IoT devices face constant cyber threats that can compromise entire business networks. Poor security choices lead to data breaches costing companies millions in damages and lost trust.
We at Clouddle see organizations struggling to find the right IoT network security solutions for their specific needs. This guide breaks down the key factors you need to evaluate when selecting protection for your connected infrastructure.
What Makes IoT Networks Vulnerable to Attacks
Weak Device Authentication Opens Attack Doors
IoT devices ship with default passwords that 31% of users keep unchanged despite having IoT knowledge. Manufacturers prioritize speed over security and leave devices with minimal authentication protocols. Attackers exploit these weak credentials to gain network access within minutes.
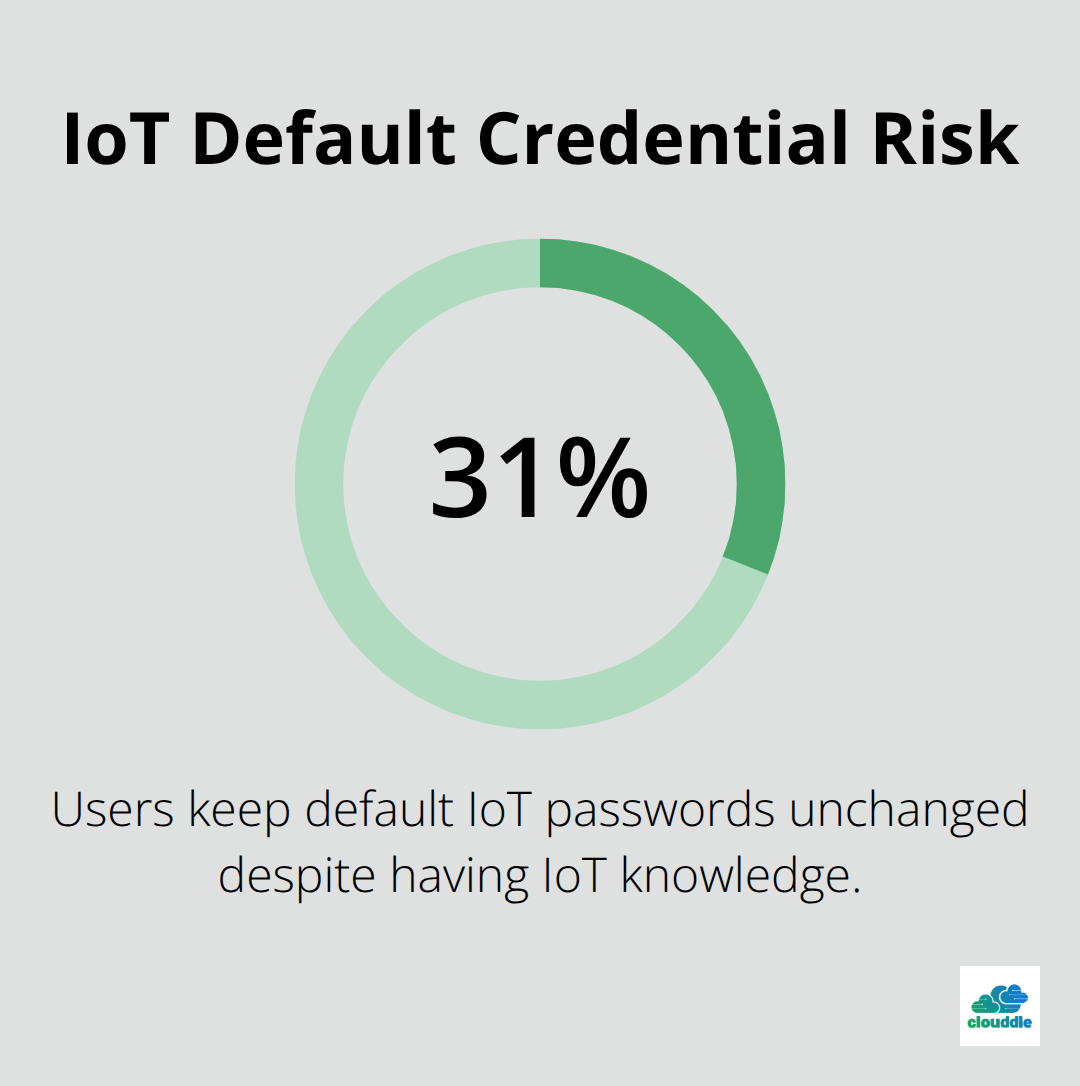
Default usernames like admin and passwords like 123456 remain active on millions of connected devices worldwide. The Mirai botnet infected 600,000 devices in 2016 when it scanned for these predictable login combinations. Device manufacturers often embed hardcoded credentials that users cannot modify, which creates permanent backdoors for cybercriminals.
Network Traffic Interception Exposes Sensitive Data
Unencrypted communication protocols allow attackers to intercept data that travels between IoT devices and backend systems. Attackers target IoT communications that lack proper encryption protection. Man-in-the-middle attacks capture sensitive information that includes user credentials, sensor readings, and control commands.
