In today’s hyper-connected business landscape, operational downtime is no longer a minor inconvenience; it’s a critical threat to revenue, reputation, and customer trust. The question isn’t if a disruption will occur, but when and how prepared you are. A vague plan stored on a dusty server is insufficient. You need a dynamic, actionable, and rigorously tested strategy to ensure business continuity.
This comprehensive disaster recovery checklist moves beyond generic advice, providing eight essential steps tailored for modern IT environments. From conducting a thorough Business Impact Analysis to establishing effective communication protocols and implementing robust backup systems, we will guide you through creating a resilient framework. Each step is designed to be clear, practical, and immediately applicable. We’ll explore how to protect your critical assets and maintain operational stability, especially when leveraging managed services to streamline implementation and management. Let’s build a plan that works when you need it most.
1. Conduct a Comprehensive Business Impact Analysis (BIA)
Before you can build a house, you need a blueprint. A Business Impact Analysis (BIA) is the foundational blueprint for your entire disaster recovery plan. It’s a systematic process that identifies your most critical business functions and quantifies the potential effects of a disruption to them. This analysis is the cornerstone of any effective disaster recovery checklist, as it provides the essential data needed to make informed decisions about resource allocation and recovery priorities.

The primary goal of a BIA is to determine the operational and financial impacts of a disaster over time. This helps establish two critical metrics: the Recovery Time Objective (RTO), which defines the maximum tolerable downtime for a system, and the Recovery Point Objective (RPO), which dictates the maximum acceptable amount of data loss. For example, a senior living facility might determine its electronic health record (EHR) system has an RTO of less than one hour and an RPO of 15 minutes to ensure patient safety and continuity of care.
How to Implement a BIA
- Interview Stakeholders: Engage leaders from every department, from front-desk operations in a hotel to maintenance in a multi-family residence. Ask them to identify their most critical daily, weekly, and monthly tasks.
- Map Dependencies: Document how different systems and processes rely on each other. For instance, your property management system (PMS) might depend on your network infrastructure, which in turn relies on a specific server.
- Quantify Impacts: Go beyond “this would be bad.” Calculate the potential financial losses per hour of downtime for each function. Consider non-financial impacts as well, such as reputational damage or regulatory fines.
- Validate Findings: Once you’ve gathered your data, present it back to the business unit leaders. This ensures your technical recovery priorities align perfectly with real-world operational needs, forming a solid first step in your disaster recovery checklist.
2. Develop and Document the Disaster Recovery Plan
With your Business Impact Analysis complete, the next critical step is to translate those findings into a formal, actionable document. The Disaster Recovery (DR) Plan is the master playbook your team will follow during a crisis. It’s a comprehensive, step-by-step guide detailing the procedures to respond to and recover from various disaster scenarios, ensuring a coordinated and efficient response even under extreme stress. This document transforms your BIA from a strategic assessment into a tactical roadmap, making it an indispensable part of any disaster recovery checklist.
A well-documented DR plan provides clarity when chaos strikes. It outlines specific roles, responsibilities, recovery procedures, and communication protocols. For instance, a retail business that suffers a server failure should have a plan that immediately triggers notifications to their managed services provider, outlines the steps for failing over to a backup system, and provides communication templates to inform store managers. As evidenced by Amazon’s rapid recovery from AWS outages, having detailed and rehearsed plans is what separates a minor hiccup from a catastrophic failure.
How to Create the DR Plan
- Use Standardized Templates: Leverage established frameworks like those from NIST or ISO 22301 to ensure you cover all essential components. This creates a consistent, easy-to-follow structure.
- Include Visual Aids: Incorporate flowcharts and network diagrams to illustrate complex recovery processes. Visuals are often easier to interpret than dense text during a high-pressure incident.
- Define Clear Roles and Responsibilities: Assign specific tasks to individuals or teams. Who is authorized to declare a disaster? Who is responsible for restoring the primary database? Clarity prevents confusion and delay.
