Network security is a critical aspect of modern business operations, protecting valuable data and systems from ever-evolving threats. At Clouddle, we understand the importance of robust security measures in safeguarding digital assets.
This comprehensive guide explores various network security methodologies, from fundamental concepts to advanced strategies. We’ll examine essential techniques and cutting-edge approaches that organizations can implement to fortify their networks against potential breaches and attacks.
What Makes Network Security Essential?
The Foundation of Digital Infrastructure
Network security forms the backbone of modern digital infrastructure. It protects organizations from numerous threats that could compromise sensitive data, disrupt operations, and damage reputations. Network security involves the implementation of measures to prevent unauthorized access, misuse, modification, or denial of computer networks and network-accessible resources.
Key Components of Secure Networks
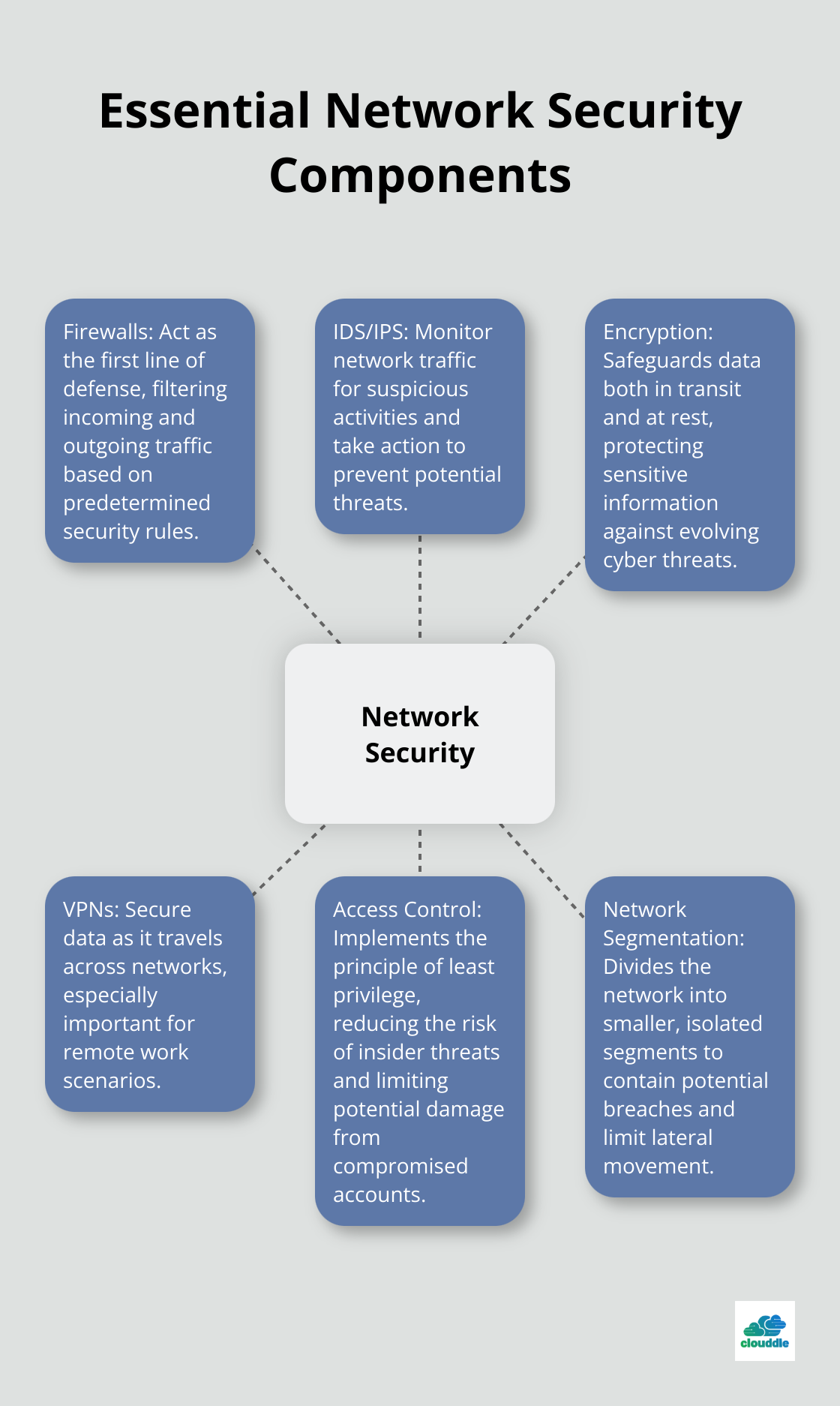
A robust network security framework consists of several essential components:
- Firewalls: These act as the first line of defense, filtering incoming and outgoing traffic based on predetermined security rules.
- Intrusion Detection and Prevention Systems (IDS/IPS): These systems monitor network traffic for suspicious activities and take action to prevent potential threats.
- Encryption: This plays a vital role in safeguarding data both in transit and at rest. It’s essential in 2025 for protecting sensitive information against evolving cyber threats.
The Ever-Evolving Threat Landscape
The network security landscape constantly changes, with new threats emerging regularly:
- Malware: This includes viruses, trojans, and ransomware.
