Hotels and resorts handle sensitive guest data every single day, yet many operate with outdated security practices that leave them exposed. Cyber attacks on hospitality properties have increased 34% year-over-year, according to recent industry reports, with attackers specifically targeting guest networks and payment systems.
At Clouddle, we’ve seen firsthand how hospitality cybersecurity solutions require a different approach than standard corporate security. This guide walks through the specific threats your property faces and the practical steps you can take to protect both your guests and your operations.
Why Hospitality Properties Face Unique Cybersecurity Threats
Hospitality properties operate fundamentally differently from corporate offices, which means your security requirements don’t match standard business playbooks. Hotels process massive volumes of sensitive data simultaneously-passport scans, credit card details, booking histories, personal identification numbers-creating an enormous attack surface that attracts cybercriminals. Hotels rank second only to retail in attack frequency, making your property a high-value target regardless of size. The Marriott International breach in 2018 exposed data for approximately 383 million guests and resulted in GDPR fines around £99 million plus potential class-action damages up to $12.5 billion, demonstrating the financial catastrophe a single incident can trigger. Your guests expect seamless connectivity, which means you cannot simply lock down your network like a traditional enterprise-you must balance guest experience with security, and attackers exploit this tension relentlessly.

The Infrastructure Problem You Inherited
Most hotels operate with legacy payment systems, property management software, and networked devices that were never designed with modern threats in mind. POS terminals, door locks, HVAC systems, and smart room technology create exponential vulnerability points, yet replacing these systems costs hundreds of thousands of dollars. Public Wi-Fi networks intended for guests provide direct pathways into your infrastructure if you fail to segment them properly, and many properties still run guest and operational networks on the same systems. Third-party booking engines, loyalty programs, and OTA integrations expand your attack surface further because attackers target these trusted pathways rather than attacking you directly. A 2025 casino hotel