IT risk management isn’t optional anymore. Cyberattacks cost organizations an average of $4.45 million per incident, according to IBM’s 2024 data breach report, and the threats keep multiplying.
At Clouddle, we’ve seen firsthand how companies that skip proper risk management end up scrambling when something goes wrong. This guide walks you through building a real, working IT risk management program that actually protects your business.
What Risks Should Your Organization Actually Fear?
IT Risks Extend Far Beyond External Threats
IT risks span far beyond the hackers that dominate headlines. Ransomware attacks continue to pose significant threats, yet internal misconfigurations and third-party vulnerabilities cause just as much damage. Insider threats account for a significant portion of incidents, whether through negligence or malice. Physical security failures, outdated systems, and supply chain weaknesses create openings that attackers exploit relentlessly. The reality is that most organizations face systematic risks tied to their technology infrastructure, regulatory risks from compliance failures, and unsystematic risks from one-off incidents.
The Risk Equation That Changes Everything
What separates companies that recover quickly from those that collapse is whether they map these threats to their actual assets and quantify the business impact. ISO 31000 provides a straightforward framework: Threat multiplied by Vulnerability multiplied by Asset equals Risk. This formula forces you to stop guessing and start measuring. You cannot manage what you don’t measure, and organizations that skip this step waste resources protecting low-impact systems while leaving critical assets exposed.
Why Formal Assessment Protects Business Continuity
Business continuity fails when companies treat risk management as a checkbox rather than an ongoing practice. Formal IT risk assessments conducted annually and after major changes (mergers, new technology deployments, remote work shifts) keep your exposure data current and actionable. Each assessment should identify and catalog your information assets first, then map threats to those assets, identify vulnerabilities through penetration testing and automated scanning, and finally calculate likelihood and impact using a simple high-medium-low scale or a 5×5 risk matrix.
Measuring What Matters Most
This structured approach reveals which risks warrant immediate investment and which can be accepted or transferred. Organizations that skip formal assessments operate blind, spending heavily on visible problems while missing the vulnerabilities that matter most. Track key metrics like mean time to detect incidents, percentage of vulnerabilities patched within 30 days, and the ratio of preventive controls to detective controls (these numbers tell you whether your program actually reduces risk or just consumes budget). Leadership needs quantified risk targets, not vague assurances that security is being handled.

With your risks mapped and measured, the next step is building the strategy that transforms this data into action.
Building Your Risk Assessment Strategy
Start your risk management program by conducting a thorough assessment that identifies what you actually own and what could go wrong. Asset identification comes first: catalog every critical application, database, server, and data repository across your organization. Many companies skip this step and assume they know what matters, then discover during an incident that undocumented systems held sensitive customer data. Asset identification and classification matters as much as inventory. Separate your assets by sensitivity and business criticality using a simple framework: classify data as public, internal, confidential, or restricted based on the damage exposure would cause. Apply the same logic to systems. A file server storing financial records requires different controls than one holding marketing materials.
Map Threats to Your Actual Assets
Once you have your asset map, identify the specific threats that could compromise each one. Threats include ransomware variants actively targeting your industry, insider negligence from employees sharing credentials, third-party vendors with weak security practices, misconfigurations in cloud environments, and supply chain vulnerabilities where attackers infiltrate through smaller suppliers. Vulnerability identification follows through penetration testing, automated scanning tools like Nessus or Qualys, and manual audits of your network architecture. NIST SP 800-30 provides guidance for conducting risk assessments of federal information systems and organizations. The output of this assessment phase should be a documented risk register that lists each identified risk with its threat, affected asset, relevant vulnerability, and current controls.
Decide How to Treat Each Risk
Translating assessment findings into action requires clear ownership and structured mitigation decisions. For each significant risk, decide whether you will mitigate it through new controls, transfer it via insurance or outsourcing, accept it with documented justification, or avoid it by retiring the system. Mitigation decisions must assign an owner, set a completion timeline, and allocate budget. A ransomware risk on your finance server, for example, might require implementation of immutable backups, multi-factor authentication on admin accounts, and endpoint detection and response software on that server cluster, with the finance director and IT security manager sharing accountability and a 60-day deadline.

Operationalize Risk Decisions Through Policy
Policies should reflect these decisions and operationalize them across teams. Your backup policy should mandate immutable snapshots for critical systems. Your access control policy should specify which roles receive elevated privileges and require quarterly review. Your incident response policy should name the incident commander, communication chains, and recovery priorities. Assign these responsibilities explicitly: IT operations owns backup verification, security owns access reviews, compliance owns policy updates, and leadership owns budget approval. Without clear ownership, mitigation plans stall and risks remain unaddressed.
Track Progress and Measure Results
Track progress monthly through a simple dashboard showing which risks have compensating controls in place, which remain open, and which have been resolved. Organizations that implement this structured approach see a measurable reduction in incident response time and breach impact compared to those managing risk informally. With your assessment complete and mitigation strategy in place, the next critical step involves selecting and implementing the specific controls that actually stop threats from materializing.
What Controls Actually Stop Threats From Materializing
Your risk assessment identified what could go wrong. Now you need the technical and operational controls that prevent those threats from becoming incidents. This is where most organizations falter-they invest in tools without connecting them to specific risks, then wonder why their security spending doesn’t reduce their breach rate.
