In today’s digital landscape, protecting your data is more critical than ever. At Clouddle, we understand the importance of robust network security measures to safeguard your valuable information.
Our comprehensive checklist for network security covers essential steps to fortify your defenses against cyber threats. From basic practices to advanced strategies, we’ll guide you through the key elements of a strong security posture.
Understanding Network Security: The Foundation of Data Protection
Defining Network Security
Network security forms the bedrock of protecting digital assets. It encompasses a set of measures designed to defend network infrastructure from unauthorized access, misuse, modification, or destruction. The primary goal of network security is to maintain the confidentiality, integrity, and availability of data.
The High Stakes of Data Protection
Protecting data isn’t just a good practice-it’s a necessity for survival in today’s digital landscape. The IBM Cost of a Data Breach Report revealed that in 2024, the global average cost of a data breach reached $4.45 million, a 10% increase over the previous year and the highest total ever. This staggering figure underscores the non-negotiable nature of robust network security.
For businesses, a security breach can result in financial losses, reputational damage, and legal consequences. Individuals face risks of identity theft, financial fraud, and personal information exposure. The consequences of inadequate security extend far and wide, with long-lasting effects.
Common Network Security Threats
To mount an effective defense, understanding the threats is paramount. Here are some of the most prevalent network security threats:
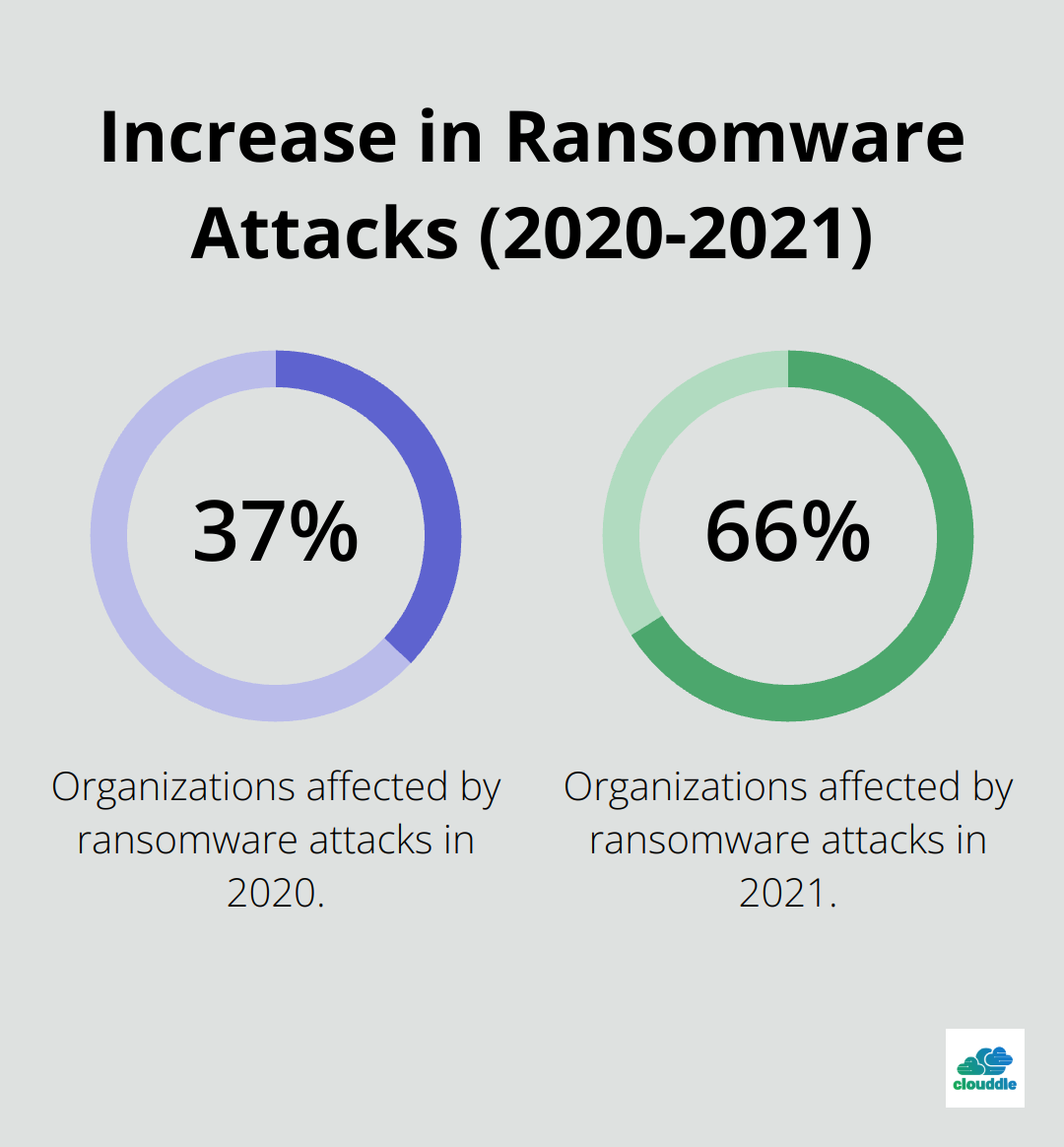
- Malware: This category includes viruses, worms, trojans, and ransomware. Sophos reported that in 2021, ransomware attacks affected 66% of organizations surveyed, up from 37% in 2020.