paid approximately $45 million to affected customers and faced roughly $100 million in total losses from disruption and legal costs, illustrating how legacy vulnerabilities compound into catastrophic expenses. The core issue isn’t that old systems are inherently bad-it’s that attackers know exactly which vulnerabilities exist in decades-old software and exploit them systematically across entire hotel chains.
Compliance Creates Operational Friction
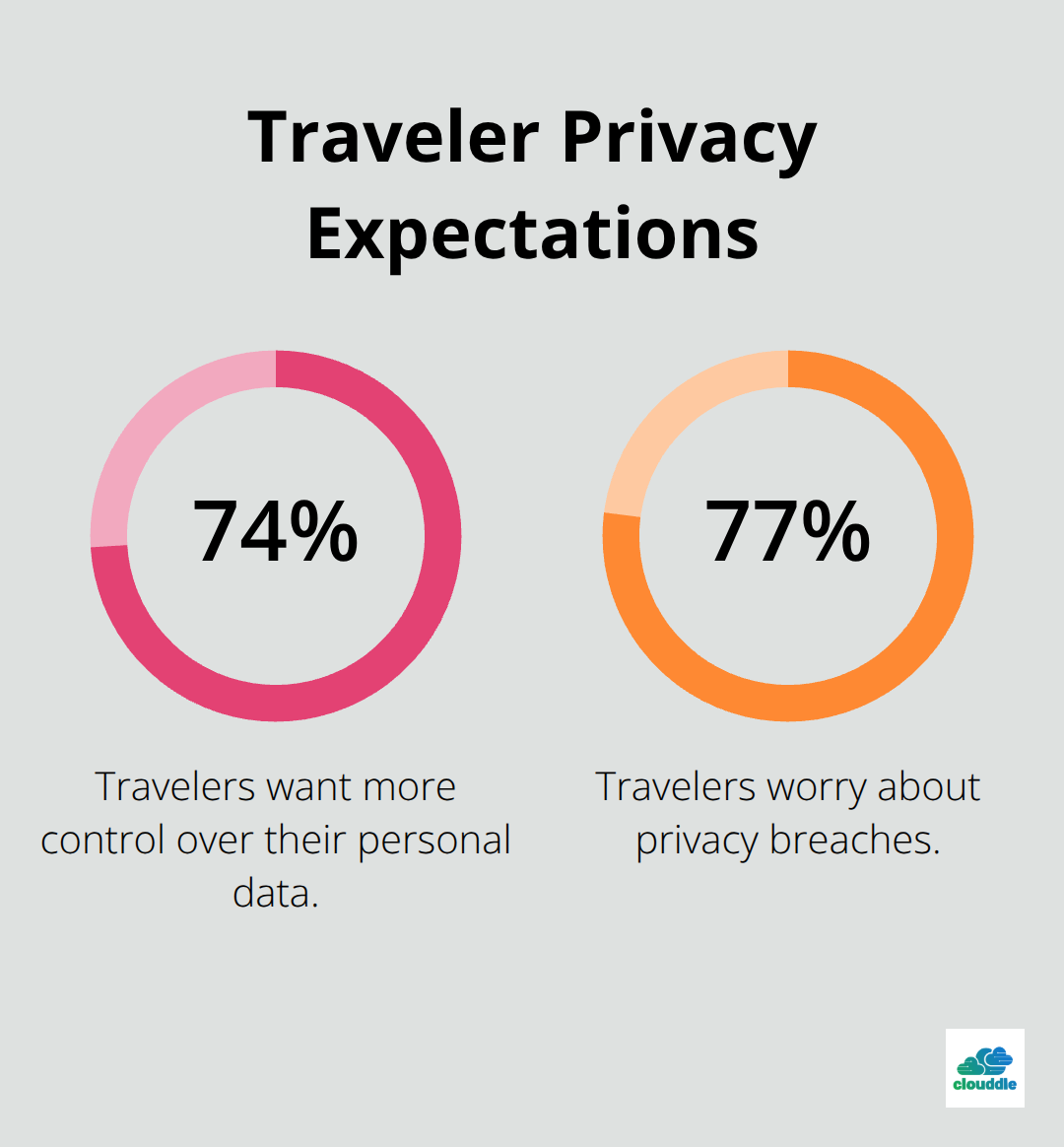
GDPR, PCI DSS, and local data protection regulations require specific security measures, yet hotels often treat compliance as a checkbox rather than a foundation for actual protection. PCI DSS mandates secure processing, storage, and transmission of card data, but enforcing these requirements across aging infrastructure demands continuous investment and staff retraining. Regulatory notification timelines force you to act within 72 hours of discovering an incident-a timeline most properties cannot meet without pre-established incident response plans. Guest expectations around data privacy have shifted dramatically, with 74 percent of travelers wanting more control over personal data and 77 percent worrying about privacy breaches, according to recent hospitality research. Non-compliance isn’t just a legal risk; it’s a reputational one that directly impacts bookings and guest loyalty when news of a breach reaches the public.
Why Standard Security Approaches Fall Short
Corporate security frameworks assume controlled environments with predictable user behavior and stable infrastructure. Hotels operate the opposite way-thousands of guests connect daily, staff turnover runs high, and your systems must remain accessible 24/7 without interruption. Attackers specifically target hospitality because they know properties prioritize guest experience over security lockdowns, and they exploit this operational reality. The combination of sensitive data, legacy systems, guest access requirements, and regulatory pressure means you need a security strategy built specifically for hospitality operations, not adapted from enterprise playbooks.
How to Protect Your Property Without Disrupting Guest Experience
Separate Networks to Contain Threats
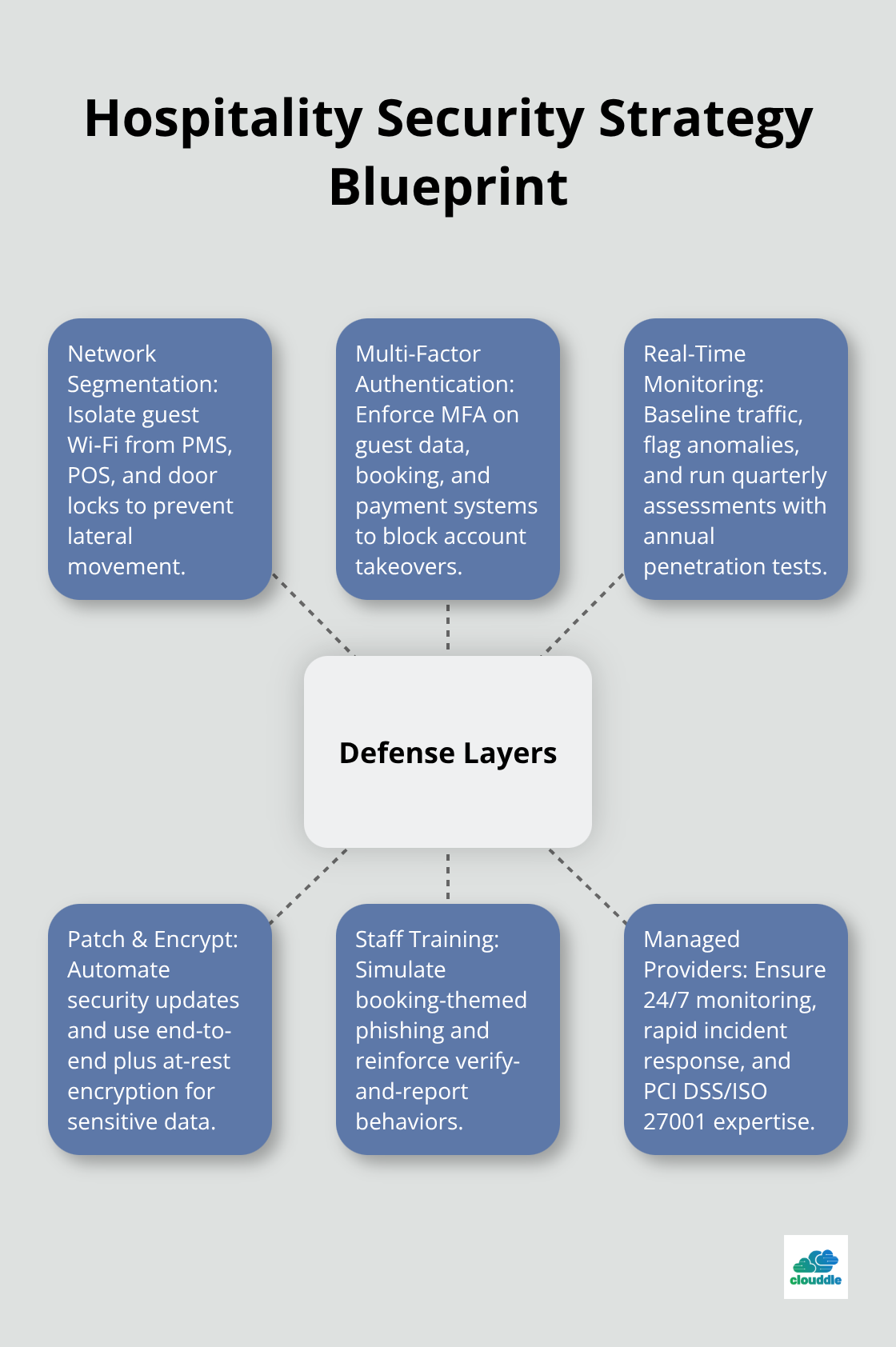
