Network attacks cost businesses an average of $4.45 million per breach in 2024, making risk assessment network security a top priority for organizations worldwide.
At Clouddle, we see companies struggle with identifying vulnerabilities before attackers exploit them. Most organizations lack a systematic approach to evaluate their network security posture.
This guide walks you through proven methods to conduct thorough network security assessments and protect your digital assets.
What Makes Network Risk Assessment Essential
Network security risk assessment identifies vulnerabilities in your IT infrastructure before attackers exploit them. This systematic process evaluates potential threats, analyzes their impact, and prioritizes remediation efforts based on business risk. Organizations that skip regular assessments face higher breach costs, with the global average cost showing a 9% decrease over last year driven by faster identification and containment. The process involves three core elements: asset discovery, threat identification, and risk quantification.
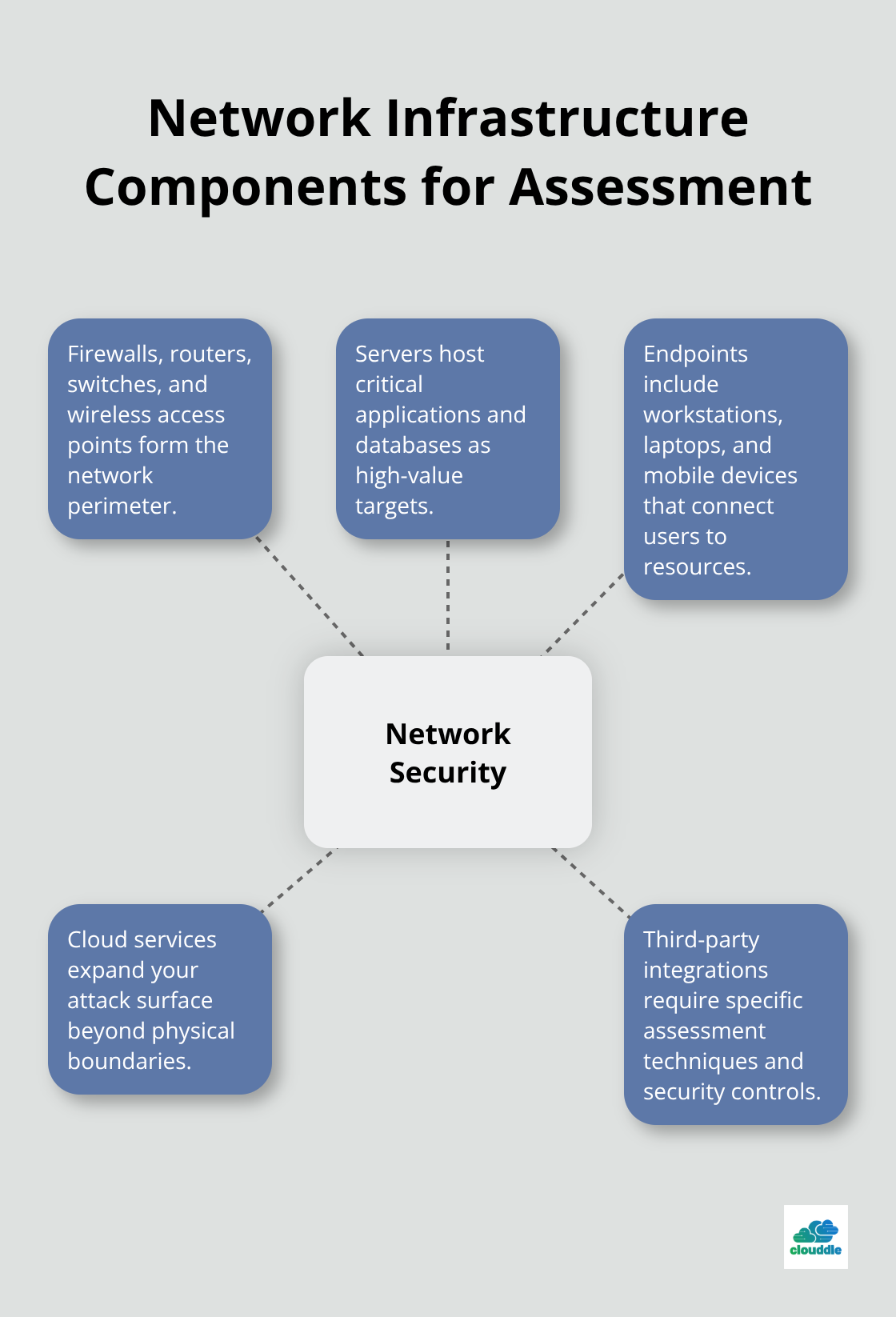
Network Infrastructure Components That Require Assessment
Your network contains multiple attack surfaces that demand evaluation. Firewalls, routers, switches, and wireless access points form the network perimeter. Servers host critical applications and databases as high-value targets. Endpoints include workstations, laptops, and mobile devices that connect users to resources. Cloud services and third-party integrations expand your attack surface beyond physical boundaries. Each component requires specific assessment techniques and security controls.