Map Controls to Your Highest-Impact Risks
Effective control implementation starts with your risk register. Each high-priority risk should map to specific preventive controls that stop the threat before it materializes, and detective controls that catch compromises in progress. Preventive controls include multi-factor authentication on privileged accounts, network segmentation that isolates critical systems, regular patching of known vulnerabilities, and data encryption at rest and in transit. Detective controls include endpoint detection and response software that identifies suspicious process behavior, security information and event management systems that correlate logs across your infrastructure, and continuous vulnerability scanning that surfaces new exposures within hours of disclosure.
Balance Prevention and Detection
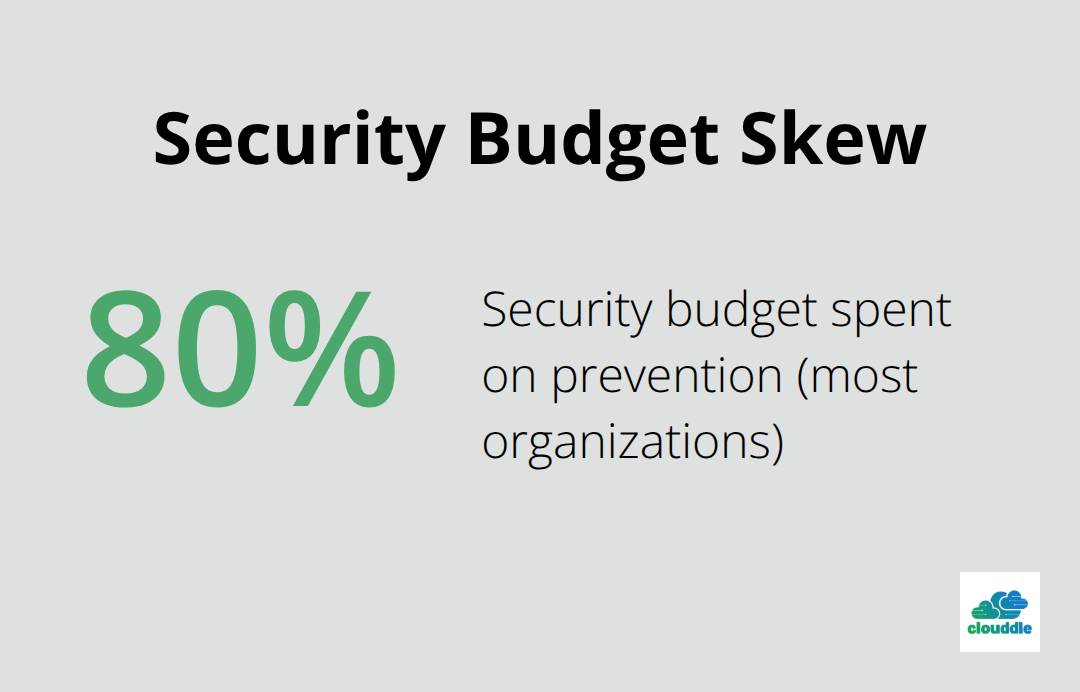
The National Institute of Standards and Technology recommends a balanced mix of both control types, though most organizations spend 80 percent of their budget on prevention and neglect detection entirely, leaving them blind to active compromises. That ratio is backwards.
Threat actors spend an average of 168 days inside networks before detection according to IBM’s 2024 data breach report, which means your detective controls matter more than your preventive ones.
Implement Immutable Backups and Recovery Systems
Backup and disaster recovery systems represent your last line of defense against ransomware and catastrophic failures. Immutable backups-copies that attackers cannot encrypt or delete even with administrative credentials-should protect every system storing sensitive data or critical business functions. Test these backups monthly through actual restore drills, not just verification scripts, because backups that cannot be restored are worthless. Organizations that conduct quarterly recovery drills reduce their mean time to recovery from weeks to hours.
Centralize Monitoring and Logging
Monitoring and logging technologies must capture activity across your entire infrastructure, not just firewalls and servers. Application logs reveal authentication failures and suspicious queries. Cloud service logs expose misconfigured permissions and unauthorized access attempts. Endpoint logs show which users accessed which files and when. Aggregate these logs into a centralized platform where you can search historical data, set alerts on suspicious patterns, and generate reports for audits. Without centralized logging, you spend weeks reconstructing incident timelines from scattered sources. With it, you answer critical questions in minutes.
Prioritize and Test Your Control Implementation
Start with the controls mapped to your highest-impact risks, implement them over 90 days, then verify they actually work through testing and monitoring before moving to the next tier.
Final Thoughts
Building an effective IT risk management program requires three concrete actions. First, conduct formal assessments annually and after major changes to keep your risk data current. Second, map your highest-impact risks to specific preventive and detective controls, then implement them systematically over 90 days. Third, establish clear ownership across your organization so mitigation plans actually execute rather than stall in planning stages.
Most organizations struggle with IT risk management not because they lack frameworks or tools, but because they lack execution discipline. You need someone accountable for each risk, a timeline for each control implementation, and monthly tracking of progress. Your risk register should be a living document reviewed in leadership meetings, not a document filed away after an audit. When leadership sees which risks remain open and what they cost to remediate, budget decisions shift toward actual protection rather than theoretical security.
At Clouddle, we handle the technical implementation of your risk controls while your team focuses on strategy and governance. Our 24/7 support means your detective controls run continuously without requiring internal staff to monitor logs at midnight. Schedule your formal risk assessment this month, identify your critical assets, map threats to those assets, and assign ownership with 90-day implementation deadlines for your highest-priority controls.


