Network security threats grow more sophisticated every day, making the right protection tools essential for any organization. Poor tool selection can leave critical vulnerabilities exposed and create operational headaches.
At Clouddle, we’ve seen businesses struggle with incompatible systems and overwhelming security alerts. This guide breaks down exactly what to look for in network security management tools and how to make the smartest choice for your specific needs.
What Features Make Network Security Tools Effective?
The most impactful network security management tools share three non-negotiable capabilities that separate effective solutions from basic systems. Real-time threat detection stands as the foundation, with AI-powered behavioral analysis proving 67% more effective at catching zero-day attacks compared to signature-based systems (according to Cybersecurity Ventures). Modern tools must analyze network behavior patterns continuously rather than rely on historical threat databases, as 43% of cyberattacks now use previously unknown methods.
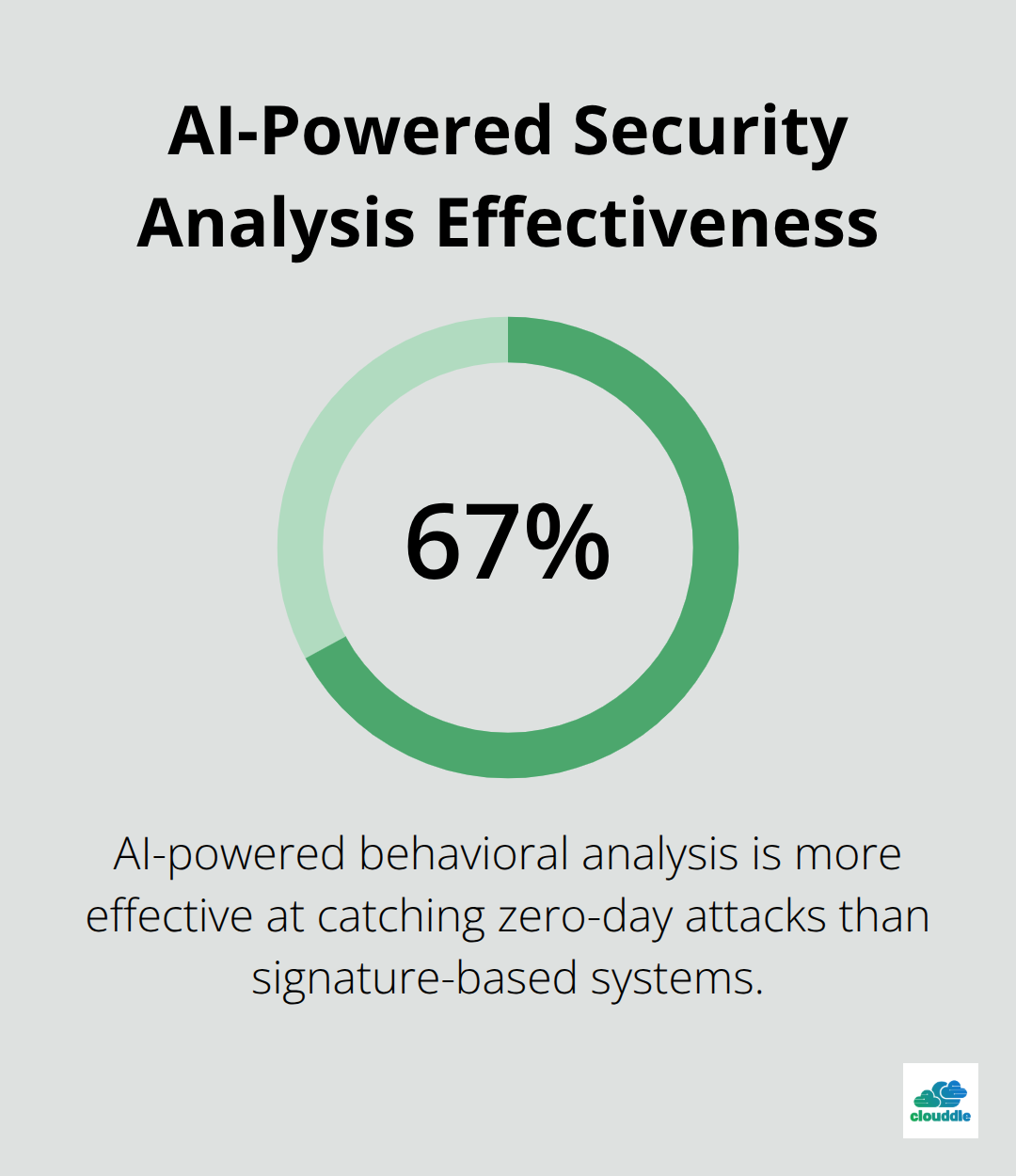
Real-Time Detection Stops Advanced Threats
Advanced platforms like Darktrace and CrowdStrike excel by learning your network’s unique baseline and flagging deviations instantly, while basic tools miss these sophisticated threats entirely. These systems focus on network behavior rather than historical data, enabling detection of previously unseen threats specific to your environment. AI-driven security solutions analyze user behavior continuously, allowing real-time threat detection and proactive responses to risks that traditional signature-based tools cannot identify.
