Network security intrusions are a constant threat in our digital world. At Clouddle, we’ve seen firsthand how these attacks can cripple businesses and compromise sensitive data.
This blog post will guide you through the most common intrusion methods, essential detection tools, and best practices for safeguarding your network. By the end, you’ll have a solid foundation for implementing robust network security intrusion detection strategies.
Common Network Intrusion Tactics
Network security intrusions pose a constant threat in our digital landscape. These attacks can devastate businesses and compromise sensitive data. Let’s explore the most prevalent tactics cybercriminals use to breach network security.
Malware Infections
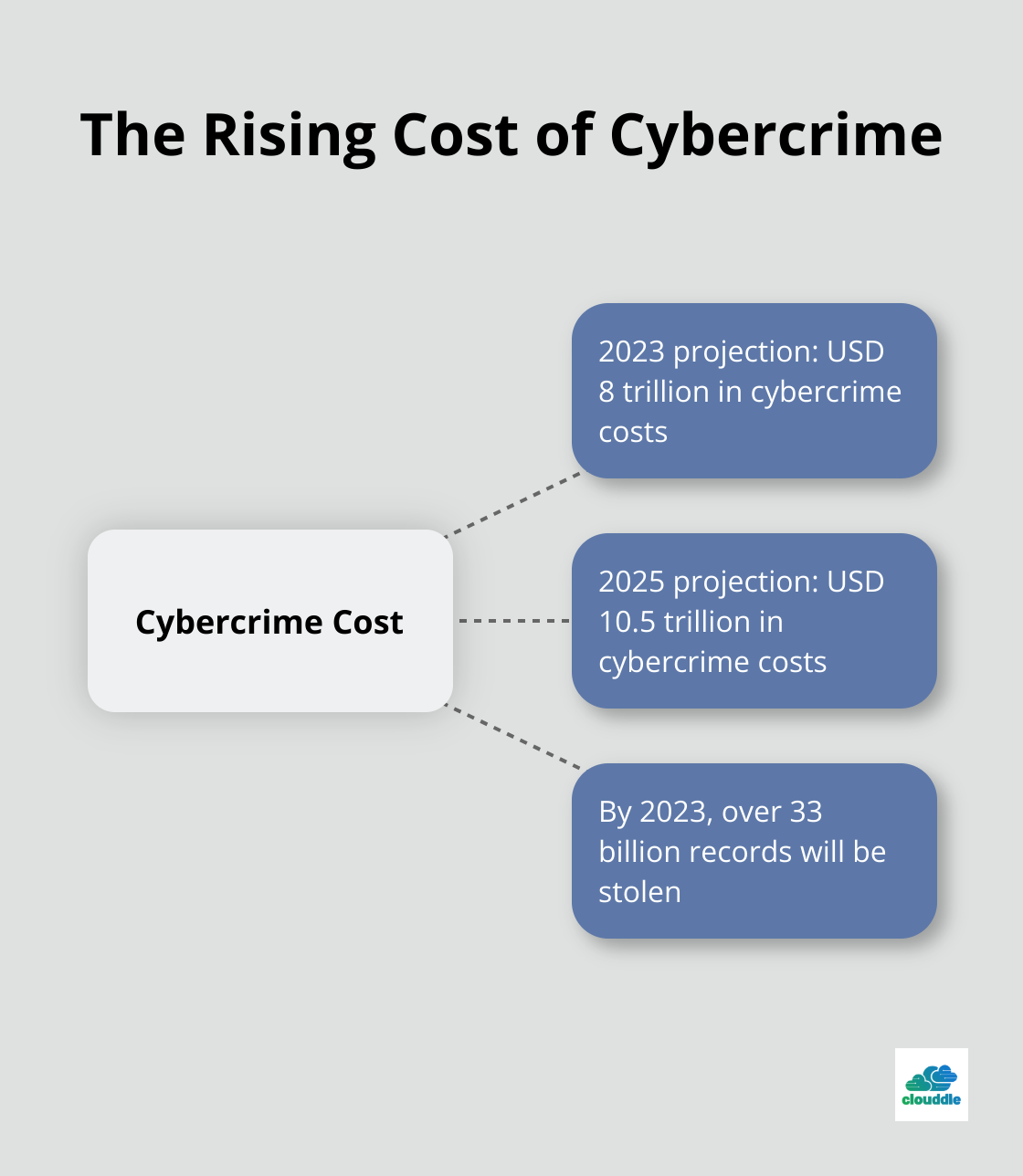
Malware continues to top the list of network security threats. The cost of cybercrime is expected to reach USD 8 trillion in 2023 and USD 10.5 trillion by 2025. By 2023, more than 33 billion records will be stolen, a 175% increase from previous years.
Ransomware, a particularly vicious form of malware, has become increasingly prevalent. These attacks encrypt valuable data and demand payment for its release, often paralyzing businesses in the process.
