Network attacks cost businesses $4.45 million on average per data breach in 2023, according to IBM’s Cost of a Data Breach Report. The importance of cryptography in network security has never been more apparent.
We at Clouddle see organizations struggling with increasingly sophisticated cyber threats targeting their network infrastructure. Modern cryptographic systems provide the mathematical foundation that keeps sensitive data protected during transmission and storage.
How Cryptography Protects Network Communications
Network cryptography transforms vulnerable data streams into protected communications through three core mechanisms. Advanced Encryption Standard (AES) with 256-bit keys serves as the industry benchmark for symmetric encryption, processing data efficiently on modern processors. RSA encryption with 2048-bit keys handles asymmetric operations, though organizations now favor Elliptic Curve Cryptography (ECC) for its superior performance at equivalent security levels.
Digital Signatures Verify Network Identity
Digital signatures authenticate sender identity and message integrity through hash functions like SHA-256. Digital signatures are used to detect unauthorized modifications to data and verify authenticity. Organizations deploy certificate authorities to manage public key infrastructure, with root certificates that last up to 20 years while intermediate certificates typically expire after 3-5 years. Multi-factor authentication systems that combine digital certificates with hardware tokens achieve 99.9% protection against unauthorized access attempts.
Key Management Systems Automate Security
Modern networks require automated key rotation every 30-90 days to maintain security effectiveness. Hardware Security Modules (HSMs) generate cryptographically secure random keys at rates of 10,000 operations per second. Key distribution protocols like Diffie-Hellman enable secure key exchange without transmitting actual keys across networks. Enterprise systems typically manage 50,000-100,000 active encryption keys simultaneously, with automated lifecycle management that reduces human error by 87% (according to Ponemon Institute research).
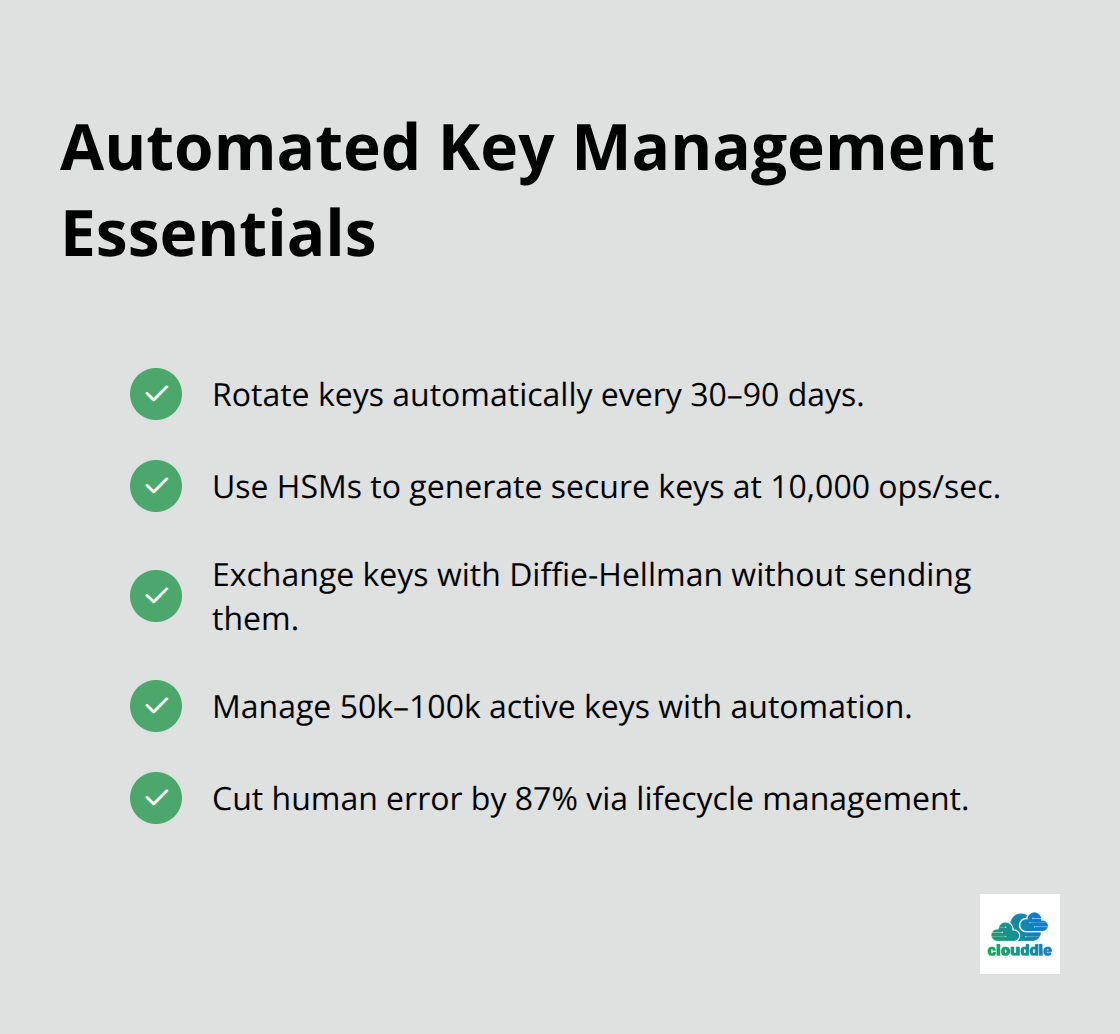
These cryptographic foundations enable specific security protocols that protect different types of network communications across various environments and use cases.
