In today’s digital landscape, the importance of computer network security cannot be overstated. Cyber threats are evolving rapidly, putting businesses and individuals at constant risk of data breaches and financial losses.
At Clouddle, we’ve seen firsthand how robust security measures can protect organizations from devastating attacks. This guide will equip you with practical strategies to fortify your network defenses and stay ahead of cybercriminals.
What Are the Biggest Network Security Threats?
Network security threats continue to evolve, posing significant risks to businesses across various industries. Understanding these threats is essential for protecting your network effectively.
The Ransomware Epidemic
Ransomware attacks have become more prevalent and sophisticated. In 2021, these attacks cost US businesses $159 billion, with average payment demands reaching $7.9 billion. Alarmingly, 24% of organizations that paid ransom failed to recover their data. These statistics underscore the need for robust backup solutions and comprehensive security measures.
Phishing: A Persistent Menace
Phishing remains one of the most common and effective attack vectors. On average, phishing incidents cost companies $14.8 million. These attacks often serve as gateways for more severe breaches, allowing attackers to gain initial access to networks. Employee training plays a critical role in combating this threat, as human error accounts for approximately 95% of cybersecurity breaches.

Exploiting Network Vulnerabilities
Unpatched software and outdated systems are prime targets for cybercriminals. An 87% increase in malware infections has been reported over the last decade, highlighting the importance of regular updates and patch management. Zero-day exploits (which target newly discovered vulnerabilities before patches are available) pose a significant risk to organizations that don’t prioritize swift updates.
The Impact on Businesses
The consequences of these threats on businesses extend beyond financial losses. Companies face reputational damage, loss of customer trust, and potential legal ramifications. For industries like hospitality and senior living, a security breach can lead to severe service disruptions and compromise sensitive customer data.
Mitigating the Risks
To combat these risks, organizations must adopt a proactive approach to network security. This includes:
- Implementing robust firewalls
- Utilizing intrusion detection systems
- Employing advanced encryption protocols
- Conducting regular security audits and vulnerability assessments
A layered security approach (combining technology solutions with employee education and strong policies) proves most effective in safeguarding networks against these evolving threats. Organizations that stay informed about the latest security trends and implement comprehensive protection measures significantly reduce their risk of falling victim to network attacks.
As we move forward, it’s clear that implementing essential network security measures is the next crucial step in fortifying your defenses. Let’s explore the fundamental strategies that form the backbone of a robust security posture.
How to Build a Strong Network Security Foundation
Fortify Your Network Perimeter
Start by implementing a next-generation firewall (NGFW) and intrusion detection system (IDS). NGFWs offer more than traditional packet filtering; they provide application-level inspection and integrated intrusion prevention. Gartner predicts that by 2023, 60% of enterprises will replace their standalone IDS with NGFWs or network detection and response (NDR) solutions. This trend underscores the value of comprehensive, integrated security solutions.
When you configure your firewall, adopt a default-deny stance. Block all traffic except what you explicitly allow. This approach provides more security than attempting to block known threats, as new attack vectors constantly emerge.
Strengthen Access Controls
Implement a robust password policy across your organization. The National Institute of Standards and Technology (NIST) recommends passphrases of at least 15 characters. Avoid common words and require a mix of uppercase, lowercase, numbers, and symbols.
Multi-factor authentication (MFA) is essential. A Microsoft study found that MFA blocks 99.9% of automated attacks. Apply MFA to all user accounts, especially those with administrative privileges. For industries handling sensitive data (like senior living facilities), consider biometric authentication methods for enhanced security.
Keep Your Systems Up-to-Date
Regular software updates and patch management play a critical role in network security. 60% of breaches were linked to a vulnerability where a patch was available, but not applied. Establish a rigorous patch management process:
- Create an inventory of all software and systems
- Prioritize critical updates
- Test patches in a non-production environment
- Deploy updates during off-peak hours
- Verify successful installation
Large networks can benefit from automated patch management tools to streamline this process.