- Maintain Version Control and Accessibility: Store both digital and physical copies of the plan in multiple, secure locations. Implement a version control system to ensure everyone is working from the most current document. Providing leadership with a concise executive summary ensures they can make informed decisions quickly.
3. Establish Backup and Data Protection Systems
If a Business Impact Analysis is the blueprint, then your data backup system is the fireproof safe where you keep your most valuable assets. Establishing robust backup and data protection is a non-negotiable part of any modern disaster recovery checklist. This process involves creating multiple, secure copies of your critical data to ensure you can restore operations quickly and with minimal loss after an incident, whether it’s a server failure, a natural disaster, or a ransomware attack.
The core principle behind effective data protection is the 3-2-1 rule, popularized by experts like Peter Krogh and companies like Veeam. This rule dictates that you should have at least three copies of your data, stored on two different types of media, with at least one copy located offsite. For instance, a hotel might have its primary data on a local server, a second copy on a network-attached storage (NAS) device, and a third, air-gapped copy in a secure cloud environment like AWS S3. This layered approach is your best defense against data loss.
How to Implement Backup and Data Protection
- Automate and Replicate: Manual backups are prone to human error. Implement automated systems that create backups on a set schedule determined by your RPO. For critical systems, use real-time data replication to a secondary site or cloud service to minimize data loss.
- Embrace Modern Defenses: Protect against sophisticated threats by using immutable backups, which cannot be altered or deleted, and air-gapped systems that are physically isolated from your main network. This is a crucial defense against ransomware.
- Verify and Document: A backup is useless if it can’t be restored. Regularly test your restore procedures to confirm data integrity and that you can meet your RTO. Clearly document your backup schedules, retention policies, and key management protocols for encrypted data. For businesses considering a move to the cloud for enhanced data protection, our cloud migration checklist offers a detailed guide.
- Monitor System Health: Actively monitor your backup success rates, job completion times, and storage capacity. Set up alerts for failed jobs or low storage to address issues proactively before they become a problem during a real disaster.
4. Create and Test Communication Plans
When a disaster strikes, technology isn’t the only thing that fails; communication often breaks down first. A robust communication plan is the vital link that holds your disaster response together, ensuring that everyone from internal staff and management to customers, vendors, and the public receives clear, timely, and accurate information. This plan acts as the central nervous system for your recovery efforts, preventing panic, managing expectations, and enabling coordinated action when it matters most.

The core purpose of a communication plan is to pre-define who says what, to whom, and through which channels. It eliminates the guesswork and chaos that can cripple a response. For instance, in a senior living facility experiencing a power outage, the plan would dictate how staff are alerted, how residents’ families are informed of the situation and safety measures, and what information is provided to emergency services. Without this, confusion reigns, trust erodes, and risks escalate, making it a critical component of any disaster recovery checklist.
How to Implement a Communication Plan
- Establish a Communication Tree: Map out a clear hierarchy for disseminating information. This includes primary and secondary contacts for every team and department, ensuring a message can flow reliably even if key individuals are unavailable.
- Utilize Multiple Channels: Don’t rely on a single method. Incorporate a mass notification system that can send alerts via SMS, email, and voice calls. Also, consider low-tech options like a physical call-in hotline or a designated out-of-state number for check-ins.
- Prepare Pre-Scripted Templates: Draft messages in advance for various potential scenarios like system outages, building evacuations, or data breaches. This saves critical time and ensures your messaging is consistent, empathetic, and professional under pressure.
- Test and Drill Regularly: A plan is useless if it’s not tested. Conduct regular communication drills, simulating different disaster scenarios to identify weak points in your protocols. Validate that contact information is up-to-date and that designated spokespeople are prepared to handle inquiries effectively.
5. Implement Recovery Site and Infrastructure Setup
With your BIA complete and critical systems identified, the next step is to establish a physical or virtual location where you can recover operations. Implementing a recovery site and its supporting infrastructure is where your disaster recovery plan moves from theory to tangible reality. This site is your lifeline, ensuring that when your primary location is unavailable, your business isn’t forced into a complete shutdown. It’s a critical component of any disaster recovery checklist.
