Network security breaches cost businesses an average of $4.45 million per incident in 2023. The advantages of network security extend far beyond preventing financial losses.
At Clouddle, we’ve seen companies transform their operations by implementing robust security measures. Strong network protection becomes a competitive advantage that drives sustainable business growth.
What Attacks Are Targeting Your Business Right Now
Phishing attacks cause 90% of successful cyber breaches according to cybersecurity research, which makes them the primary threat businesses face today. Ransomware specifically targets companies with fewer than 1,000 employees in 82% of cases, while small businesses experience three times more cyberattack attempts than larger organizations. The financial reality hits hard: 46% of all data breaches occur in businesses with fewer than 1,000 employees, and 61% of small businesses reported cyberattack victimization in 2021.

The Real Cost of Security Failures
Recovery costs from cybercrime incidents can reach $653,587 for small businesses, with 60% facing bankruptcy within six months of a major breach. These numbers reflect direct costs like system recovery, legal fees, and regulatory fines. The hidden costs prove even more devastating: customer trust erosion, operational downtime, and competitive disadvantage. Industries that handle sensitive data face amplified risks – healthcare organizations pay average ransoms of $1.4 million, while financial services experience 300% more attacks than other sectors. Manufacturing companies lose an average of 23 days of production after successful attacks.
Industry Attack Patterns Show Clear Targets
Cybercriminals exploit specific vulnerabilities in different sectors with precision. Healthcare systems face attacks on patient databases and connected medical devices, while retail businesses become targets during high-transaction periods like holidays. Professional services firms experience email-based attacks designed to steal client information and financial data. Construction and real estate companies face threats through project management systems and financial transactions. Manufacturing operations encounter attacks on industrial control systems that can halt production lines entirely.
Attack Methods Evolve Rapidly
Modern attackers use sophisticated techniques that bypass traditional security measures. Social engineering attacks manipulate employees through psychological tactics (often impersonating trusted contacts), while advanced persistent threats infiltrate networks and remain undetected for months. Zero-day exploits target previously unknown software vulnerabilities, and supply chain attacks compromise trusted vendors to access multiple organizations simultaneously.
These attack patterns reveal why businesses need comprehensive security measures that address both technical vulnerabilities and human factors.
Which Security Tools Actually Stop Modern Attacks
Firewall protection serves as your first defense line, but configuration determines effectiveness. Modern firewalls require application-layer inspection rather than simple port blocking – this means they examine actual data content, not just network addresses. Next-generation firewalls with intrusion prevention systems provide enhanced threat protection compared to basic packet filters. Configure your firewall to deny all traffic by default, then create specific rules for necessary business applications. Weekly firewall log reviews reveal attack patterns and help identify configuration gaps that criminals exploit.