Wireless protocols like Zigbee and Bluetooth contain known vulnerabilities that enable attackers to eavesdrop on device communications. The WPA2 KRACK attack demonstrated how attackers can decrypt WiFi traffic from IoT devices when they exploit protocol weaknesses. Packet sniffing tools (readily available online) make network interception accessible to novice hackers who target poorly secured IoT deployments.
Cloud Infrastructure Becomes Single Point of Failure
Backend systems that manage IoT fleets concentrate massive amounts of device data and control capabilities in centralized locations. API vulnerabilities in cloud platforms expose entire IoT networks to unauthorized access and data theft. The 2019 Ring camera breach affected 3.2 million users when attackers compromised cloud authentication systems.
Inadequate access controls allow lateral movement within cloud environments and expand attack scope beyond initial entry points. Database misconfigurations expose IoT device logs that contain location data, usage patterns, and personal information to unauthorized parties (often without organizations realizing the exposure).
These vulnerabilities highlight why organizations need comprehensive security solutions that address threats at every level of their IoT infrastructure.
What Security Features Actually Protect IoT Networks
Multi-Layered Authentication Blocks Unauthorized Access
Effective IoT security requires zero-trust authentication that treats every device as potentially compromised. Multi-factor authentication prevents 99.9% of automated attacks according to Microsoft research, but most IoT implementations still rely on single-factor systems. Certificate-based authentication uses PKI infrastructure to provide device identity verification that attackers cannot easily replicate.
Hardware security modules store cryptographic keys in tamper-resistant chips that protect against physical device compromise. Role-based access controls limit device permissions to specific functions and prevent lateral movement when individual devices face breaches.
Real-Time Detection Stops Attacks Before Damage
Network monitoring systems that analyze traffic patterns in real-time catch anomalous behavior within seconds of attack initiation. Behavioral analytics identify when devices communicate outside normal parameters or attempt unauthorized network connections. The SolarWinds attack went undetected for months because organizations lacked continuous monitoring of their network traffic.
Machine learning algorithms detect zero-day exploits when they recognize attack signatures that traditional rule-based systems miss. SIEM platforms correlate events across multiple devices to identify coordinated attacks that target IoT infrastructure. Network segmentation isolates compromised devices and prevents attackers from accessing critical systems.
Encryption Standards Block Data Theft
AES-256 encryption renders intercepted data useless to attackers who lack proper decryption keys. Transport Layer Security protocols protect data in transit between devices and cloud platforms. End-to-end encryption prevents man-in-the-middle attacks that target communication channels.
The NSA recommends Suite B cryptographic algorithms for protection of classified and unclassified information using publicly known algorithms like AES, ECC, and SHA-2. Perfect forward secrecy generates unique session keys that prevent retroactive decryption even when long-term keys face compromise. Hardware-based encryption offloads cryptographic processing from device CPUs and maintains performance while it protects sensitive data streams.
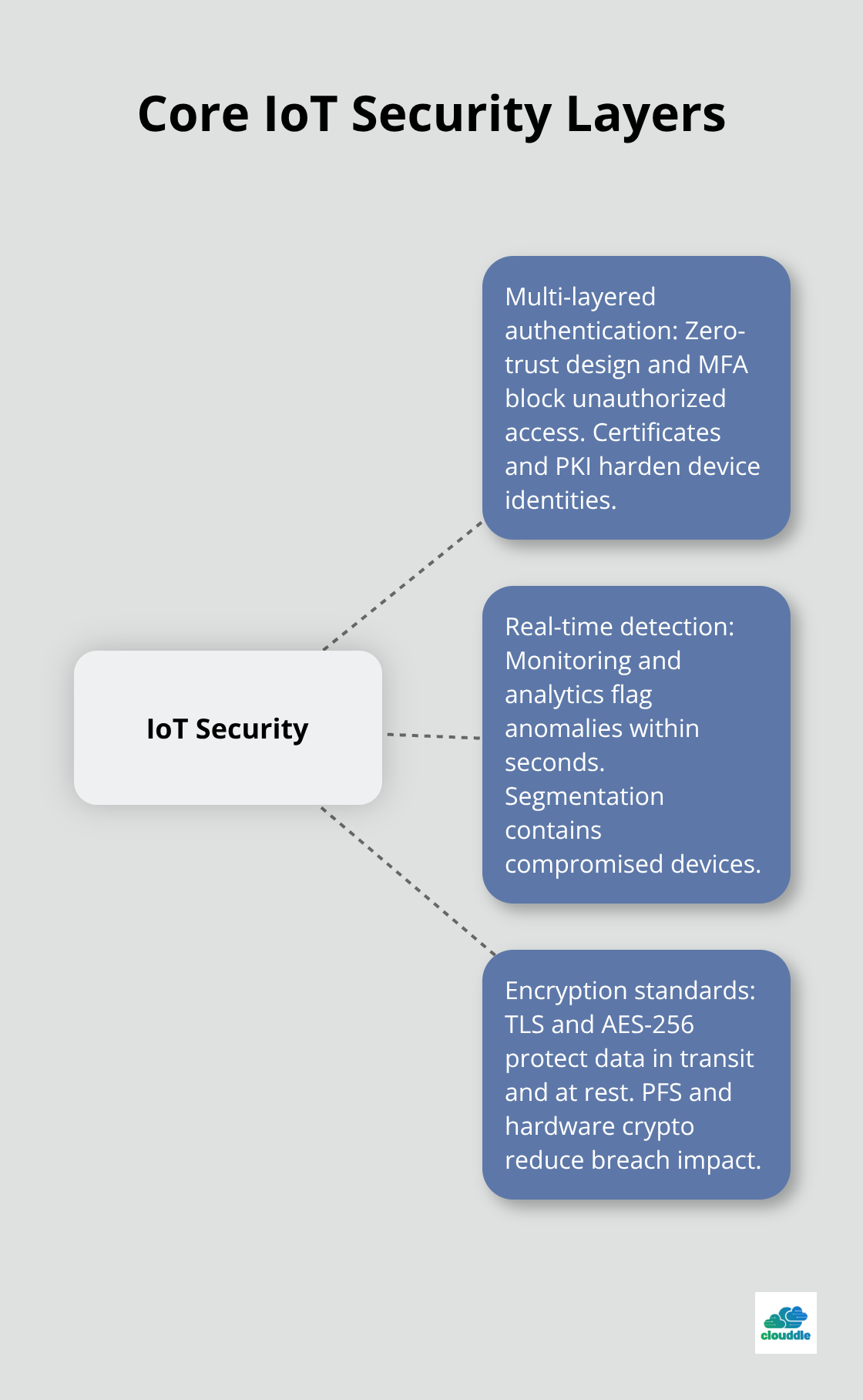
These security features form the foundation of robust IoT protection, but organizations must evaluate how well potential security providers implement and support these capabilities across their specific infrastructure requirements.
How Do You Pick the Right IoT Security Provider
Performance Under Pressure Reveals True Capabilities
