Cloud computing and network security breaches cost organizations an average of $4.45 million per incident in 2023, according to IBM’s Data Breach Report. The threats are real, and they’re growing faster than most companies can defend against them.
At Clouddle, we’ve seen firsthand how organizations struggle to balance accessibility with protection. The good news is that securing your infrastructure doesn’t require choosing between convenience and safety-it requires the right strategy and partner.
The Real Threats Targeting Your Cloud Infrastructure
Account Compromise: The Silent Entry Point
Unauthorized access remains the leading cause of cloud breaches. Most of these incidents stem from weak credentials, stolen API keys, or compromised service accounts rather than sophisticated hacking techniques. The problem intensifies in multi-cloud environments where teams manage identities across AWS, Azure, and Google Cloud simultaneously.
A single forgotten access token stored in a GitHub repository exposes your entire infrastructure. Organizations that enforce non-phishable multi-factor authentication like WebAuthn and hardware keys see dramatically lower compromise rates than those relying on SMS or standard authenticator apps. The cost of inaction proves substantial: a single account compromise leads to data exfiltration, lateral movement across your network, and weeks of remediation work.
Infrastructure Attacks: Beyond Traditional Network Threats
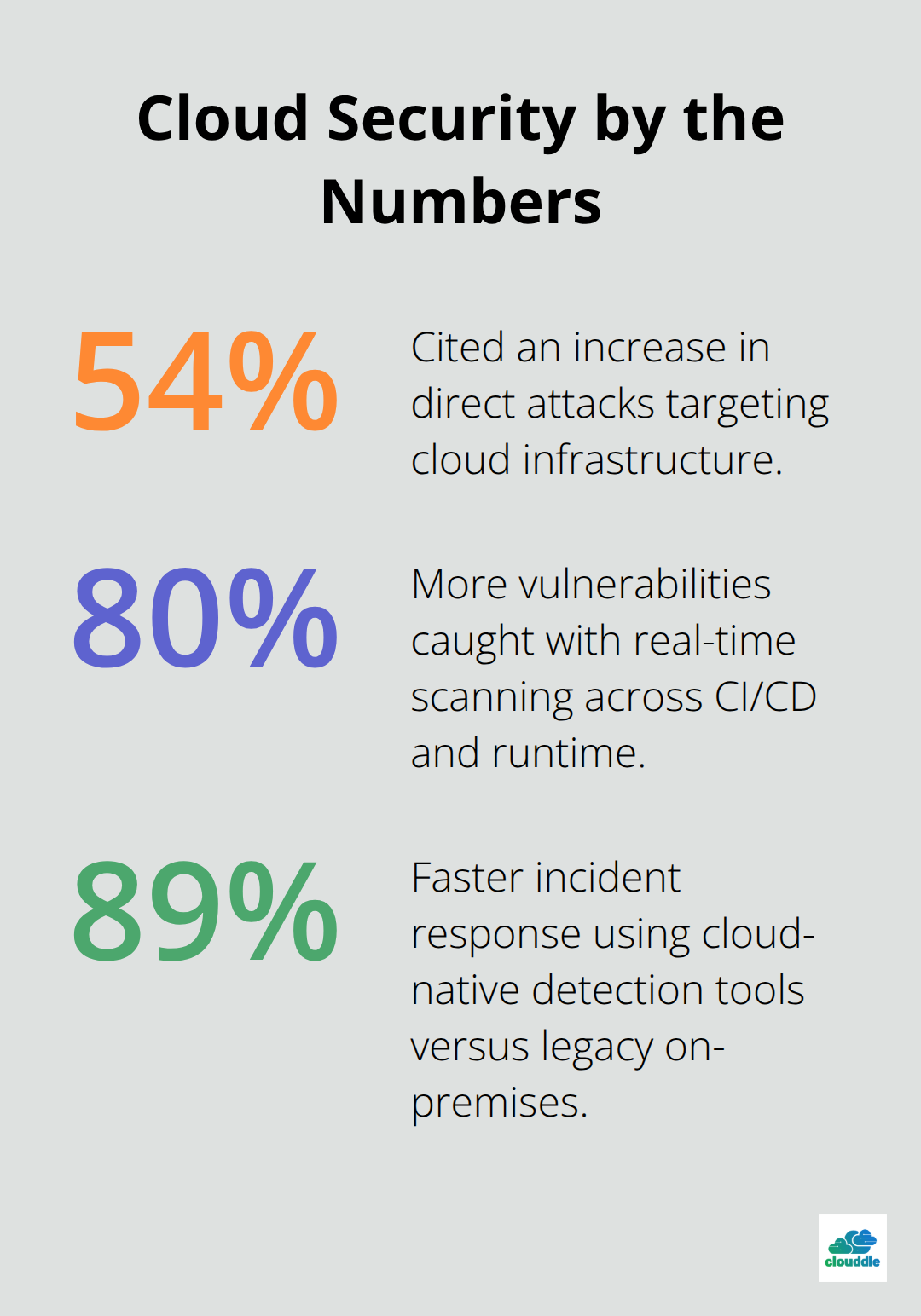
Network attacks have evolved far beyond simple DDoS floods. 54% cited an increase in direct attacks to compromise infrastructure. Ransomware operators now focus on cloud workloads because they know most teams struggle with visibility across hybrid environments.
Malware detection becomes harder when attackers hide malicious code inside container images or serverless functions that traditional security tools never scan. Many organizations still lack continuous vulnerability scanning for both virtual machines and containers. Teams that implement real-time scanning throughout their CI/CD pipelines and runtime environments catch 80% more vulnerabilities before attackers strike.
The Response Gap That Costs Organizations Time and Money
The gap between detection and response matters enormously. Organizations using cloud-native detection tools respond to incidents roughly 89% faster than those relying on legacy on-premises security infrastructure. This speed advantage translates directly into reduced damage, faster containment, and lower recovery costs when breaches occur.
