IT threats cost businesses an average of $4.45 million per data breach in 2023, according to IBM’s Cost of a Data Breach Report. Poor risk management turns minor vulnerabilities into major financial disasters.
We at Clouddle see companies struggle daily with cyber attacks, system failures, and compliance violations. The benefits of IT risk management extend far beyond basic security-they protect your entire business foundation.
Smart risk management transforms IT from a cost center into a competitive advantage.
What Exactly Is IT Risk Management
IT risk management identifies, evaluates, and controls technology threats that could damage your business operations, data, or reputation. This process involves three core components that work together: risk assessment finds vulnerabilities, risk mitigation implements protective measures, and continuous monitoring adapts to new threats.
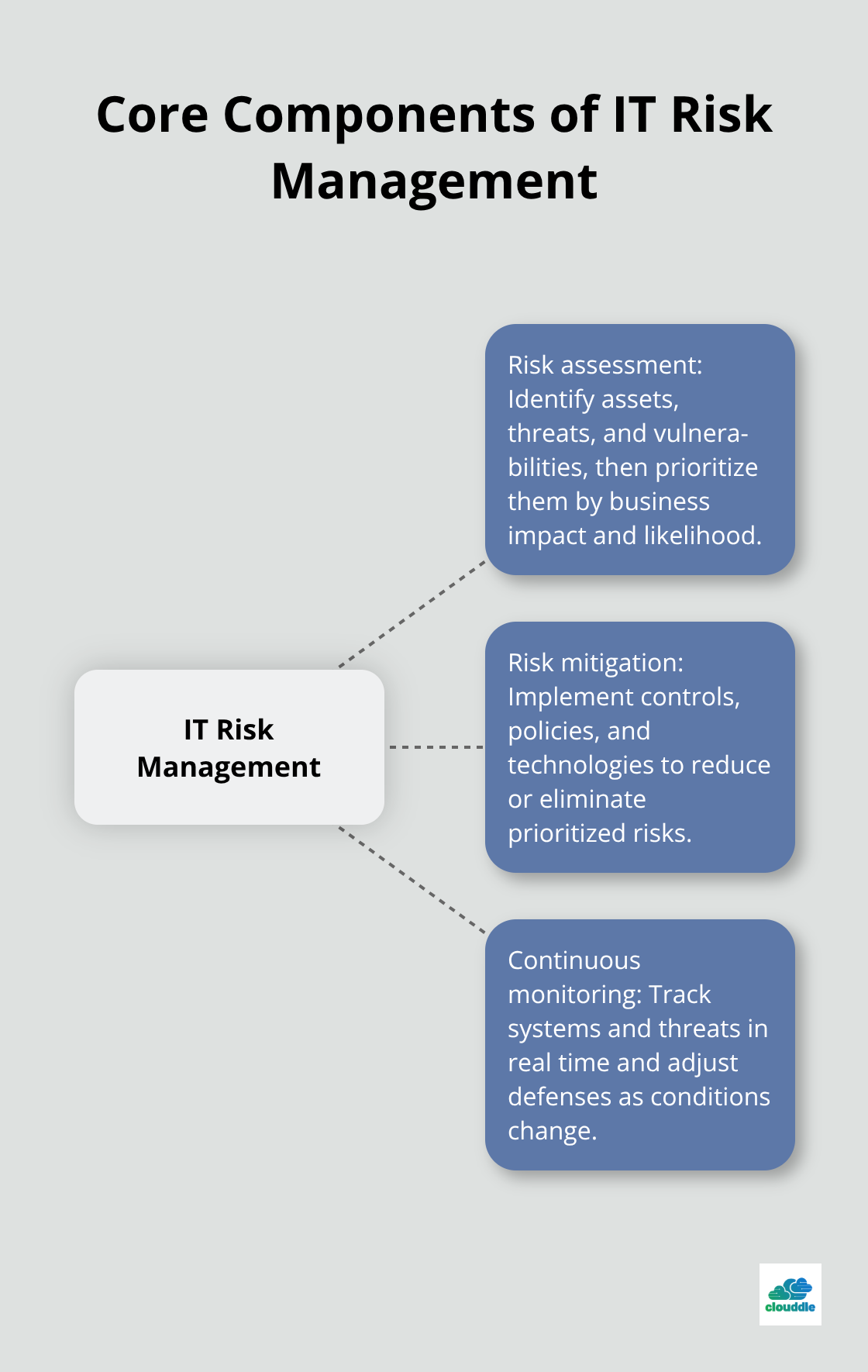
Organizations must evaluate their entire technology ecosystem, from cloud services and network infrastructure to employee devices and third-party software integrations.
