Hybrid cloud environments combine on-premises infrastructure with cloud services, creating complex security challenges. Misconfigured services, weak access controls, and unmonitored traffic expose your network to real threats.
At Clouddle, we’ve seen firsthand how organizations struggle with hybrid cloud network security across multiple environments. This guide walks you through the vulnerabilities you face and the practical steps to lock down your infrastructure.
Where Your Hybrid Cloud Security Actually Fails
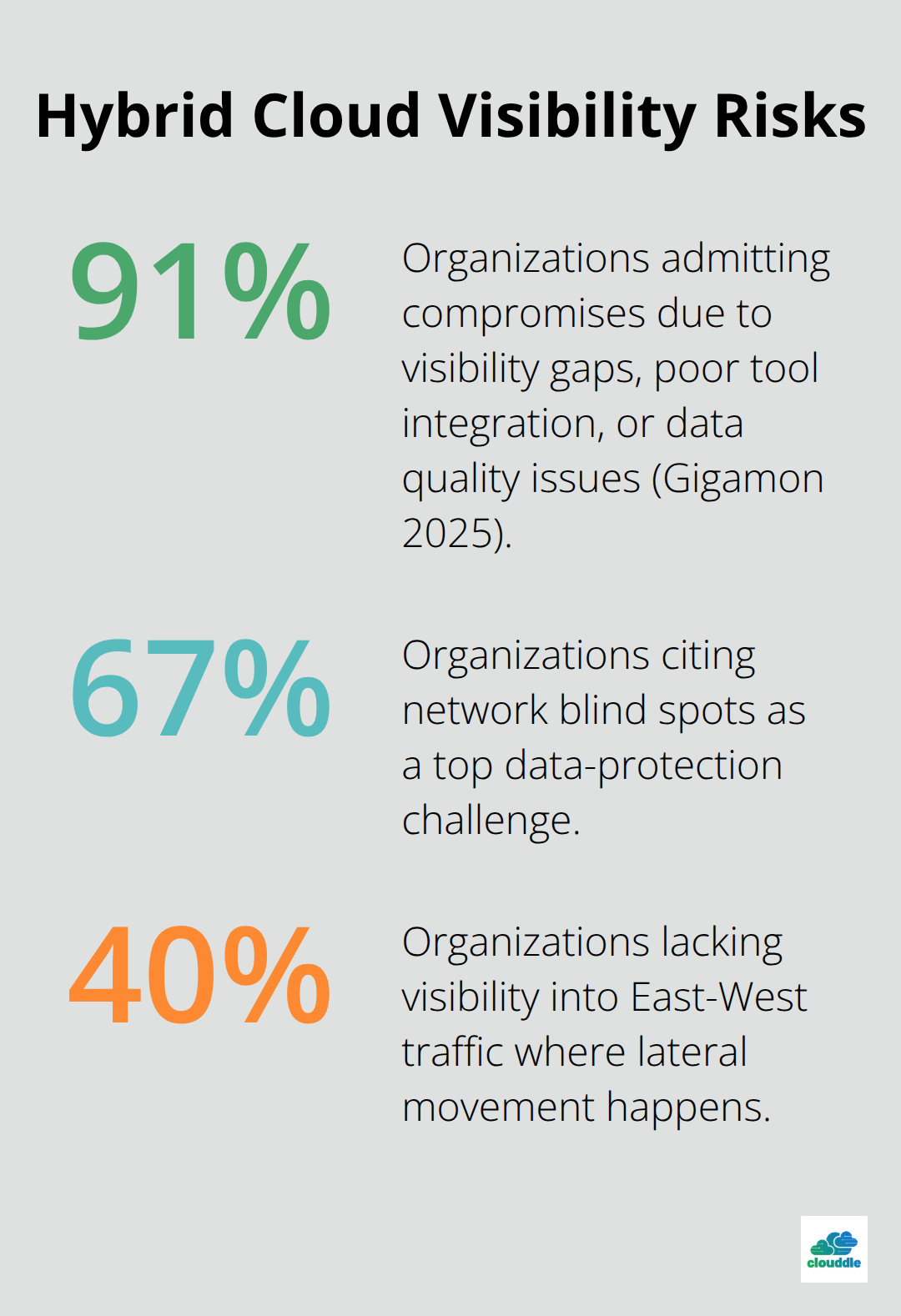
Your hybrid cloud infrastructure has more exposure points than you realize. According to the Gigamon 2025 Hybrid Cloud Security Survey, 91% of organizations admit compromises due to visibility gaps, poor tool integration, or data quality issues. The problem isn’t that security tools don’t exist-it’s that most organizations have blind spots they don’t know about.