Social Engineering Scams
Phishing attacks continue to evolve in sophistication. The 2023 Verizon Data Breach Investigations Report revealed that 74% of breaches involved the human element, with many falling victim to social engineering tactics.
These attacks often disguise themselves as legitimate communications from trusted sources, deceiving users into revealing sensitive information or granting unauthorized access. Spear phishing, which targets specific individuals or organizations, proves particularly effective.
Network Overload Attacks
Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks aim to overwhelm network resources, rendering services inaccessible.
These attacks can cause significant downtime and financial losses.
Intercepting Network Traffic
Man-in-the-Middle (MitM) attacks involve intercepting communications between two parties, often to steal sensitive data or inject malicious content. While less common than other methods, these attacks can prove devastating when successful.
This underscores the importance of implementing strong encryption protocols and secure communication channels.
To combat these intrusion tactics effectively, organizations must adopt a multi-layered security approach. This includes implementing robust firewalls, regularly updating software, conducting security awareness training, and utilizing advanced threat detection tools. As we move forward, let’s examine the essential tools that can help detect and prevent these network security intrusions.
Essential Tools for Network Intrusion Detection
Network security requires a robust toolkit to detect and prevent intrusions effectively. This section explores the must-have tools for safeguarding your network against various threats.
Intrusion Detection Systems (IDS)
An Intrusion Detection System acts as your network’s vigilant guardian. It monitors traffic for suspicious activities and known threats, alerting your IT team to potential risks. A 2024 Global Cybersecurity Skills Gap Report revealed that 87% of organizations experienced at least one security breach in 2023, highlighting the importance of IDS implementation.
Two main types of IDS exist:
- Network-based IDS (NIDS): These systems analyze real-time data packets across your entire network.
- Host-based IDS (HIDS): These focus on individual devices, monitoring changes to files and user behavior.
For comprehensive protection, we recommend implementing both NIDS and HIDS. This hybrid approach provides a more thorough defense against various attack vectors.
Advanced Network Monitoring Software
While IDS focuses on threat detection, network monitoring software offers a broader view of your network’s health and performance. These tools help identify unusual traffic patterns or protocol violations that might indicate an intrusion.
Key features to look for include:

Efficient monitoring provides organizations with critical visibility into the network traffic to detect anomalies, signs of cyber attacks, or equipment failure.
Next-Generation Firewalls and Access Control
Traditional firewalls no longer suffice in today’s complex threat landscape. Next-generation firewalls (NGFW) combine traditional firewall capabilities with advanced features such as:
- Deep packet inspection
- Intrusion prevention
- Application awareness and control
- SSL/TLS inspection
Pair your NGFW with robust access control lists (ACLs) to restrict unauthorized access to sensitive network segments. The principle of least privilege should guide your ACL configuration, ensuring users only have access to the resources necessary for their roles.
Log Analysis and SIEM Tools
Log analysis plays a vital role in detecting and investigating security incidents. Security Information and Event Management (SIEM) tools centralize log data from various sources, applying analytics to identify potential threats.
When selecting a SIEM tool, prioritize features like:
- Real-time log collection and analysis
- Automated threat detection and alerting
- User and entity behavior analytics (UEBA)
- Integration with other security tools
Tools are only as effective as the people using them. Regular training and updates maximize the benefits of your security toolkit. The next section will explore best practices for implementing these tools and responding to potential intrusions, ensuring your network remains protected against evolving threats.
How to Implement Effective Network Intrusion Detection
Network intrusion detection requires a comprehensive approach that combines technology, processes, and people. Organizations can significantly improve their security posture by adopting these best practices.
Conduct Regular Security Audits
Security audits identify vulnerabilities before attackers can exploit them. Research from the Ponemon Institute indicates that 63% of organizations cannot confidently identify where all their sensitive data resides in their infrastructure. We recommend comprehensive audits at least quarterly, with more frequent checks for critical systems.
During these audits, focus on:
- Identifying outdated software and systems
- Reviewing access controls and user privileges
- Assessing network segmentation effectiveness
- Evaluating encryption protocols
Include third-party vendors in your audit scope.
Prioritize Employee Training
Human error remains a significant factor in security breaches. This statistic underscores the importance of comprehensive employee training programs.
Effective training should cover:
- Recognizing phishing attempts and social engineering tactics
- Proper handling of sensitive data
- Password hygiene and multi-factor authentication
- Reporting suspicious activities
Make training engaging and relevant by using real-world examples and simulations.
Develop a Robust Incident Response Plan
When a security incident occurs, every second counts. A well-crafted incident response plan can significantly reduce the impact of a breach.
Your incident response plan should include:
- Clear roles and responsibilities for team members
- Step-by-step procedures for containment and eradication
- Communication protocols for internal and external stakeholders
- Regular tabletop exercises to test and refine the plan
Update your plan regularly to account for new threats and changes in your IT environment.
