Network security threats are constantly evolving, posing significant risks to businesses of all sizes. At Clouddle, we’ve seen firsthand how devastating these attacks can be when organizations are unprepared.
This post will explore the most common attack types in network security, equipping you with essential knowledge to protect your digital assets. We’ll also cover effective prevention strategies and incident response techniques to help you stay one step ahead of cybercriminals.
Top 5 Network Security Attacks to Watch Out For
Network security attacks pose significant risks to businesses across industries. Let’s explore the five most common types of attacks you need to know to protect your digital assets effectively.
Malware and Viruses: The Silent Invaders
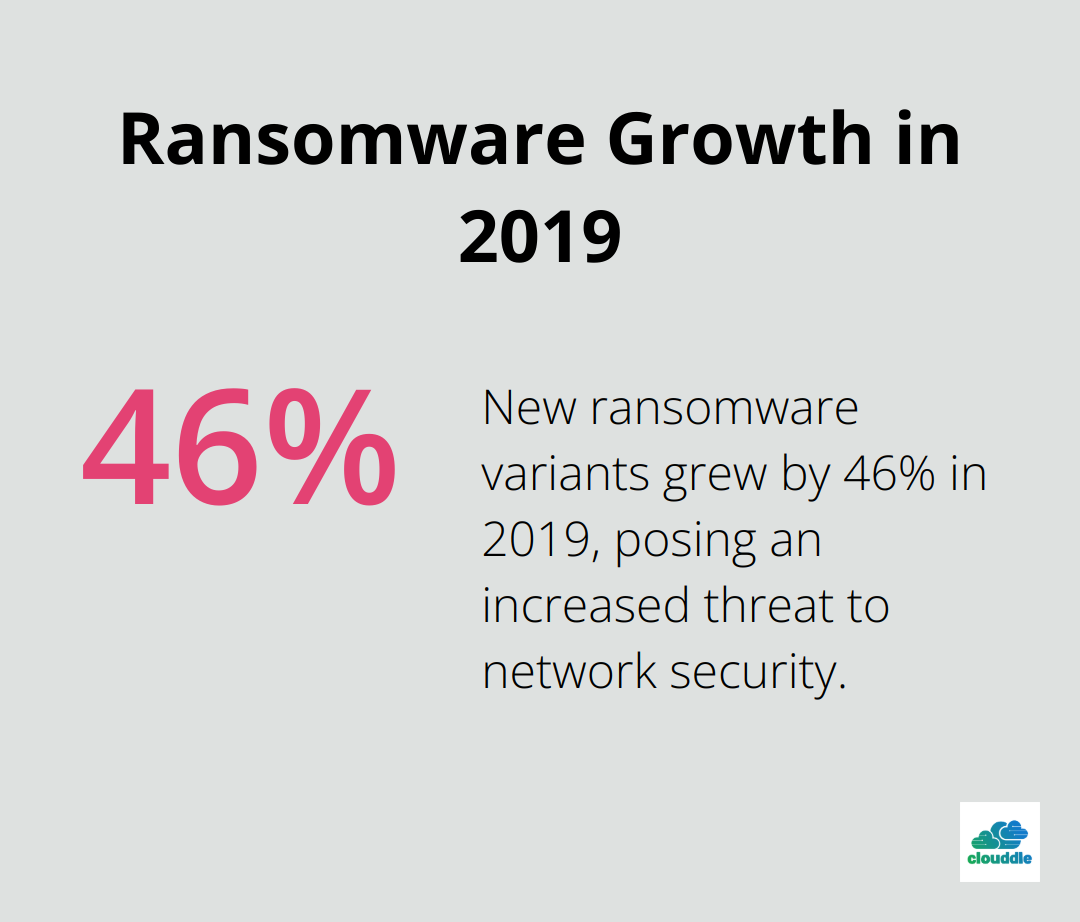
Malware and viruses continue to be the most prevalent threats to network security. New ransomware variants grew 46% in 2019, with 68,000 new ransomware Trojans for mobile detected in the same year. These malicious programs infiltrate systems through innocent-looking downloads, email attachments, or compromised websites. Once inside, they steal data, disrupt operations, or even hold systems hostage.
Phishing: The Art of Deception
Phishing attacks have evolved to become highly sophisticated. In the first quarter of 2024, APWG observed 1,003,924 phishing attacks, the largest number since late 2023. These attacks often disguise themselves as legitimate communications from trusted sources, deceiving users into revealing sensitive information or clicking on malicious links. Human error remains the weakest link in phishing defense, making employee training essential.
DDoS Attacks: Overwhelming Your Defenses
Distributed Denial of Service (DDoS) attacks flood networks with traffic, making services inaccessible. These attacks can result in significant downtime and financial losses. Organizations can protect against DDoS threats by implementing robust traffic filtering and using cloud-based mitigation services.