Modern Businesses Face These Critical IT Risks
Cyber attacks represent the most expensive threat, with ransomware incidents alone costing companies an average of $2 million. Data breaches expose sensitive customer information and trigger regulatory penalties under GDPR, HIPAA, and state privacy laws. System failures from outdated hardware or poor maintenance halt operations for hours or days, while insider threats from current or former employees account for 34% of all security incidents (according to Verizon’s Data Breach Investigations Report). Cloud misconfigurations create massive security gaps, and supply chain attacks through compromised vendors spread malware across entire networks.
Poor IT Risk Management Destroys Business Value
Companies without proper risk management face catastrophic financial losses that extend far beyond the initial incident cost. The Ponemon Institute found that organizations take an average of 287 days to identify and contain a breach, during which damage compounds daily. Regulatory fines reach millions of dollars, while customer trust takes years to rebuild after a major security incident. Small businesses suffer the most severe impact, with 60% closing within six months of a significant cyber attack. Insurance premiums skyrocket after incidents, and some insurers refuse coverage entirely for businesses with poor security practices.
These mounting risks make effective IT risk management strategies essential for business survival and growth.
How IT Risk Management Protects Your Business
Stronger Security Stops Attacks Before They Start
Effective IT risk management creates multiple defense layers that help prevent cyber attacks, as AI continues to create new challenges for security according to Microsoft’s research. Companies that implement comprehensive security frameworks reduce their breach likelihood by 78% compared to reactive approaches. Multi-factor authentication alone blocks 99.9% of automated attacks, while network segmentation limits damage when breaches occur.
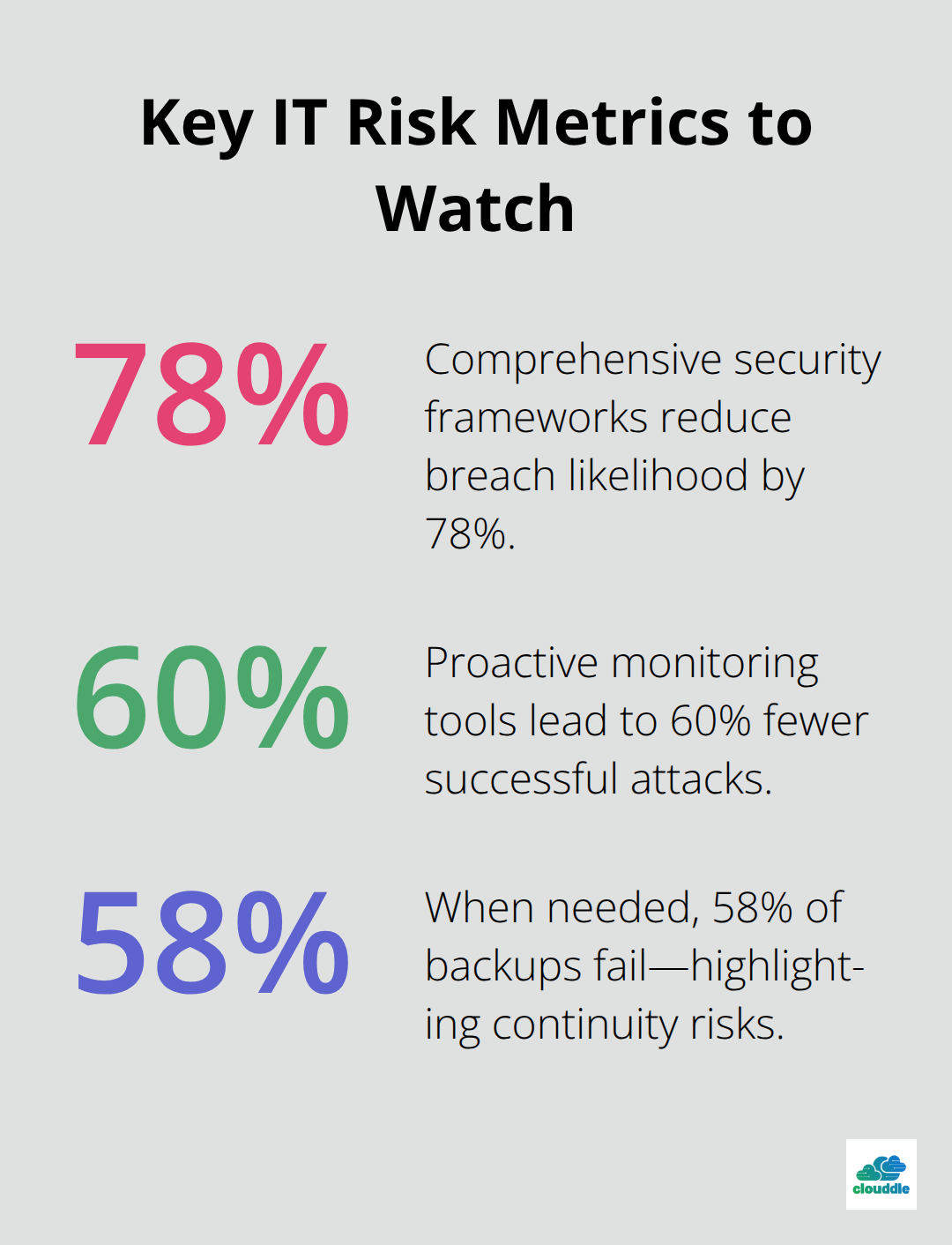
Regular vulnerability assessments identify weaknesses before attackers exploit them. Endpoint detection systems catch threats within minutes rather than the industry average of 287 days. Organizations that use proactive monitoring tools report 60% fewer successful attacks and recover three times faster from incidents.