Empower Your Employees
Your staff can serve as your strongest defense or your weakest link. Implement comprehensive security awareness training programs. The SANS Institute recommends focusing on these key areas:
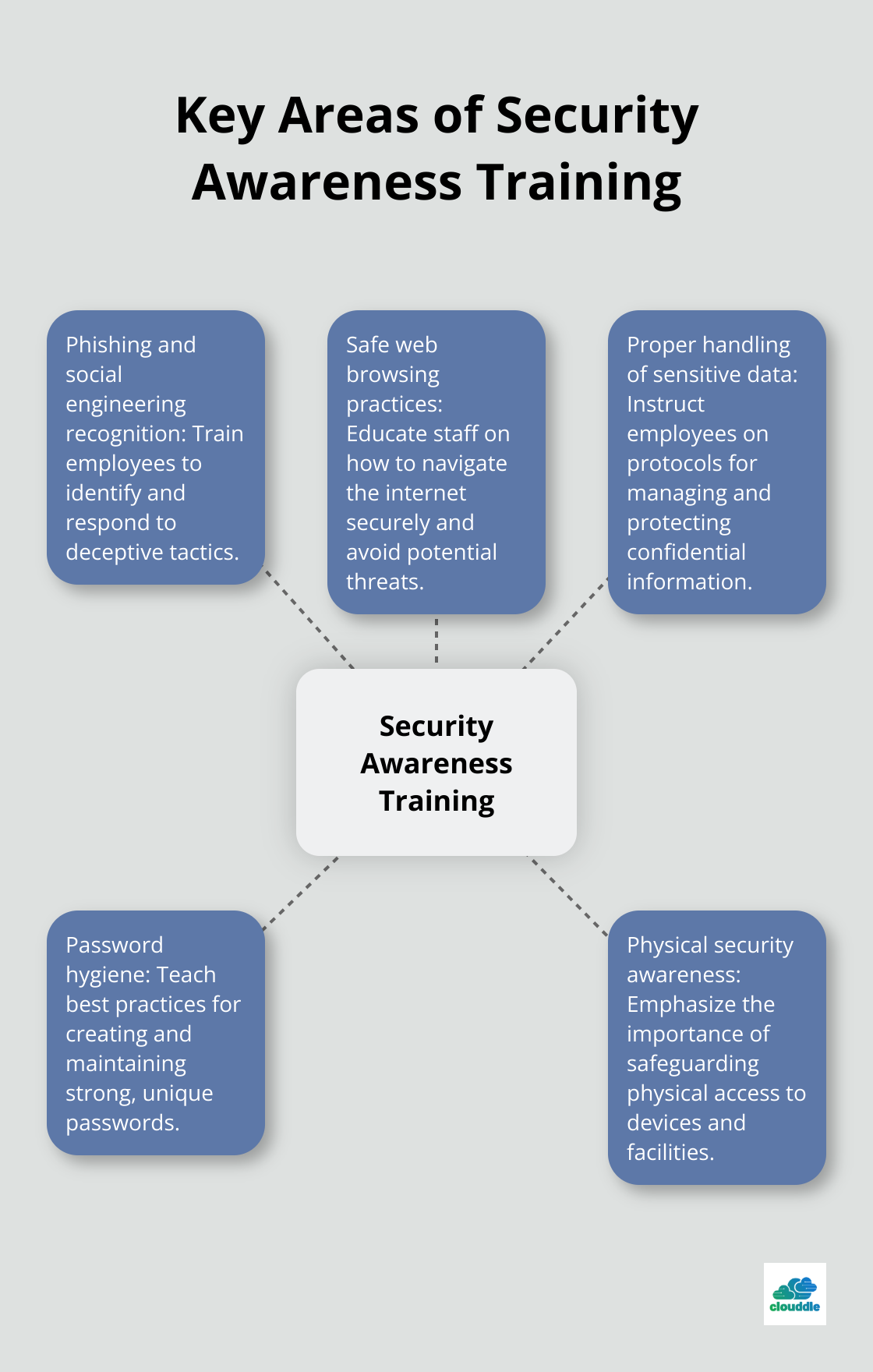
Create engaging and relevant training. Use real-world examples and conduct simulated phishing exercises to test and reinforce learning. Provide regular refresher courses to keep up with rapidly evolving cyber threats.
