In an era of unprecedented volatility, from cyber threats and supply chain disruptions to natural disasters and economic shifts, the question isn’t if your business will face a disruption, but when. A reactive approach is a recipe for failure. Proactive resilience, built on a robust and well-tested business continuity plan (BCP), is the new competitive advantage.
This guide provides a definitive, actionable business continuity planning checklist, moving beyond generic advice to offer a detailed roadmap. We will break down the essential components, from initial risk assessments to advanced supply chain management, empowering you to protect your operations, assets, and reputation.
You will gain specific insights into:
- Identifying and prioritizing critical business functions.
- Establishing a clear crisis management command structure.
- Implementing failsafe data backup and recovery protocols.
- Preparing for remote operations and alternative work sites.
- Securing your vendor and partner relationships against disruption.
- Creating a multi-channel communication strategy.
- Testing your plan to ensure it works under pressure.
- Maintaining your BCP as a living, relevant document.
For businesses leveraging integrated technology solutions, like those provided by Clouddle Inc., a solid BCP ensures that your managed security, cloud, and network services continue to function as the backbone of your resilience strategy, even in the face of the unexpected. This checklist isn’t just a document; it’s a blueprint for enduring stability and growth. We will equip you with the tools to transform your organization from vulnerable to resilient, ensuring you can withstand and recover from any crisis that comes your way.
1. Risk Assessment and Business Impact Analysis (BIA)
The cornerstone of any effective business continuity planning checklist is a thorough Risk Assessment and Business Impact Analysis (BIA). This foundational step is not just a suggestion; it’s a systematic process for identifying potential threats to your business and understanding the full operational and financial impact if those threats materialize. A BIA helps you pinpoint vulnerabilities, prioritize your most critical functions, and determine how quickly each one must be restored to avoid unacceptable losses.
How It Works
The process involves two core activities. First, Risk Assessment identifies potential disruptions, from natural disasters like hurricanes to technological failures like a server crash or a major data breach. For each risk, you evaluate its likelihood and potential severity. Second, the Business Impact Analysis quantifies the consequences of a disruption to specific business functions over time. This helps define the Maximum Tolerable Downtime (MTD) for each process.
For example, after Hurricane Sandy, JPMorgan Chase’s BIA revealed that critical trading operations had a recovery time objective (RTO) of less than 15 minutes, prompting investment in redundant, geographically dispersed data centers. This level of granular analysis is what separates a theoretical plan from a practical, life-saving one.
Implementing Your BIA
To get started, involve department heads and key process owners. Their firsthand knowledge is invaluable for accurately assessing operational impacts.
- Categorize Functions: Start by identifying high-level business functions (e.g., Sales, Operations, Customer Support) before drilling down into the specific processes that support them.
- Use Standardized Metrics: Employ a consistent scoring matrix to rate the impact of a disruption across different areas, such as financial loss, customer dissatisfaction, and reputational damage.
- Determine Recovery Objectives: Based on the impact assessment, establish a Recovery Time Objective (RTO) and a Recovery Point Objective (RPO) for each critical function.
This BIA process provides a clear roadmap for your business continuity strategy. The following infographic illustrates the core workflow for conducting a comprehensive analysis.
