Cybersecurity threats are evolving at an alarming rate, leaving many businesses vulnerable to attacks. At Clouddle, we understand the critical need for robust protection against these ever-changing risks.
Managed IT security solutions offer a comprehensive approach to safeguarding your digital assets. This guide will help you navigate the process of selecting the right security partner for your organization’s unique needs.
Assess Your IT Security Needs
Uncover Security Vulnerabilities
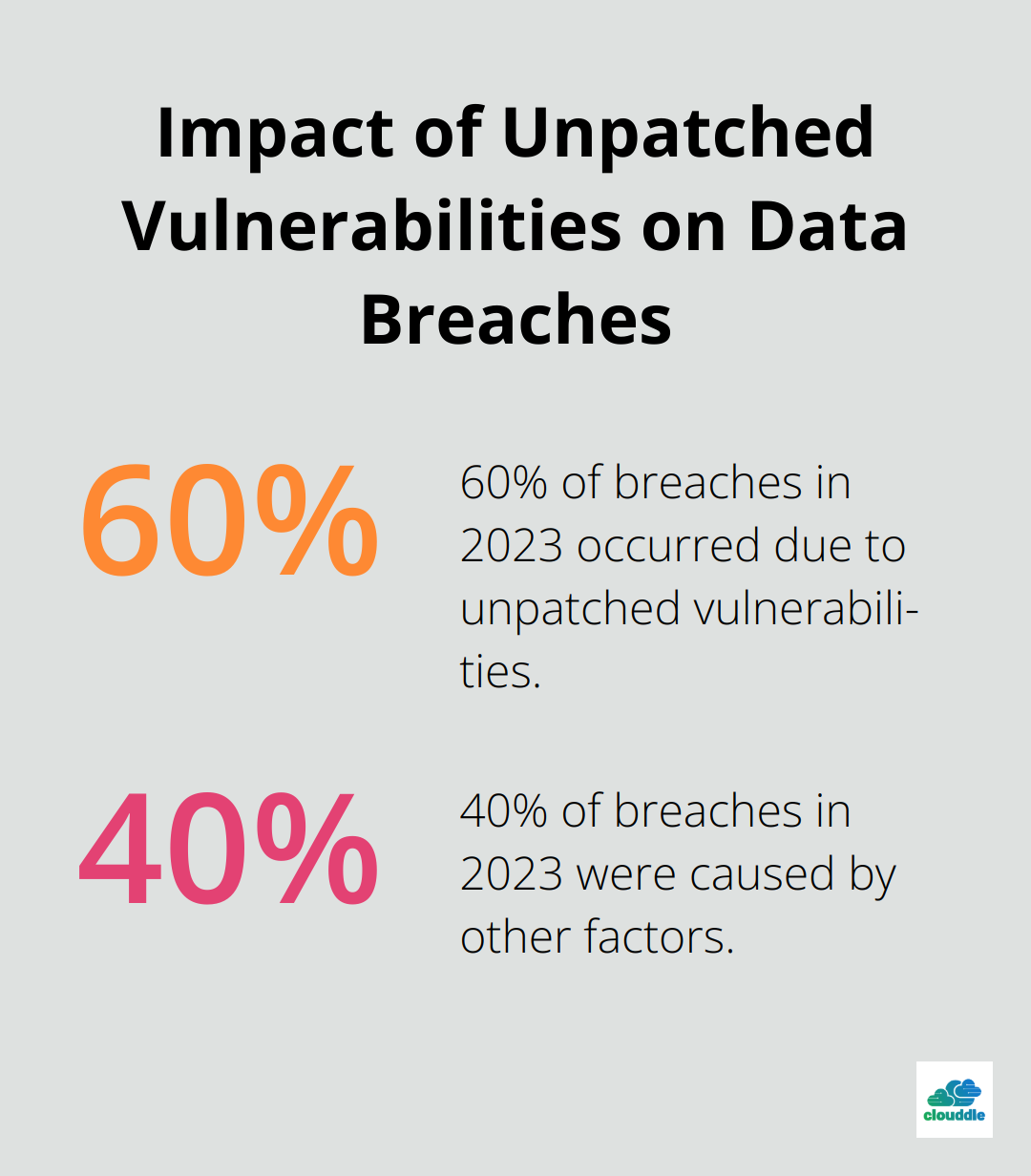
The first step in choosing the right managed security solution is to conduct a comprehensive security audit. This process involves using automated tools for real-time monitoring, regularly reviewing security logs, conducting vulnerability assessments, and adjusting controls based on findings. A recent study by Ponemon Institute revealed that 60% of breaches in 2023 occurred due to unpatched vulnerabilities. To avoid this pitfall, use vulnerability assessment tools or engage a third-party auditor to identify your weak spots.
