Network security compliance has become a non-negotiable requirement for businesses across all industries. Organizations face mounting pressure from regulators, customers, and stakeholders to protect sensitive data and maintain robust security standards.
At Clouddle, we understand that achieving compliance can feel overwhelming. This guide breaks down the essential steps, tools, and strategies you need to build a compliant network security framework that protects your business and satisfies regulatory requirements.
Understanding Network Security Compliance Requirements
Major Regulatory Frameworks You Cannot Ignore
NIST Cybersecurity Framework stands as the gold standard for most organizations, though recent data shows 58% of organizations experienced data breaches or cybersecurity incidents in the past two years according to the Ponemon Institute. This framework provides five core functions that work: Identify, Protect, Detect, Respond, and Recover. ISO/IEC 27001 offers international credibility with its systematic approach to information security management, covering 114 security controls across 14 categories. Organizations that follow ISO 27001 report 43% fewer security incidents compared to non-certified companies (based on research from the British Standards Institution).

Industry-Specific Requirements That Demand Attention
Healthcare organizations face HIPAA regulations with penalties that reach $1.5 million per violation, while financial services must comply with SOX requirements and PCI DSS standards that mandate quarterly vulnerability scans and annual penetration tests. Energy companies operate under NERC CIP standards with mandatory 15-minute incident reports. Manufacturing firms that handle defense contracts must meet CMMC Level 3 certification, which requires 130 security controls and third-party assessments that cost between $50,000 to $300,000. The SEC now mandates public companies to disclose material cybersecurity incidents within four business days, which creates immediate compliance pressure that affects stock valuations.
Financial Impact of Compliance Failures
Non-compliance costs have reached devastating levels across industries. GDPR fines have reached over €300 million in total according to the European Data Protection Board, while healthcare HIPAA breaches cost organizations an average of $10.93 million per incident based on IBM Security data. Companies face additional costs that include legal fees (averaging $2.4 million), regulatory investigation expenses of $800,000, and reputation damage that reduces stock prices by 7.5% on average within six months of a major breach announcement. The Verizon Data Breach Investigations Report shows that 95% of successful attacks exploit known vulnerabilities that compliance frameworks specifically address.