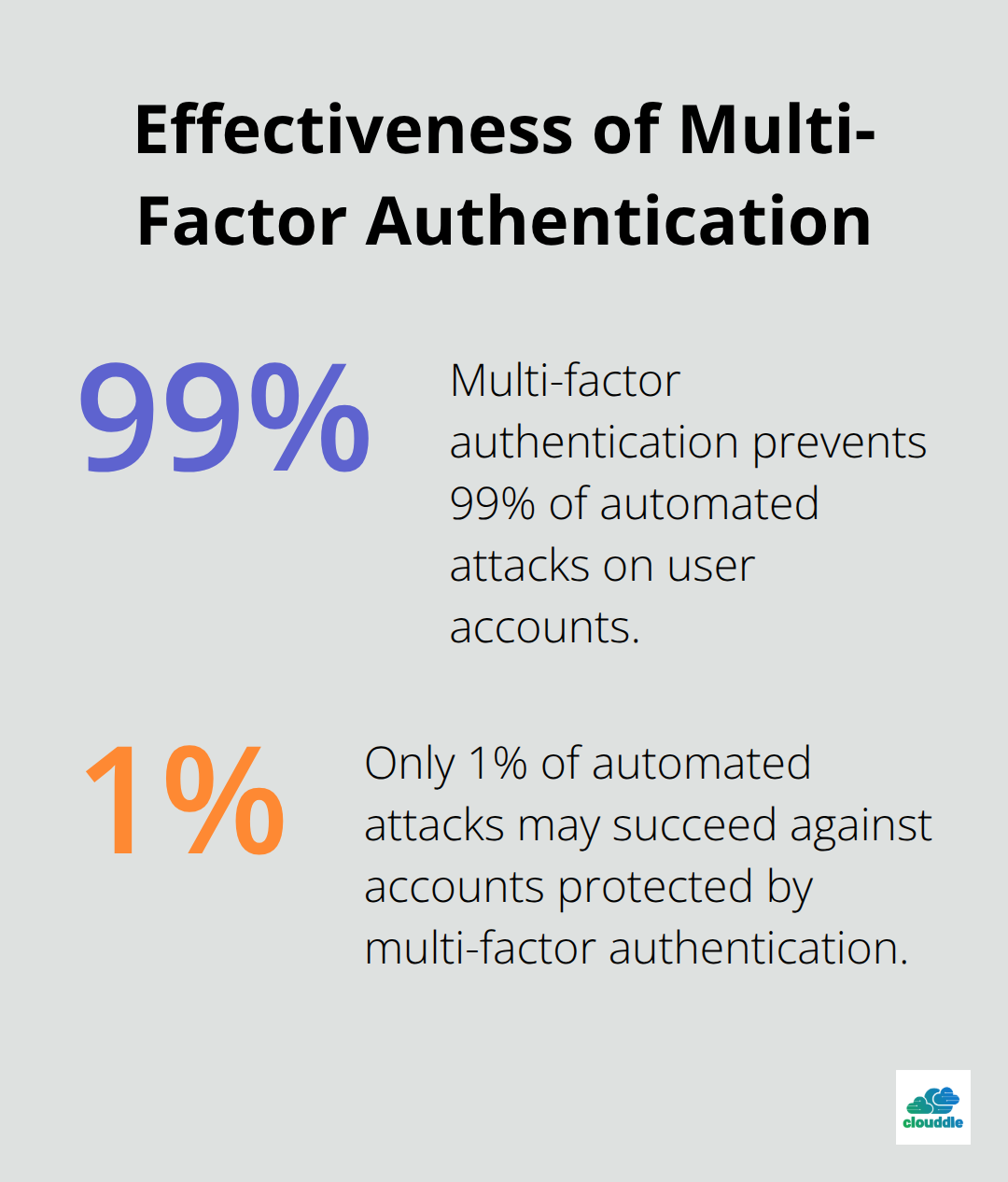
Multi-Factor Authentication Stops 99% of Account Breaches
Microsoft data shows multi-factor authentication prevents 99% of automated attacks on user accounts. SMS-based codes provide minimal security since attackers intercept text messages regularly. Authenticator apps like Google Authenticator or Microsoft Authenticator offer stronger protection through time-based codes. Hardware security keys provide the highest protection level – they resist phishing attempts and work across all major platforms. Implement MFA on every system that contains business data, starting with email accounts and administrative access. Employee resistance disappears when you explain that MFA takes 10 seconds but prevents weeks of breach recovery.
Patch Management Windows Create Attack Opportunities
Unpatched systems account for 60% of successful data breaches according to Ponemon Institute research. Cybercriminals exploit known vulnerabilities within 24 hours of public disclosure, which makes immediate updates essential. Automated patch management systems reduce human error and deployment delays that create security gaps. Critical security patches require installation within 72 hours, while other updates can follow monthly schedules. Test patches on isolated systems first to prevent operational disruptions. Windows Update for Business and similar enterprise tools streamline this process across multiple devices simultaneously.
Network Monitoring Detects Threats in Real-Time
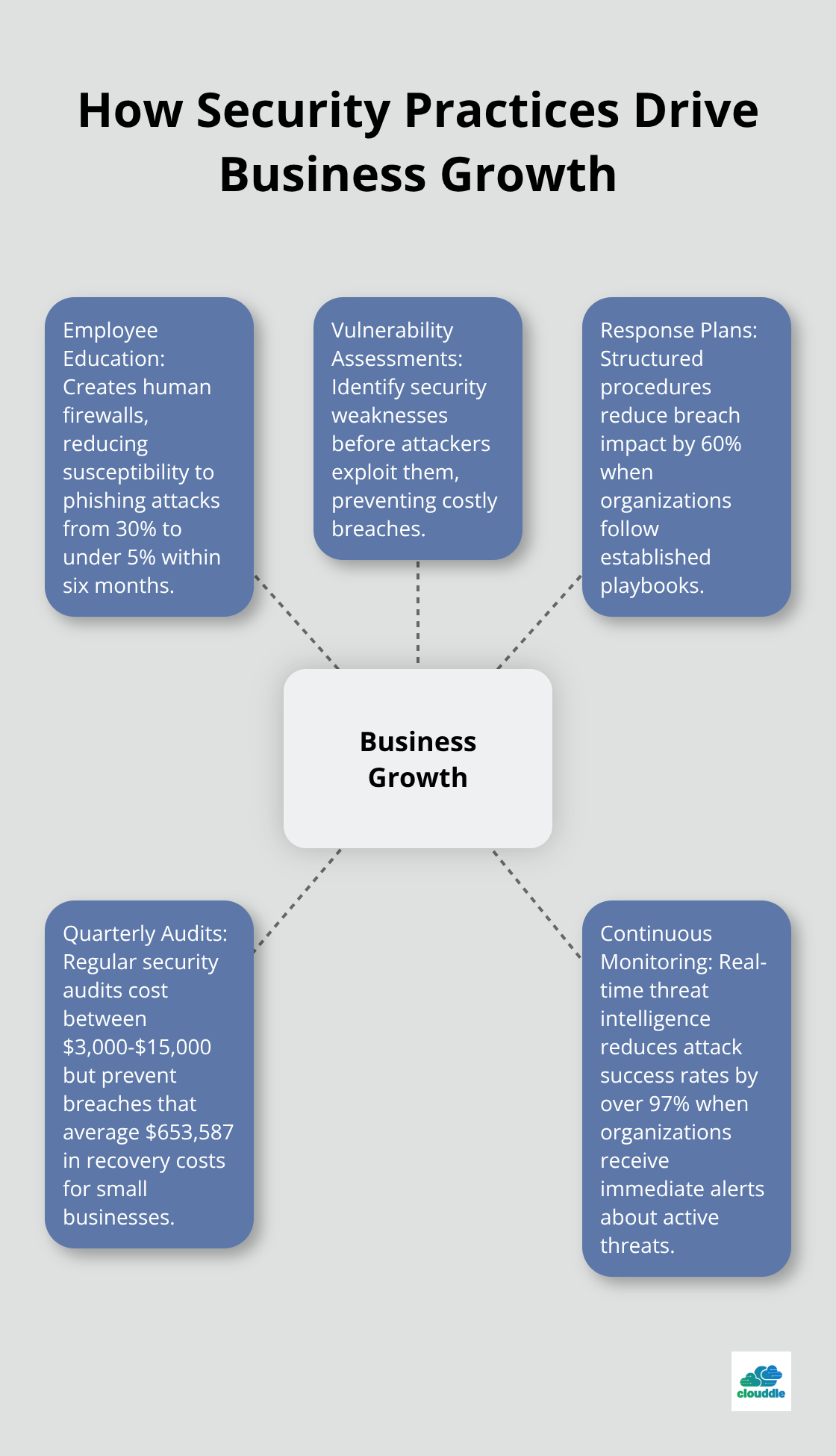
Advanced threat detection tools use artificial intelligence and behavioral analytics to identify complex cyberattacks before they cause damage. These systems monitor network traffic patterns and flag unusual activities (like data transfers at odd hours or access from unexpected locations). Real-time threat intelligence reduces attack success rates by over 97% when organizations receive immediate alerts about active threats. Network monitoring solutions track user behavior and system performance to spot insider threats and compromised accounts quickly.
Security tools work best when they operate together as an integrated defense system rather than isolated solutions.
How Security Practices Drive Business Growth
Companies that invest in security awareness programs show positive training effects according to cybersecurity research, which transforms security from a cost center into a growth enabler. Employees who receive regular phishing simulations and threat awareness programs become the strongest defense against attacks that target human vulnerabilities. Quarterly security sessions that include real attack examples and hands-on exercises produce measurable results within 90 days. Organizations should conduct monthly phishing tests and track click rates – successful programs reduce employee susceptibility from 30% to under 5% within six months.
Employee Education Creates Human Firewalls