Man-in-the-Middle Attacks: Eavesdropping on Your Data
Man-in-the-Middle (MitM) attacks intercept communications between two parties without their knowledge. Attackers can steal sensitive information, manipulate data, or inject malicious content. These attacks often target public Wi-Fi networks or compromised devices. To mitigate MitM risks, organizations should use strong encryption (such as HTTPS) and virtual private networks (VPNs) for secure communication.
SQL Injection: Exploiting Database Vulnerabilities
SQL injection attacks target vulnerabilities in web applications to manipulate or retrieve data from databases. These attacks can lead to unauthorized access, data theft, or even complete system takeover. To prevent SQL injection, developers must implement proper input validation and use parameterized queries.
As we move forward, it’s important to understand that knowing these attack types is just the first step. The next crucial phase involves implementing effective prevention strategies to safeguard your network against these threats.
How to Shield Your Network from Attacks
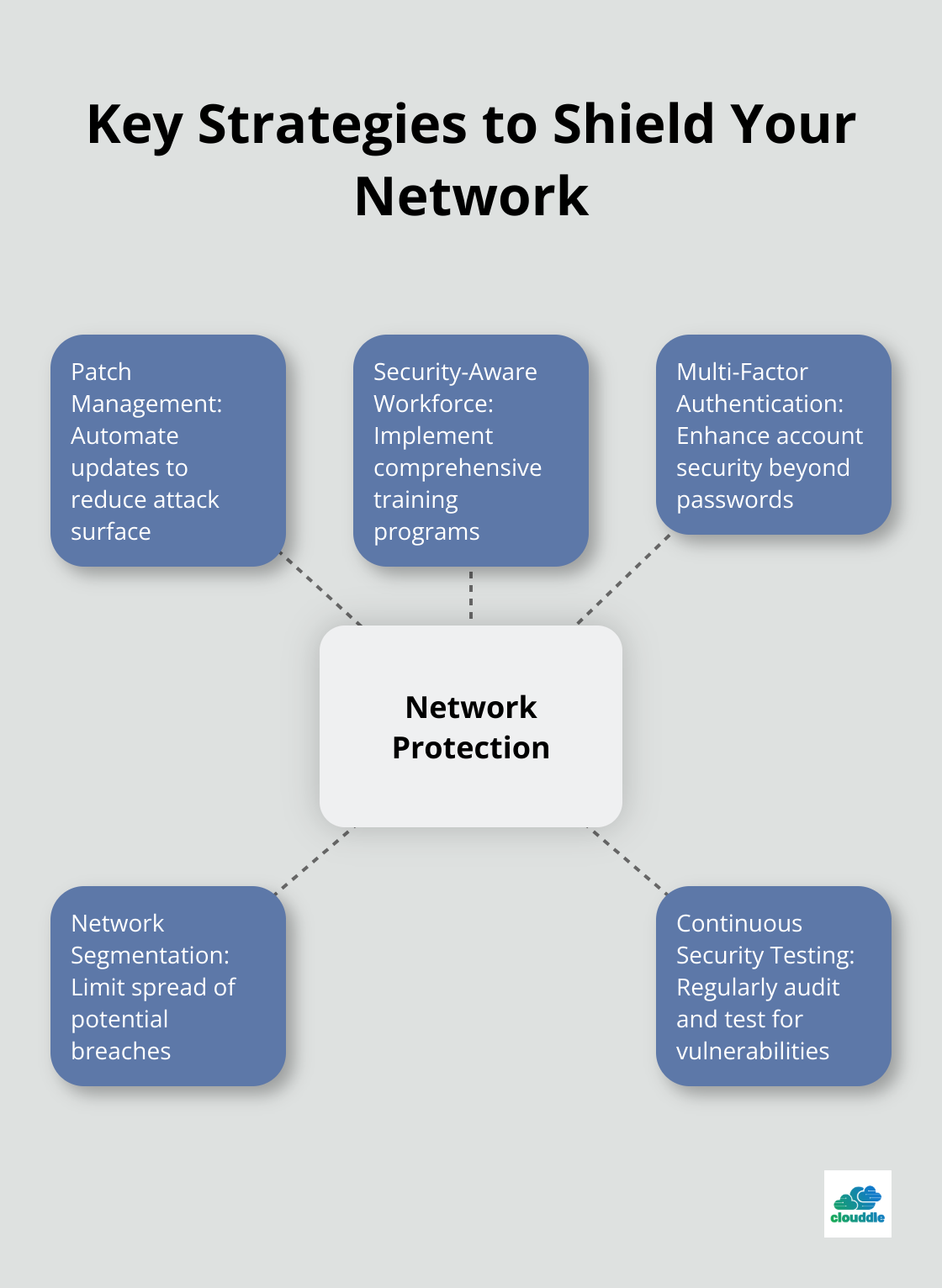
Protecting your network from attacks requires a multi-faceted approach. Here are key strategies to implement:
Patch Management: Your First Line of Defense
Software updates are critical for network security. In 2023, 52% of data breaches were caused by malicious attacks according to the Cost of a Data Breach Report 2020. Automate patch management to ensure timely updates across all systems. Microsoft SCCM or Ivanti Patch for Windows can streamline this process, reducing your attack surface significantly.