These compliance requirements create the foundation for your security strategy, but implementation requires systematic assessment and planning to transform regulatory mandates into actionable security measures.
Essential Steps for Network Security Compliance
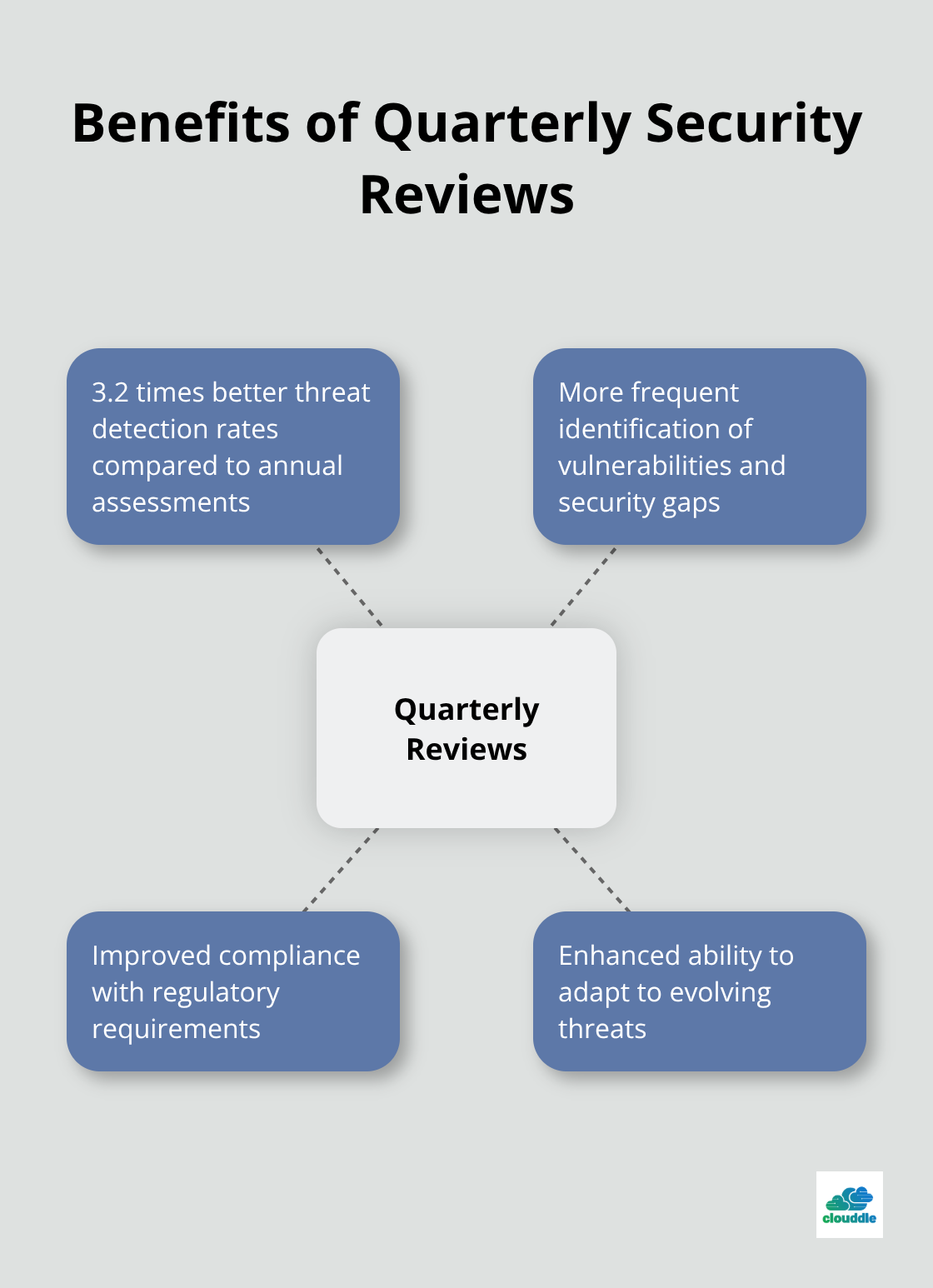
Security assessments form the backbone of effective compliance programs, yet most organizations approach them incorrectly. The Department of Homeland Security reports that 76% of organizations conduct annual assessments when quarterly reviews deliver 3.2 times better threat detection rates. Start with asset discovery using automated tools like Nessus or Qualys that scan your entire network perimeter every 30 days. Document every device, application, and data flow because compliance auditors demand complete visibility. Network segmentation assessments reveal critical gaps where compliance failures occur according to research.
Comprehensive Security Assessment Methods
Asset inventory tools must catalog every device that connects to your network infrastructure. Vulnerability scanners identify security gaps that attackers exploit most frequently. Penetration tests simulate real-world attacks against your systems and reveal weaknesses that automated tools miss. Configuration reviews examine firewall rules, access permissions, and security settings across all network devices. Risk assessments prioritize threats based on potential business impact and likelihood of occurrence (helping teams focus resources on the most critical vulnerabilities).
Access Control Implementation That Actually Works
Multi-factor authentication deployment must reach 100% coverage for privileged accounts within 90 days. Verizon research shows that 61% of breaches involve compromised credentials, making identity management your highest priority. Deploy privileged access management solutions that rotate passwords every 24 hours and log every administrative action. Role-based access controls should follow the principle of least privilege with quarterly access reviews that remove 15-20% of unnecessary permissions. Zero-trust architecture requires device certificates, user verification, and application-level controls that validate every connection attempt against your security policies.