The choice of recovery site directly impacts your recovery speed and costs, aligning with the RTOs and RPOs defined in your BIA. Options range from fully operational hot sites to cloud-based Disaster Recovery as a Service (DRaaS) solutions. For instance, a large hotel chain might use a hot site to failover its central reservation system instantly, while a smaller residential property could leverage a cost-effective DRaaS provider like Zerto to replicate its property management system to the cloud.
This process flow visualizes the high-level stages of establishing a functional recovery site, from initial selection to final testing.
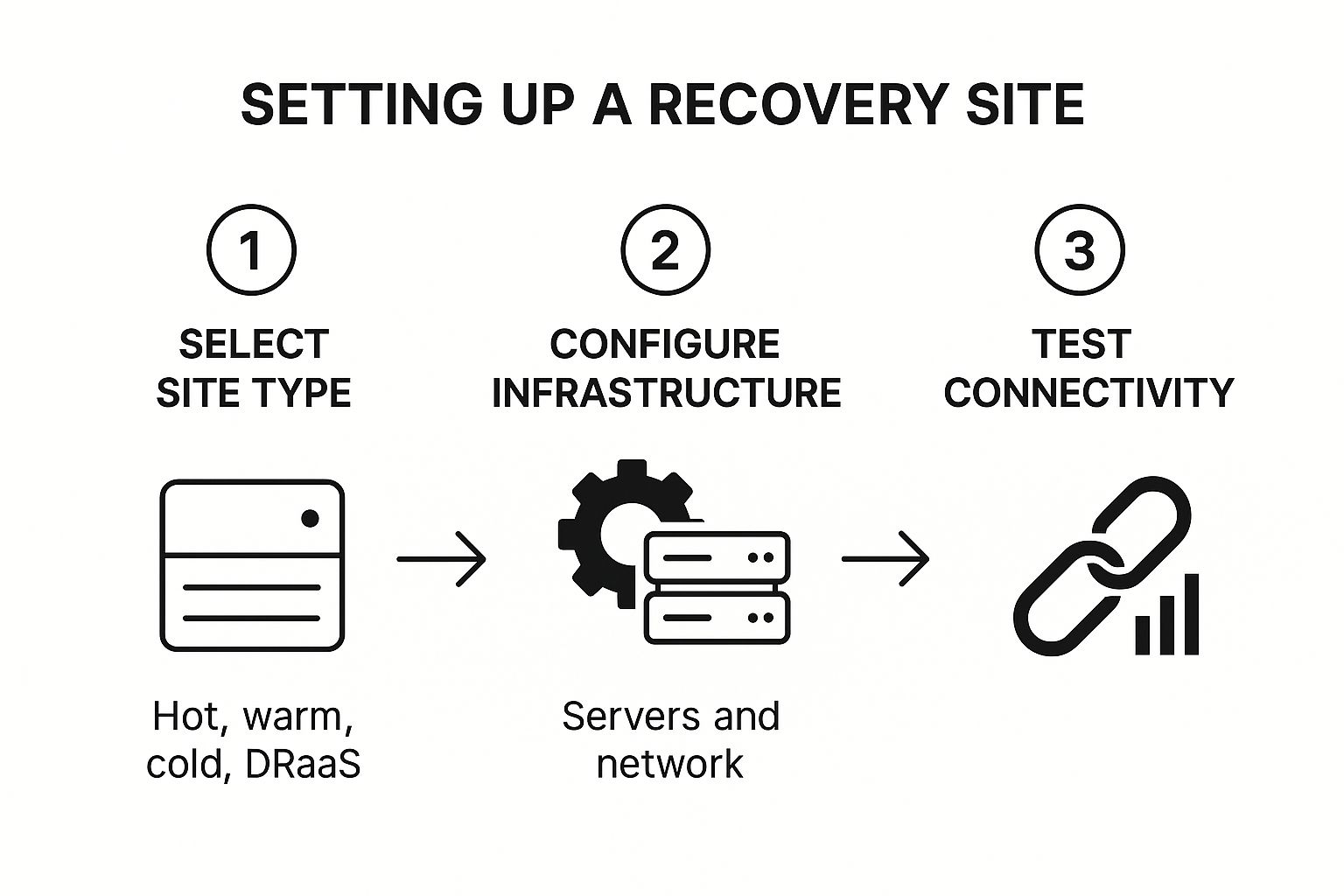
Following this sequence ensures that decisions about site type inform the necessary infrastructure, which is then validated through rigorous connectivity and performance testing.
