In today’s digital landscape, network security is paramount. Intrusion Prevention Systems (IPS) have become a critical component in safeguarding networks against evolving threats.
At Clouddle, we’ve seen firsthand how Network Security IPS can significantly reduce the risk of successful cyberattacks. This post will guide you through the essentials of IPS, its key features, and best practices for implementation.
What is an Intrusion Prevention System?
The Core Function of IPS
An Intrusion Prevention System (IPS) monitors network traffic for potential threats and automatically blocks them by alerting the security team. This powerful network security tool analyzes network traffic patterns and compares them against a database of known threats. When it detects suspicious activity, it automatically takes action to prevent potential attacks.
The proactive approach of IPS sets it apart from its predecessor, the Intrusion Detection System (IDS). While an IDS only alerts administrators to potential threats, an IPS actively blocks malicious traffic. This key difference can determine whether an attack succeeds or fails.
Types of IPS Solutions
Three main types of IPS solutions protect different aspects of your network:
- Network-based IPS (NIPS): These systems monitor traffic across the entire network, typically deployed at key network entry points.
- Host-based IPS (HIPS): Installed on individual devices, HIPS protects specific endpoints from threats.
- Wireless IPS (WIPS): Designed to safeguard wireless networks, WIPS monitors for unauthorized access and potential attacks on Wi-Fi systems.
Practical Benefits of IPS Implementation
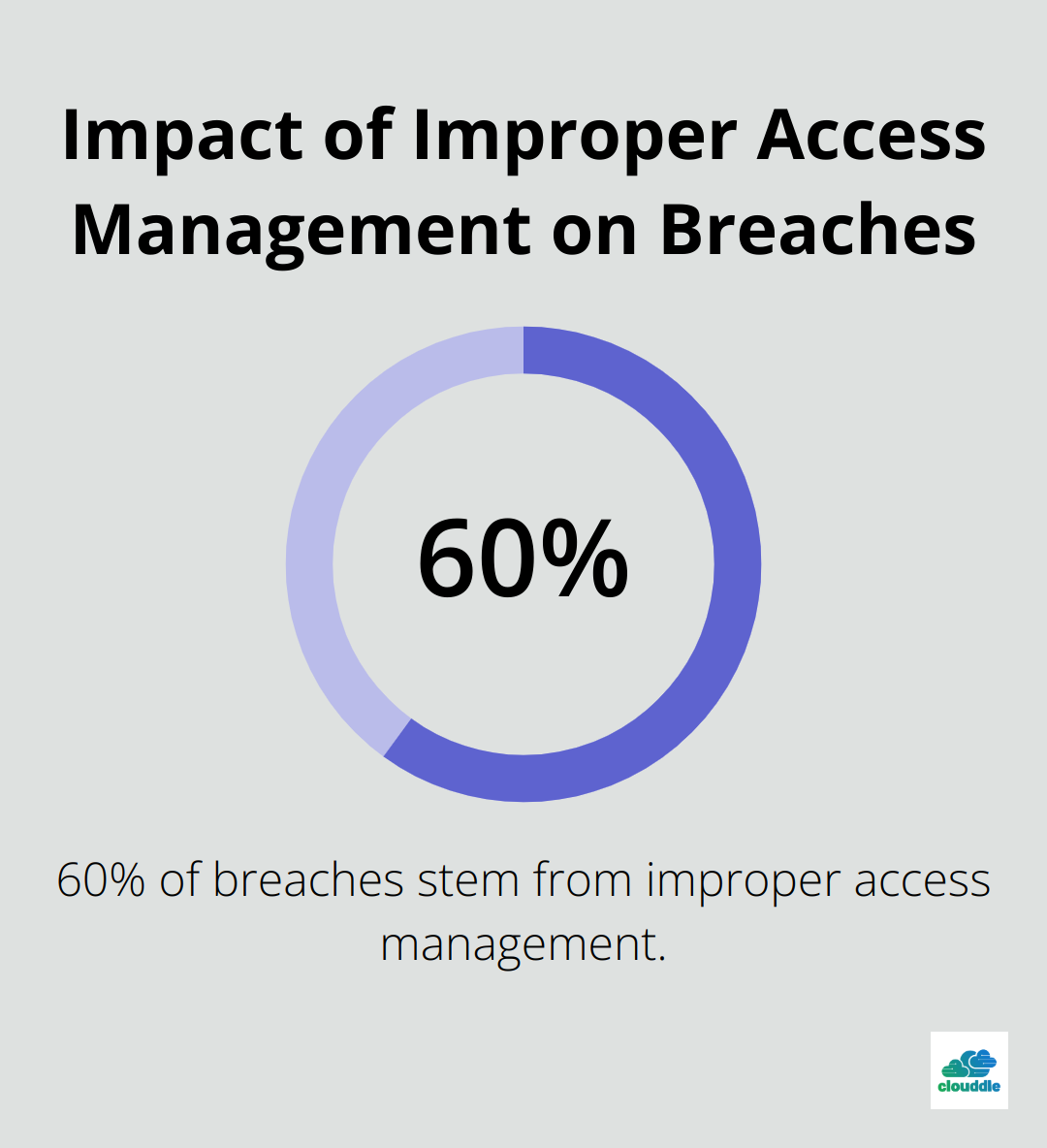
Implementing an IPS can significantly enhance your network security posture. A survey by Cybersecurity Ventures indicates that 60% of breaches stem from improper access management.