Which Protocols Actually Protect Network Traffic
Transport Layer Security now dominates web communications with TLS 1.3 adopted by 70.1% of surveyed sites by May 2024 according to SSL Labs data. TLS 1.3 reduces connection establishment from two round trips to one, cutting latency by 40% while strengthening cipher suites. Perfect Forward Secrecy generates unique session keys that prevent retroactive decryption even if long-term keys become compromised. Certificate pinning adds another security layer by binding specific certificates to domains, though implementation requires careful planning since incorrect pinning blocks legitimate traffic.
IPSec Transforms VPN Performance
Internet Protocol Security operates at the network layer and encrypts entire IP packets rather than just application data. IPSec tunnel mode achieves throughput rates of 10 Gbps on modern hardware while it maintains AES-256 encryption strength. Site-to-site VPN connections that use IPSec typically show 15-20ms additional latency compared to unencrypted traffic. Authentication Header protocol prevents packet tampering while Encapsulating Security Payload handles both authentication and encryption. Automatic key exchange through IKEv2 reduces VPN reconnection time to under 3 seconds after network interruptions.
WPA3 Eliminates Wireless Vulnerabilities
Wi-Fi Protected Access 3 replaces the vulnerable four-way handshake with Simultaneous Authentication of Equals, which makes password-based attacks mathematically impractical. WPA3 generates unique encryption keys for each device session and prevents lateral movement between connected devices. Enterprise networks benefit from 192-bit encryption strength that meets government security requirements (CNSS Policy 15). Personal networks gain protection against offline dictionary attacks that previously compromised WPA2 within hours.
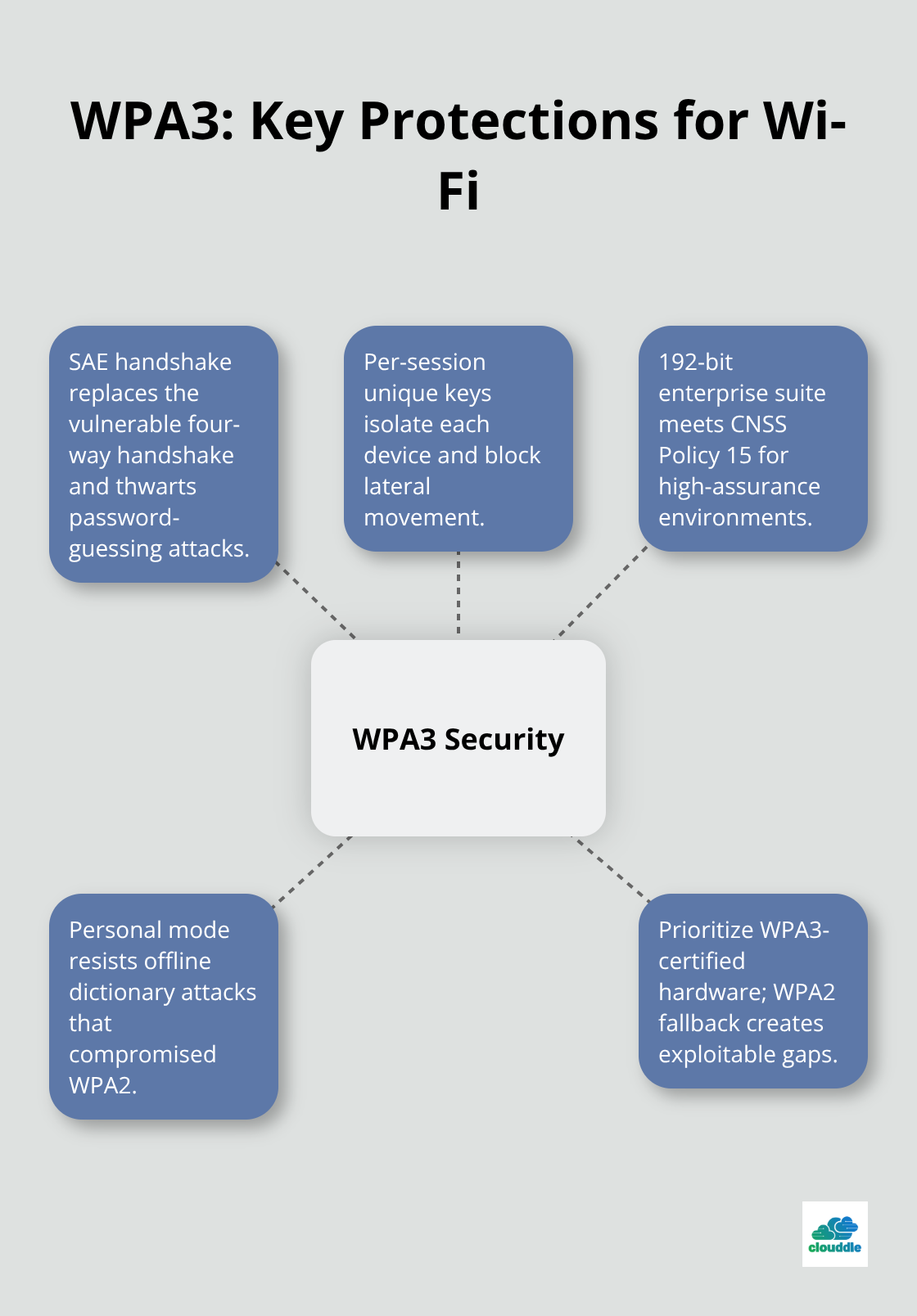