How to Implement a Recovery Site
- Select the Right Site Type: Choose a model based on your RTO/RPO needs. Hot sites are fully equipped and ready for immediate failover. Warm sites have infrastructure but require software and data restoration. Cold sites offer only basic space and utilities, while DRaaS provides a flexible, cloud-based alternative.
- Configure and Document: Set up all necessary hardware, software, and networking to mirror your critical production environment. Meticulously document every configuration detail, IP address, and setup procedure to ensure a smooth and predictable failover process.
- Test Connectivity and Bandwidth: Regularly test the network connection between your primary and recovery sites. Verify that you have sufficient bandwidth to handle data replication and support user access during a disaster without creating crippling bottlenecks.
- Plan for People and Processes: A recovery site isn’t just about technology. Ensure you have a plan for how your staff will access the systems and where they will work if your main office is inaccessible. This includes planning for workspace recovery if necessary.
6. Conduct Regular Testing and Exercises
A disaster recovery plan that sits on a shelf is nothing more than a document. To transform it into a living, effective defense, you must rigorously and regularly test it. Conducting frequent tests and exercises is the only way to validate your plan’s effectiveness, uncover hidden flaws, and ensure your team can execute it under pressure. This process moves your plan from a theoretical concept to a practiced, reliable procedure, making it an indispensable part of any disaster recovery checklist.
The purpose of testing is to measure your actual recovery capabilities against your established RTO and RPO metrics. It reveals whether the steps outlined in your plan are practical and if your technology functions as expected during a failover. For instance, a retail business might simulate a point-of-sale (POS) system failure to confirm that its backup processing system can be activated within its 30-minute RTO, preventing significant revenue loss. Major organizations like Amazon institutionalize this with “GameDay” exercises, intentionally creating failures to test system and team resilience.
How to Implement Regular Testing
- Start with Tabletop Exercises: Begin with discussion-based sessions where your team walks through a specific disaster scenario, like a ransomware attack on a senior living facility’s records. This low-stress method helps identify initial gaps in communication and procedure without touching live systems.
- Progress to Simulations: Graduate to technical simulations or failover tests. This could involve switching your property management system (PMS) to its secondary data center during off-peak hours to measure the actual time and data loss involved in the switch.
- Conduct Full-Scale Tests: At least annually, perform a comprehensive test that mimics a real disaster. This involves all relevant personnel, including third-party vendors, and tests the end-to-end recovery process, from initial alert to full operational restoration.
- Document and Iterate: Meticulously document the results of every test, noting what worked, what failed, and the actual recovery times achieved. Use these lessons learned to update and strengthen your disaster recovery checklist and plan, creating a cycle of continuous improvement.
7. Train Staff and Assign Recovery Roles
A disaster recovery plan is only as effective as the people who execute it. Simply creating documentation isn’t enough; your team must understand their specific roles and responsibilities when a crisis occurs. Comprehensive staff training transforms your plan from a static document into a dynamic, living protocol, ensuring a coordinated and efficient response. This is a critical step in any disaster recovery checklist because it empowers your personnel to act decisively and correctly under pressure.
The goal is to eliminate confusion and hesitation during an actual disaster. Well-defined roles, backed by regular training, ensure that everyone from IT technicians restoring servers to front-desk staff at a hotel managing guest communications knows exactly what to do. For example, Kaiser Permanente implements role-based emergency response training for both clinical and administrative staff, ensuring patient care and operations continue seamlessly. Similarly, Southwest Airlines famously cross-trains employees, creating operational resilience and flexibility during disruptions.