Business Continuity Plans Minimize Downtime Costs
Structured risk management transforms system failures from business-ending disasters into minor inconveniences. Companies with tested disaster recovery plans resume operations within 4 hours compared to 72 hours for unprepared businesses. Automated backup systems prevent data loss entirely, while redundant infrastructure maintains service availability during hardware failures, though 58% of backups actually fail when needed.
Organizations without proper disaster recovery planning face significant risks to their business survival. Smart businesses prepare for the worst-case scenarios before they happen.
Compliance Protection Prevents Million-Dollar Penalties
Risk management frameworks align security practices with regulatory requirements and avoid devastating fines that destroy profit margins. GDPR violations cost companies up to 4% of annual revenue, while HIPAA penalties reach $1.5 million per incident. Organizations that follow SOC 2 and ISO 27001 standards pass audits 90% faster and face 85% fewer compliance issues.
Automated compliance monitoring tracks regulatory changes and adjusts policies immediately. Documentation systems provide audit trails that satisfy regulators during investigations (which can save companies thousands in legal fees).
These protective benefits create the foundation for successful risk management implementation, but organizations need specific strategies to achieve these results.
How Do You Build Bulletproof IT Risk Management
Start With Comprehensive Risk Discovery
Effective risk management begins with systematic asset inventory and threat identification that most organizations completely skip. Companies should catalog every device, application, and data repository within 30 days with automated discovery tools like Lansweeper or ManageEngine AssetExplorer. The NIST Cybersecurity Framework requires organizations to document all hardware, software, and data flows before they implement any security controls.

Risk assessments must evaluate both internal vulnerabilities and external threats, with quarterly reviews that adapt to new business conditions. Organizations that conduct monthly vulnerability scans catch more security gaps compared to annual assessments. Teams need to map data flows across all systems and identify critical assets that require the strongest protection.
Build Security Policies That Actually Work
Security policies fail when they create unrealistic restrictions that employees bypass daily. Effective policies balance protection with productivity through zero-trust principles that verify every user and device continuously. Password policies should require 12-character minimum lengths with multi-factor authentication rather than complex requirements that force weak passwords.
Network access controls must segment critical systems from general user networks, while data classification policies define proper procedures for sensitive information. Companies need incident response procedures that activate within 15 minutes of threat detection, with clear escalation paths and communication protocols that prevent confusion during attacks.
Transform Employees Into Security Assets
Human error causes 95% of successful cyber attacks, which makes employee education the most cost-effective security investment available. Monthly security awareness sessions reduce phishing click rates by 70% within six months, while simulated attacks identify vulnerable employees who need additional support. Organizations should implement security champions programs that designate tech-savvy employees as local experts who support colleagues with security questions.
Education must cover password management, email security, social engineering tactics, and proper incident notification procedures that encourage immediate threat reports without fear of punishment (this approach increases incident reports by 300%).
Final Thoughts
The benefits of IT risk management extend far beyond basic security measures to protect your entire business foundation. Organizations that implement comprehensive risk management strategies reduce breach likelihood by 78%, recover from incidents three times faster, and avoid devastating regulatory penalties that can reach millions of dollars. These protective measures transform IT departments from cost centers into competitive advantages that drive business growth.
The financial case for investment becomes clear when you consider that data breaches cost an average of $4.45 million, while 60% of small businesses close within six months of major cyber attacks. Companies with proper risk management frameworks pass compliance audits 90% faster and face 85% fewer regulatory issues. Smart organizations create substantial cost savings that justify initial investments (and protect their long-term viability).
Implementation starts with comprehensive asset discovery, followed by realistic security policies and employee education programs that reduce human error by 70%. We at Clouddle help businesses implement these strategies through our managed IT services that combine network security and 24/7 support. Effective risk management protects your reputation, maintains customer trust, and provides the stable foundation needed for sustainable growth in an increasingly connected world.