Network segmentation is non-negotiable, yet most properties still route guest and operational traffic through the same infrastructure. You must create isolated zones where a breach in guest Wi-Fi cannot cascade into your payment systems, door locks, or property management software. Your guests connect to a public network with limited access while your staff systems, POS terminals, and sensitive data sit behind stronger authentication requirements. Implement this separation at the router level and enforce it consistently across all properties in your chain, because a single misconfigured access point can undo months of security work.
Enforce Authentication and Access Limits
Multi-factor authentication for staff accessing critical systems adds a second verification layer beyond passwords. MFA can stop 30% to 50% of account compromise attacks, making it one of the highest-impact controls you can deploy. Require MFA for anyone accessing guest data, booking systems, or payment processing, and do not allow exceptions for convenience. Access controls should follow the principle of least privilege, meaning each employee sees only the data necessary for their role-a front-desk agent does not need access to financial records, and housekeeping staff should not view booking histories.
Monitor for Abnormal Activity in Real Time
Advanced threat detection systems identify abnormal behavior in real time rather than waiting for known attack signatures to match. These systems learn your normal network traffic patterns and flag deviations immediately, catching zero-day attacks and insider threats that traditional firewalls miss. Deploy continuous monitoring across your entire infrastructure, not just perimeter defenses, because attackers increasingly move laterally once inside your network. Regular vulnerability assessments should happen quarterly at minimum, with penetration testing conducted by external security firms at least annually to simulate real attack scenarios.
Patch Systems Immediately and Encrypt Everything
Patch management requires automation because manual updates create gaps-configure your POS systems, property management software, and operating systems to install security patches immediately upon release rather than waiting for scheduled maintenance windows. Encryption protects data both in transit and at rest, meaning credit card information and guest details remain unreadable even if intercepted or stolen. Implement end-to-end encryption for guest communications (emails and booking confirmations) and store all sensitive data encrypted on servers and backup systems.
