Network security audits are essential for safeguarding your organization’s digital assets. These comprehensive evaluations help identify vulnerabilities, assess risks, and strengthen your overall security posture.
At Clouddle, we understand the critical role these audits play in maintaining a robust defense against cyber threats. This guide will walk you through the key steps and best practices for conducting thorough network security audits, ensuring your organization stays protected in an ever-evolving threat landscape.
What Are Network Security Audits?
Definition and Purpose
Network security audits are detailed evaluations of an organization’s IT infrastructure to identify vulnerabilities, risks, and compliance issues. These audits play a vital role in protecting sensitive data, maintaining regulatory compliance, and preventing costly breaches.
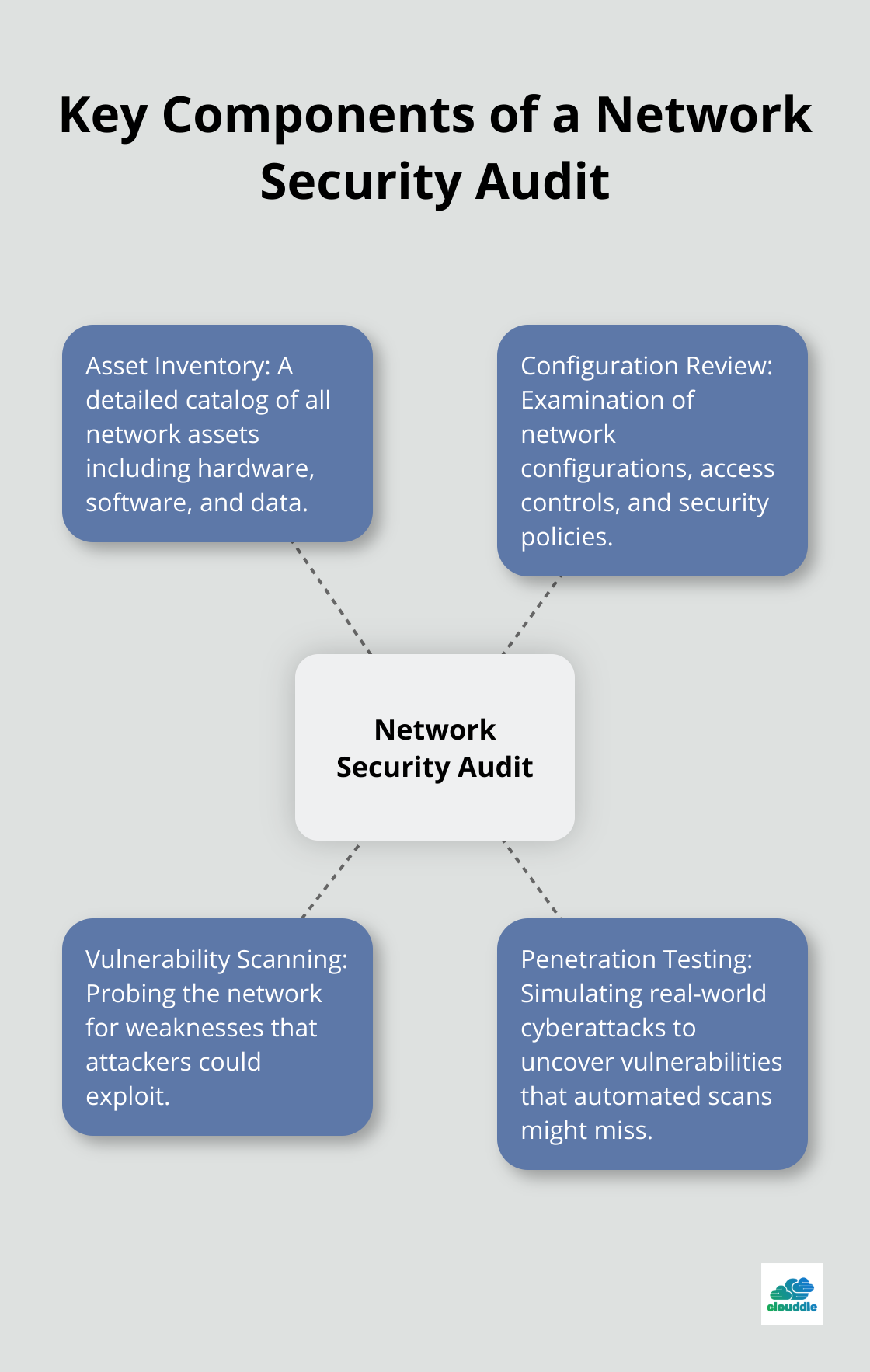
Key Components of a Network Security Audit
A thorough network security audit includes several essential elements:
- Asset Inventory: This involves a detailed catalog of all network assets (hardware, software, and data). Understanding the full scope of what needs protection is critical.