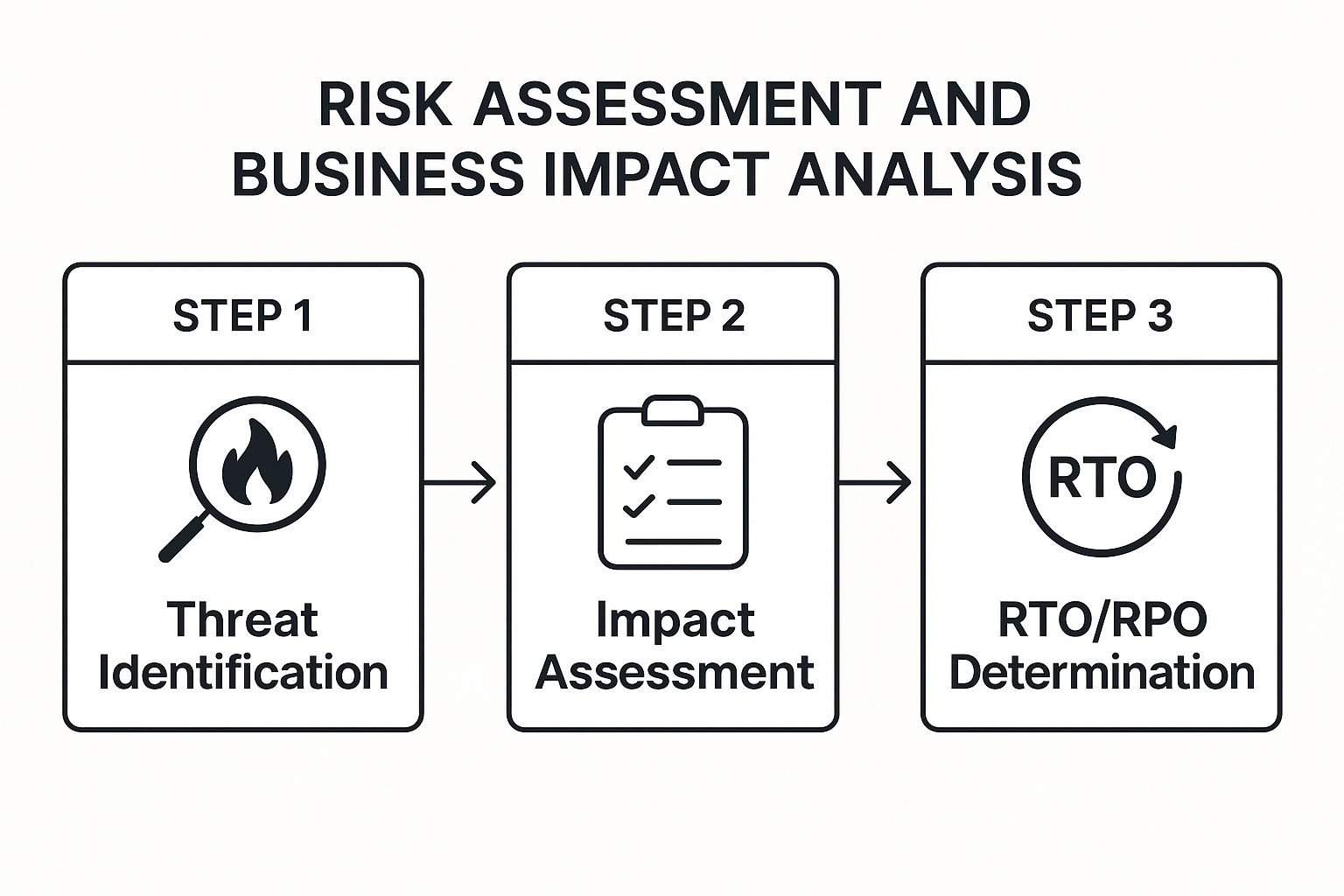
Following this sequential process ensures that your recovery objectives are directly tied to identified threats and their potential business impact. By completing a BIA, you move from guessing what’s important to knowing precisely what to protect and in what order, forming the strategic backbone of your entire business continuity plan. For a deeper dive into evaluating technology-specific vulnerabilities, our IT security audit checklist provides a complementary framework.
2. Crisis Management Team Structure and Roles
Once you have identified your risks, the next critical item on your business continuity planning checklist is establishing a formal Crisis Management Team (CMT). This team is your command center during a disruption, providing the leadership, decision-making, and communication necessary to navigate the chaos. A well-defined team structure prevents confusion, eliminates delays in response, and ensures that all actions are coordinated and aligned with the recovery objectives identified in your BIA.

How It Works
The core function of a Crisis Management Team is to centralize control and communication when a disruptive event occurs. This team is not responsible for performing the hands-on recovery tasks; rather, it directs the overall response strategy. The structure typically includes a team leader (often a senior executive), along with representatives from key departments like Operations, IT, HR, Legal, and Communications. Each member has a predefined role and the authority to make critical decisions related to their area of responsibility.