Evaluate Your Risk Appetite
After identifying vulnerabilities, assess your organization’s risk tolerance. This doesn’t mean eliminating all risks (an impossible task), but understanding which risks you’ll accept and which need immediate attention. For example, a financial services firm might have zero tolerance for data breaches, while a small retail business might prioritize point-of-sale system security.
Navigate Compliance Requirements
Industry-specific regulations can significantly impact your security needs. Healthcare organizations must comply with HIPAA, while companies handling credit card data need to adhere to PCI DSS. Failure to meet these standards can result in hefty fines (HIPAA violations alone resulted in over $15 million in penalties in 2023). Identify which regulations apply to your business and make them a cornerstone of your security strategy.
Align Security with Your Budget
Consider your budget constraints when selecting a managed IT security solution. While it’s tempting to opt for the most comprehensive package, it’s not always necessary or feasible. 72% of companies in IT services and software plan to increase their cybersecurity budgets in 2025, while only 48% in the public sector will do the same. Focus on solutions that address your most critical needs first, then scale up as your budget allows.
Select a Tailored Approach
Choosing the right managed IT security solution isn’t just about ticking boxes-it’s about creating a customized approach that fits your unique business landscape. A thorough assessment of your current IT infrastructure will equip you to select a solution that not only protects your assets but also supports your business goals.
Now that you’ve assessed your IT security needs, it’s time to explore the key features you should look for in managed IT security solutions. These features will form the backbone of your cybersecurity strategy and help you stay ahead of evolving threats.
Essential Features of Top-Tier Managed IT Security Solutions
Round-the-Clock Vigilance
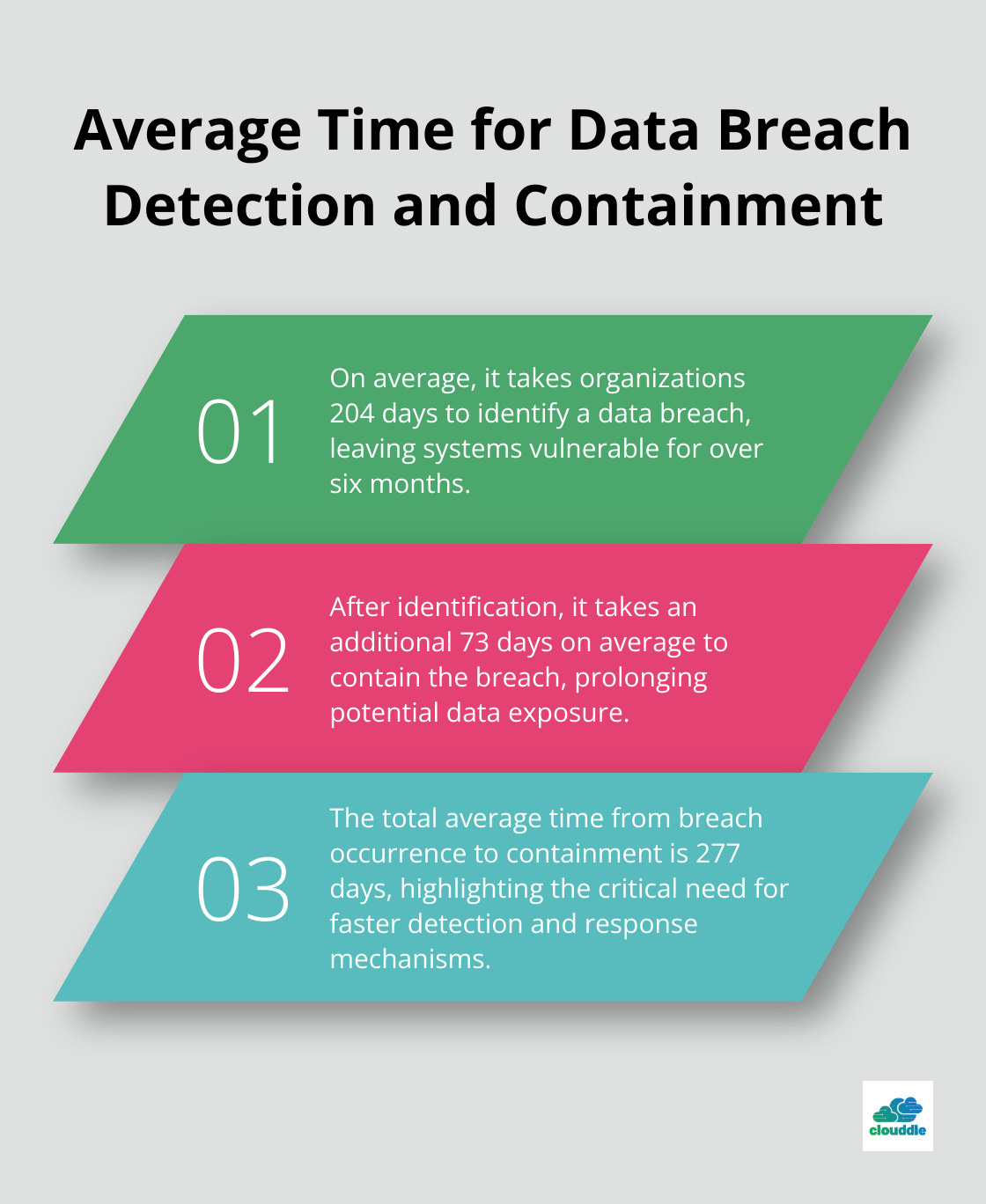
24/7 monitoring and threat detection form the cornerstone of effective cybersecurity strategies. It takes organizations an average of 204 days to identify a data breach and 73 days to contain it. Top-tier solutions employ AI and machine learning to detect anomalies quickly, slashing response times. When evaluating providers, prioritize those offering continuous monitoring with real-time alerts.