- Configuration Review: Auditors examine network configurations, access controls, and security policies to ensure alignment with best practices and compliance requirements.
- Vulnerability Scanning: Specialized tools probe the network for weaknesses that attackers could exploit. This process often reveals issues like outdated software, misconfigured firewalls, or weak passwords.
- Penetration Testing: Also known as ethical hacking, this simulates real-world cyberattacks to uncover vulnerabilities that automated scans might miss. According to Getastra, 1 in 5 companies do not test their software for security vulnerabilities.
Timing and Frequency Considerations
The frequency of network security audits depends on various factors:
- Industry regulations
- Sensitivity of handled data
- Overall risk profile of the organization
Most experts recommend conducting a full audit at least annually. High-risk industries (e.g., finance or healthcare) may require more frequent audits. For instance, the Health Insurance Portability and Accountability Act (HIPAA) requires covered entities to perform a security risk analysis whenever significant changes occur in their IT environment.
Additional audits are necessary after major changes to network infrastructure, such as:
- Implementing new systems
- Migrating to cloud services
These transition periods often introduce new vulnerabilities that need prompt addressing.
The Impact of Neglecting Audits
Failing to conduct regular network security audits can have severe consequences. IBM’s Cost of a Data Breach Report revealed that the average cost of a data breach reached $4.35 million in 2022. This figure doesn’t account for long-term damage to reputation and customer trust that often follows a significant security incident.

Regular, thorough network security audits allow organizations to identify and address vulnerabilities before exploitation. This proactive approach can potentially save millions in breach-related costs and preserve reputation in an increasingly security-conscious market.
As we move forward, it’s important to understand the specific steps involved in conducting a comprehensive network security audit. Let’s explore the planning, execution, and reporting phases that make up an effective audit process.
How to Conduct a Network Security Audit
Planning and Preparation
The first step in any successful audit requires thorough planning. Define clear objectives and scope. Determine which systems to include and which compliance standards to meet. A survey by Ponemon Institute reveals that 60% of organizations face challenges with audit scoping, often resulting in incomplete assessments.
Assemble your audit team next. Include IT staff, security specialists, and potentially external consultants. Assign roles and responsibilities clearly to ensure smooth execution.
Create a detailed timeline for the audit process. Consider potential disruptions to normal business operations. Communicate this schedule to all stakeholders to minimize resistance and ensure cooperation.
Data Collection and Analysis
With your plan in place, start gathering data. This includes network diagrams, asset inventories, security policies, and access logs. Use automated tools to collect information on network traffic, user activities, and system configurations.
Gartner reports that organizations which automate more than 70% of their network management tasks reduce downtime by an average of 50%. Tools like network scanners and log analyzers can significantly speed up this process.
Analyze the collected data to identify patterns, anomalies, and potential security gaps. Look for inconsistencies between documented policies and actual practices. Pay special attention to privileged access accounts (often targets for attackers).
Vulnerability Assessment
Now, actively probe your network for weaknesses. Start with vulnerability scans using tools like Nessus or OpenVAS. These scans can identify known vulnerabilities in your systems and applications.
Follow up with penetration testing. This simulates real-world attack scenarios to uncover vulnerabilities that automated scans might miss.
Don’t overlook social engineering tests. The human element often represents the weakest link in security. Simulated phishing campaigns can reveal gaps in employee awareness and training.