Critical Threats That Target Modern Networks
Ransomware attackers received approximately $813.55 million in payments in 2024, showing significant criminal activity. Social engineering tactics target employees through phishing emails and credential theft. Malware exploits unpatched software vulnerabilities to gain network access. Insider threats from disgruntled employees or compromised accounts pose significant risks. Misconfigured security settings create backdoors for attackers. Advanced persistent threats use multiple attack vectors to maintain long-term network access.
Why Risk Assessment Frequency Matters
Network threats evolve rapidly, which makes regular assessment schedules necessary. Most organizations conduct annual assessments, but high-risk industries require quarterly reviews. Major infrastructure changes trigger immediate reassessment needs. New software deployments, hardware additions, and policy updates create fresh vulnerabilities. The dynamic nature of cyber threats means yesterday’s secure network may have new weaknesses today.
Now that you understand the foundation of network risk assessment, the next step involves implementing a structured methodology to systematically evaluate your infrastructure vulnerabilities.
How Do You Execute a Complete Network Risk Assessment
Begin with comprehensive asset discovery across your entire network infrastructure. Automated scanning tools like Nmap or OpenVAS identify every connected device, from servers and workstations to IoT devices and forgotten test equipment. Document operating systems, software versions, open ports, and network services for each asset. Classification follows discovery – categorize assets by criticality, data sensitivity, and business impact. High-value targets like domain controllers and databases demand immediate attention, while guest network devices receive lower priority. Network mapping tools such as Lansweeper or ManageEngine AssetExplorer provide real-time visibility into asset changes and help maintain accurate inventories.
Vulnerability Detection and Threat Intelligence Integration
Deploy both authenticated and unauthenticated vulnerability scans with tools like Tenable Nessus or Rapid7 Nexpose. Authenticated scans provide deeper system access and identify more vulnerabilities, while unauthenticated scans simulate external attacker perspectives. Schedule weekly scans for critical systems and monthly scans for standard infrastructure. Integrate threat intelligence feeds from sources like MITRE ATT&CK framework to understand current attack patterns. Cross-reference discovered vulnerabilities with active exploit databases and prioritize patches for vulnerabilities with available exploits. Penetration tests complement automated scans and simulate real attack scenarios to identify logic flaws that scanners miss.
Risk Scoring and Remediation Strategy
Calculate risk scores with the Common Vulnerability Scoring System (CVSS) framework combined with asset criticality and threat likelihood. A critical vulnerability on a public-facing web server scores higher than the same vulnerability on an isolated development machine. IBM’s research provides up-to-date insights into cybersecurity threats and their financial impacts on organizations, making rapid remediation plans essential. Create remediation timelines based on risk scores – patch critical vulnerabilities within 72 hours, high-risk issues within two weeks, and medium-risk vulnerabilities within 30 days (track progress with ticketing systems and validate fixes through follow-up scans).

The next phase requires selecting appropriate tools and frameworks that align with your organization’s specific security requirements and compliance obligations.
Which Tools Work Best for Network Security Assessment
Professional network security assessment requires purpose-built tools that match your organization’s specific infrastructure and compliance requirements. Tenable Nessus is a globally renowned vulnerability scanner that scans for misconfigurations, malware, and outdated software. Rapid7 Nexpose excels in authenticated scans and provides superior asset discovery capabilities across hybrid cloud environments. OpenVAS offers a cost-effective open-source alternative with regular vulnerability feed updates, though it requires more technical expertise to deploy effectively.
Penetration Testing Tool Selection
Metasploit Pro automates exploit delivery and post-exploitation activities for comprehensive security validation. Burp Suite Professional handles web application security tests with advanced crawl and scan features that identify complex vulnerabilities. Nmap provides network discovery and port analysis capabilities that form the foundation of most security assessments. Wireshark captures and analyzes network traffic to identify suspicious communications and protocol anomalies.
Compliance Framework Implementation Strategies
NIST Cybersecurity Framework helps organizations to better understand and improve their management of cybersecurity risk, with clear identify, protect, detect, respond, and recover categories. ISO 27001 certification requires documented risk assessments every 12 months and after significant infrastructure changes. PCI DSS mandates quarterly vulnerability scans for organizations that process credit card data, with approved vendors like Trustwave or Rapid7 that provide certified reports. HIPAA compliance demands annual risk assessments for healthcare organizations (focus on protected health information access controls and encryption requirements).