- Phishing: These deceptive attacks trick users into revealing sensitive information. The Anti-Phishing Working Group (APWG) observed over 1 million phishing attacks in the first quarter of 2022 alone.
- Distributed Denial of Service (DDoS): These attacks overwhelm networks or servers, causing service disruptions. Cloudflare noted a 67% increase in DDoS attacks in Q4 2022 compared to the previous year.
- Man-in-the-Middle (MitM) Attacks: Attackers intercept communication between two parties to steal data. While less frequent, these attacks can be devastating when successful.
- Zero-Day Exploits: These attacks target newly discovered vulnerabilities before patches become available. Google’s Project Zero team reported 18 zero-day vulnerabilities (actively exploited) in 2022.
The Power of Proactive Security Measures
Effective network security doesn’t react to threats-it prevents them proactively. This approach involves implementing robust firewalls, updating software regularly, using strong encryption, and educating users about security best practices.
For businesses seeking comprehensive protection, managed security services can provide round-the-clock monitoring, threat detection, and rapid response capabilities. This approach ensures that experts (who stay ahead of evolving threats) protect your network.
As we move forward, we’ll explore the essential network security measures that form the backbone of a robust defense strategy. These measures will help you build a strong foundation to protect your valuable data from the ever-evolving landscape of cyber threats.
How to Implement Essential Network Security Measures
Fortify Your Network’s First Line of Defense
Start with a next-generation firewall (NGFW). Unlike traditional firewalls, NGFWs provide deep packet inspection, intrusion prevention, and application-level filtering. Pair your NGFW with an intrusion detection system (IDS) to monitor network traffic for suspicious activities.
Small to medium-sized businesses should consider open-source solutions like pfSense for firewalls and Snort for intrusion detection. These tools offer enterprise-level security without the hefty price tag.
Strengthen Access Controls
Implement a strong password policy. The National Institute of Standards and Technology (NIST) recommends using passphrases of at least 15 characters. Enforce this policy across your organization.
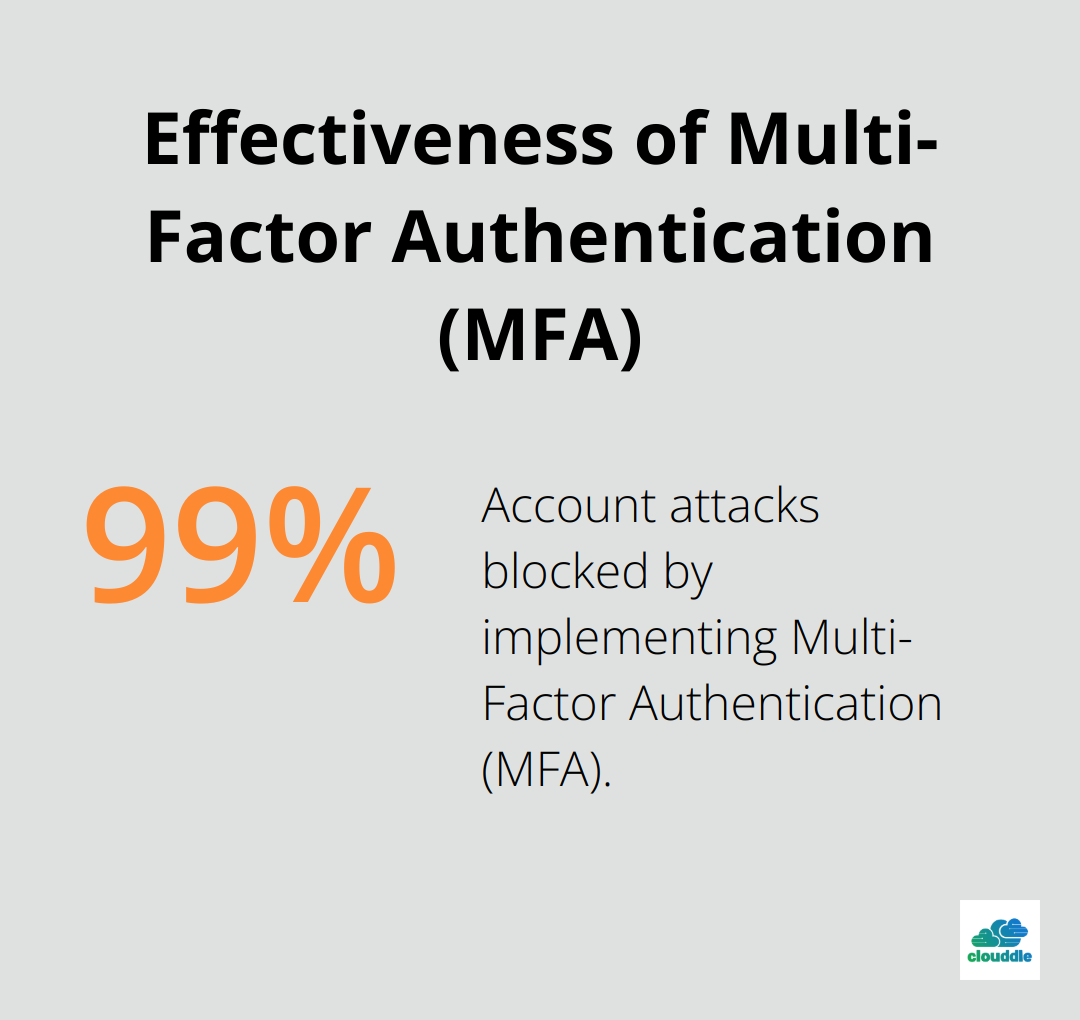
Multi-factor authentication (MFA) is essential. MFA can block over 99.9% of account attacks. Enable MFA on all accounts, especially for administrative access.
Keep Your Systems Up-to-Date
Unpatched vulnerabilities create a playground for hackers. Set up automatic updates for all systems and applications where possible.
For critical systems, establish a patch management process. Test patches in a controlled environment before deploying them network-wide. This approach balances security with operational stability.
Encrypt Everything
