Cyber attacks hit businesses every 39 seconds, making digital protection more urgent than ever. Most companies use fragmented security approaches that leave dangerous gaps.
We at Clouddle believe the right cybersecurity tools can transform your defense strategy. This guide covers the most effective solutions to build comprehensive protection for your business.
Which Tools Form Your Security Foundation
Antivirus and Anti-malware Protection
Antivirus software serves as your first defense line, but traditional signature-based detection shows varying effectiveness rates. Modern solutions like Bitdefender and Norton AntiVirus Plus combine behavior-based detection with machine learning to identify zero-day threats. Bitdefender scored 100% in recent independent lab tests for both protection and performance, while Norton achieved perfect scores across all major testing categories. These tools cost between $30-80 annually but prevent average breach costs of $4.45 million (per IBM’s 2023 data).
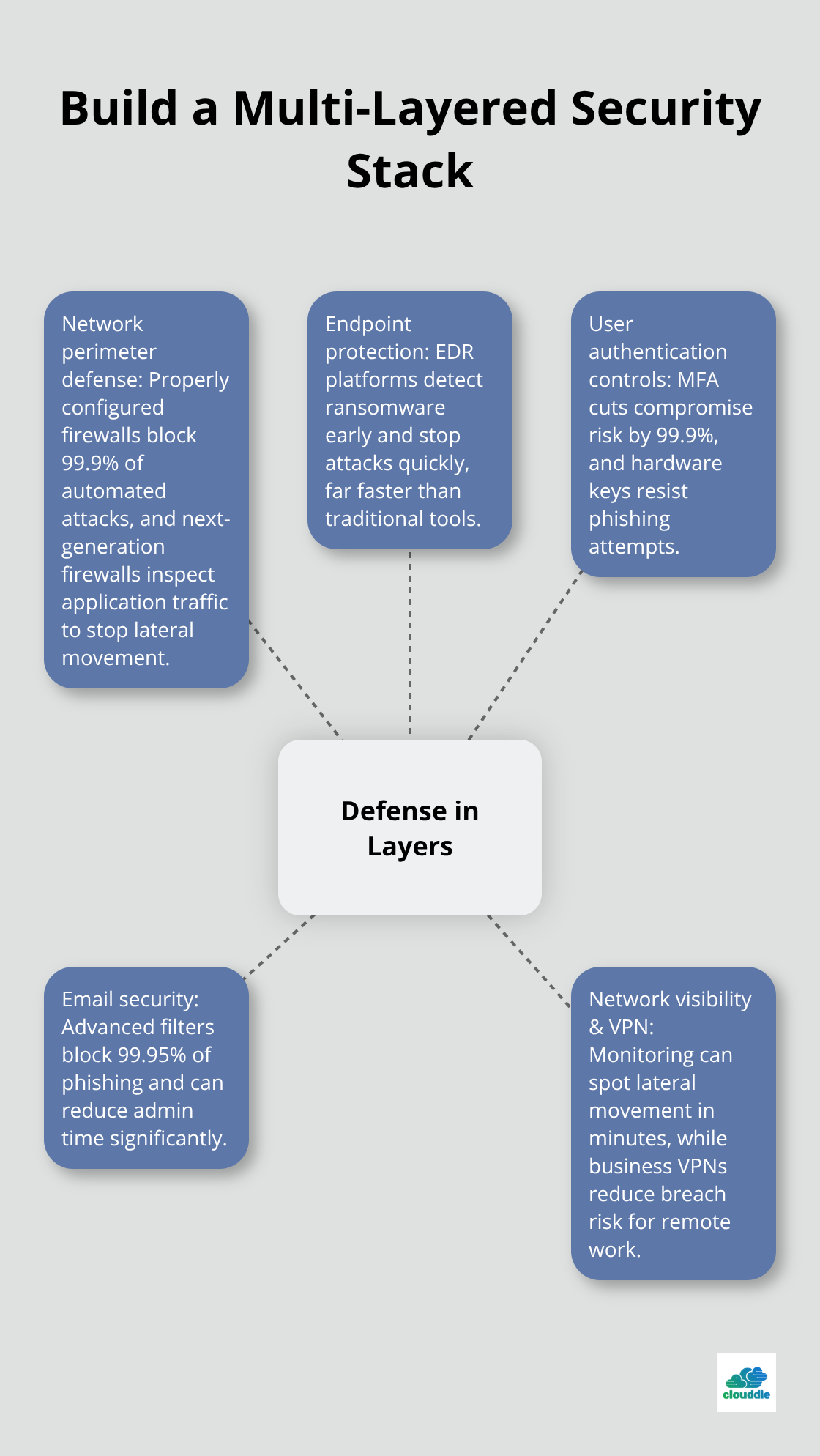
Network Perimeter Defense
Firewalls block 99.9% of automated attacks when you configure them properly, yet 60% of small businesses still rely on basic router firewalls. Next-generation firewalls from Fortinet and Palo Alto Networks inspect application-layer traffic and detect advanced persistent threats that bypass traditional port-based filtering. These solutions identify suspicious patterns in encrypted traffic and prevent lateral movement within networks. Implementation takes 2-4 weeks for most organizations, with monthly costs ranging from $200-2000 depending on throughput requirements and feature sets.