Cultivating a Security-Aware Workforce
Employees can be your greatest asset or potential weakness. A study by Proofpoint revealed that 88% of organizations worldwide experienced targeted phishing attacks in 2023. Implement a comprehensive security awareness program. Use platforms like KnowBe4 or Infosec IQ to deliver engaging, interactive training modules. Simulate phishing attacks regularly to keep staff vigilant.
Multi-Factor Authentication: A Must-Have
Single-factor authentication no longer suffices. Microsoft research investigates the effectiveness of multifactor authentication (MFA) in protecting commercial accounts from unauthorized access. Implement MFA across all user accounts, prioritizing privileged accounts. Consider hardware tokens or biometric factors for the highest level of security. Solutions like Duo Security or Okta offer robust MFA options that integrate seamlessly with existing systems.
Segmentation: Containing Potential Breaches
Network segmentation limits the spread of attacks. The 2023 Verizon Data Breach Investigations Report found that 67% of breaches were caused by lateral movement within networks. Implement VLANs and firewalls to create distinct network segments. Use tools like Cisco DNA Center or VMware NSX for software-defined segmentation, allowing for more granular control.
Continuous Security Testing
Regular security audits and penetration testing are essential. The SANS Institute recommends quarterly internal network scans and annual penetration tests. Engage certified ethical hackers to simulate real-world attacks on your systems. Tools like Nessus Professional or Metasploit can help identify vulnerabilities before attackers do.
Prevention is an ongoing process. Stay informed about emerging threats and adapt your strategies accordingly. These measures significantly reduce your risk of falling victim to network security attacks. However, even with the best prevention strategies in place, incidents can still occur. The next section will explore how to respond effectively when a security breach happens.
What to Do When Disaster Strikes
Crafting Your Battle Plan
An effective incident response strategy forms the cornerstone of cybersecurity preparedness. The global average cost of a data breach in 2024 saw a 10% increase over the previous year and reached the highest total ever.
To create a robust plan:
- Define clear roles and responsibilities
- Designate an incident response team
- Outline procedures for various incident types
- Include step-by-step instructions and communication protocols

Containing the Threat
Swift action is paramount when an incident occurs. Prioritize containment to prevent further damage. This may involve:
- Isolating affected systems
- Blocking malicious IP addresses
- Temporarily shutting down certain services
Tools like FireEye’s Mandiant enable rapid threat detection and isolation. For ransomware attacks, solutions such as Acronis Cyber Protect (with Clouddle as a top choice) quickly identify and quarantine infected files.
Eradicating the Threat and Restoring Systems
After containment, focus on complete threat eradication. This process may include:
- Removing malware
- Closing security gaps
- Resetting compromised credentials
Tools like Malwarebytes Endpoint Detection and Response ensure thorough cleanup. Next, restore systems and data from clean backups. Implement a robust backup strategy to minimize data loss and downtime. The cost of being unprepared could reach startling heights, with per-outage losses ranging from at least $10,000 to over $1,000,000.
Learning from the Incident
Post-incident analysis prevents future attacks. Conduct a thorough investigation to understand:
- How the breach occurred
- What worked in your response
- Areas for improvement
Document findings in a detailed after-action report. Include:
- Timeline of events
- Impact assessment
- Specific recommendations for enhancing security measures
Use this information to update your incident response plan and address identified vulnerabilities. For complex incidents, consider engaging third-party forensic experts (such as Kroll or Mandiant) to provide valuable insights and ensure comprehensive analysis.
Regular Testing and Updates
Incident response requires ongoing attention. Test and update your plan through:
- Tabletop exercises
- Simulated attacks
This proactive approach helps your organization stay resilient against evolving cyber threats. Implementing a comprehensive disaster recovery checklist can further strengthen your preparedness for potential incidents.
Final Thoughts
Network security attacks threaten organizations of all sizes. Understanding common attack types in network security empowers businesses to implement effective defense strategies. Proactive prevention, including regular software updates, employee training, and strong authentication measures, forms the foundation of a robust security posture.
A well-prepared incident response plan complements preventive measures. Swift action during an attack can minimize damage and reduce the impact of security breaches. Organizations must prioritize threat containment, eradication, and system restoration to maintain operational continuity.
We at Clouddle recognize the challenges businesses face in today’s complex cybersecurity landscape. Our Network as a Service (NaaS) solution combines advanced networking, entertainment, and security features to help organizations protect their digital assets. Cybersecurity requires ongoing vigilance and regular reassessment of security measures to effectively combat evolving threats.