Network security requires ongoing attention and adaptation. Regular assessments of your security posture, penetration testing, and staying informed about emerging threats will help you maintain a robust defense. These essential measures form the foundation of a strong security strategy, but advanced techniques can further enhance your protection. Let’s explore some sophisticated strategies to take your network security to new heights.
How to Implement Advanced Network Security Strategies
Segment Your Network for Enhanced Protection
Network segmentation creates a robust defense against sophisticated threats. This strategy divides your network into smaller, isolated segments to restrict access to sensitive data and critical systems.
Network segmentation offers several benefits, including enhanced data security, improved breach containment, greater compliance, reduced attack surface, and increased network performance.
Implement Virtual Local Area Networks (VLANs) to create logical separations within your physical network. For instance, separate guest Wi-Fi from your internal network, or isolate IoT devices from critical business systems. This segmentation reduces the attack surface and complicates an attacker’s ability to move freely within your network.
Encrypt Data in Transit and at Rest
Strong encryption protocols protect both data in transit and at rest. The National Institute of Standards and Technology (NIST) recommends AES-256 for symmetric encryption and RSA-3072 or higher for asymmetric encryption.
For data in transit, use TLS 1.3, which offers improved security and performance over its predecessors. Enable HTTPS across all web applications and services. For data at rest, employ full-disk encryption on all devices, especially mobile ones prone to theft or loss.
Implement a data classification system to ensure appropriate encryption levels for different types of information. This approach allows you to apply stronger encryption to your most sensitive data while balancing performance and usability for less critical information.
Monitor and Analyze Logs Continuously
Continuous monitoring and log analysis detect and respond to security incidents quickly. IBM’s Cost of a Data Breach Report 2021 revealed that organizations using security AI and automation experienced on average $3.81 million less in breach costs compared to those that did not.