Visibility Gaps Create Hidden Exposure
About 67% of organizations report network blind spots as a top data-protection challenge, and roughly 40% lack visibility into East-West traffic where lateral movement happens. This is where attackers operate. Misconfigured storage buckets, unencrypted data flows between environments, and weak access controls create gaps that tools miss. Your on-premises infrastructure follows one security standard, your AWS environment follows another, and your Azure setup operates independently. Meanwhile, data moves between them without consistent monitoring.
The Gigamon survey shows that network data volumes continue to grow, making manual oversight impossible. You cannot track what you cannot see.
When Security Tools Fail to Detect Breaches
When you can’t see what’s happening across your entire hybrid environment, you operate without situational awareness. The 2025 survey data reveals that 55% of organizations suffered a breach in the past year, up 17% from the prior year, and about half say their current security tools failed to detect the breach. This isn’t because attackers are smarter-it’s because organizations deployed point solutions that don’t talk to each other.
Your SIEM sees application logs, your network monitoring tool sees traffic patterns, and your cloud provider sees configuration changes, but nobody connects the dots. Real-time threat detection requires network-derived intelligence flowing into your security stack continuously. Without it, threats hide in encrypted traffic, lateral movements go undetected, and misconfigurations persist until someone exploits them.
Encryption Without Inspection Leaves You Vulnerable
Encryption alone doesn’t protect you. You need encryption in transit with TLS and at rest with AES, but you also need the ability to inspect encrypted traffic for threats. Most organizations encrypt everything, then assume it’s safe. Attackers know this. They move laterally through your network in encrypted channels, and your monitoring tools can’t see them.
Access control compounds the problem. Least-privilege access is the standard recommendation, but enforcement across hybrid environments remains inconsistent. AWS IAM policies differ from Azure role-based access control, and on-premises Active Directory uses different rules entirely. Add multi-factor authentication across all three, and you manage three separate authentication systems.
Organizations that implement Zero Trust architecture-verifying every access attempt and limiting lateral movement through microsegmentation-reduce breach impact significantly. The difference between a contained incident and a major breach often comes down to whether attackers could move freely through your network or hit microsegmentation walls. This foundation of visibility and access control determines what happens next in your security strategy.
Building a Security Foundation That Actually Works
Verify Every Access Attempt with Zero Trust
Zero Trust architecture isn’t optional in hybrid cloud environments anymore. The model requires verification of every access attempt, regardless of whether the request originates from inside your network or outside. This means you stop trusting network location and start trusting identity. In practice, this means implementing multi-factor authentication across all three environments simultaneously-AWS, Azure, and on-premises.