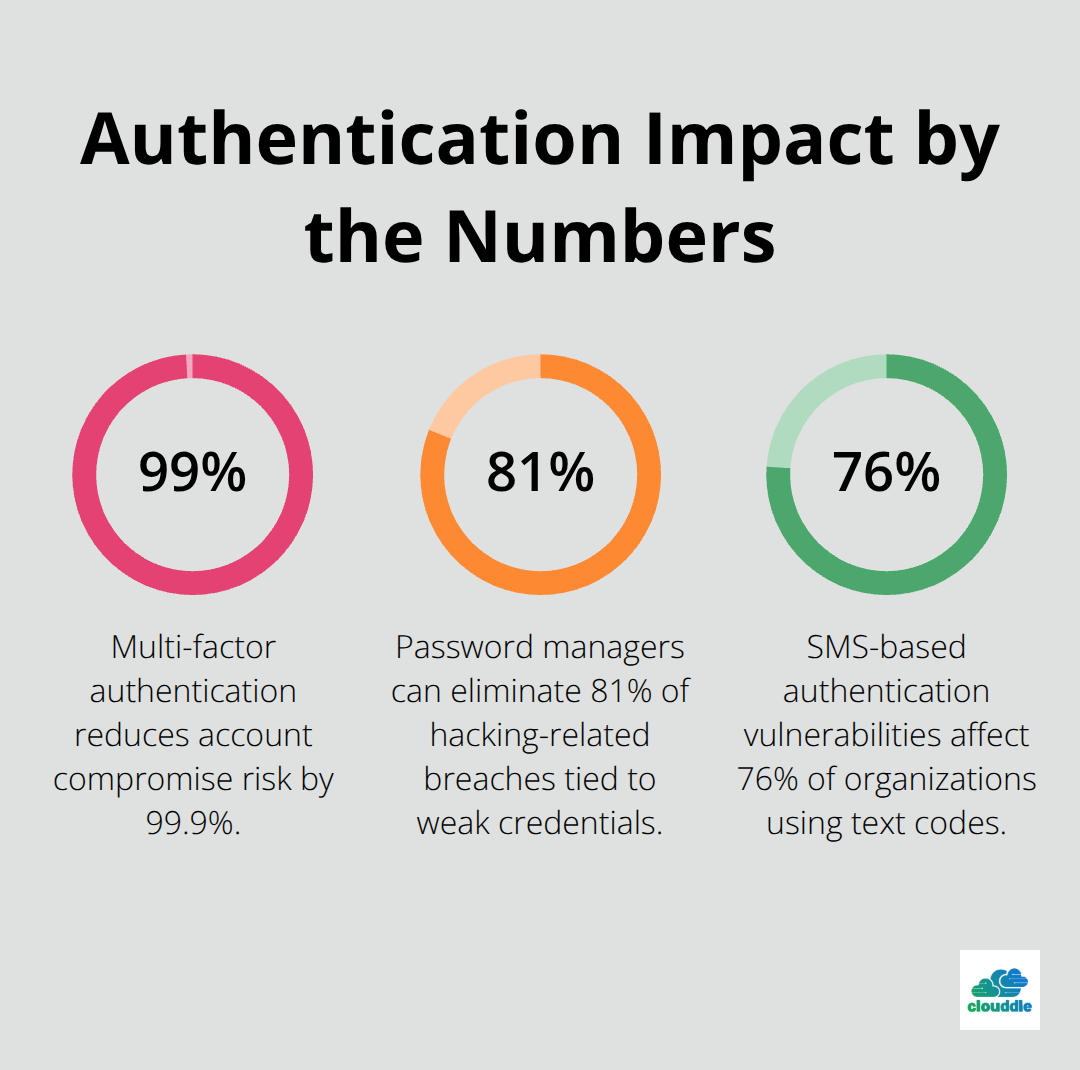
Authentication and Access Control
Password managers eliminate 81% of hacking-related breaches caused by weak credentials, according to Verizon’s 2023 Data Breach Report. Bitwarden offers enterprise-grade encryption at $3 per user monthly, while 1Password provides advanced sharing controls and travel mode features for $8 monthly. Multi-factor authentication reduces account compromise risk by 99.9%, making it essential for business accounts. Hardware tokens like YubiKey provide the strongest protection against phishing attacks, costing $25-70 per device but eliminating SMS-based vulnerabilities that affect 76% of organizations using text-based codes.