The gold standard for this approach was set during the 1982 Tylenol crisis. Johnson & Johnson’s CEO, James Burke, assembled a core team that immediately took decisive action, prioritizing public safety over short-term profits. This swift, centralized response not only saved the brand but also became a foundational case study in effective crisis management. More recently, Microsoft’s dedicated incident response teams for major Azure outages demonstrate a modern, technology-focused application of the same principle, ensuring rapid technical and customer communication.
Implementing Your CMT
To build an effective team, focus on roles rather than just titles. Ensure every critical function is covered and that there is clear accountability.
- Designate Primary and Backup Personnel: No single person should be a point of failure. Assign a primary and at least one backup for every critical role on the team to account for unavailability.
- Create Role-Specific Playbooks: Develop clear, concise action plans for each role. These “playbooks” should outline immediate responsibilities, step-by-step procedures, and key contacts, so team members can act decisively under pressure.
- Establish Clear Communication Protocols: Define how the team will communicate with each other, with employees, and with external stakeholders like vendors and emergency services. This includes setting up a primary communication channel (e.g., a dedicated conference line or chat group) and backups.
- Conduct Regular Tabletop Exercises: A plan on paper is untested. Run regular drills and simulations to test team coordination, identify gaps in your playbooks, and build the muscle memory needed for a real crisis.
A clearly defined CMT provides the human infrastructure needed to execute your business continuity plan. As outlined by frameworks from the Federal Emergency Management Agency (FEMA), this structure transforms your plan from a static document into a dynamic, actionable response capability, ensuring your organization can lead with confidence through any disruption.
3. Data Backup and Recovery Procedures
While a BIA identifies what’s critical, Data Backup and Recovery Procedures ensure that your most valuable asset, your data, can actually be restored after a disruption. This element of your business continuity planning checklist goes beyond simply saving files; it involves establishing comprehensive protocols for protecting, storing, and recovering the critical information and systems that power your operations. These procedures are the technical and procedural safety net that guarantees data integrity and availability when an incident occurs.
Effective backup and recovery is not a one-time task but a continuous cycle of protection and validation. For instance, Netflix’s famous “Chaos Monkey” tool intentionally disables production instances to test how the system responds to failure, including its ability to rely on backups. This proactive approach ensures their recovery processes are not just theoretical but proven to work under real-world stress, a core principle for any robust continuity strategy.

How It Works
This process involves defining what data needs protection, how often it should be backed up, where it will be stored, and the exact steps required to restore it. It aligns directly with the RTO and RPO identified in your BIA. The Recovery Point Objective (RPO) dictates the maximum acceptable amount of data loss, measured in time, and therefore determines your backup frequency. The Recovery Time Objective (RTO) defines how quickly you must restore that data, guiding your choice of technology and procedures.
For example, Salesforce’s ability to offer 99.9%+ uptime relies heavily on its sophisticated, multi-layered backup and recovery architecture. They use near real-time replication to secondary data centers, ensuring that in the event of a site failure, customer data can be recovered with minimal loss and within a very short timeframe. This commitment to data resilience is fundamental to their service delivery.
Implementing Your Backup and Recovery Plan
A successful strategy requires a clear, documented, and regularly tested plan. Start by engaging your IT team or a trusted technology partner to build a framework that fits your specific operational needs.
- Follow the 3-2-1 Rule: Maintain at least three copies of your data, store them on two different types of media (e.g., local disk and cloud), and keep one copy offsite to protect against localized disasters like fire or flood.
- Automate and Monitor: Use automated software to perform backups consistently and set up alerts that notify you immediately if a backup fails. Manual backups are prone to human error and are easily forgotten.
- Test Restores Regularly: Don’t assume your backups work. Schedule monthly or quarterly tests where you perform a full restore of a critical system or dataset to a test environment. This validates the integrity of your backup media and the accuracy of your recovery procedures.
- Document Everything: Create step-by-step recovery playbooks for different scenarios (e.g., server failure, ransomware attack, accidental deletion). These documents should be clear enough for any qualified IT professional to follow.
By creating and testing these procedures, you ensure your data is not only safe but also recoverable within a timeframe that aligns with your business requirements. For a more granular view of the technical steps involved, our comprehensive disaster recovery checklist provides a detailed, complementary guide.