How to Implement Staff Training and Role Assignment
- Develop Role-Specific Playbooks: Don’t give everyone the entire disaster recovery plan. Create condensed, role-specific guides or “playbooks” that outline the exact steps an individual needs to take. An IT manager’s playbook will differ vastly from that of a senior living facility’s care coordinator.
- Conduct Realistic Simulations: Move beyond simple tabletop exercises. Use simulation software or conduct live drills that mimic real-world scenarios, like a network outage or a physical security breach. This tests your plan and builds muscle memory.
- Implement a Training Cadence: Training is not a one-time event. Schedule mandatory annual or semi-annual training sessions and drills. For smaller teams, integrating this with a co-managed IT support partner can provide specialized expertise and resources for technical training.
- Document Everything: Keep meticulous records of who was trained, when they were trained, and on which procedures. This is vital for compliance, accountability, and identifying any gaps in your readiness. Create wallet cards with key contacts and initial steps for easy access.
8. Monitor, Review, and Update Recovery Plans
A disaster recovery plan is not a “set it and forget it” document; it’s a living guide that must evolve with your business. Establishing a formal process to monitor, review, and update your plans is the final, crucial step in any disaster recovery checklist. This ongoing cycle ensures your strategies remain relevant and effective against a backdrop of changing technologies, business priorities, and emerging threats. Without continuous improvement, even the most meticulously crafted plan will quickly become obsolete.
The primary goal of this stage is to embed disaster recovery into your organization’s operational rhythm. It transforms the plan from a static file into a dynamic tool that reflects your current reality. Think of it like regular maintenance for a critical piece of machinery. Federal agencies, for example, are often required to conduct annual continuity plan assessments, while tech giants like Salesforce perform quarterly reviews to stay aligned with rapid innovation. This commitment to upkeep is what separates a theoretical plan from a truly resilient operation.
How to Implement Ongoing Plan Reviews
- Establish a Formal Schedule: Don’t leave reviews to chance. Schedule them at regular intervals, such as quarterly or annually, and tie them to key business events like budget cycles or technology upgrades. This ensures the review process is consistent and predictable.
- Implement Version Control: Use a version control system to manage your DR plan documents. This prevents confusion by ensuring everyone is working from the most current version and provides a clear history of all changes, updates, and approvals.
- Incorporate Lessons Learned: After every test, drill, or actual incident, conduct a post-mortem analysis. Document what went well, what failed, and why. Integrate these findings directly into the plan to strengthen it for the future.
- Align with Business and Technology Changes: Your business is not static, and neither is your technology. Regularly re-evaluate your plan to ensure it aligns with new business processes, updated software like your property management system, and changes in your IT infrastructure. A key part of this is continuous network monitoring to detect changes or vulnerabilities that could impact your recovery capabilities.
