Network hardware security is often overlooked, yet it’s a critical component of a robust cybersecurity strategy. At Clouddle, we’ve seen firsthand how vulnerable networks can be when hardware security is neglected.
In this post, we’ll explore common hardware vulnerabilities and share best practices to fortify your network’s physical defenses. We’ll also delve into advanced security measures that can provide an extra layer of protection against sophisticated threats.
What Are the Biggest Network Hardware Vulnerabilities?
Network hardware vulnerabilities pose a significant threat to businesses of all sizes. The past few years have witnessed an alarming increase in hardware-based attacks, which can be particularly devastating due to their often long-undetected nature.
Supply Chain Attacks
Supply chain attacks represent one of the most common types of hardware attacks. In 2018, Bloomberg reported a controversial story about Chinese spies allegedly inserting malicious chips into Supermicro server motherboards (potentially affecting major tech companies and government agencies). While disputed, this report highlighted the very real threat of supply chain compromises.
Rogue Devices
The use of rogue devices presents another prevalent threat. Attackers can exploit small, malicious devices plugged into network ports to gain unauthorized access. A security researcher demonstrated in 2019 how a $5 Raspberry Pi could breach a major corporation’s network in just 30 seconds, underscoring the severity of this vulnerability.
Firmware Vulnerabilities
Firmware vulnerabilities often directly involve the firmware of networking devices and have quickly been exploited by attackers after discovery. These flaws could allow attackers to bypass security controls and gain deep, persistent access to affected systems.
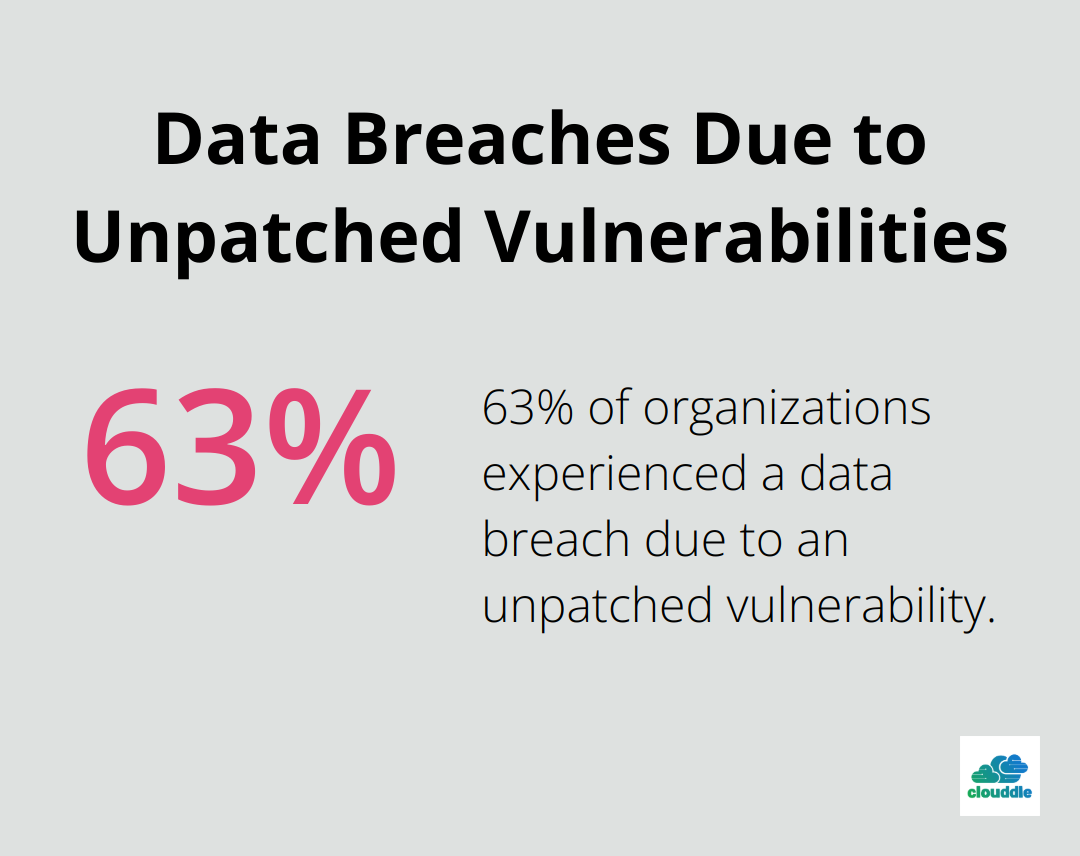
Outdated software and firmware presents another significant risk. A 2019 Forrester study revealed that 63% of organizations had experienced a data breach due to a vulnerability for which a patch was available but not applied.