Understanding these threats reveals why your current security approach may fall short. The next section examines the specific measures that actually stop these attacks before they compromise your data and operations.
Building Defenses That Actually Work
Stopping attackers requires moving beyond checkbox security. Organizations that treat multi-factor authentication as optional or vulnerability scanning as occasional tasks consistently experience breaches that could have been prevented. The difference between security theater and real protection comes down to execution and discipline.
Non-Phishable Authentication Stops Account Compromise
Hardware security keys eliminate phishing vectors that compromise standard authenticators. Microsoft reported that accounts protected with hardware keys experience zero successful phishing attacks, while SMS-based MFA still fails regularly. Deploy hardware keys for your admin and service accounts first, then expand to all users with cloud access. This single change stops the majority of account compromise incidents before they start.
Least-Privilege Access Reduces Your Attack Surface
Implement least-privilege access across your entire infrastructure. Teams that restrict permissions to the absolute minimum needed for each role reduce their attack surface dramatically. AWS and Azure both provide role-based access control, but most organizations configure roles too broadly. Audit your current permissions quarterly and remove access immediately when employees change roles or leave the organization. Dormant accounts with lingering permissions create entry points attackers exploit months after someone departs.
Continuous Vulnerability Scanning Catches Issues Before Production
Vulnerability management must happen continuously, not quarterly. Organizations that scan their virtual machines and containers throughout their CI/CD pipeline catch vulnerabilities before deployment rather than discovering them months later in production. Real-time scanning integrates directly into your development workflow, giving developers immediate feedback on security issues in their code and dependencies.
Encryption and Key Management Protect Data Everywhere
Encrypt all data in transit and at rest using strong encryption standards like AES-256 for stored data and TLS for transmitted data. Many organizations encrypt selectively, leaving sensitive databases unencrypted because they assume internal access is safe. That assumption fails when an insider threat or compromised account gains access. Encryption should be the default, not the exception. Rotate your encryption keys regularly and store key management separate from your data.