- Phishing Attacks: These continue to be prevalent.
- Distributed Denial of Service (DDoS) Attacks: These pose another significant threat. Cloudflare reported mitigating a DDoS attack that peaked at 26 million requests per second in 2024.

Proactive Measures for Enhanced Security
Organizations must adopt a proactive approach to network security to combat these threats effectively:
- Regular Vulnerability Assessments: These help identify potential weaknesses before malicious actors can exploit them.
- Employee Training: This is critical, as human error remains a significant factor in security breaches.
- Comprehensive Patch Management: This strategy addresses known vulnerabilities.
As we move forward, we’ll explore essential network security methodologies that organizations can implement to fortify their defenses against these evolving threats.
How to Implement Essential Network Security Methodologies
Network security requires complex strategies, but implementing essential methodologies can significantly enhance your organization’s defense against cyber threats. These strategies protect businesses across various industries.
Firewalls and Intrusion Detection Systems: Your First Line of Defense
Firewalls and Intrusion Detection Systems (IDS) form the cornerstone of network security. Modern Next-Generation Firewalls (NGFWs) offer advanced features like packet filtering, network address translation (NAT), URL filtering, deep packet inspection (DPI), and intrusion detection and prevention. These systems not only filter traffic but also inspect packet contents, providing deeper security insights.
When you configure your firewall, adopt a default-deny stance. This approach blocks all traffic except what’s explicitly allowed, significantly reducing your attack surface. Additionally, update your firewall rules regularly to align with your current network needs and emerging threats.
For IDS, consider both network-based and host-based systems. Network-based IDS monitor traffic on entire network segments, while host-based IDS focus on individual devices. Combining both provides comprehensive coverage. The key is to fine-tune these systems to minimize false positives while catching genuine threats.
VPNs and Encryption: Securing Data in Transit
Virtual Private Networks (VPNs) and encryption protect data as it travels across networks. With remote work becoming the norm, VPNs have seen a surge in adoption.
When you implement a VPN solution, opt for protocols like OpenVPN or WireGuard, known for their strong security and performance. Ensure your VPN uses robust encryption standards (such as AES-256) for data protection.
For data at rest, implement full-disk encryption on all devices. This protects sensitive information even if a device is lost or stolen. Many operating systems now offer built-in encryption tools, making implementation straightforward.
Access Control: The Power of Least Privilege
Effective access control grants users only the permissions they need to perform their jobs. This principle of least privilege significantly reduces the risk of insider threats and limits the potential damage from compromised accounts.
Implement Role-Based Access Control (RBAC) to streamline permission management. RBAC authorizes and restricts system access to users based on their role(s) within an organization, making it easier to maintain consistent security policies as your organization grows or changes.
Multi-Factor Authentication (MFA) is another critical component of access control. Implement MFA across all your systems, especially for privileged accounts and remote access.
Network Segmentation: Containing Potential Breaches
Network segmentation divides your network into smaller, isolated segments. This approach contains potential breaches, limiting an attacker’s ability to move laterally through your network.
Start by identifying your most critical assets and isolating them in their own network segments. Use firewalls or virtual LANs (VLANs) to control traffic between segments. For even greater security, consider microsegmentation, which applies security policies at the individual workload level.
A well-segmented network not only improves security but can also enhance performance by reducing unnecessary traffic between segments.
Implementing these methodologies requires careful planning and ongoing management. Regular security audits and penetration testing can help identify weaknesses in your implementation. As we move forward, we’ll explore advanced network security strategies that build upon these essential methodologies to create a robust, multi-layered defense against evolving cyber threats.
How Advanced Network Security Strategies Protect Your Business
In today’s rapidly evolving threat landscape, basic security measures no longer suffice. Advanced network security strategies are essential for businesses to stay ahead of sophisticated cyber threats.