Disaster Recovery Checklist: 8 Key Components Comparison
| Item | Implementation Complexity 🔄 | Resource Requirements ⚡ | Expected Outcomes 📊 | Ideal Use Cases 💡 | Key Advantages ⭐ |
|---|---|---|---|---|---|
| Conduct a Comprehensive Business Impact Analysis (BIA) | High: Involves extensive stakeholder engagement and data gathering | Significant time and cross-department input | Clear recovery priorities, RTO and RPO established | Organizations seeking data-driven recovery planning | Foundation for DR plans, prioritizes recovery efforts |
| Develop and Document the Disaster Recovery Plan | Medium-High: Detailed documentation and scenario planning required | Time-intensive writing and periodic updates | Consistent crisis response and reduced recovery time | Organizations needing structured DR procedures | Provides clear guidance during emergencies |
| Establish Backup and Data Protection Systems | Medium: Setup automated backups; encryption and verification | Ongoing storage, monitoring, and bandwidth costs | Rapid data recovery; data integrity maintained | Businesses prioritizing data security and recovery | Protects against data loss, ransomware, and failures |
| Create and Test Communication Plans | Medium: Establish multi-channel systems and contact trees | Regular updates and drills; communication tools | Clear, coordinated communication during disasters | Entities requiring strong stakeholder communication | Reduces confusion, maintains public and internal trust |
| Implement Recovery Site and Infrastructure Setup | High: Involves physical or cloud infrastructure setup | High upfront and ongoing maintenance costs | Rapid operational resumption with minimal downtime | Organizations needing alternate operational sites | Enables fast recovery; flexible recovery options |
| Conduct Regular Testing and Exercises | Medium-High: Planning and executing varied test types | Time, personnel, and resource allocation | Validated plans and identification of gaps | Organizations focused on DR plan validation | Builds confidence, ensures compliance, and uncovers gaps |
| Train Staff and Assign Recovery Roles | Medium: Develop role-based programs and conduct trainings | Continuous training investment and assessment | Skilled staff able to perform recovery roles effectively | Companies emphasizing operational resilience | Reduces human errors, creates redundancy |
| Monitor, Review, and Update Recovery Plans | Medium: Ongoing review and integration of lessons learned | Dedicated resources for regular maintenance | Up-to-date, effective, and compliant recovery plans | All organizations with evolving technology/business | Ensures continuous improvement and relevance |
From Checklist to Confidence: Your Next Steps in Resilience
Completing a detailed disaster recovery checklist is more than an administrative task; it’s a foundational step toward building an organization that can withstand unforeseen challenges. We have journeyed through the critical components of a robust strategy, from conducting a meticulous Business Impact Analysis (BIA) and establishing resilient data backup systems to assigning clear roles and running regular, realistic drills. This isn’t just about creating a document that sits on a shelf. It’s about cultivating a culture of preparedness where response is practiced, reliable, and deeply ingrained in your operational DNA.
The true value of this process lies in transforming abstract plans into tangible confidence. For a hospitality manager, it means knowing guest data and reservation systems are secure even if a local server fails. For a multi-family property operator, it’s the assurance that resident communication channels and access control systems can be restored quickly after a power grid failure. Each step you’ve reviewed contributes to a larger system of resilience, ensuring business continuity and protecting your reputation.
Key Takeaways for Lasting Resilience
Your journey doesn’t end once the checklist is complete. The most successful disaster recovery strategies are living, breathing frameworks. To ensure your plan remains effective, focus on these core principles:
- Integration is Essential: Your disaster recovery plan cannot exist in a vacuum. It must be woven into your daily operations, from staff training and onboarding to technology procurement and change management protocols.
- Testing is Non-Negotiable: A plan that has never been tested is not a plan; it’s a theory. Regular, rigorous testing is the only way to uncover hidden flaws, validate your recovery time objectives (RTOs), and build muscle memory within your response teams.
- Proactive Adaptation: Threats evolve, technology changes, and your business grows. Your disaster recovery plan must adapt in tandem. A commitment to continuous monitoring, reviewing, and updating is what separates a vulnerable organization from a resilient one.
Your Actionable Path Forward
The path from checklist to confidence is paved with deliberate action. Begin by scheduling a dedicated review session with your key stakeholders to assess your current state against the items discussed. Identify the most significant gaps, whether it’s an outdated communication plan or an untested backup system. Prioritize these vulnerabilities and create a clear, time-bound roadmap for addressing them.
Ultimately, mastering this disaster recovery checklist shifts your organization’s posture from reactive to proactive. You move from fearing disruptions to being methodically prepared for them. This preparedness is no longer a luxury; it’s a competitive advantage that builds trust with clients, residents, and partners, proving that your business is built to last.
Ready to transform your disaster recovery checklist from a document into a powerful, managed reality? The experts at Clouddle Inc specialize in implementing and managing the very security, network, and cloud solutions that form the backbone of a resilient business. Let us help you build a comprehensive and automated disaster recovery strategy, so you can focus on what you do best.