Patch Management Prevents Exploitation-Based Breaches
Establish a patch management process that treats security updates as emergency work, not routine maintenance. Critical vulnerabilities in widely used software get exploited within days of public disclosure. Subscribe to vulnerability feeds for your specific infrastructure components and test patches in staging environments before deploying them to production. Teams that patch within two weeks of release prevent the majority of exploitation-based breaches. These foundational controls form the backbone of your defense strategy, but they only work when you monitor what’s happening across your infrastructure and respond quickly when threats emerge.
Who Should Manage Your Cloud Security
The True Cost of Building Internal Security Teams
Deciding between building an in-house security team and partnering with a managed security provider often comes down to one brutal reality: most organizations lack the budget and expertise to do both effectively. The average cloud security engineer salary is $152,773 per year, and you need at least three to five people to cover monitoring, incident response, and vulnerability management across multiple cloud platforms. That investment tops $500,000 to $900,000 per year before tools, training, and overhead. Organizations pursuing this path still struggle because security expertise remains scarce and retention rates are poor as larger enterprises poach talent with higher compensation.
What Actually Matters in a Security Partner
A better approach involves evaluating managed security providers based on what actually matters: their ability to detect threats faster than your internal team could, respond to incidents in minutes rather than hours, and maintain compliance without creating operational friction. Start by examining their certifications and compliance validations. SOC 2 Type II certification proves they undergo independent audits of their security controls and operational processes. ISO 27001 certification demonstrates they maintain an information security management system. FedRAMP authorization shows they meet federal government security standards. These certifications matter because they indicate third-party verification rather than self-reported claims. Ask potential partners for their most recent audit reports and review what controls they’ve implemented.
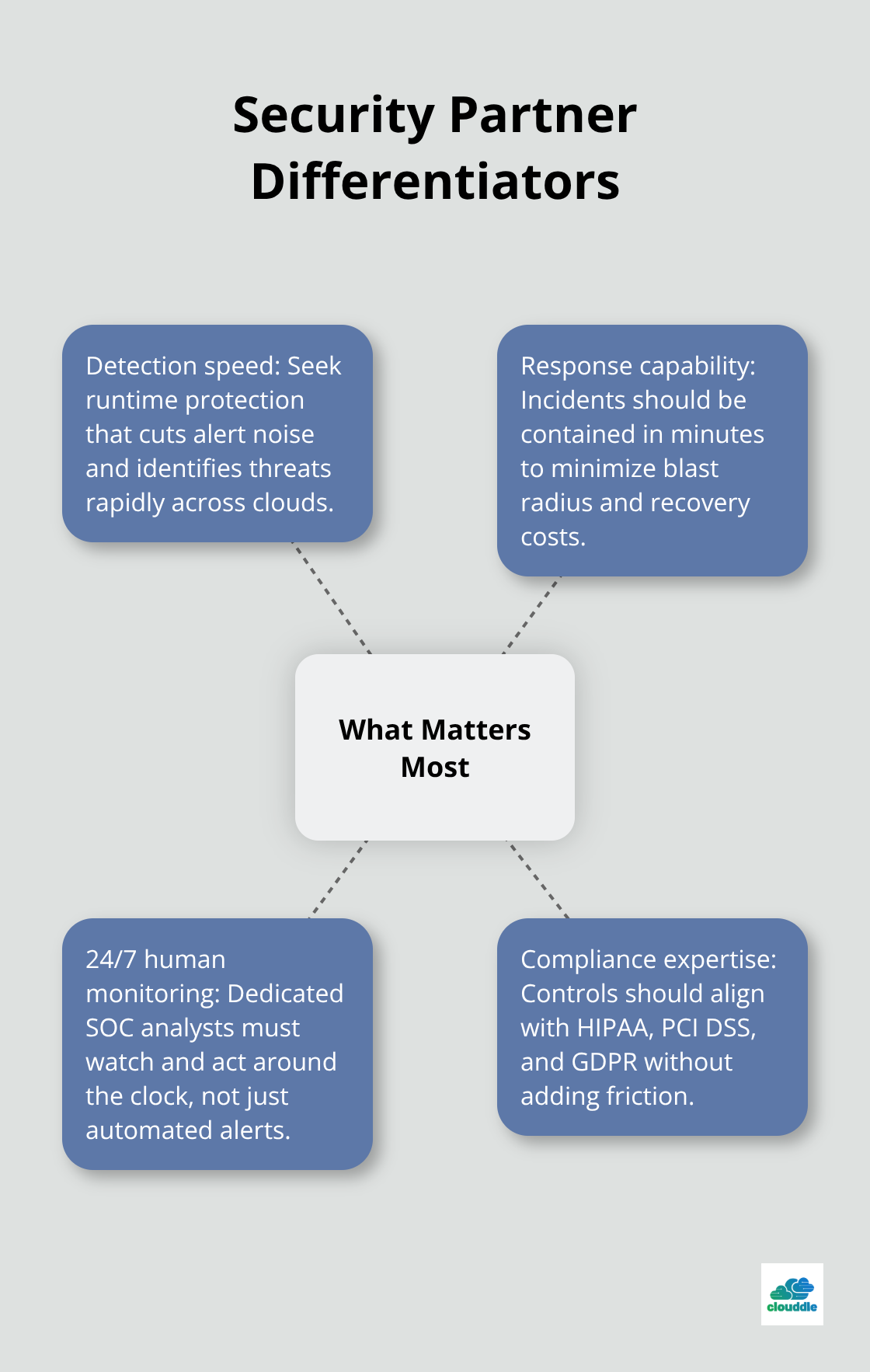
Detection Speed and Response Capabilities
The real differentiator between mediocre and exceptional security partners comes down to three operational capabilities that directly impact your breach outcome. First, examine their detection and response speed. Modern cloud-native detection platforms provide runtime protection across multi-cloud environments with significant reductions in alert noise and faster incident response compared to legacy approaches. Faster response means less data exfiltration, smaller blast radius, and lower recovery costs when incidents occur.