Data encryption serves as your last line of defense. Use HTTPS for all web traffic. For data at rest, implement full-disk encryption on all devices.
Businesses handling sensitive data should consider implementing a data loss prevention (DLP) solution. DLP tools can automatically encrypt or block the transmission of sensitive information.
Empower Your Employees
Your staff can be your strongest asset or your weakest link. Regular security awareness training is vital.
Conduct phishing simulations to test and improve your employees’ ability to spot malicious emails. Tools like Gophish allow you to run these tests in-house at no cost.
Network security requires constant vigilance and adaptation. The next section will explore advanced strategies to further enhance your network‘s resilience against evolving cyber threats.
Elevating Your Network Defense: Advanced Strategies for Comprehensive Protection
Network Segmentation: A Divide and Conquer Approach
Network segmentation limits the potential damage of a breach. This strategy divides your network into smaller, isolated segments to contain threats and prevent lateral movement. A study by Ponemon Institute based on a representative sample of 237 organizations in six countries provides insights into the annual cost of cybercrime.
We recommend the implementation of Virtual Local Area Networks (VLANs) to separate different departments or types of data. For example, keep your finance department on a separate VLAN from marketing. This approach enhances security and improves network performance by reducing unnecessary traffic.
Continuous Monitoring: Your Digital Watchdog
Continuous monitoring alerts you to potential threats before they escalate. A Security Information and Event Management (SIEM) system aggregates and analyzes log data from across your network. SIEM tools detect anomalies that might indicate a breach in progress.
Securonix provides precise, fast, and efficient threat detection, investigation, and response capabilities. It leverages an AI-reinforced cloud-native platform for enhanced security monitoring.
Incident Response Planning: Preparation is Key
No security measure is foolproof, so a solid incident response plan is essential. IBM reports that companies with incident response teams and extensive testing of their IR plans experienced $1.23 million less in data breach costs compared to those without.
We advise the creation of a detailed incident response plan that outlines roles, responsibilities, and steps to take during a security event. Regular tabletop exercises test and refine your plan. These simulations help identify gaps in your response strategy before a real incident occurs.
Penetration Testing: Find Vulnerabilities Before Attackers Do
Penetration testing simulates real-world attacks to identify weaknesses in your network defenses. A survey by Ponemon Institute found that 53% of IT security professionals believe penetration testing is essential for a strong security posture.