4. Alternative Work Arrangements and Remote Operations
A critical component of a modern business continuity planning checklist is the ability to maintain operations when primary facilities are inaccessible. Establishing robust alternative work arrangements and remote operations ensures your team can remain productive, whether facing a localized event like a fire or a widespread disruption like a pandemic. This strategy focuses on building the technological and procedural infrastructure needed to support a distributed workforce, transforming potential downtime into a seamless operational pivot.

How It Works
This element of your plan involves creating a framework that decouples work from a physical location. It relies on a combination of technology, policy, and culture. The technology aspect ensures employees have secure access to necessary data, applications, and communication tools from any location. The policy aspect defines clear expectations for remote work, including communication protocols, security requirements, and performance metrics.
For example, Shopify’s transition to a “digital by default” model during the pandemic was successful because it was more than a technology shift; it was a cultural one. The company invested heavily in virtual collaboration tools and re-engineered its communication practices to thrive in a distributed environment. This proactive approach, also championed by fully remote companies like GitLab and Automattic, proves that with the right infrastructure, location becomes irrelevant to productivity.
Implementing Your Remote Operations Strategy
To build a resilient remote work model, focus on creating a comprehensive and well-tested system. Involve IT, HR, and department leaders to ensure all facets of the employee experience are covered.
- Invest in Cloud-First Architecture: Migrate critical systems and data to the cloud. This provides secure, scalable, and location-independent access to essential business tools.
- Equip Your Team for Success: Provide employees with necessary hardware, such as laptops and headsets, and consider internet stipends to ensure they have reliable connectivity.
- Establish Clear Remote Work Policies: Document guidelines on work hours, communication response times, data security protocols, and methods for measuring productivity.
- Test and Train Regularly: Don’t wait for a disaster. Conduct regular tests of your remote access systems, VPNs, and backup connectivity options to identify and resolve issues before they become critical.
By embedding alternative work arrangements into your operational DNA, you build resilience and agility. This approach not only prepares you for disruptions but also provides a competitive advantage by attracting talent and enabling greater operational flexibility, making it an indispensable part of your business continuity planning checklist. For more insights on securing your distributed workforce, consider exploring resources on remote employee security best practices.
5. Vendor and Supply Chain Risk Management
A modern business continuity planning checklist is incomplete without addressing external dependencies. Vendor and Supply Chain Risk Management is the process of identifying, assessing, and mitigating risks associated with your third-party partners, from raw material suppliers to critical software-as-a-service (SaaS) providers. In an interconnected economy, your organization’s resilience is directly tied to the resilience of your supply chain, making this a non-negotiable component of any robust BCP.
How It Works
This process extends your internal risk analysis to your entire network of suppliers and service providers. It begins with Vendor Identification and Criticality Assessment, where you map out all third parties and classify them based on how essential their product or service is to your operations. This is followed by Risk Evaluation, where you analyze the specific vulnerabilities of each critical vendor, such as their geographic location, financial stability, or their own BCP maturity. The goal is to proactively manage these dependencies before they can cause a disruption.
For example, after the 2011 tsunami in Japan, Apple’s well-developed supplier diversification strategy allowed it to shift production away from affected suppliers with minimal impact. This foresight, born from rigorous supply chain risk management, prevented catastrophic delays and financial losses, highlighting the value of not putting all your operational eggs in one basket.
Implementing Your Supply Chain Strategy
Effective implementation requires a proactive and collaborative approach with your partners. Start by integrating continuity planning into your procurement and vendor management lifecycle.
- Classify Vendors by Criticality: Tier your suppliers based on their impact on your business. A “Tier 1” vendor might be the sole provider of a critical component, while a “Tier 3” vendor provides office supplies. Focus your efforts on Tier 1 and 2.
- Require BCP Transparency: Make it a contractual obligation for critical vendors to provide you with a summary of their own business continuity plans. This ensures they are as prepared for a disaster as you are.
- Establish Backup Relationships: Identify and pre-qualify alternative suppliers for critical goods and services. Even if you don’t use them regularly, having these relationships in place can drastically reduce recovery time.
- Conduct Regular Audits: Periodically review the financial health and operational capabilities of your key vendors. This is especially vital when selecting a long-term partner for essential services; for more on this, see our guide on choosing a managed service provider.