Physical Security Risks
Physical security often emerges as the weakest link in network hardware protection. The U.S. Government Accountability Office (GAO) reported in 2018 that physical security weaknesses in federal facilities put sensitive data at risk. They discovered unlocked server rooms, unattended laptops, and other physical security lapses that could lead to data breaches or hardware tampering.
Even small oversights can result in major consequences. In 2017, a major airline’s flights were grounded for hours because a contractor accidentally cut a cable in a data center. This incident emphasizes the importance of strict physical access controls and proper change management procedures.
Organizations need a comprehensive approach to network hardware security to mitigate these risks. This approach should include rigorous supply chain management, regular firmware updates, and robust physical security measures. The next section will explore best practices for implementing these essential safeguards, providing you with actionable steps to enhance your network’s hardware security posture.
How to Fortify Your Network Hardware
Network hardware security requires a proactive approach. We’ve identified key strategies that reduce vulnerabilities and strengthen your network’s defenses.
Update Firmware Regularly
Keeping your network hardware’s firmware up-to-date is essential. Firmware attacks are a growing concern, with trends such as unaddressed vulnerabilities, unprotected data, endpoint complexity, and failing security controls contributing to the risk. To combat this:
- Establish a regular update schedule
- Use automated update services offered by vendors
- Test updates in a sandbox environment for critical infrastructure before deployment
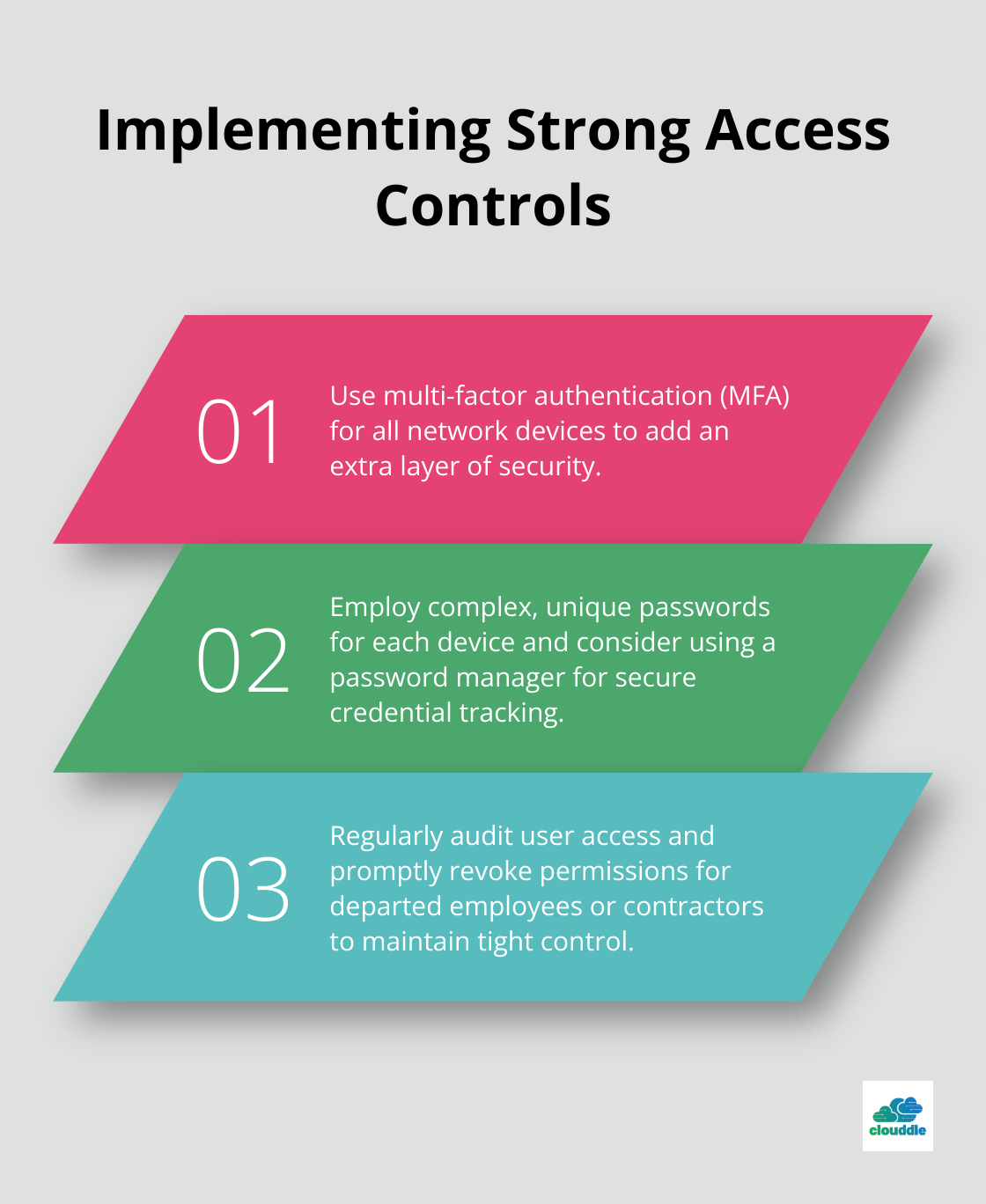
Implement Strong Access Controls
Strong access controls serve as your first line of defense. The 2019 Verizon Data Breach Investigations Report revealed that 29% of breaches involved the use of stolen credentials. To mitigate this risk:
Enhance Physical Security
Physical security often gets overlooked, but it’s vital. The Ponemon Institute’s 2019 study on data center security found that 60% of organizations had experienced at least one security incident due to a lack of physical security controls. To improve physical security:
- Install surveillance cameras
- Implement strict access policies for server rooms and network closets
- Use biometric access controls where possible
- Maintain detailed logs of all physical access to network hardware
Leverage Network Segmentation
Network segmentation limits the spread of potential breaches. Gartner reports that by 2023, 60% of enterprises will phase out most of their remote access virtual private networks (VPNs) in favor of zero trust network access. To implement effective segmentation:
- Use VLANs to isolate different parts of your network
- Deploy firewalls between segments to control traffic flow
- Contain breaches and make it harder for attackers to move laterally within your network
These practices significantly enhance your network hardware security. However, the landscape of network security continues to evolve rapidly. In the next section, we’ll explore advanced security measures that provide an extra layer of protection against sophisticated threats.
Advanced Hardware Security Techniques
Network hardware security requires more than basic measures. Organizations must adopt advanced security techniques to counter sophisticated attacks targeting hardware vulnerabilities.
Hardware-Based Authentication
Traditional software-based authentication methods face increasing vulnerability to attacks. Hardware-based authentication offers a more robust solution. By implementing FIDO authentication, various industries can achieve higher security standards, improve user experience, and ensure compliance.
Hardware security keys provide an effective method. These small USB devices generate one-time passwords for each login attempt. Google implemented hardware keys for its 85,000+ employees in 2017 and reported zero successful phishing attacks since then.
Biometric authentication built into hardware devices offers another option. Fingerprint sensors and facial recognition systems integrated into laptops and smartphones provide a secure and convenient way to authenticate users.
Trusted Platform Modules
Trusted Platform Modules (TPMs) are specialized chips that provide hardware-based security functions. The Trusted Computing Group has developed several technologies that can be used to implement cryptographic device identity and attestation.