Organizations should prioritize WPA3-certified hardware since backward compatibility with WPA2 creates security gaps that attackers actively exploit.
These protocol implementations form the foundation for real-world security deployments across different industries, where specific requirements drive unique cryptographic approaches.
How Organizations Deploy Cryptography
Enterprise networks process 2.5 quintillion bytes of data daily, which makes cryptographic implementation a matter of operational necessity rather than optional security enhancement. Fortune 500 companies deploy Zero Trust architectures that encrypt every network connection, with organizations implementing comprehensive encryption strategies to protect their data assets. Financial institutions lead cryptographic adoption with end-to-end encryption for all transaction processing, while JPMorgan Chase operates quantum-resistant algorithms across their global network infrastructure. Healthcare systems face stricter requirements under HIPAA compliance and implement Advanced Encryption Standard with 256-bit keys for patient data transmission while they achieve 99.97% uptime through redundant cryptographic systems.
Banks Process 50 Billion Encrypted Transactions Daily
Financial networks handle transaction volumes that would collapse without military-grade encryption protocols. Swift network processes over 42 million messages daily with triple-DES encryption, though major banks now transition to AES-256 for quantum resistance. Payment processors like Visa encrypt credit card data with tokenization systems that replace sensitive information with random values and reduce fraud by 87% according to their 2023 security report. Real-time fraud detection systems analyze encrypted transaction patterns within 100 milliseconds and flag suspicious activity while they maintain customer privacy through homomorphic encryption techniques that enable computation on encrypted data without decryption.