Documentation Standards That Pass Audits
Risk assessment reports must include executive summaries with quantified risk metrics, detailed vulnerability inventories with CVSS scores, and remediation timelines with assigned ownership. Track mean time to remediation across vulnerability categories to demonstrate security program maturity to auditors and executives. Document false positive rates for each tool to justify tool selection decisions and budget allocations. Maintain evidence of patch deployment verification through follow-up scans and configuration management systems.
Automated Assessment Platform Benefits
Qualys VMDR and Tenable.io provide continuous monitoring evidence that SOC 2 Type II audits require for compliance documentation. These platforms automate vulnerability detection, risk scoring, and report generation to reduce manual assessment overhead. Asset inventories require quarterly updates with change tracking to support compliance audits and incident response activities (automated discovery tools maintain accuracy without manual intervention).
Final Thoughts
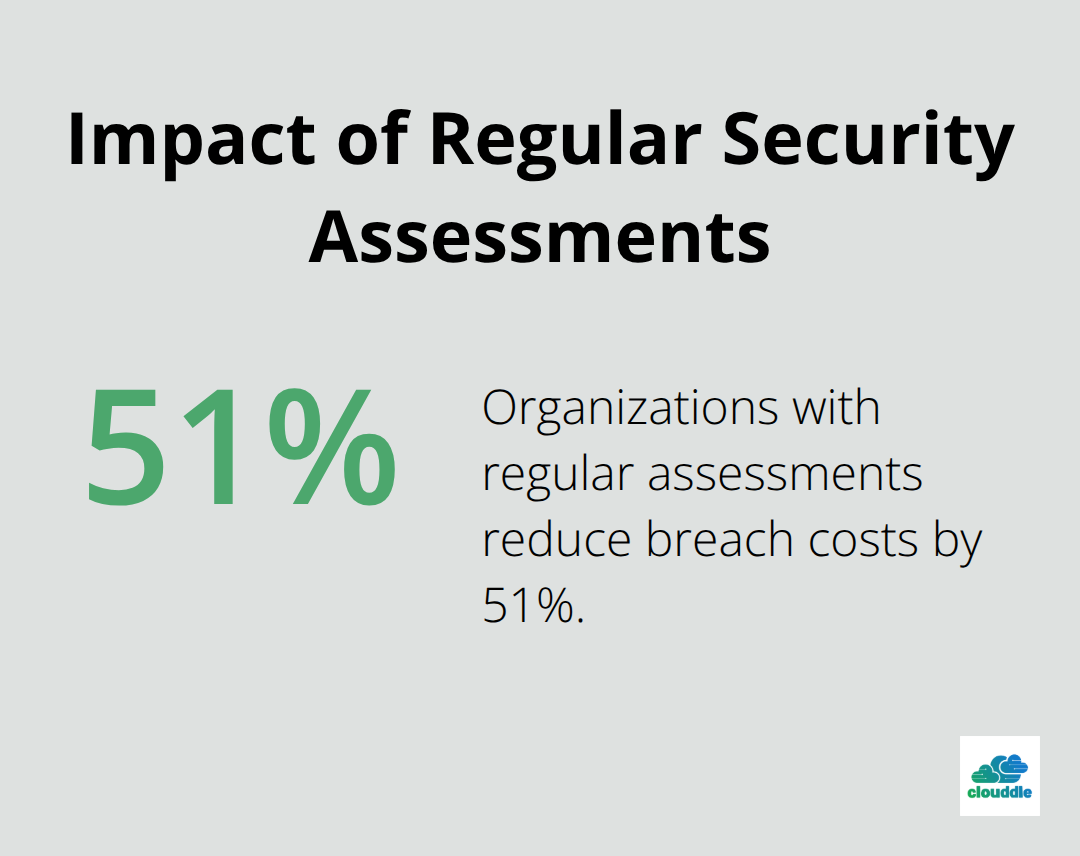
Network security risk assessment transforms reactive damage control into proactive threat prevention when you implement it systematically. Organizations that conduct regular assessments reduce breach costs by 51% compared to those with ad-hoc security practices. The structured approach we outlined identifies vulnerabilities before attackers exploit them and prioritizes remediation efforts based on actual business risk.
Your implementation timeline should begin with asset discovery within the first two weeks, followed by initial vulnerability scans in week three. Complete your first comprehensive risk assessment within 45 days, then establish quarterly review cycles for high-risk environments or annual assessments for stable networks. Document everything meticulously since compliance auditors require evidence of systematic risk management processes (track key metrics like mean time to patch critical vulnerabilities).
Continuous monitoring represents the evolution beyond periodic assessments through automated vulnerability scanners that provide real-time alerts when new threats emerge. Integrate threat intelligence feeds to understand current attack patterns that target your industry. We at Clouddle provide managed IT and security services with 24/7 monitoring capabilities that help organizations maintain robust risk assessment network security practices while supporting business growth objectives.


