Industrial network security is no longer a luxury-it’s a necessity. In today’s interconnected world, the risks to industrial systems have grown exponentially, threatening not just data but also physical infrastructure and human safety.
At Clouddle, we’ve seen firsthand how proper security measures can make or break an industrial operation. This post will guide you through the essential steps to fortify your industrial networks against evolving threats.
What Are the Biggest Industrial Network Security Risks?
Industrial network security risks have multiplied in recent years. Attacks targeting industrial control systems (ICS) and operational technology (OT) networks have surged. These threats now extend beyond data theft, posing risks to physical infrastructure and human safety.
Outdated Systems and Unpatched Vulnerabilities
One of the most prevalent vulnerabilities is outdated systems. Many industrial networks continue to operate on legacy software and hardware that haven’t received updates in years. These systems often harbor known vulnerabilities that hackers can exploit with ease. In 2022, reconnaissance attacks targeting the Modbus/TCP port 502 (a protocol commonly used in industrial settings) increased by 2,000%.

Lack of Network Segmentation
Poor network segmentation presents another major risk. Industrial networks are often flat, allowing attackers who gain access to one part of the network to move freely to other areas. This absence of segmentation can transform a minor breach into a catastrophic event.
Insufficient Access Controls
Weak access controls constitute a significant vulnerability. Many industrial networks still use default passwords or share login credentials among multiple users, making unauthorized access easy for attackers. A recent study revealed that 77% of government and public sector organizations lack complete visibility over their IoT devices, underscoring the need for improved access management.
The consequences of these vulnerabilities can be severe. In 2021, a cyberattack on a Florida water treatment plant nearly poisoned the water supply. The attacker gained access through an outdated Windows 7 computer and unsecured remote access software.
Emerging Threats in the Industrial Sector
New threats continue to surface. AI-powered attacks that can learn and adapt to defense mechanisms are on the rise. These attacks can employ machine learning algorithms to identify system vulnerabilities, predict security responses, and adapt in real-time to circumvent defenses.
Ransomware attacks have evolved as well. They no longer just encrypt data – they now threaten to leak sensitive information if ransoms remain unpaid. This double extortion tactic poses particular danger for industrial networks that often contain proprietary information and critical infrastructure data.
The U.S. government has identified a malware strain called Pipedream, specifically designed to disrupt ICS systems. This discovery highlights the increasing sophistication of threats targeting industrial networks.
To combat these risks, industrial organizations must implement a multi-layered security approach. This approach should include regular security audits, employee training, and advanced threat detection systems.
The next section will explore best practices for industrial network security, providing actionable strategies to protect your systems from these evolving threats.
How to Fortify Your Industrial Network
Industrial network security requires a proactive, multi-layered approach. Let’s explore proven strategies to enhance your industrial network security.
Segment Your Network
Network segmentation serves as your first line of defense. Divide your network into smaller, isolated segments to limit potential damage from a breach. Separate your operational technology (OT) network from your information technology (IT) network to prevent attackers from moving laterally if they compromise one segment.
Implement virtual local area networks (VLANs) to create logical separations within your physical network. Use firewalls between segments to control traffic flow. This approach reduces the attack surface and contains potential breaches.
Conduct Regular Security Audits
Security is an ongoing process. Regular security audits help identify vulnerabilities before attackers can exploit them. Try to schedule quarterly audits at minimum, with more frequent checks for critical systems.
Use automated vulnerability scanning tools to identify known weaknesses in your network. Don’t rely solely on automation. Engage professional penetration testers annually to simulate real-world attacks and uncover hidden vulnerabilities.
Train Your Employees
Your employees can serve as a human firewall against cyber threats. Implement a comprehensive security awareness program that covers:

Make training engaging and relevant. Use real-world examples and simulations to emphasize the importance of security. Consider gamification elements to increase participation and retention.
Secure Remote Access
The rise of remote work has made securing access points more critical than ever. Implement a zero-trust architecture for remote access. This model requires verification of every user and device, ensuring trusted access in today’s evolving IT environments.
Use multi-factor authentication (MFA) for all remote logins. Deploy virtual private networks (VPNs) with strong encryption for secure communication. Consider implementing jump servers or privileged access workstations for administrative access to critical systems.
Monitor remote access logs closely. Set up alerts for unusual access patterns or attempts from unexpected locations. This vigilance allows you to quickly detect and respond to potential breaches.
These strategies significantly enhance your industrial network security posture. However, the landscape of cybersecurity is ever-evolving. The next section will explore advanced technologies that can take your industrial network protection to new heights.
How Advanced Tech Boosts Your Industrial Network Security
Industrial network security evolves rapidly, and staying ahead of threats requires cutting-edge solutions. Let’s explore some game-changing tech that can fortify your industrial networks.