Real IoT security providers handle 10,000+ devices without performance degradation while inferior solutions crash at 1,000 concurrent connections. Load tests separate legitimate vendors from marketing-heavy companies that cannot scale. Cisco reports that IoT deployments require a holistic approach working through the entire value chain for security. API response times must stay under 100 milliseconds even during peak traffic periods or your IoT operations will suffer delays.
Integration capabilities matter more than feature lists when existing infrastructure spans multiple vendors. Native support for protocols like MQTT, CoAP, and LoRaWAN prevents costly middleware development. Legacy system compatibility determines whether you can protect current investments or face expensive infrastructure replacement. VMware integration reduces deployment complexity by 40% compared to standalone security appliances that require dedicated hardware.
Certifications Expose Security Provider Credibility
SOC 2 is a compliance and privacy standard that specifies how organizations should manage customer data and related systems through annual third-party security audits rather than self-reported compliance claims. NIST Cybersecurity Framework alignment demonstrates systematic risk management approaches that government agencies require for critical infrastructure protection. ISO 27001 certification indicates comprehensive information security management systems that protect customer data throughout the entire service lifecycle.

FIPS 140-2 Level 3 validation confirms that cryptographic modules meet federal standards for sensitive data protection. Common Criteria EAL4+ certification requires independent laboratory tests of security functions under standardized evaluation criteria. FedRAMP authorization enables government and regulated industry deployment while it validates cloud security controls through rigorous assessment processes.
Implementation Support Determines Success or Failure
24/7 technical support prevents IoT security incidents from escalation into business disruptions that cost companies an average of .6 million per breach (according to IBM research). On-site implementation teams reduce deployment timeframes from months to weeks while they prevent configuration errors that create security gaps. Dedicated customer success managers provide ongoing optimization recommendations that improve security posture over time.
Professional services teams should include certified security architects who understand your industry requirements rather than generalist consultants. Training programs for internal IT staff prevent knowledge gaps that compromise long-term security effectiveness. Response time guarantees under 15 minutes for critical incidents separate serious providers from those that treat IoT security as secondary business lines.
Final Thoughts
IoT network security solutions demand multi-layered authentication, real-time monitoring, and enterprise-grade encryption to defend against evolving cyber threats. Organizations that ignore these fundamentals face average breach costs of $5.6 million and permanent damage to customer trust. Choose security providers with proven scalability beyond 10,000 devices, SOC 2 compliance, and 24/7 technical support.
Integration capabilities with existing infrastructure matter more than feature lists when you protect current investments. NIST framework alignment and FIPS 140-2 validation separate credible vendors from marketing-heavy companies. Implementation success depends on professional services teams with certified security architects who understand your industry requirements (response time guarantees under 15 minutes for critical incidents prevent business disruptions).
We at Clouddle combine managed IT services with comprehensive security solutions through our Network as a Service platform. Start with a comprehensive risk assessment of your current IoT infrastructure and document device inventories, network protocols, and data flows before you select security solutions. Partner with providers who offer ongoing optimization rather than one-time implementations.