By systematically managing vendor risk, you build a protective buffer around your core operations. This transforms your BCP from an internal document into a comprehensive resilience strategy that accounts for the external forces your business depends on.
6. Communication Plans and Stakeholder Management
A critical, yet often underestimated, component of any business continuity planning checklist is a robust Communication Plan. When a disruption occurs, technology and operations are only half the battle; maintaining trust and confidence with employees, customers, suppliers, and investors is paramount. A structured communication plan ensures that accurate, consistent, and timely information is disseminated to all stakeholders, preventing panic, misinformation, and reputational damage.
How It Works
The core function of a crisis communication plan is to control the narrative. This involves pre-defining who says what, to whom, and through which channels. Instead of improvising under pressure, your team follows a pre-approved protocol. The plan identifies key stakeholders, maps out their specific information needs, and establishes a clear chain of command for releasing communications. It moves your response from reactive damage control to proactive stakeholder management.
For example, when Southwest Airlines faced a massive operational meltdown during the 2022 holidays, their initial communication was criticized as slow and insufficient, worsening customer frustration. This highlights the lesson that a plan must be ready for immediate activation. In contrast, Zoom’s transparent communication about its security and capacity challenges during the COVID-19 pandemic helped it maintain user trust while it rapidly scaled its infrastructure.
Implementing Your Communication Plan
Effective implementation requires forethought and preparation long before a crisis hits. Your goal is to create a communication toolkit that can be deployed at a moment’s notice.
- Develop Message Templates: Pre-draft messages for various scenarios like power outages, cyberattacks, or supply chain disruptions. These templates for internal memos, social media posts, press releases, and customer emails will save critical time.
- Establish a Communication Team: Designate a primary spokesperson and a small, empowered communication team. This ensures a single source of truth and prevents conflicting messages from different departments.
- Segment Stakeholders and Channels: Create distinct communication strategies for different groups. Employees might need operational details via an emergency text system, while customers require reassurance through email and social media.
- Practice and Refine: Integrate communication drills into your tabletop exercises. Test your ability to draft and release information under simulated pressure to identify weaknesses in your plan.
A well-executed communication strategy is the key to preserving stakeholder relationships and protecting your brand’s reputation during a business interruption. The following video provides further insight into crafting a crisis communication plan.
By prioritizing clear and strategic communication, you ensure that stakeholders remain informed and confident in your ability to manage the crisis. This element of your business continuity plan is not just about public relations; it is a fundamental pillar of operational resilience.
7. Testing, Training, and Exercise Programs
A business continuity plan that exists only on paper is functionally useless. This is why a rigorous program of testing, training, and exercises is a non-negotiable component of any serious business continuity planning checklist. This systematic validation process ensures your plan is not just a theoretical document but a practical, effective tool that your team can execute flawlessly under the extreme pressure of a real crisis. It reveals weaknesses, confirms assumptions, and builds muscle memory for response teams.
How It Works
This process involves regularly validating your BCP through simulated events. Testing focuses on specific components, like checking if backup systems can be restored within the required timeframe. Training equips employees with the knowledge and skills needed to perform their roles during a disruption. Exercises bring it all together, simulating a crisis scenario to test the plan, technology, and people in an integrated way.
For instance, Amazon Web Services (AWS) famously runs “GameDay” exercises, where engineers are tasked with breaking their own systems to find vulnerabilities before they cause real-world outages. Similarly, British Airways conducts extensive crisis simulations following major IT incidents to ensure its response teams are prepared for future disruptions, reflecting a commitment to turning past failures into future strengths.
Implementing Your Testing Program
A successful program should be built incrementally, starting simple and growing in complexity. This approach builds confidence and capability without overwhelming your organization.
- Start with Tabletop Exercises: Begin with discussion-based sessions where team members walk through a simulated scenario, discussing their roles and responses without any actual technical failovers. This is a low-cost way to identify major gaps in the plan.
- Vary Scenarios: Don’t just test for a data center failure. Run exercises based on different threats identified in your BIA, such as a cyberattack, a key supplier failure, or a localized natural disaster. Surprise drills can offer a true test of your team’s real-world readiness.