Real-Time Monitoring and Response Systems
Security information and event management platforms must process logs from every network device, server, and application within your infrastructure. IBM’s global Cost of a Data Breach Report 2025 provides up-to-date insights into cybersecurity threats and their financial impacts on organizations. Configure automated alerts for failed login attempts that exceed three attempts per hour, unusual data transfers above 10GB, and privilege escalation events. Incident response procedures require documented playbooks with specific actions for each threat type, communication protocols that notify stakeholders within 15 minutes, and recovery procedures that restore operations within defined time objectives.
Continuous Compliance Monitoring
Automated compliance tools track security controls and generate reports that auditors require. Real-time dashboards display compliance status across all regulatory frameworks your organization must meet. Regular compliance scans identify configuration drift and policy violations before they create audit findings. Documentation systems maintain evidence of security controls and remediation efforts (which auditors examine during compliance reviews). These monitoring capabilities create the foundation for the specialized tools and technologies that streamline compliance management across your entire organization.
Tools and Technologies for Compliance Management
Network monitoring platforms must process massive data volumes without creating alert fatigue that paralyzes security teams. Splunk provides hands-on big data analytics capabilities for processing and deriving business value from data in real time, while SolarWinds Network Performance Monitor tracks 200,000+ network elements across distributed infrastructures. These platforms identify configuration drift within 15 minutes and flag unauthorized changes that create compliance violations. Real-time traffic analysis reveals data exfiltration attempts and policy violations that manual reviews miss entirely.
Security Information and Event Management Platforms
SIEM platforms like IBM QRadar and Microsoft Sentinel aggregate logs from every network device, application, and security tool within your environment. QRadar leverages big data analytics for enhanced cybersecurity, focusing on threat detection, incident response, and SIEM systems. Configure automated playbooks that respond to specific threat patterns within 30 seconds, block malicious IP addresses automatically, and generate incident tickets for security analysts. Custom correlation rules must align with your specific compliance requirements because generic SIEM configurations miss industry-specific threats that regulators scrutinize during audits.
Automated Compliance Reporting Solutions
Compliance automation tools like Rapid7 InsightVM and Tenable Nessus generate reports that map directly to regulatory frameworks without manual intervention. These systems track 500+ security controls simultaneously and produce audit-ready documentation that saves 40 hours per compliance cycle. Automated vulnerability scans run every 24 hours and prioritize remediation based on CVSS scores and regulatory impact ratings. Dashboard visualizations display compliance posture across NIST, ISO 27001, and PCI DSS frameworks with drill-down capabilities that reveal specific control gaps.
Integration and Workflow Automation
Integration with ticketing systems creates automatic remediation workflows that track progress and provide auditors with complete evidence trails of security improvements. API connections between security tools eliminate data silos and create unified compliance dashboards that executives can review in real-time. Automated patch management systems deploy security updates within 72 hours of release (meeting most regulatory requirements for critical vulnerabilities). Workflow orchestration platforms like Phantom and Demisto coordinate responses across multiple security tools and reduce incident response times by 60% compared to manual processes.
Final Thoughts
Network security compliance requires systematic implementation across assessment, access control, and monitoring phases. Organizations that follow structured approaches reduce security incidents by 43% while they avoid costly regulatory penalties that average $10.93 million per breach. The frameworks and tools outlined in this guide create sustainable compliance programs that protect sensitive data and satisfy regulatory requirements.

Companies with robust compliance programs experience 60% faster incident response times and generate audit-ready documentation that saves 40 hours per compliance cycle. These improvements strengthen customer trust and operational resilience while they reduce insurance premiums and legal exposure. Network security compliance delivers measurable business benefits beyond regulatory adherence.
Organizations must schedule quarterly vulnerability assessments, implement automated compliance reports, and maintain current documentation for all security measures. Continuous monitoring and regular updates to security controls form the foundation of effective compliance management (which prevents costly violations and security breaches). We at Clouddle provide managed IT and security services that support compliance efforts across multiple industries through our Network as a Service solutions.