Reporting and Recommendations
The final step involves compiling your findings into a comprehensive report. This should include:
- An executive summary for non-technical stakeholders
- Detailed findings, categorized by severity
- Specific, actionable recommendations for addressing each vulnerability
- A proposed timeline for implementing fixes
Prioritize your recommendations based on risk level and potential impact. The SANS Institute reports that 80% of cyber attacks exploit known vulnerabilities with available patches. Focus on these low-hanging fruit first.
An audit’s value lies in the actions it inspires. Work closely with IT and management to develop a remediation plan. Set clear deadlines and assign responsibility for each task.
The insights gained from each audit should refine your security policies and procedures. Regular audits, combined with ongoing monitoring, form the backbone of a robust security posture.
As we move forward, let’s explore common network vulnerabilities and their solutions to further enhance your organization’s security measures. Conduct thorough vendor assessments to ensure all aspects of your network security are covered.
Exposing Common Network Vulnerabilities
The Danger of Outdated Software
Outdated software and firmware represent one of the most prevalent vulnerabilities in network security. A Ponemon Institute study revealed that 52% of data breaches were caused by malicious attacks. Many organizations fail to update their systems promptly due to concerns about compatibility or downtime.
To combat this issue, organizations should implement a robust patch management system. Automation of updates, especially for critical systems, can significantly reduce risks. For complex environments, a phased approach (testing updates in a sandbox before full deployment) can mitigate potential issues. Clear update schedules, strictly adhered to, can prevent exposure to new threats.
Breaking Through Weak Access Controls
Weak passwords and poor access management continue to pose major security risks. The 2022 Verizon Data Breach Investigations Report found that 82% of breaches involved the human element, including weak or stolen credentials.
Organizations must implement multi-factor authentication (MFA) across all systems as a standard practice. The use of password managers encourages strong, unique passwords for each account. Regular audits of user access rights, with prompt removal of unnecessary privileges when employees change roles or leave the organization, further strengthen security.
The Firewall Fallacy
Misconfigured firewalls and security settings often create vulnerabilities. Many organizations set up firewalls but fail to maintain them properly. A study by FireMon showed that 30 percent of respondents reported that they manage firewalls.

Regular firewall rule reviews help remove outdated or conflicting rules. Automated tools can check for misconfigurations and policy violations. Next-generation firewalls offer deeper packet inspection and application-level controls, providing enhanced protection.
The Enemy Within
Insider threats, both malicious and accidental, pose significant risks. The 2022 Cost of Insider Threats Global Report by Ponemon Institute found that the average cost of insider threats rose to $15.4 million per incident.
To mitigate these risks, organizations should implement robust employee training programs that focus on security awareness and social engineering tactics. Data loss prevention (DLP) tools can monitor and control sensitive data movement. The principle of least privilege ensures employees only have access to necessary resources for their roles.
Continuous Monitoring and Adaptation
Network security requires ongoing vigilance and adaptation. Regular audits (at least annually, more frequently for high-risk industries) help identify new vulnerabilities. Continuous monitoring tools can detect anomalies in real-time, allowing for swift responses to potential threats.
Organizations should also stay informed about emerging threats and evolving best practices. Industry forums, security conferences, and partnerships with cybersecurity firms (such as Clouddle) can provide valuable insights and support in maintaining a robust security posture. Understanding network protocols is crucial for enhancing overall network security and identifying potential vulnerabilities.
Final Thoughts
Network security audits form the foundation of a robust cybersecurity strategy. These audits provide organizations with a clear picture of their vulnerabilities, enabling proactive measures against evolving threats. Regular audits are not just a best practice; they are a necessity in today’s digital landscape where cyber attacks grow increasingly sophisticated and frequent.
Effective implementation of network security audits requires a structured approach. Organizations must define clear objectives, assemble skilled teams, and create detailed timelines. During the audit, a combination of automated tools and manual testing uncovers vulnerabilities (both known and unknown).
At Clouddle, we understand the importance of network security in today’s interconnected world. Our Network as a Service (NaaS) solution combines networking, entertainment, and security, providing businesses with a comprehensive approach to network management. We invite you to explore how Clouddle can enhance your network security strategy.