These foundational tools create your base security layer, but modern threats require specialized solutions that target specific attack vectors and business environments.
Which Protection Tools Stop Advanced Threats
Advanced Endpoint Security
VMware Carbon Black Cloud and CrowdStrike Falcon represent the gold standard for endpoint detection and response, catching threats that traditional antivirus misses. CrowdStrike achieved 99% detection coverage by conclusively reporting 75 of the 76 adversary techniques during the MITRE ATT&CK evaluation, and stops attacks within 6 minutes on average, compared to 200+ days for traditional solutions. These platforms use behavioral analysis to identify ransomware before encryption begins, saving companies an average of $3.2 million per incident (according to Sophos research). Implementation costs range from $8-15 per endpoint monthly, but the ROI becomes clear when considering that 70% of successful breaches start at endpoints.
Email Attack Prevention
Microsoft Defender for Office 365 and Proofpoint block 99.95% of phishing attempts, yet organizations still experience successful email attacks according to Proofpoint’s State of the Phish report. Advanced email security solutions analyze sender reputation, attachment behavior, and URL destinations in real-time. Mimecast reduces email-borne threats by 99.9% while cutting security management time by 50%. These tools cost $2-8 per user monthly but prevent average phishing losses of $4.9 million per successful attack. Configuration takes 24-48 hours, with most solutions integrating directly with existing email infrastructure without user disruption.
Network Visibility and VPN Security
Wireshark provides free network packet analysis for security teams, while enterprise solutions like SolarWinds offer comprehensive traffic monitoring across hybrid environments. Network monitoring tools detect lateral movement within 15 minutes compared to 287 days for unmonitored networks (according to IBM’s Threat Intelligence Index). NordLayer and Perimeter 81 lead business VPN solutions, encrypting data transmission and providing zero-trust network access. Business VPNs cost -12 per user monthly and reduce data breach risk by 58% when employees work remotely. Modern solutions integrate with identity providers and support WireGuard protocol for 40% faster connection speeds than traditional VPN technologies.
The effectiveness of these advanced tools depends heavily on proper selection and implementation strategies that match your specific business requirements and existing infrastructure.
How Do You Select Tools That Actually Work
Match Tools to Your Business Scale
Your business size directly determines which cybersecurity tools make financial sense and provide adequate protection. Companies with 1-50 employees need streamlined solutions that cost $50-500 monthly total, while enterprises require comprehensive platforms that cost $5,000+ monthly (according to Ponemon Institute research). Small businesses should prioritize cloud-based tools like Microsoft Defender for Business at per user monthly, which covers endpoint protection and email security in one package. Medium companies with 50-500 employees benefit from specialized tools like CrowdStrike Falcon Go at $8.99 per endpoint, which protects against all types of threats and deploys in minutes. Large enterprises must invest in enterprise-grade solutions with dedicated security operations centers, typically spending 3-5% of IT budgets on cybersecurity according to Gartner research.
Integration Requirements Matter More Than Features
Most cybersecurity tool failures happen because of poor integration, not inadequate protection capabilities. Tools must connect with your existing systems within 24-48 hours, or implementation costs increase by 200-400% (according to ESG research). Single sign-on compatibility reduces user resistance by 67% and cuts administrative overhead significantly. API availability determines long-term flexibility – solutions without robust APIs become security silos that block threat intelligence sharing.
Choose tools that support your current identity provider, whether Microsoft Active Directory, Okta, or Google Workspace, to maintain consistent access controls across your environment.
Calculate True Implementation Costs
Cybersecurity tool pricing extends far beyond licensing fees, with implementation and training adding 40-60% to initial costs (according to Forrester analysis). Factor in staff training time, which averages 40 hours per tool for proper deployment, plus ongoing maintenance that requires 10-15% of implementation time monthly. Hidden costs include compliance reporting features, premium support contracts, and data storage fees that can double annual expenses. Calculate ROI using average breach costs – $4.88 million globally according to IBM – versus tool investment over three years. Tools that pay for themselves within 18 months through prevented incidents or reduced insurance premiums represent sound investments for most organizations.
Final Thoughts
Strategic cybersecurity tools selection delivers better protection than random security purchases. Organizations that implement comprehensive protection see 67% fewer successful attacks and save $2.1 million annually compared to those with fragmented approaches. Start with foundational tools like next-generation firewalls, endpoint detection systems, and password managers before you add specialized solutions.