- Involve External Stakeholders: Your business doesn’t operate in a vacuum. Include critical vendors, key clients, and even local emergency services in relevant exercises to ensure your coordinated response is seamless.
- Document and Iterate: Treat every exercise as a learning opportunity. Meticulously document what worked, what didn’t, and any unexpected challenges. Use these “lessons learned” to immediately update and improve your BCP.
As promoted by leading bodies like the Business Continuity Institute (BCI) and the Disaster Recovery Institute International (DRI), this continuous cycle of testing and refinement is what transforms a static plan into a dynamic and resilient organizational capability. It ensures that when a crisis hits, your response is not one of panic but of practiced, confident execution.
8. Plan Documentation and Maintenance
A business continuity plan is only effective if it is clearly documented, regularly updated, and immediately accessible when a crisis hits. Plan Documentation and Maintenance is the systematic process of creating, versioning, and preserving all BCP-related information. This crucial step on any business continuity planning checklist ensures that your strategies are not just theoretical but are codified into actionable, reliable guides that your team can execute under pressure.
How It Works
This process involves translating your BIA, recovery strategies, and communication plans into a set of formal documents. The core activity is not just writing the plan but establishing a lifecycle for it. This includes version control to track changes, secure storage in multiple formats and locations (both physical and cloud-based), and a scheduled review process to ensure the plan remains aligned with evolving business operations, technologies, and risks.
For instance, following the ISO 22301 standard, organizations like Microsoft integrate their business continuity documentation directly into their broader security and operational frameworks. This means that a change in a key software system automatically triggers a review of the associated recovery documentation, ensuring the plan never becomes obsolete. This moves documentation from a static file to a living component of your operational resilience.
Implementing Your Plan Documentation
To create a robust and maintainable plan, focus on clarity, accessibility, and accountability. A plan that no one can find or understand is useless in an emergency.
- Create Multiple Formats: Develop a detailed, comprehensive plan for reference and a separate, condensed quick-reference guide or “grab-and-go” checklist for immediate actions.
- Assign Clear Ownership: Make specific individuals or departments responsible for maintaining each section of the plan. This accountability is vital for keeping information current.
- Establish a Review Cadence: Schedule regular reviews of the BCP, tying them to the business calendar. For example, conduct an annual review in Q4 or after any significant organizational change, such as a merger or new product launch.
- Use Simple Language: Write the plan in clear, simple language, avoiding technical jargon wherever possible. The goal is for anyone on the response team to understand their role and responsibilities without needing a translator.
By formalizing the documentation and maintenance process, you ensure that your business continuity plan is a reliable and practical tool. It provides the structured guidance needed to navigate a disruption confidently, ensuring that everyone knows exactly what to do, when to do it, and how. This disciplined approach transforms your BCP from a binder on a shelf into a cornerstone of your organization’s resilience. For more guidance on creating structured technical documents, the framework outlined in NIST Special Publication 800-34 offers a valuable reference.
Business Continuity Planning Checklist Comparison
| Item | Implementation Complexity 🔄 | Resource Requirements ⚡ | Expected Outcomes 📊 | Ideal Use Cases 💡 | Key Advantages ⭐ |
|---|---|---|---|---|---|
| Risk Assessment and Business Impact Analysis (BIA) | High – extensive stakeholder input needed | Moderate – requires dedicated time & tools | Clear prioritization of risks and impacts | Foundational risk evaluation for all organizations | Data-driven planning foundation; compliance support |
| Crisis Management Team Structure and Roles | Moderate – defining roles and protocols | Moderate – ongoing training and maintenance | Rapid, coordinated crisis response | Organizations needing defined crisis leadership | Fast decision-making; clear accountability |
| Data Backup and Recovery Procedures | High – complex infrastructure and testing | High – storage, security, and monitoring | Minimized data loss; rapid recovery | Data-critical businesses requiring high availability | Data protection; regulatory compliance |
| Alternative Work Arrangements and Remote Operations | Moderate – requires technology setup | Moderate – investment in remote tools and security | Business continuity with flexible work locations | Businesses needing location-independent operations | Cost-effective continuity; operational flexibility |