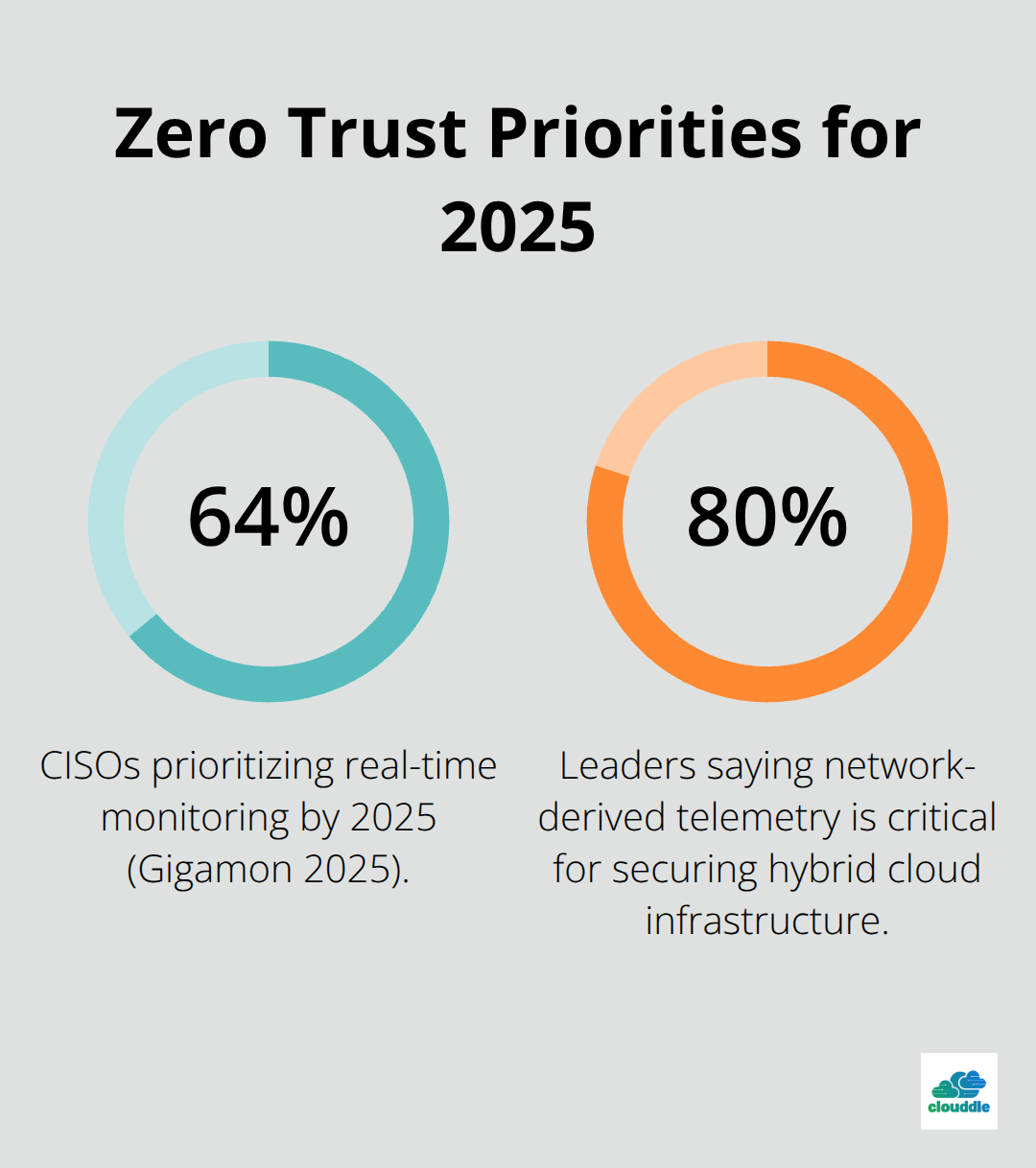
The Gigamon 2025 Hybrid Cloud Security Survey found that 64% of CISOs will prioritize real-time monitoring by 2025, and 80% say network-derived telemetry is critical for securing hybrid cloud infrastructure. This shift reflects a fundamental change: organizations that segment networks and enforce strict access controls contain breaches faster than those relying on perimeter defense alone.
Enforce Consistent Access Controls Across Environments
Start with microsegmentation in your data center, then extend identical policies to your cloud environments. AWS IAM policies should mirror your Azure role-based access control principles. Your on-premises Active Directory should integrate with a centralized identity provider that enforces the same MFA requirements everywhere. This consistency matters because attackers test every authentication pathway. One weak system becomes your entry point. Enforce least-privilege access relentlessly-users access only what their role requires, nothing more. Update these permissions quarterly as roles change. Automation handles this at scale. Infrastructure as Code tools like Terraform enforce security rules automatically when resources are created, reducing human error and ensure policies apply consistently across environments.