Unified Command Centers Beat Scattered Alerts
Centralized dashboards transform chaotic security operations into manageable workflows, with organizations reporting 73% faster incident response times when using unified interfaces. The best platforms consolidate alerts from firewalls, endpoints, and cloud services into single views with risk scoring that prioritizes genuine threats over false positives. Security teams waste 21% of their time sorting through redundant alerts from disconnected tools, making centralized reporting essential for productivity. Top-tier solutions provide customizable metrics and automated report generation for compliance frameworks like SOC 2 and ISO 27001 (eliminating manual documentation tasks).
Seamless Integration Prevents Security Gaps
Network security tools must integrate flawlessly with existing SIEM platforms, endpoint protection, and cloud infrastructure to avoid dangerous blind spots that attackers exploit. Organizations using integrated security stacks detect breaches 108 days faster than those with standalone tools, according to IBM Security. The most effective platforms offer native APIs and pre-built connectors for popular systems like Splunk, Microsoft Defender, and major cloud providers.
These foundational capabilities set the stage for understanding the different types of security solutions available in today’s market.
Which Security Solution Architecture Fits Your Business?
The fundamental choice between comprehensive platforms and specialized tools determines your security effectiveness and operational complexity. Organizations that use all-in-one platforms like CrowdStrike Falcon or Palo Alto Prisma report 45% lower operational costs compared to those that manage multiple point solutions, according to Gartner research. These integrated platforms eliminate compatibility issues and reduce the average of 76 security tools that enterprises typically manage.
However, specialized tools like Wireshark for network analysis or Nessus for vulnerability scanning often provide deeper functionality in specific areas. Companies with dedicated security teams frequently choose specialized tools for advanced capabilities, while smaller organizations benefit more from unified platforms that require less expertise to manage effectively.
Cloud Platforms Deliver Superior Scalability
Cloud-based security solutions now handle 78% of enterprise network monitoring compared to just 23% five years ago, driven by superior scalability and automatic updates. SolarWinds and Datadog demonstrate how cloud platforms provide instant deployment across hybrid environments without hardware investments or maintenance overhead.
