Hospitality properties handle millions of guest records annually, making them prime targets for cybercriminals. Data breaches cost the hospitality industry an average of $4.45 million per incident, according to IBM’s 2024 Cost of a Data Breach report.
At Clouddle, we’ve seen firsthand how hospitality network security services have become non-negotiable. The right protection strategy stops ransomware, secures payment systems, and keeps guest information safe from the threats that plague this sector.
What Makes Hospitality Networks Such Attractive Targets
Hospitality properties operate in a state of constant vulnerability. The sector faces a perfect storm of circumstances that cybercriminals exploit relentlessly. According to VikingCloud’s 2025 State of Hospitality Cyber Report, 82% of North American hotels fell victim to cyberattacks last summer, and 66% of hotel IT and security executives expect more frequent attacks this year. The threats aren’t abstract possibilities-they’re happening now, across properties of all sizes.

Guest-Facing Systems Present the Highest Risk
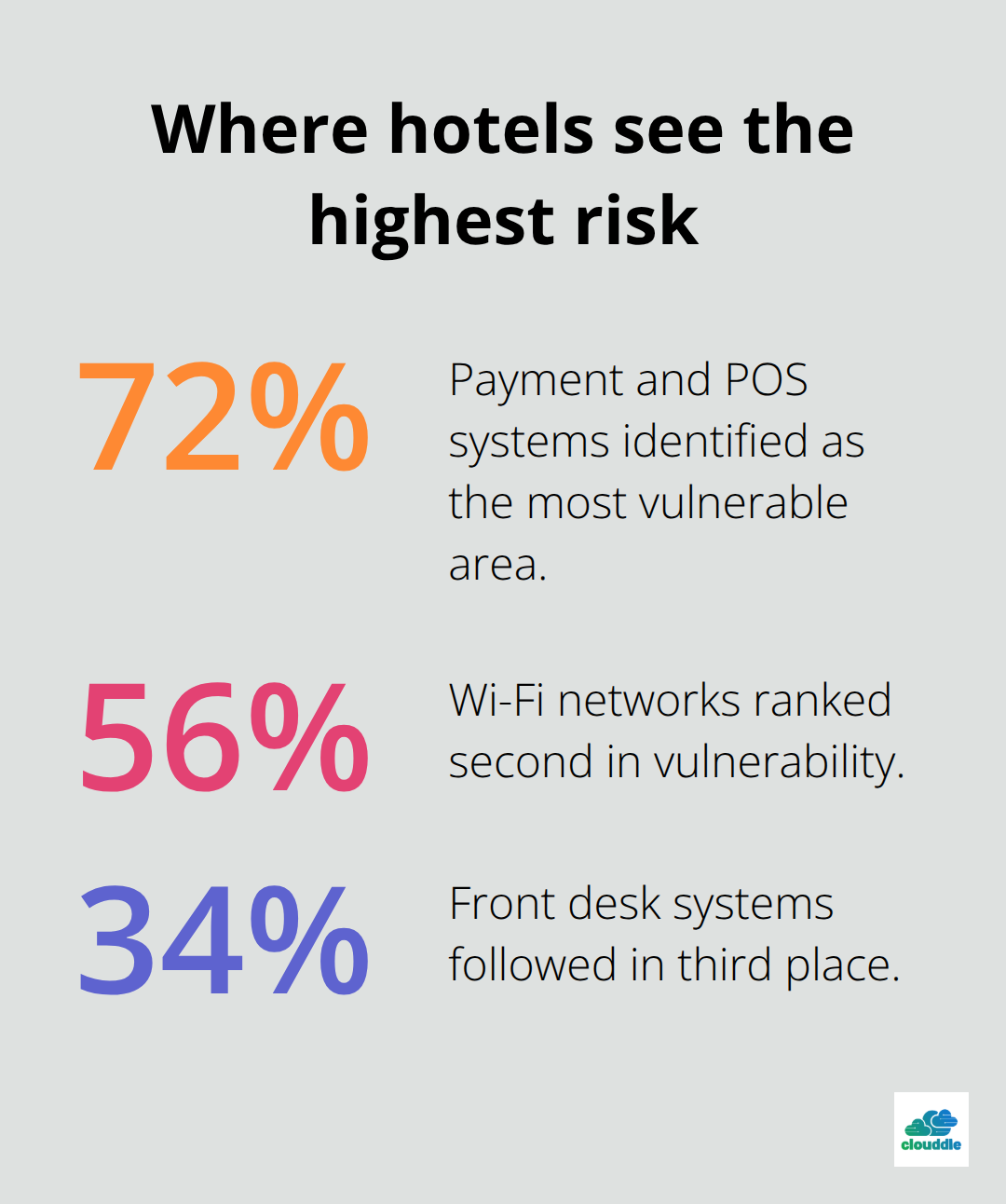
Guest-facing systems like payment and POS systems represent the highest risk, with 72% of hotels identifying these as their most vulnerable area. Wi-Fi networks rank second at 56%, followed by front desk systems at 34%.