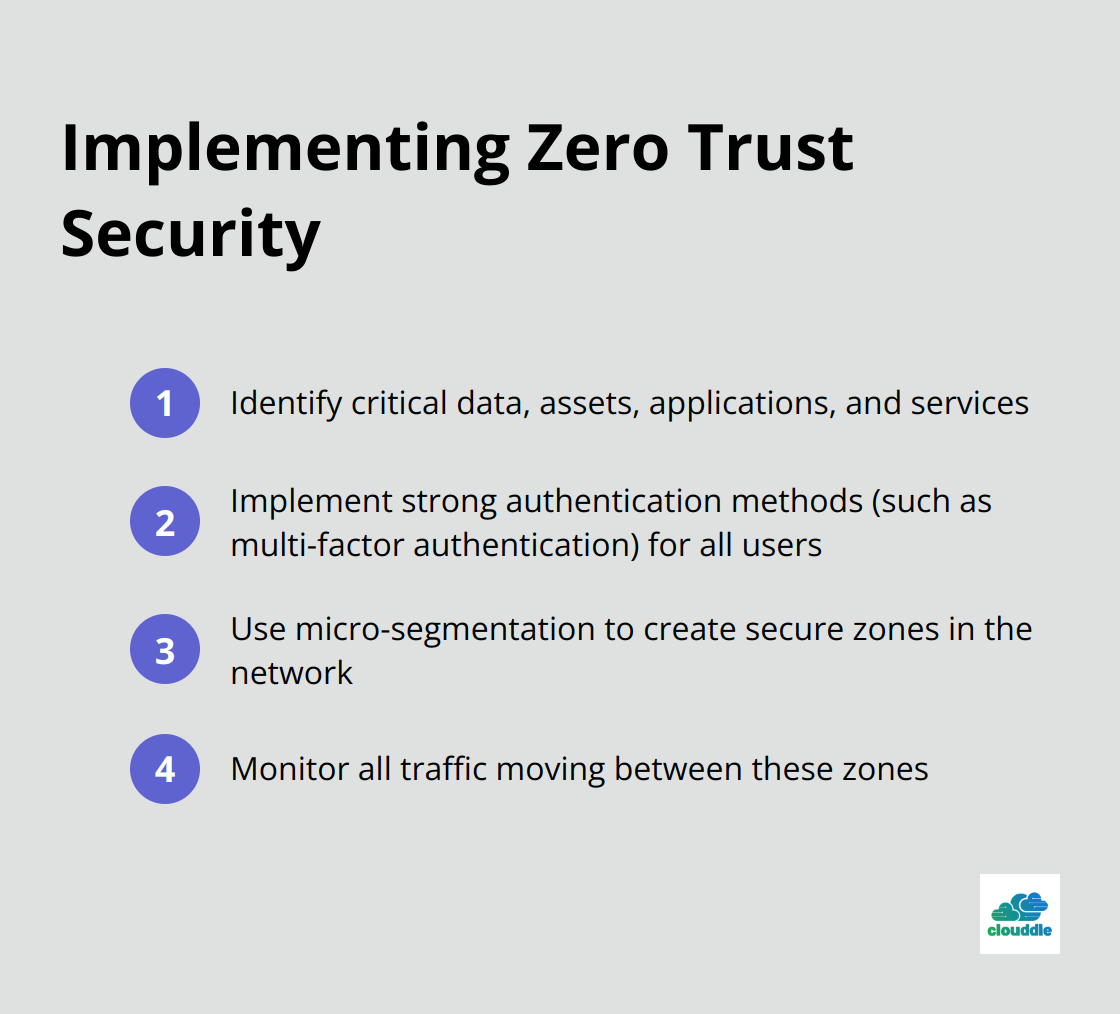
Zero Trust Model: A New Security Paradigm
The Zero Trust model has gained significant traction in recent years. This approach assumes that no user, device, or network should be trusted by default, even if they’re already inside the network perimeter. Instead, every access request must be verified before granting access.
Zero Trust security model strengthens an organization’s cyber resilience, ensuring critical protection against unauthorized access. Implementing Zero Trust involves:
SIEM: Enhanced Visibility for Better Security
Security Information and Event Management (SIEM) systems provide real-time analysis of security alerts generated by network hardware and applications. SIEM tools collect and aggregate log data from various sources across the network, allowing for comprehensive threat detection and incident response.
To maximize the effectiveness of a SIEM solution, organizations should:
- Integrate as many data sources as possible (firewalls, intrusion detection systems, antivirus software, and application logs)
- Regularly review and update correlation rules
- Train security personnel to interpret SIEM data effectively
AI and ML: The Future of Proactive Defense
AI and ML revolutionize network security. These technologies analyze vast amounts of data to identify patterns and anomalies that might indicate a threat, often before a human analyst could spot them.
Organizations can leverage AI and ML in network security by:
- Implementing AI-powered threat detection systems
- Using ML algorithms to improve the accuracy of anomaly detection
- Employing AI for automated incident response
Securing Cloud and Hybrid Environments
As businesses increasingly adopt cloud and hybrid infrastructures, securing these environments has become paramount. Cloud security requires a different approach than traditional on-premises security.
To enhance cloud and hybrid security, organizations should:
- Understand the shared responsibility model of their cloud provider
- Implement strong access controls
- Encrypt data both in transit and at rest
- Use cloud-native security tools provided by the cloud platform
- Maintain consistent security policies across on-premises and cloud infrastructure
These advanced network security strategies significantly enhance an organization’s defense against cyber threats. However, security is an ongoing process that requires regular review and updates to stay ahead of evolving threats.
Final Thoughts
Network security methodologies form the backbone of robust defense against cyber threats. Organizations must employ a multi-faceted approach to protect their digital assets, from fundamental practices to advanced strategies. The landscape of network security evolves constantly, with new threats emerging alongside technological advancements.
A layered security strategy proves essential in today’s complex digital ecosystem. Multiple security measures create a comprehensive defense that addresses various potential vulnerabilities. This approach enhances protection against known threats and improves resilience against emerging risks.
At Clouddle, we recognize the importance of strong network security methodologies in safeguarding businesses. Our Network as a Service (NaaS) solution combines networking, entertainment, and security services to provide seamless operations and enhanced protection. Regular assessments, employee training, and partnerships with trusted security providers remain key components of a forward-thinking security strategy.