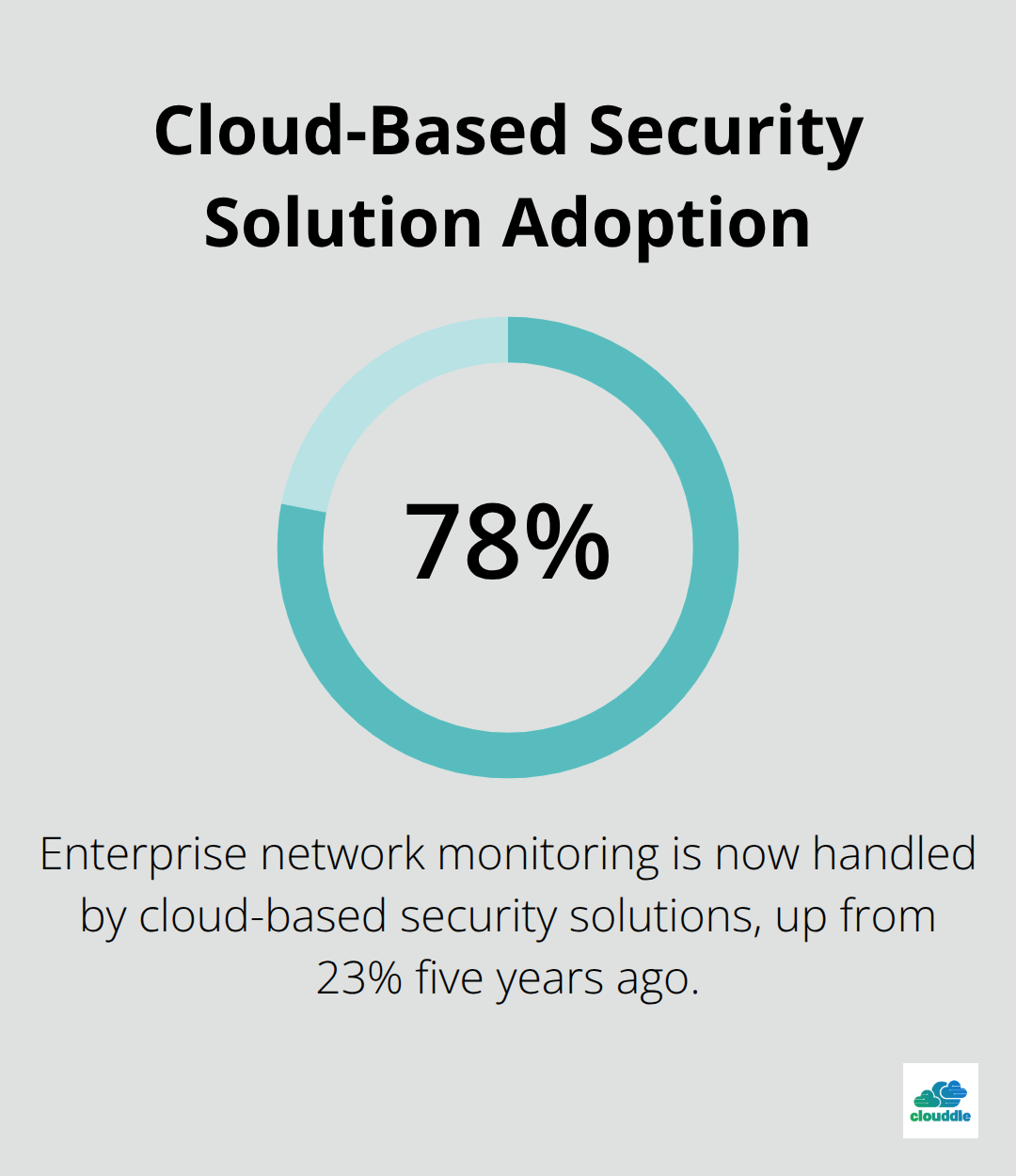
On-premises solutions still serve organizations with strict data residency requirements or air-gapped networks, but cloud platforms reduce deployment time from weeks to hours while they provide global threat intelligence updates. The total cost difference becomes significant at scale, with cloud solutions typically costing 40% less over three years when you factor in hardware, maintenance, and staffing requirements.
Managed Services Address Skills Shortages
The cybersecurity skills gap affects 3.5 million positions globally, which makes managed security services increasingly attractive for organizations that lack internal expertise. Companies that use managed services detect threats 200 days faster than those that rely solely on internal teams (according to Ponemon Institute research).
Managed Security Service Providers handle monitoring, incident response, and compliance reporting while they maintain 24/7 coverage that most internal teams cannot sustain. However, organizations with sensitive data or unique compliance requirements often prefer in-house management for greater control over security policies and faster response times to business-specific threats.
The architecture you choose directly impacts how you evaluate and compare specific network security monitoring tools, which requires a systematic approach to match capabilities with your actual security requirements.
How Do You Pick the Right Security Tool for Your Organization?
Security requirements analysis starts with mapping your actual attack surface, not theoretical frameworks. Organizations with fewer than 500 endpoints typically need unified platforms like CrowdStrike or SentinelOne that handle multiple security functions, while enterprises above 2,000 endpoints often benefit from specialized tools like Splunk for SIEM and Nessus for vulnerability management. Compliance requirements drive tool selection more than technical preferences, with healthcare organizations that require HIPAA-compliant solutions and financial services that need tools supporting PCI DSS frameworks.
Network complexity matters tremendously – hybrid cloud environments with AWS, Azure, and on-premises systems demand tools with native multi-cloud visibility, while single-cloud deployments can use provider-specific solutions. Small businesses need different approaches than enterprises when building secure network infrastructure.