This concentration of risk means attackers know exactly where to strike. Marriott’s massive breach exposed over 300 million guest records, resulting in a $52 million FTC settlement that reshaped industry standards. The financial damage extends beyond penalties. MGM Resorts experienced a 60-hour ransomware-induced outage in 2023 that paralyzed booking platforms, payment networks, and even door lock systems. Properties lose revenue during downtime, face angry guests, and suffer permanent reputation damage.
The data breaches expose credit card information, passport numbers, and personal preferences that criminals sell on dark markets or use for targeted fraud. Compliance requirements add another layer of pressure. Hotels must meet GDPR standards for European guests, CCPA requirements for California residents, and PCI DSS compliance for payment processing. Failure to meet these standards triggers fines and legal exposure that dwarf the cost of proper security infrastructure.
IoT and Payment Systems Create Sprawling Attack Surfaces
Modern hotels deploy hundreds of connected devices that traditional network security never anticipated. Smart locks, keycard readers, thermostats, occupancy sensors, and door systems all connect to hotel networks, and most lack adequate security hardening. Each device represents a potential entry point for attackers. Compromised payment systems pose the most immediate threat because they directly access guest credit cards during transactions.
Malware embedded in POS or Property Management Systems intercepts card data before encryption occurs. These systems often run outdated software because hotels hesitate to take systems offline for updates during operating hours. Front desk staff frequently reuse passwords across multiple systems or write credentials on sticky notes. The combination of legacy systems, minimal patching schedules, and human shortcuts creates environments where attackers operate freely.
Guest Wi-Fi networks amplify the problem. Hotels typically separate guest and administrative networks, but this separation often exists only on paper. Weak encryption, shared passwords, and poor network segmentation mean attackers who compromise guest Wi-Fi can pivot to internal systems. The 2025 VikingCloud report shows that nearly half of hotels cannot confidently detect AI-powered threats, indicating that staff lack both training and detection tools to stop sophisticated attacks.
Ransomware Operators Now Target Hospitality Specifically
Ransomware attacks against hospitality properties have evolved from opportunistic to deliberate. Criminal groups now study hotel operations, identifying which systems cause maximum disruption when encrypted. Attackers lock PMS systems to halt reservations and payments, then demand ransoms that properties feel compelled to pay because every hour offline means lost revenue. The Caesars Entertainment ransomware incident resulted in a $15 million ransom payment, demonstrating that even major operators eventually capitulate.
Smaller properties face even greater pressure because they lack the resources to sustain extended outages. Attackers know this and price their demands accordingly. Phishing remains the entry point for most ransomware campaigns. AI-powered phishing threats targeting hotel staff now include deepfakes that mimic voices and faces with hyperrealism, allowing attackers to impersonate legitimate authority figures. Staff receive emails appearing to come from corporate headquarters or vendor accounts requesting urgent access or password resets.
Hotels with Managed Security Service Providers resolve incidents in under 12 hours at a rate over 80% higher than properties relying on internal teams, according to VikingCloud’s research. This speed difference determines whether ransomware spreads to backup systems or remains contained to a single device. The right security infrastructure and response protocols transform how quickly your property stops an attack before it spreads across critical systems.
Building Your Hospitality Security Infrastructure
Knowing which threats target your property is only half the battle. The other half requires deploying the right security infrastructure that actually stops attackers before they reach guest data. The difference between properties that suffer breaches and those that don’t comes down to three core capabilities: stopping unauthorized traffic at the perimeter, controlling who accesses what systems, and detecting threats in real time before they spread.

Managed Firewalls and Intrusion Detection Stop Attacks at Entry Points
Managed firewalls form the first line of defense by filtering incoming traffic and blocking known malicious IP addresses and domains. Intrusion detection systems work alongside firewalls to analyze network traffic patterns and identify suspicious behavior that firewalls alone might miss. Hotels with these systems deployed catch ransomware command-and-control communications before encryption begins. The firewall examines every packet entering your network, while intrusion detection systems watch for attack signatures and behavioral anomalies that indicate compromise attempts. Together, these tools reject threats at the perimeter rather than allowing them to penetrate deeper into your infrastructure.
Network Segmentation Prevents Lateral Movement Across Systems
Network segmentation separates guest Wi-Fi from administrative networks, payment systems from general operations, and staff workstations from critical infrastructure. This isolation prevents attackers who compromise one segment from pivoting to others. Access control systems enforce role-based permissions so front desk staff cannot reach PMS databases, housekeeping cannot access payment systems, and vendors cannot touch security configurations. Properties that implement network segmentation reduce breach impact because attackers cannot move laterally across systems. The MGM Resorts incident demonstrated this principle harshly: attackers accessed the network through a compromised service account and then moved freely across unsegmented systems for days before detection. Proper segmentation would have contained the threat to a single zone within hours.