| Vendor and Supply Chain Risk Management | High – ongoing due diligence and monitoring | Moderate to High – coordination and auditing | Reduced supply chain disruptions | Companies reliant on multiple suppliers | Risk reduction; supplier visibility |
| Communication Plans and Stakeholder Management | Moderate – preparation and updating of templates | Moderate – resource allocation for communication | Maintained stakeholder trust and clear messaging | Organizations needing structured crisis communication | Reduces misinformation; supports compliance |
| Testing, Training, and Exercise Programs | High – regular, resource-intensive exercises | High – time and personnel involvement | Validated plans and trained personnel | Organizations focused on plan effectiveness and readiness | Identifies gaps; builds competence |
| Plan Documentation and Maintenance | Moderate – requires continuous updates | Moderate – administrative and storage needs | Up-to-date, accessible continuity plans | All organizations needing structured documentation | Consistency; supports knowledge transfer |
Transforming Your Plan into a Resilient Reality
Navigating the intricacies of a comprehensive business continuity planning checklist is a significant achievement. You have moved beyond abstract concepts and delved into the specific, actionable steps required to safeguard your organization. From conducting a thorough Business Impact Analysis to defining crisis management roles and establishing robust communication protocols, you have laid the groundwork for genuine operational resilience. However, the true mark of a successful BCP isn’t the completion of a document; it’s the integration of preparedness into the very fabric of your company culture.
Think of your BCP not as a static manual collecting dust on a shelf, but as a living, breathing component of your strategic operations. The business landscape is in constant flux. New technologies emerge, supply chains evolve, and unforeseen risks materialize. Your plan must evolve in tandem to remain effective. This transformation from a documented plan to a resilient reality hinges on a continuous cycle of review, refinement, and practice.
Key Takeaways: From Checklist to Capability
To ensure your efforts translate into tangible security, let’s distill the core principles from our checklist into three essential pillars of ongoing success:
- Pillar 1: Proactive Analysis. Your initial Risk Assessment and BIA were foundational. Now, make this analysis a recurring event. Schedule annual or semi-annual reviews to re-evaluate threats, assess the impact of new business processes, and update recovery time objectives. A new key software vendor or a shift to a hybrid work model fundamentally changes your risk profile and must be reflected in your plan.
- Pillar 2: Empowered People. A plan is only as good as the people who execute it. Your Crisis Management Team needs more than just assigned titles; they need regular training and realistic drills. Moving beyond simple tabletop exercises to functional drills, where teams actually perform recovery tasks (like restoring data from a backup or setting up an alternative communication channel), builds muscle memory and exposes hidden flaws in your procedures.
- Pillar 3: Dynamic Documentation. Your BCP document is your single source of truth during a crisis. It must be accessible, current, and easy to understand. Storing it solely on a local server that could be compromised during a flood or cyberattack is a critical oversight. Utilize secure, cloud-based platforms and ensure key personnel have offline access to essential contact lists and protocols. Regularly audit contact information, vendor details, and procedural steps to eliminate outdated information.
Key Insight: Resilience is not a one-time project; it is an ongoing operational discipline. The goal is to move from “having a plan” to “being a prepared organization,” where every team member understands their role in maintaining continuity.
The True Value of a Well-Maintained BCP
Ultimately, the exhaustive work detailed in this business continuity planning checklist delivers value far beyond disaster recovery. It fosters a culture of proactive problem-solving and risk awareness that permeates every level of your business. It enhances stakeholder confidence, from investors and clients who see you as a stable partner to employees who feel secure in their workplace. This process forces you to understand your own operations on a granular level, often revealing inefficiencies and opportunities for process improvement that benefit you every single day, not just during a crisis.
By committing to this continuous cycle of planning, testing, and improving, you are not just preparing for the worst-case scenario. You are building a more agile, robust, and future-proof enterprise capable of thriving in an unpredictable world. Don’t let this momentum fade. Take the final, crucial step from planning to action and solidify the resilience you’ve worked so hard to design.
Is your IT infrastructure a potential point of failure in your business continuity plan? Secure your data, enable seamless remote operations, and ensure rapid recovery with the expert managed technology solutions from Clouddle Inc. Let us handle the complexities of your IT resilience so you can focus on leading your business through any challenge.