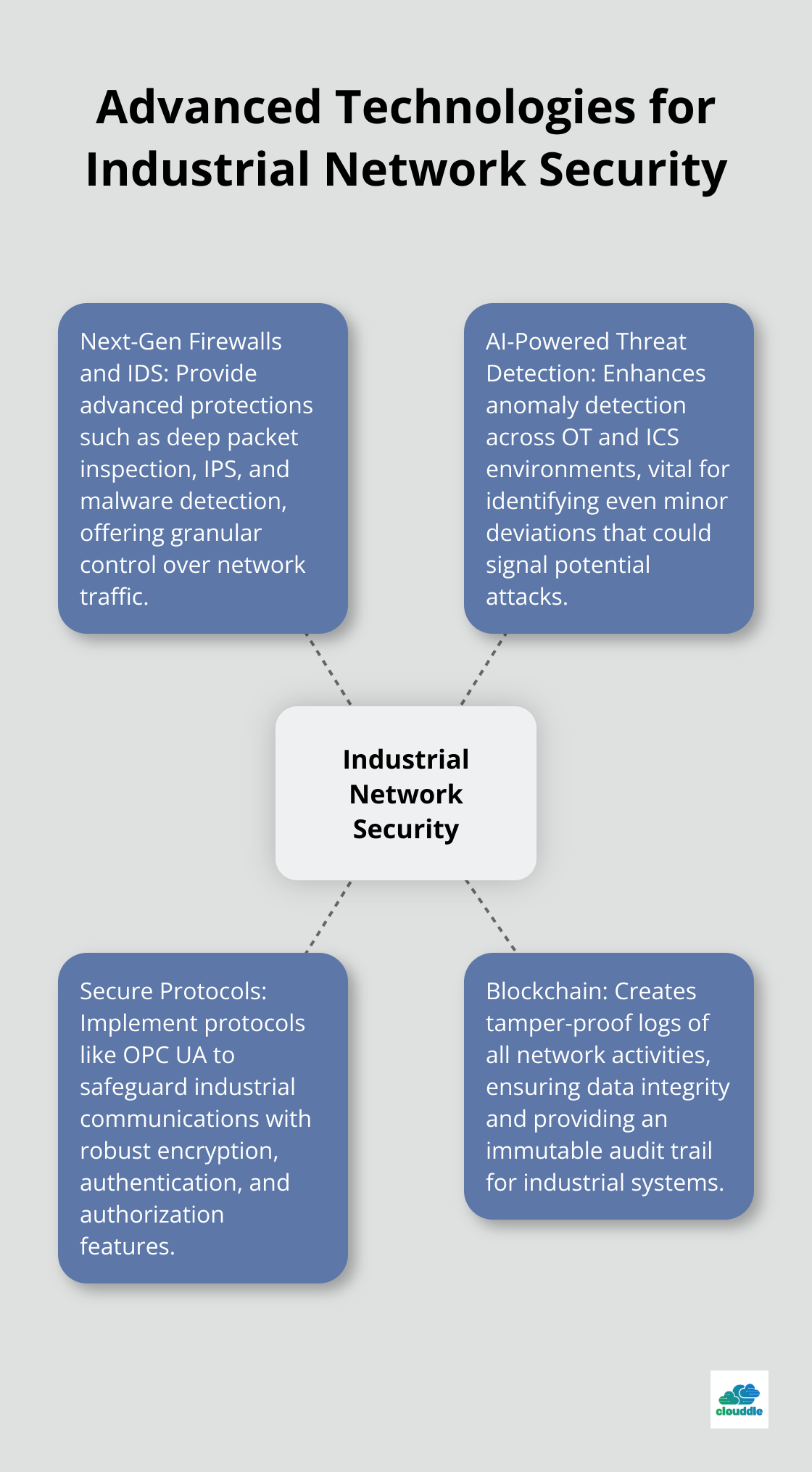
Next-Gen Firewalls and IDS: Your First Line of Defense
Traditional firewalls no longer suffice in today’s threat landscape. Next-generation firewalls (NGFWs) offer advanced protections such as deep packet inspection, IPS, and malware detection, surpassing traditional firewalls. These features provide granular control over network traffic and can detect sophisticated attacks that might slip past conventional defenses.
When combined with advanced intrusion detection systems (IDS), these solutions identify and neutralize threats in real-time.
AI-Powered Threat Detection: Staying One Step Ahead
Artificial Intelligence (AI) revolutionizes threat detection and response. AI-powered security platforms enhance anomaly detection across OT (operational technology) and ICS (industrial control systems) environments. This capability proves vital in industrial settings where even minor deviations can signal a potential attack.
Secure Protocols: Safeguarding Industrial Communications
Industrial control systems often rely on legacy protocols that weren’t designed with security in mind. Implementing secure communication protocols is essential for protecting sensitive data and control signals.
The OPC UA (Open Platform Communications Unified Architecture) protocol gains traction in industrial settings. It offers robust encryption, authentication, and authorization features.
Blockchain: Ensuring Data Integrity
While blockchain is often associated with cryptocurrencies, its potential for enhancing industrial network security is significant. Blockchain creates tamper-proof logs of all network activities, ensuring data integrity and providing an immutable audit trail.
Implementing these advanced technologies requires expertise and careful planning. Try to integrate cutting-edge security solutions into existing industrial networks (this often involves assessing your current security posture and implementing the right mix of advanced technologies to protect your critical infrastructure).
Technology alone isn’t a silver bullet. These advanced solutions should be part of a comprehensive security strategy that includes employee training, regular audits, and robust incident response plans.
Final Thoughts
Industrial network security demands immediate attention and ongoing vigilance. The risks to industrial systems are multifaceted and ever-evolving, with potential consequences extending beyond data breaches to physical infrastructure damage and human safety risks. A multi-layered approach is essential to combat these threats, including network segmentation, regular security audits, and employee training programs.
Advanced technologies play a pivotal role in fortifying industrial networks. Next-generation firewalls, AI-powered threat detection systems, and secure communication protocols contribute to a robust security posture. These cutting-edge solutions, when properly implemented, can significantly enhance an organization’s ability to detect, prevent, and respond to cyber threats.
Clouddle understands the complexities of securing industrial networks in today’s digital landscape. Our Network as a Service (NaaS) solution combines networking, entertainment, and security, providing a comprehensive approach to industrial network protection. Organizations that prioritize and invest in robust security measures today will be better positioned to face the challenges of tomorrow (ensuring the integrity and resilience of their industrial networks in an increasingly connected world).