Swift Incident Response
In security incidents, time is of the essence. IBM’s global Cost of a Data Breach Report 2025 provides up-to-date insights into cybersecurity threats and their financial impacts on organizations. An effective managed security solution must include rapid incident response and remediation. Providers should present a clear, documented process for addressing and mitigating threats promptly.
Proactive Vulnerability Management
Staying ahead of potential threats requires a robust vulnerability management program. Your security solution should help navigate this sea of potential weaknesses. Look for regular scans, vulnerability prioritization, and swift patching focused on your infrastructure’s most critical areas.
Comprehensive Security Awareness Training
Human error remains a significant factor in security breaches. Effective security solutions should offer engaging, evolving training programs that adapt to emerging threats. This proactive approach empowers employees to become the first line of defense against cyber attacks.
Integrated Cloud Security
As businesses increasingly rely on cloud services, integrated cloud protection becomes paramount. Your managed security solution should offer robust cloud protection (including data encryption, access controls, and compliance management) tailored to your specific cloud environment.
These key features form the foundation of a comprehensive cybersecurity strategy. As you evaluate potential managed IT security providers, consider how they address each of these critical areas. The next step in your selection process involves a thorough assessment of managed security service providers themselves.
How to Evaluate Managed Security Service Providers
Selecting the right Managed Security Service Provider (MSSP) is essential for your organization’s cybersecurity. Here’s how to effectively evaluate potential MSSPs:
Verify Certifications and Expertise
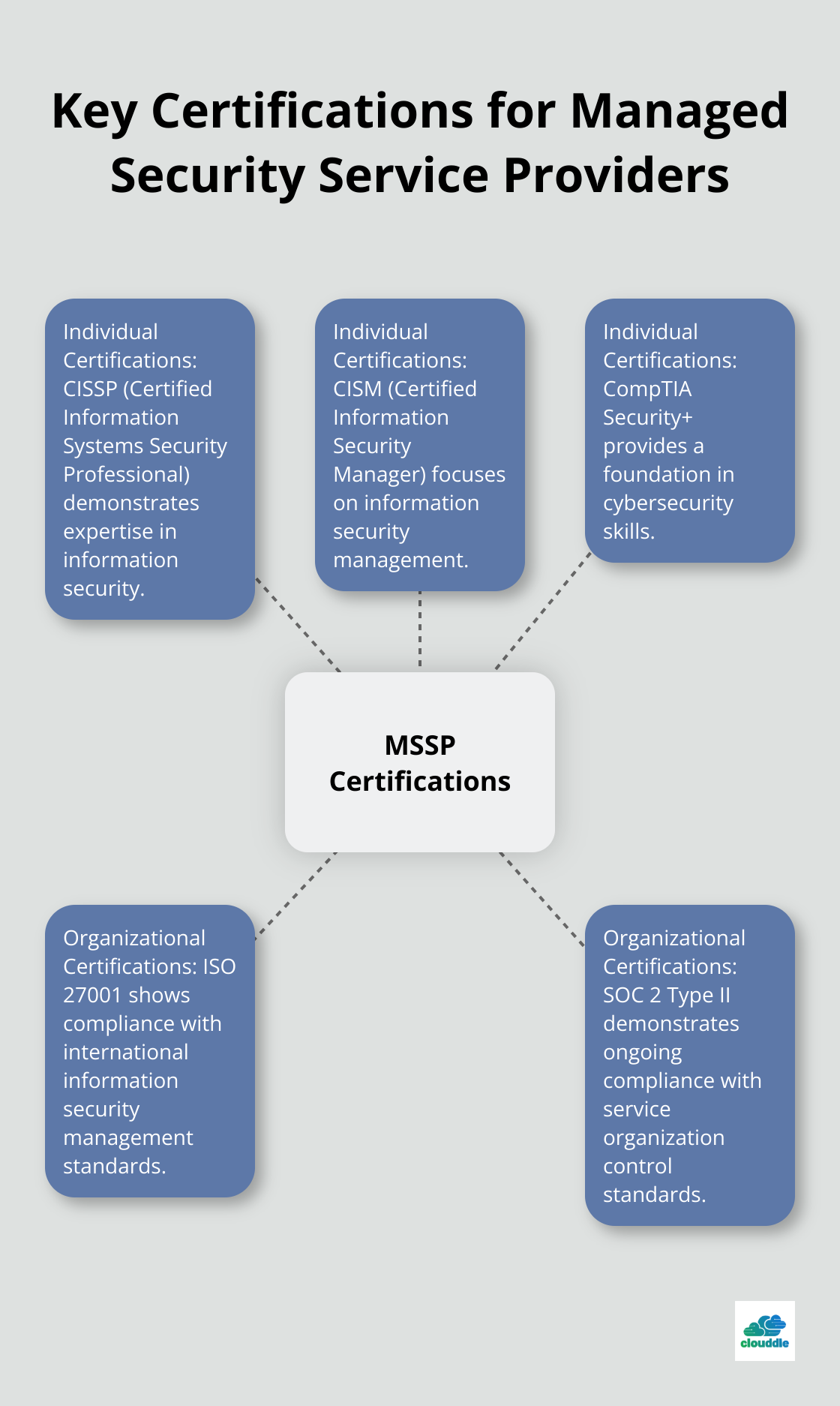
Start by examining the provider’s industry certifications. Look for recognized credentials like CISSP, CISM, or CompTIA Security+. These certifications indicate a commitment to maintaining high standards of security knowledge.
Check if the MSSP holds organizational certifications like ISO 27001 or SOC 2 Type II. These demonstrate a company-wide commitment to security best practices.
Assess Technology Stack and Partnerships
Evaluate the MSSP’s technology partnerships and the tools they use. A strong MSSP should have relationships with leading security vendors. If they’re partnered with Palo Alto Networks or Fortinet, that’s a good sign. These partnerships often translate to early access to threat intelligence and cutting-edge security tools.