TPMs offer several security benefits:
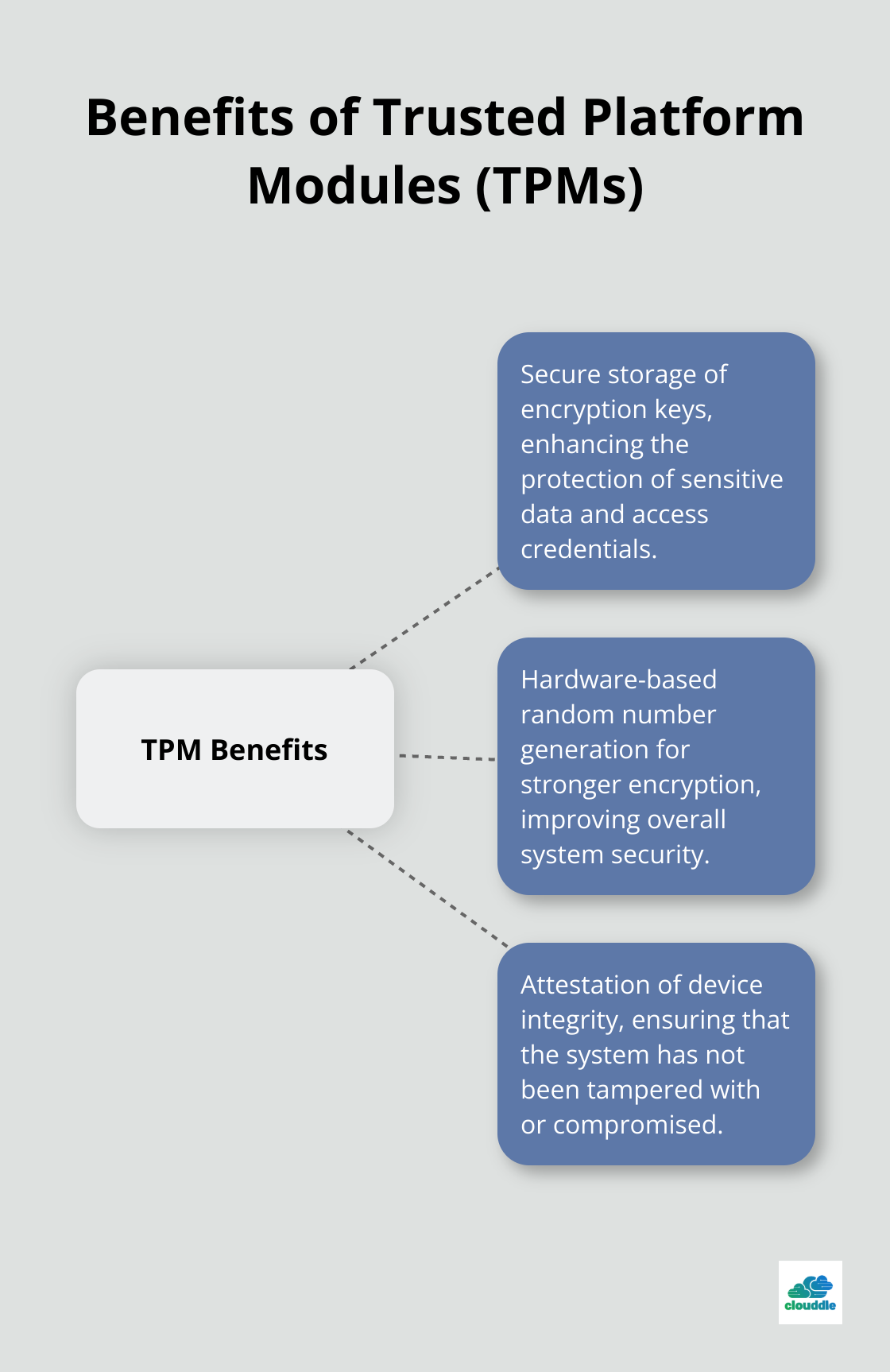
Microsoft requires TPMs for Windows 11, which highlights their growing importance in system security.
Secure Boot and Hardware Root of Trust
Secure boot verifies the digital signature of each piece of boot software, firmware, and the operating system before allowing execution. This process ensures that only trusted software runs during the boot process.
Hardware root of trust anchors the trust in hardware components. This creates an unbroken chain of trust from the hardware to the operating system.
Intel’s Boot Guard technology uses a hardware root of trust to prevent malicious BIOS modifications. AMD offers similar protection with its Hardware-Validated Boot technology.
Hardware-Level Encryption
Hardware-level encryption provides stronger protection for data at rest compared to software-based encryption. It offloads encryption tasks to dedicated hardware, which improves performance and security.
Self-encrypting drives (SEDs) exemplify hardware-level encryption. These drives automatically encrypt all data written to them, which makes data recovery nearly impossible without the encryption key.
Implementation of these advanced hardware security measures requires careful planning and expertise. They offer powerful protection but also introduce complexity. Organizations should conduct a thorough risk assessment and consult with security experts before deployment.
Final Thoughts
Network hardware security requires a comprehensive approach to protect against diverse and evolving threats. Organizations must implement best practices and advanced techniques to safeguard their infrastructure effectively. The challenge lies in balancing robust security measures with system performance and user experience.
We expect future trends in network hardware security to include quantum-resistant encryption, AI-driven threat detection, and new strategies for securing IoT devices. These advancements will shape the landscape of network protection in the coming years. Organizations need to stay informed and adapt their security strategies accordingly.
At Clouddle, we offer managed IT and security services to help businesses navigate the complexities of network hardware security. Our solutions aim to provide strong protection without compromising performance or usability. We encourage organizations to take a proactive stance in securing their network infrastructure against current and future threats.