Implement a Security Information and Event Management (SIEM) system to centralize log collection and analysis. Configure the SIEM system to align with the organization’s security policies and objectives. This involves setting up log collection, defining correlation rules, and establishing alert mechanisms.
Use User and Entity Behavior Analytics (UEBA) to establish baseline behavior patterns and identify anomalies that may indicate a compromise. This approach can help detect insider threats and sophisticated attacks that might evade traditional signature-based detection methods.
Create a Comprehensive Incident Response Plan
A well-prepared incident response plan reduces the impact and cost of a security incident. The SANS Institute recommends these key steps in your incident response plan:
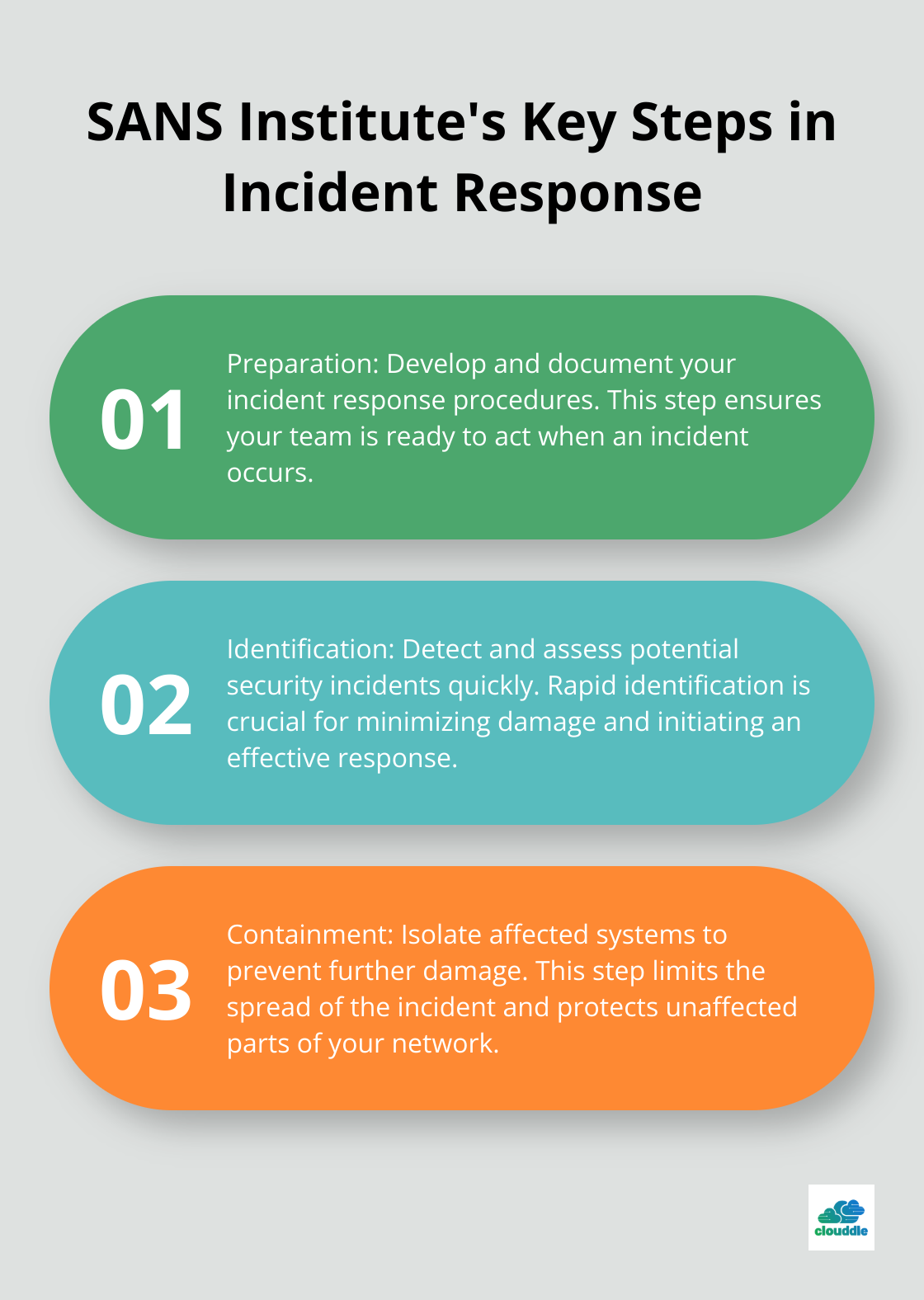
Test and update your incident response plan regularly through tabletop exercises and simulated attacks. This practice ensures your team acts swiftly and effectively when a real incident occurs.
Incorporate disaster recovery planning into your overall security strategy. Maintain offsite backups and establish clear procedures for restoring critical systems and data. Test your disaster recovery plan at least annually to identify and address any gaps or inefficiencies.
Final Thoughts
The importance of computer network security cannot be overstated in today’s digital landscape. Cyber threats evolve rapidly, putting businesses and individuals at constant risk of data breaches and financial losses. Organizations must adopt a proactive approach to network security, implementing robust firewalls, intrusion detection systems, and advanced encryption protocols.
Artificial intelligence and machine learning will play an increasingly significant role in threat detection and response. The rise of edge computing and 5G networks will introduce new security challenges, requiring adaptive and scalable solutions. Zero Trust architectures will become more prevalent, moving away from traditional perimeter-based security models to a more granular, identity-based approach.
We at Clouddle understand the critical nature of network security for businesses across various industries. Our Network as a Service (NaaS) solutions combine cutting-edge networking, entertainment, and security features to provide a comprehensive experience for our clients. Organizations should stay informed about emerging threats, regularly assess their security posture, and seek expert guidance when needed (such as from Clouddle).