24/7 Monitoring Detects Threats Before They Spread
Real-time monitoring separates properties that know when attacks occur from those that discover breaches weeks or months after the fact. VikingCloud’s research shows hotels with managed security service providers resolve incidents in under 12 hours more than 80 percent of the time, while properties without dedicated monitoring average response times measured in days. Round-the-clock monitoring means security analysts watch your network traffic, log files, and system behavior while your staff focuses on guest operations. When anomalies appear (failed login attempts spike, data transfers to unknown locations begin, or encryption processes launch unexpectedly), analysts immediately investigate and contain the threat. Properties cannot afford to wait for morning shifts or rely on staff to notice suspicious activity amid daily operations.
Combining All Three Capabilities Creates Comprehensive Protection
The combination of these three capabilities creates a security posture that stops most attacks before guest data is compromised. Managed firewalls block entry vectors, network segmentation prevents lateral movement, and 24/7 monitoring catches anything that slips through. Properties that deploy all three see dramatically fewer incidents than those implementing any single component alone. However, infrastructure alone cannot protect your property without the people and processes that operate it. Your staff must understand how to recognize threats, follow security protocols, and report suspicious activity immediately.
How to Stop Attacks Before They Reach Your Guests
Multi-Factor Authentication Eliminates Credential-Based Entry Points
Multi-factor authentication represents the single most effective defense against credential theft and unauthorized access, yet fewer than half of hospitality properties enforce it across all systems. When staff members use only passwords to access PMS, payment systems, and administrative panels, attackers who steal credentials through phishing gain immediate access to your most sensitive infrastructure. A second authentication factor-whether a time-based code, hardware token, or biometric verification-makes stolen passwords worthless to attackers. Properties that implement MFA reduces successful credential-based attacks by over 99 percent according to Microsoft security research. The cost of deploying MFA infrastructure remains negligible compared to the expense of responding to a breach. Start with systems that handle guest data and payments, then expand to all staff accounts within 90 days. Do not allow exceptions for remote access or vendor accounts; these represent exactly the entry points attackers exploit most aggressively.
Vulnerability Assessments Expose Weaknesses Before Criminals Weaponize Them
Regular security audits and vulnerability assessments transform your security posture from reactive to proactive. Hotels that conduct quarterly penetration testing identify exploitable weaknesses in payment systems, Wi-Fi networks, and front desk software before criminals weaponize them. Third-party security firms bring specialized tools and expertise that internal teams cannot replicate, testing your defenses from an attacker’s perspective. These assessments should specifically target guest-facing systems where vulnerabilities concentrate. Properties that schedule annual penetration tests catch critical flaws that automated scanning misses, including misconfigurations in access controls and outdated encryption protocols. The assessment identifies not just technical vulnerabilities but also procedural gaps where staff bypass security controls. Implement findings within 30 days for critical issues; do not allow technical debt to accumulate across your infrastructure.
Staff Training Addresses Real Attack Methods, Not Generic Awareness
Phishing attacks succeed because hotel employees receive minimal training on recognizing sophisticated social engineering tactics. AI-powered phishing now includes deepfakes and voice mimicry that make fraudulent requests appear legitimate, yet staff struggle to detect these threats. Training must move beyond generic awareness sessions to scenario-based exercises where staff practice identifying actual attack methods targeting hospitality properties. Show employees real phishing emails sent to hotel staff, demonstrate how attackers impersonate vendors and corporate headquarters, and teach the specific red flags that indicate social engineering attempts. Conduct monthly simulated phishing campaigns where staff receive fake malicious emails and track who clicks suspicious links. Staff who fail simulations receive immediate retraining; this accountability drives behavioral change. Make reporting suspicious activity effortless by establishing a dedicated email address and removing penalties for false alarms; staff must feel safe reporting threats without fear of punishment.
Final Thoughts
Hospitality network security services represent the difference between properties that protect guest data and those that suffer costly breaches. Eighty-two percent of North American hotels experienced cyberattacks last year, and attackers continue refining their methods specifically to exploit hospitality vulnerabilities. Your guests trust you with their credit card information, passport numbers, and personal preferences-that trust evaporates instantly when a breach exposes their data or ransomware locks your systems during peak season.
The security infrastructure outlined in this article-managed firewalls, network segmentation, and 24/7 monitoring-stops most attacks before they reach guest information. Multi-factor authentication eliminates credential-based entry points that phishing exploits so effectively. Regular vulnerability assessments expose weaknesses before criminals weaponize them, and staff training transforms your team into your first line of defense. These components work together to create a comprehensive defense that adapts as threats evolve.
Evaluating your current security posture requires honest assessment of your guest-facing systems, network architecture, and staff capabilities. We at Clouddle combine networking, security services, and 24/7 support to deliver comprehensive hospitality solutions without requiring massive upfront investment. Contact our team to schedule a security assessment and discover exactly where your property stands against modern threats.


