, prioritize ruthlessly. Focus first on eliminating public exposure of sensitive resources, then on enabling MFA for all privileged accounts, then on encrypting data at rest. These three actions address the highest-impact vulnerabilities according to IBM research. Skip the nice-to-haves and attack the problems that actually drive breaches.

Public exposure represents your most immediate threat. Attackers scan for exposed resources constantly and exploit them within hours. MFA on privileged accounts prevents attackers from owning your entire infrastructure with a single compromised password. Encryption at rest protects data if other defenses fail. These three controls stop the attack patterns that actually harm organizations.
Select a Provider That Fits Your Infrastructure
Selecting a security provider matters less than selecting one that integrates with your existing infrastructure without requiring a complete rebuild. Evaluate providers based on their ability to support your specific cloud platforms and workload types, not on marketing claims about coverage. Ask vendors for concrete examples of how they detect and respond to the threats you actually face, not hypothetical scenarios.
Require proof that their platform handles encrypted traffic inspection at Layer 7, manages secrets securely, and integrates with your identity provider through standard protocols like SAML or OIDC. The right provider fits your environment rather than forcing you to reshape your environment around their tool.
Deploy Capabilities in Phases, Not All at Once
During deployment, resist the temptation to enable every feature at once. Start with perimeter defense and identity controls, then add encryption and advanced detection capabilities once your team understands the basics. Set up centralized logging from day one, even if you don’t actively monitor it yet. Most organizations waste months trying to piece together what happened during an incident because logs were scattered across different systems or not collected at all.
Configure alerts for specific high-risk events like privilege escalation, new administrative account creation, and failed authentication attempts exceeding normal thresholds. Test your incident response plan monthly by simulating breaches and measuring how quickly your team detects and contains them. Regular testing cuts response time dramatically.
Final Thoughts
Cloud-based network security stops the attack patterns that actually harm organizations, and the financial case for implementation is straightforward. A single breach costs millions in recovery, downtime, and regulatory penalties, while proper security costs far less to deploy. When your security infrastructure scales automatically with your cloud workloads, your team spends less time managing infrastructure and more time responding to actual threats.
Centralized logging and monitoring reduce incident detection time from 283 days to hours, and automated compliance checks eliminate manual audits and regulatory surprises. These operational improvements compound over time, freeing your security team to focus on strategic priorities instead of firefighting. Your next step is conducting that asset inventory we discussed-document what runs in your cloud environments, identify public exposure, and enable MFA on privileged accounts.
We at Clouddle help organizations implement cloud-based network security that actually works through managed security services combining networking, connectivity, and threat protection into a unified platform. With 24/7 support and flexible contracts, you get enterprise-grade security without the enterprise overhead. Learn more about how we can strengthen your security posture at Clouddle’s security solutions.