Aggregate Data Into a Single Monitoring Platform
Real-time monitoring separates organizations that detect threats in hours from those that discover them in months. The 2025 survey revealed that 55% of organizations suffered a breach in the past year, with roughly half saying their current tools failed detection entirely. This failure rate drops dramatically when network-derived intelligence flows continuously into your security stack. Deploy a single integrated platform that aggregates data from on-premises systems, AWS, Azure, and Google Cloud simultaneously. Your SIEM receives encrypted traffic inspection data, application logs, cloud configuration changes, and East-West network activity in one place. This consolidation matters because threats hide in the gaps between disconnected tools. When your network monitoring tool sees unusual traffic patterns at 2 AM, your SIEM correlates that activity with identity logs and cloud resource changes happening simultaneously. Organizations using unified platforms report faster mean time to detection.
Inspect Encrypted Traffic and Automate Response
Decrypt TLS/SSL traffic and apply application filtering to inspect encrypted channels for threats while maintaining privacy compliance. This requires network taps or traffic aggregators in your data center and equivalent capture points in cloud environments. Implement automated response capabilities that isolate compromised workloads instantly rather than waiting for manual intervention. The difference between containment in minutes versus hours determines whether attackers move laterally or hit a wall. Conduct continuous penetration testing to identify vulnerabilities before attackers do. Run these assessments quarterly minimum, focusing on lateral movement paths and privilege escalation routes across your hybrid environment. This proactive approach reveals weaknesses in your microsegmentation strategy and access control enforcement before real attackers exploit them.
What Tools Actually Stop Hybrid Cloud Breaches
Unified Platforms Eliminate Detection Gaps
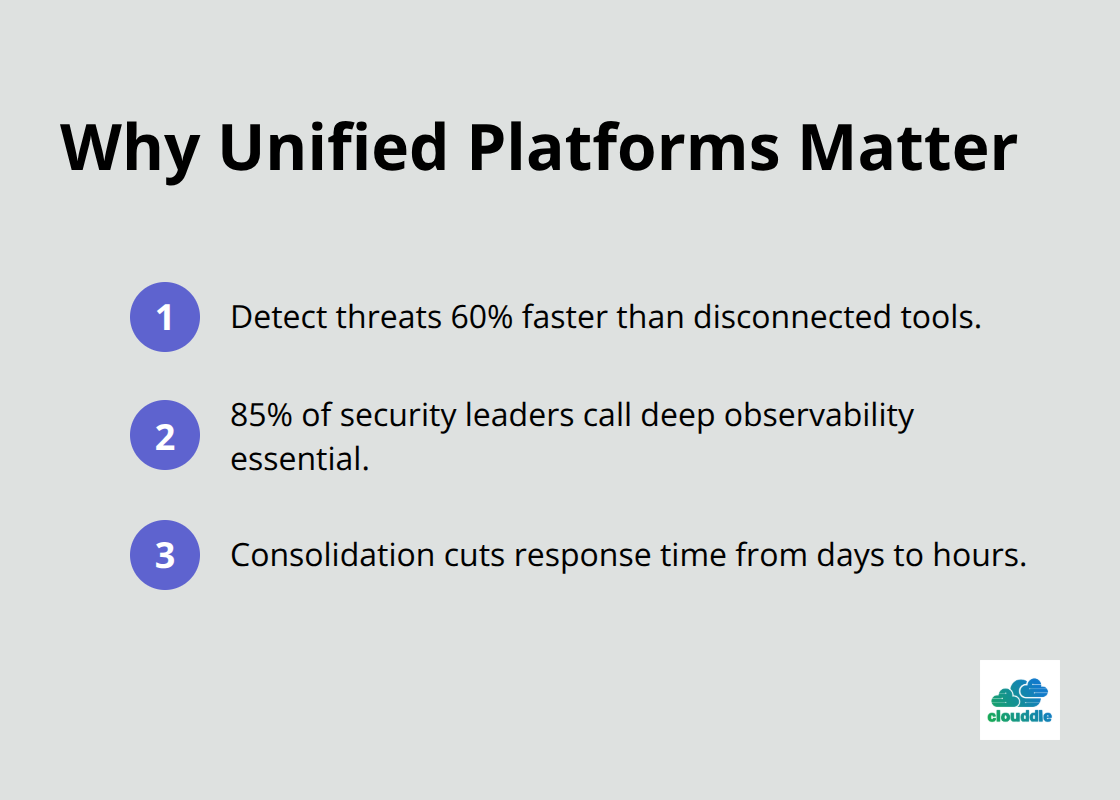
Unified security platforms are non-negotiable for hybrid cloud environments. Organizations that deploy a single integrated platform aggregating data from on-premises systems, AWS, Azure, and Google Cloud simultaneously detect threats 60% faster than those managing disconnected point solutions. The Gigamon 2025 Hybrid Cloud Security Survey found that 85% of security leaders view deep observability as essential to hybrid cloud security, yet most organizations still operate with fragmented tooling that creates detection gaps. A platform that consolidates your SIEM, network monitoring, and cloud-native security into one system eliminates the blind spots where attackers hide. When your security team investigates an alert, they see encrypted traffic inspection results, identity logs, cloud configuration changes, and East-West network activity in a single dashboard rather than jumping between three separate consoles. This consolidation directly impacts incident response time. Organizations that deploy unified platforms contain breaches within hours instead of days because correlation happens automatically rather than requiring manual investigation across disconnected systems.