Staff members who understand current threats like business email compromise, fake invoices, and credential harvesting attacks protect organizations more effectively than generic security concepts. Interactive workshops that simulate real attack scenarios help employees recognize suspicious emails and social engineering attempts. Companies track improvement through metrics like reduced click rates on test phishing emails and faster threat reporting times. Security champions within each department spread awareness and reinforce best practices during daily operations.
Vulnerability Assessments Prevent Costly Breaches
Quarterly vulnerability assessments identify security weaknesses before attackers exploit them, with penetration tests that simulate real-world attack scenarios. Network traffic analysis examines all connected devices including IoT sensors, printers, and mobile devices that often contain outdated firmware. Access control audits reveal excessive user permissions – the principle of least privilege restricts account creation and permission levels to only the resources a user needs for authorized activities. Third-party vendor security reviews protect against supply chain attacks that compromise trusted partners to access your network (regular security audits cost between $3,000-$15,000 but prevent breaches that average $653,587 in recovery costs for small businesses).
Response Plans Minimize Attack Impact
Structured incident response procedures reduce breach impact by 60% when organizations follow established playbooks with clear roles and communication protocols. Response teams include IT leadership, legal counsel, communications staff, and executive decision-makers who can authorize emergency spending. Recovery procedures prioritize critical business systems and customer-facing operations to minimize revenue loss during incidents. Backup restoration tests every 90 days confirm data recovery capabilities work when needed – untested backups fail 40% of the time during actual emergencies. Post-incident analysis identifies security gaps and process improvements that strengthen defenses against future attacks.
Final Thoughts
Network security transforms from a defensive expense into a competitive advantage when companies implement it strategically. The advantages of network security extend beyond breach prevention to include customer trust, operational efficiency, and sustainable growth. Companies with robust security infrastructure experience fewer disruptions, faster recovery times, and stronger market positions.
Your implementation roadmap starts with immediate actions: deploy multi-factor authentication across all systems, configure next-generation firewalls with application-layer inspection, and establish automated patch management. Within 90 days, conduct vulnerability assessments and implement employee training programs that reduce phishing susceptibility below 5%. Long-term success requires quarterly security audits, continuous threat monitoring, and incident response plans that minimize breach impact by 60%.
We at Clouddle understand that comprehensive security requires integrated solutions that work together seamlessly. Our Network as a Service platform provides businesses with enterprise-grade security without the complexity of traditional implementations. The investment in proper network security pays dividends through operational stability and competitive advantage in an increasingly connected business environment.