We suggest conducting both internal and external penetration tests at least annually (or more frequently if your industry regulations require it). Use the results to prioritize security improvements and allocate resources effectively.
Cloud Security: Protecting Beyond Traditional Boundaries
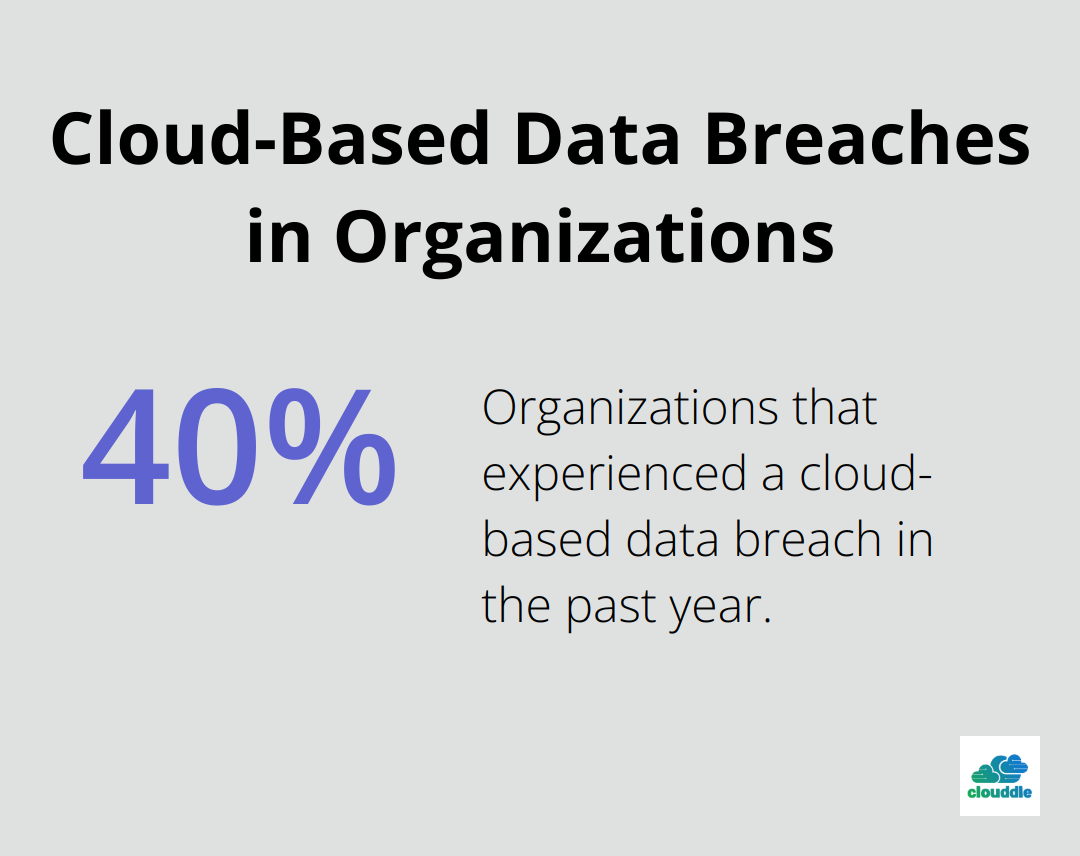
As businesses increasingly rely on cloud services, securing these environments becomes paramount. The 2021 Thales Cloud Security Study revealed that 40% of organizations experienced a cloud-based data breach in the past year.
Cloud Access Security Brokers (CASBs) extend your security policies to cloud services. CASBs provide visibility into cloud usage, data protection, and threat prevention across multiple cloud platforms.
We recommend the use of cloud-native security tools provided by your cloud service provider. These tools (designed specifically for cloud environments) can offer more effective protection than traditional security measures.
Final Thoughts
This checklist for network security outlines a multi-faceted approach to protect your data. Each layer adds protection against evolving cyber threats, from foundational measures to advanced strategies. The cybersecurity landscape demands ongoing vigilance and adaptation to maintain a robust defense.
Start by assessing your current vulnerabilities to implement a comprehensive network security strategy. Prioritize critical areas for improvement and create a roadmap for implementing the discussed measures. Security is an ongoing process that requires constant attention and updates.
Businesses seeking to enhance their network security without in-house management can benefit from managed security services. These services provide expert protection and peace of mind (especially for organizations with limited IT resources). At Clouddle, we offer cutting-edge technology solutions to help businesses stay secure in an increasingly connected world.