Network Detection and Response Targets Lateral Movement
Network Detection and Response solutions address the exact gaps where most organizations fail. NDR tools are essential for detecting threats moving between your workloads rather than entering from the perimeter. These solutions decrypt TLS/SSL traffic, apply application-level filtering, and analyze internal network patterns continuously. Real-time threat detection requires this level of inspection because encrypted channels hide attacker movement, and traditional firewalls miss lateral attacks entirely. Deploy NDR alongside your SIEM and cloud-native security platform, not as a replacement. The combination ensures that network-derived intelligence flows into your security stack in real time, enabling your analysts to correlate traffic anomalies with identity events and configuration changes simultaneously.
Managed Security Services Provide 24/7 Response
Managed Security Service Providers handle continuous protection with 24/7 monitoring and automated response capabilities for misconfigurations and incidents, reducing reaction time from hours to minutes. Evaluate providers based on their detection rate in your specific environment rather than theoretical benchmarks. Ask for references from organizations running similar hybrid architectures and request proof of their mean time to detection in production environments. The difference between providers often comes down to how quickly they respond to your specific threats rather than generic threat categories.
Final Thoughts
Hybrid cloud network security requires three interconnected actions: visibility across all environments, consistent access controls, and automated threat response. Organizations that implement these foundations contain breaches in hours instead of days. The data proves this-55% of organizations suffered breaches last year, and half said their tools failed to detect them, yet this failure rate drops dramatically when you aggregate data from on-premises systems, AWS, Azure, and Google Cloud into a single platform that correlates events in real time.
Your long-term security posture depends on treating hybrid cloud infrastructure as one integrated system rather than separate environments. Enforce Zero Trust architecture consistently across all three domains, implement multi-factor authentication everywhere, and deploy network monitoring that inspects encrypted traffic and detects lateral movement. Automate configuration validation so misconfigurations trigger remediation instantly, and conduct quarterly penetration testing to reveal weaknesses before attackers exploit them.
We at Clouddle understand that hybrid cloud network security demands more than point solutions and disconnected tools. Our managed security services combine networking, security, and 24/7 support to protect your infrastructure without the complexity of managing multiple vendors, allowing your security team to focus on threat hunting and strategic decisions rather than tool integration.