Implement Continuous Monitoring
Traditional periodic scanning is no longer sufficient in today’s rapidly evolving threat landscape. Continuous monitoring allows for real-time detection and response to potential intrusions. According to a 2023 Gartner report, organizations that implement continuous monitoring can reduce incident response times by up to 70%.
Key components of an effective continuous monitoring strategy include:
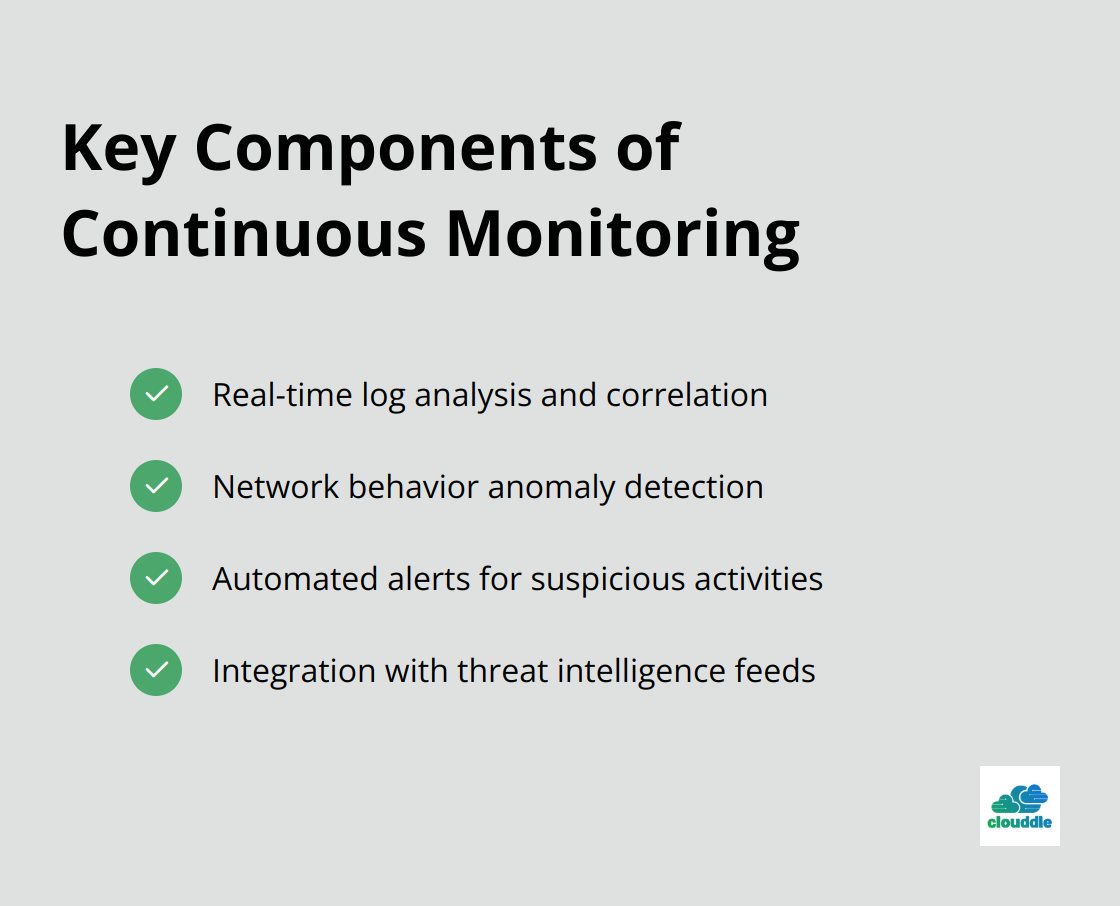
When implementing continuous monitoring, fine-tune alert thresholds to minimize false positives while ensuring critical events aren’t missed. This balance is essential for maintaining the effectiveness of your security team and avoiding alert fatigue.
Final Thoughts
Cyber threats evolve rapidly, making proactive network security intrusion detection essential for all organizations. A multi-layered approach combines advanced tools like IDS and SIEM solutions with regular security audits and comprehensive employee training. We expect AI and Machine Learning to play an increasingly significant role in threat detection, enabling faster and more accurate identification of potential intrusions.
Cloud-native security solutions will provide greater flexibility for organizations managing complex networks. Automation in security operations will help teams cope with the increasing volume of threats and alerts. These advancements will empower businesses to stay ahead of cyber threats in an increasingly connected world.
We at Clouddle understand the importance of robust network security in today’s digital landscape. Our managed IT and security services provide comprehensive protection against network intrusions. We empower organizations to focus on growth and innovation without compromising security (leveraging cutting-edge technology and industry expertise).