Your infrastructure now resists common attack vectors, but attackers adapt constantly. The next layer of defense requires your staff to recognize threats before they reach your systems.
Building a Comprehensive Security Strategy
Your technical controls stop most automated attacks, but a determined adversary will target your staff through phishing, social engineering, and booking-themed impersonations that exploit trust in familiar workflows. Hotels face a specific threat landscape that requires staff training tailored directly to hospitality operations rather than generic corporate security awareness. Early 2026 booking-related phishing campaigns targeted hotel staff with Booking.com impersonations and ClickFix social engineering tactics to deliver malware such as DCRat, which enabled persistent remote access and credential theft across properties. Most hotels treat security awareness as an annual checkbox rather than continuous reinforcement tied to actual job workflows-a critical mistake that leaves staff unprepared for real threats.
Train Staff on Real Hospitality Threats
Your front-desk agents, reservations team, and finance staff need training that mirrors real booking inquiries, guest complaints, account reactivations, and fake verification prompts they encounter daily, not hypothetical scenarios disconnected from their reality. Effective awareness programs operate through short, booking-themed simulations staged across weeks one through four of employment, with ongoing variations rather than infrequent long-form training that staff forget immediately. The default staff response should be simple and reinforced constantly: do not click or respond inside booking messages, verify through trusted platforms like saved Booking.com accounts or official phone numbers, and report immediately without fear of punishment.
Four metrics reveal whether your program actually works: reporting rate, miss rate, time-to-report, and unknown-vendor reporting volume. These metrics show whether staff escalate suspicious messages quickly enough for your security team to contain threats-the only outcome that prevents breaches. Your security culture must reward reporting as the default action because speed of escalation directly determines whether an attacker gains foothold in your systems.
Integrate Physical and Cyber Security
Smart door locks, security cameras, and access control systems now connect to your network, meaning a breach in your PMS could grant attackers the ability to unlock guest rooms or disable security monitoring. Segment these operational technology systems from guest networks and staff workstations using dedicated networks with restricted access, which ensures that compromising one system does not cascade into others. This integration prevents attackers from exploiting the gap between your network controls and your building access systems.
Partner with Managed Security Providers
Managed security service providers handle continuous monitoring, threat detection, incident response, and compliance requirements that lean hotel security teams cannot sustain alone. A qualified provider should offer 24/7 monitoring with real-time alerting, quarterly vulnerability assessments, annual penetration testing, and incident response capabilities that activate immediately when threats appear. Verify that your provider maintains certifications such as ISO/IEC 27001 and understands PCI DSS compliance requirements specific to hospitality payment processing.
Your provider should also conduct regular security audits of third-party integrations like booking engines and loyalty platforms, since attackers frequently target these trusted pathways to reach your core systems. Avoid providers that treat security as a product you purchase; instead, partner with firms that embed security into your operational workflows and provide training aligned to your staff’s actual job responsibilities.
Final Thoughts
Protecting your property from cyber threats requires sustained commitment across technology, processes, and people. The investments you make today in network segmentation, staff training, and advanced monitoring directly reduce the likelihood of breaches that could cost millions in recovery, legal fees, and reputational damage. Hotels that treat cybersecurity as an operational priority rather than a compliance burden gain competitive advantage through guest trust and operational resilience.
Your hospitality cybersecurity solutions must address the specific vulnerabilities your property faces: legacy systems that cannot be replaced overnight, guest networks that must remain accessible, and staff who need practical training tied to real booking workflows. Technical controls alone cannot stop determined attackers, which is why your security strategy must integrate network infrastructure, threat detection, staff awareness, and incident response capabilities into a cohesive system. The 34 percent year-over-year increase in hospitality attacks means waiting to act is not an option-start your audit now against the practices outlined in this guide (network segmentation, multi-factor authentication, patch management, and staff training).
At Clouddle, we provide managed IT, networking, Wi-Fi, and security services specifically designed for hospitality properties through our Network as a Service offering. This approach combines reliable connectivity with enterprise-grade security and 24/7 support, allowing your team to focus on guest operations while we handle the technical complexity of keeping your systems secure and compliant. Identify gaps in your current infrastructure, prioritize based on risk, and implement changes systematically across your properties.