Ask about their Security Information and Event Management (SIEM) platform. A robust SIEM is critical for effective threat detection and response. SIEM is a configurable security system of record that aggregates and analyzes security event data from on-premises and cloud environments.
Scrutinize Reporting and Communication
Clear, actionable reporting is vital. Ask for sample reports and evaluate their clarity and depth. The best MSSPs provide customizable dashboards and reports that align with your specific needs.
Communication during incidents is equally important. Ask about their escalation procedures and average response times.
Evaluate Scalability and Flexibility
Your security needs will evolve. Ensure the MSSP can scale their services as your business grows. Ask about their capacity to handle increased data volumes and new technologies.
Flexibility in service models is also important. Some organizations prefer a fully outsourced security operation, while others want to retain some control in-house. The right MSSP should offer flexible engagement models to suit your preferences.
Test Customer Support
Don’t underestimate the importance of responsive customer support. Request a trial period or demo to experience their support firsthand. Pay attention to their availability, expertise, and willingness to explain complex issues in understandable terms.
Try to choose an MSSP that excels in this area.
Final Thoughts
Selecting the right managed IT security solutions will significantly impact your organization’s cybersecurity posture. Every organization faces unique risks and compliance requirements, which necessitates a tailored approach to security measures. A personalized strategy ensures optimal protection without overspending on unnecessary features or leaving critical vulnerabilities unaddressed.
Cybersecurity requires ongoing attention and adaptation as your business evolves. Regular reassessment of your needs and adjustment of your managed IT security solutions will help you stay ahead of emerging threats. The potential costs of a data breach (both financial and reputational) far outweigh the investment in robust security measures.
We at Clouddle understand the importance of comprehensive, tailored security solutions for industries like hospitality, multi-family dwelling, and senior living. Our managed IT security services combine cutting-edge technology with 24/7 support to protect your business. Don’t wait until it’s too late-make managed IT security solutions a top priority in your organization today.