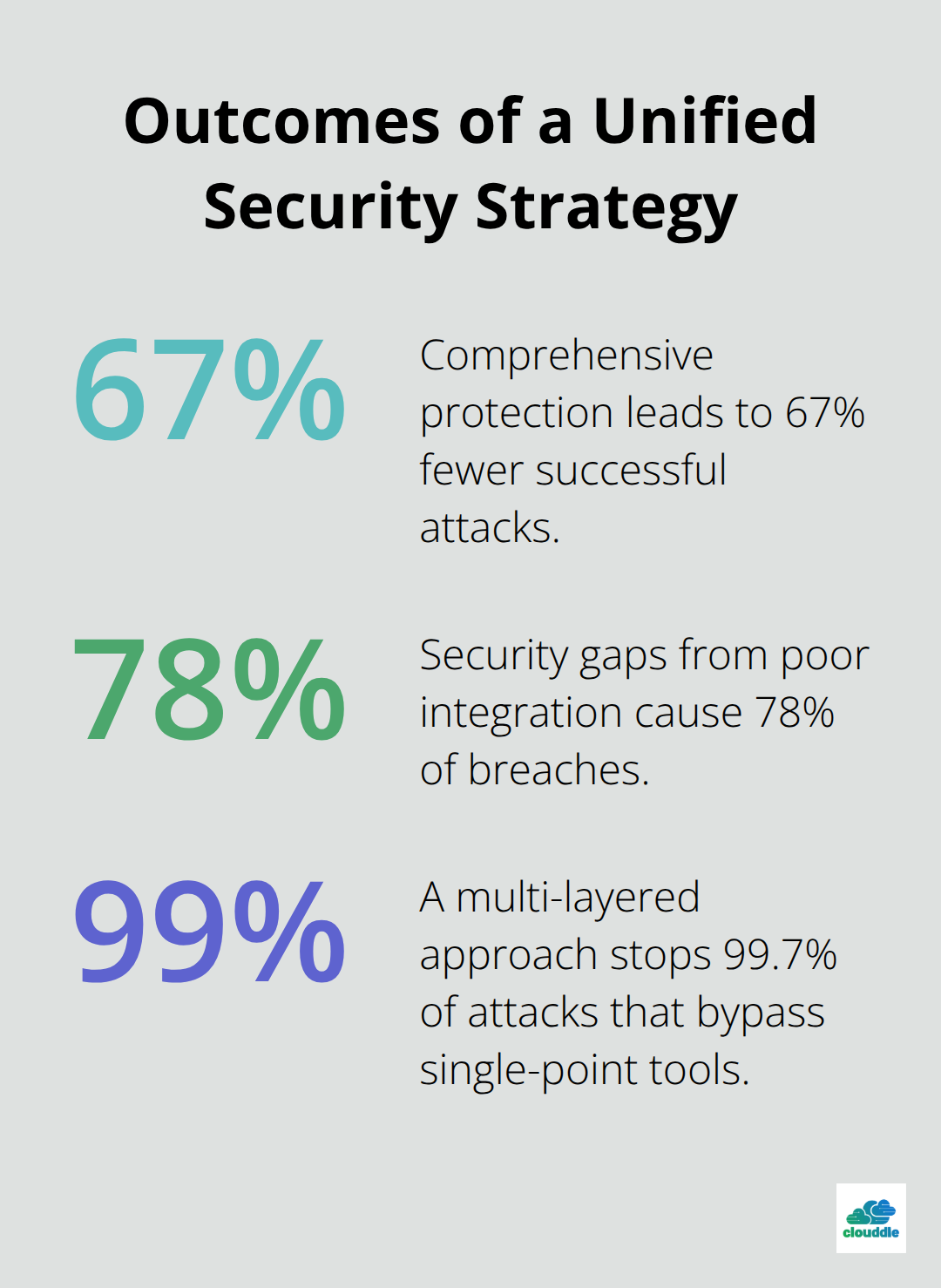
Integration capabilities matter more than individual features because tools that connect seamlessly prevent the security gaps that cause 78% of breaches. Budget plans must include hidden costs like training and maintenance (which add 40-60% to initial investments). Proper cybersecurity tools implementation pays for itself within 18 months through prevented incidents and reduced insurance premiums.
Layer your security strategy with network perimeter defense, endpoint protection, and user authentication controls. This multi-layered approach stops 99.7% of attacks that bypass single-point solutions. We at Clouddle provide managed IT and security services that combine networking, security, and support into unified protection strategies, helping businesses focus on growth while maintaining robust digital defenses.