Pricing Models Hide True Costs
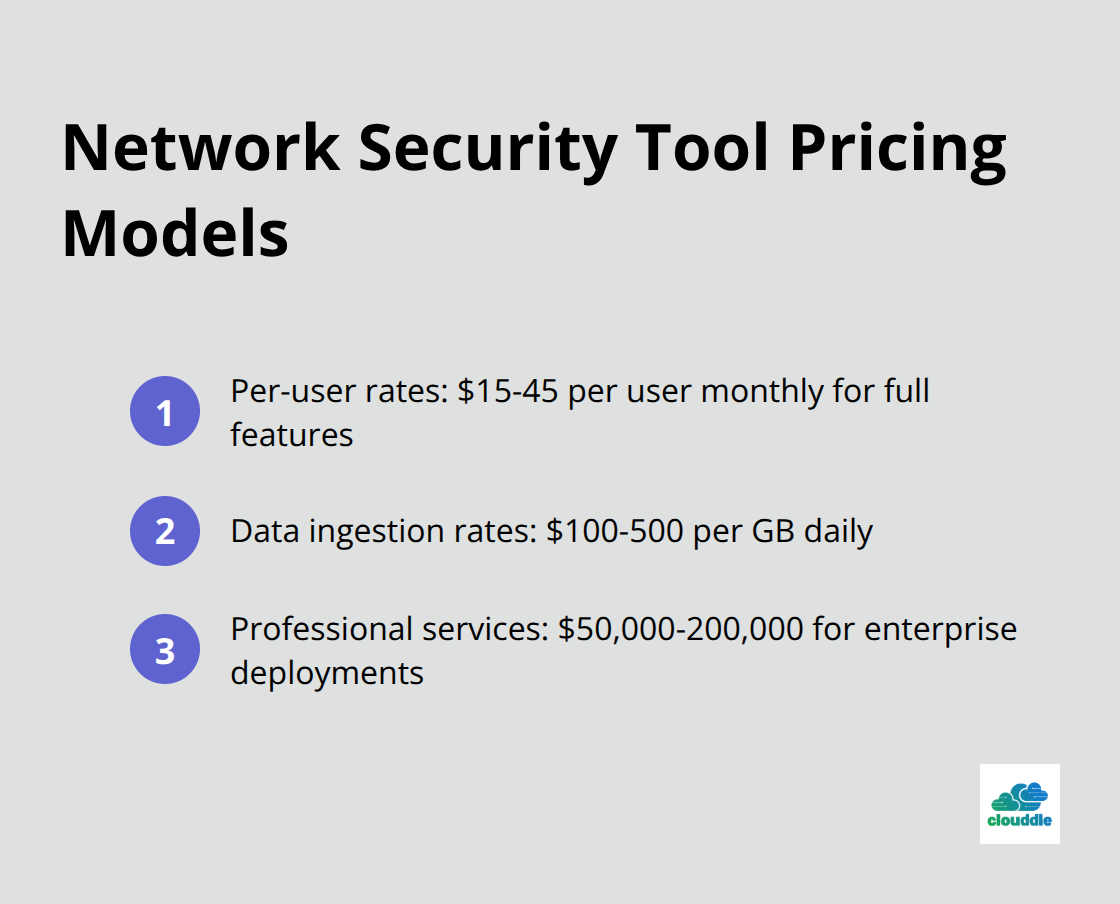
Per-user rates seem straightforward but become expensive as teams grow, with some platforms that charge $15-45 per user monthly for full features. Data ingestion rates work better for large organizations, typically ranging from $100-500 per GB daily, though costs spike unpredictably during security incidents when log volumes increase above normal levels.
Total ownership costs include hidden expenses like professional services for implementation, which average $50,000-200,000 for enterprise deployments, plus ongoing training that consumes significant security team time during the first year. Managed services eliminate these variables with fixed monthly rates but cost more than self-managed solutions over three years.
Trial Testing Reveals Performance Reality
Proof-of-concept deployments expose compatibility issues that vendor demos never show, with organizations discovering integration problems during trials. Deploy tools in production-like environments with actual network traffic volumes, not sanitized lab conditions that hide performance bottlenecks.
Test alert accuracy through simulated attacks – quality tools maintain low false positive rates while detecting MITRE ATT&CK techniques effectively. Response time testing matters more than feature counts, with top-tier platforms delivering threat alerts within 60 seconds compared to longer response times for basic solutions.
Final Thoughts
Network security management tools require careful evaluation of real-time threat detection capabilities, centralized reporting functions, and seamless integration with existing infrastructure. Organizations that prioritize AI-powered behavioral analysis over signature-based systems achieve 67% better protection against zero-day attacks. Unified dashboards reduce incident response times by 73% compared to scattered alert systems.
Your choice between comprehensive platforms and specialized tools depends on team size and expertise levels. Companies with fewer than 500 endpoints benefit most from all-in-one solutions, while larger enterprises often need specialized tools for advanced functionality. Cloud-based platforms now handle 78% of enterprise monitoring due to superior scalability and automatic updates (making them the preferred choice for most organizations).
Professional implementation becomes critical for enterprise deployments, with setup costs that average $50,000-200,000 but prevent costly security gaps. Trial tests in production-like environments reveal compatibility issues that vendor demos miss, which makes proof-of-concept deployments essential before final selection. We at Clouddle provide comprehensive technology solutions that include managed security services, which eliminate the complexity of tool selection and implementation while your organization focuses on core business operations.