Medical Networks Protect 4.5 Billion Patient Records
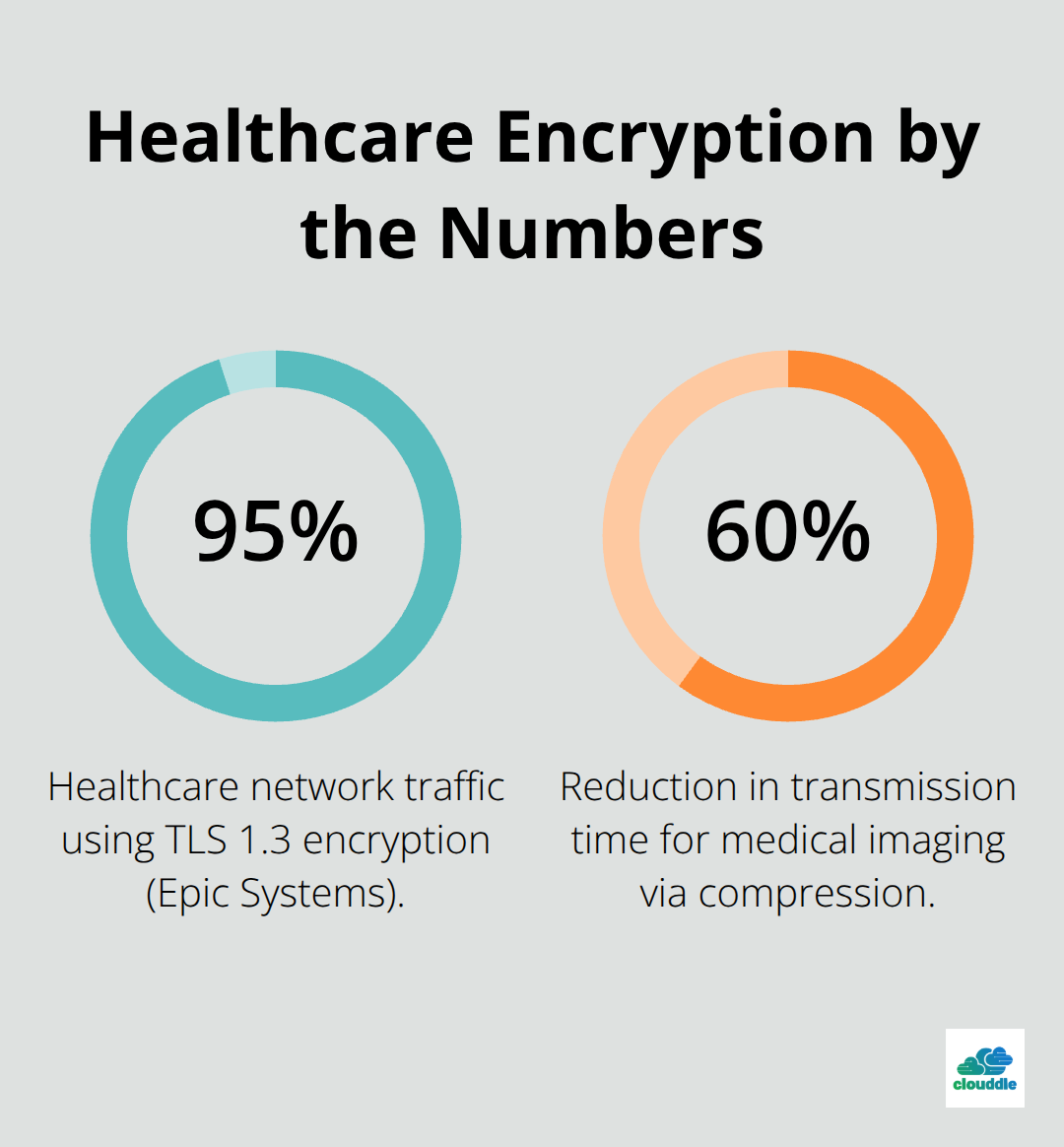
Healthcare organizations encrypt electronic health records during transmission between hospitals, with Epic Systems reports that 95% of their network traffic uses TLS 1.3 encryption. Telemedicine platforms process encrypted video streams that consume 3-5 Mbps per connection while they maintain HIPAA compliance through end-to-end encryption. Medical systems transmit encrypted CT scans and MRI data that average 150-300 MB per file (with compression algorithms that maintain diagnostic quality while they reduce transmission time by 60%).
Remote patient devices generate encrypted data streams every 30 seconds, with edge systems that process vital signs locally before they transmit anonymized patterns to central databases.
Final Thoughts
Cryptographic protection delivers measurable security improvements across all network environments. Organizations that implement comprehensive encryption strategies reduce data breach costs by 51% compared to those with limited cryptographic controls, according to IBM’s 2023 security research. The importance of cryptography in network security extends beyond basic data protection to enable business continuity and regulatory compliance.
Quantum computers will reshape cryptographic requirements within the next decade. Post-quantum algorithms like CRYSTALS-Kyber already undergo standardization through NIST, with major technology companies that plan migration timelines for 2025-2030. Homomorphic encryption enables secure cloud computing without exposure of sensitive data, while zero-knowledge proofs allow authentication without credential revelation.
Professional implementation remains essential for cryptographic effectiveness. Misconfigured encryption systems create false security that attackers exploit regularly (with devastating financial consequences). We at Clouddle provide comprehensive security services that include proper cryptographic deployment and management for hospitality, multi-family dwelling, and senior living industries.