24/7 Monitoring With Real People
Second, verify they offer genuine 24/7 monitoring with actual people responding, not just automated alerts that sit in a queue until business hours. Many providers claim 24/7 monitoring but route incidents to on-call engineers who respond within hours. Your security partner should have dedicated security operations center staff monitoring your infrastructure continuously. This staffing model ensures someone responds to threats immediately, not after a delay that allows attackers to move laterally through your systems.
Industry-Specific Compliance Expertise
Third, confirm they handle your specific compliance requirements. If you operate in healthcare, they must understand HIPAA requirements for protected health information. Financial services demand PCI DSS compliance for payment card data. Regulations like GDPR impose strict data residency and protection requirements across the European Union. A partner who understands your industry’s regulatory landscape prevents misconfigurations that create compliance violations and regulatory penalties.
Final Thoughts
Cloud computing and network security breaches persist because organizations treat protection as a one-time project rather than an ongoing discipline. The threats outlined in this post-account compromise, infrastructure attacks, and detection gaps-continue to damage companies that implement controls inconsistently or fail to monitor their effectiveness over time. Real security requires three permanent operational commitments: enforce non-phishable authentication and least-privilege access, encrypt all data in transit and at rest by default, and establish 24/7 monitoring with actual people responding to threats immediately.

Organizations that execute these fundamentals experience measurably better outcomes. They catch vulnerabilities before production deployment, respond to incidents 89% faster than competitors using legacy tools, and prevent the account compromises that cause the majority of breaches. The investment in proactive security pays dividends through reduced incident costs, faster recovery times, and maintained customer trust when breaches occur.
Partner with providers who understand your industry’s compliance requirements, maintain genuine 24/7 monitoring, and demonstrate their capabilities through third-party certifications like SOC 2 Type II and ISO 27001. We at Clouddle combine managed IT, networking, and security services with 24/7 support to help organizations implement comprehensive protection without the burden of building internal expertise. Explore how managed security services streamline your defenses while your team focuses on business growth.