The automated response capabilities of IPS can save valuable time for IT teams.
Selecting the Right IPS for Your Organization
When choosing an IPS solution, consider factors such as network size, industry-specific regulations, and integration capabilities with existing security tools. For instance, a healthcare provider might prioritize an IPS with strong HIPAA compliance features, while a financial institution might focus on solutions with advanced fraud detection capabilities.
A thorough network assessment before implementing an IPS helps identify potential vulnerabilities and ensures that the chosen IPS solution aligns with your specific security needs.
The Role of IPS in Modern Cybersecurity
As cyber threats continue to evolve, IPS technology adapts to meet new challenges. Modern IDS solutions use machine learning algorithms to detect and respond to previously unknown threats (also known as zero-day attacks). This adaptive capability makes IPS an essential component of a comprehensive cybersecurity strategy.
The integration of IPS with other security tools (such as firewalls and SIEM systems) creates a more robust defense against sophisticated cyber attacks. This multi-layered approach provides organizations with a more comprehensive view of their security posture and enables faster, more effective responses to potential threats.
What Makes IPS a Game-Changer for Network Security?
Real-Time Threat Detection and Prevention
Intrusion Prevention Systems (IPS) have revolutionized network security with their advanced capabilities. IPS solutions help filter out malicious activity before it reaches other security devices or controls. This reduces the manual effort of security teams.
Consider a scenario where a zero-day exploit attempts to infiltrate your network. An IPS can instantly recognize the unusual behavior and block the attack before it causes any damage. This proactive approach significantly reduces the risk of successful breaches.
Automated Incident Response
One of the most powerful features of IPS is its ability to automate responses to security incidents. This automation not only speeds up reaction times but also reduces the workload on security teams.
A survey by ESG Research found that organizations using automated IPS responses saw a 60% reduction in the time spent on manual threat investigation. This frees up valuable resources, allowing security professionals to focus on more strategic tasks.

Tailored Security Policies
Modern IPS solutions offer highly customizable rules and policies. This flexibility allows organizations to fine-tune their security measures to match their specific needs and risk profiles.
For instance, a financial institution might configure its IPS to have stricter controls on transactions and customer data access (due to regulatory requirements), while a manufacturing company might prioritize protecting its industrial control systems.
Seamless Integration with Existing Security Infrastructure
IPS doesn’t operate in isolation. Its true power comes from its ability to integrate with other security tools, creating a comprehensive defense ecosystem.
When combined with firewalls, SIEM systems, and endpoint protection, IPS becomes part of a holistic security strategy. This integration enhances threat intelligence sharing and coordinated responses across the entire network.
A Gartner report highlights that organizations with well-integrated security tools experience 30% fewer security incidents compared to those with siloed solutions.
Adaptive Defense Against Emerging Threats
IPS technology not only protects against known threats but also adapts to emerging risks. Machine learning algorithms enable modern IPS solutions to detect and respond to previously unknown threats (also known as zero-day attacks).
This adaptive capability makes IPS an essential component of a comprehensive cybersecurity strategy. As cyber threats continue to evolve, IPS technology evolves alongside them, providing organizations with a dynamic defense mechanism.
The next chapter will explore best practices for implementing IPS in your organization, ensuring you maximize the benefits of this powerful security tool.
How to Implement IPS Effectively
Assess Your Network Thoroughly
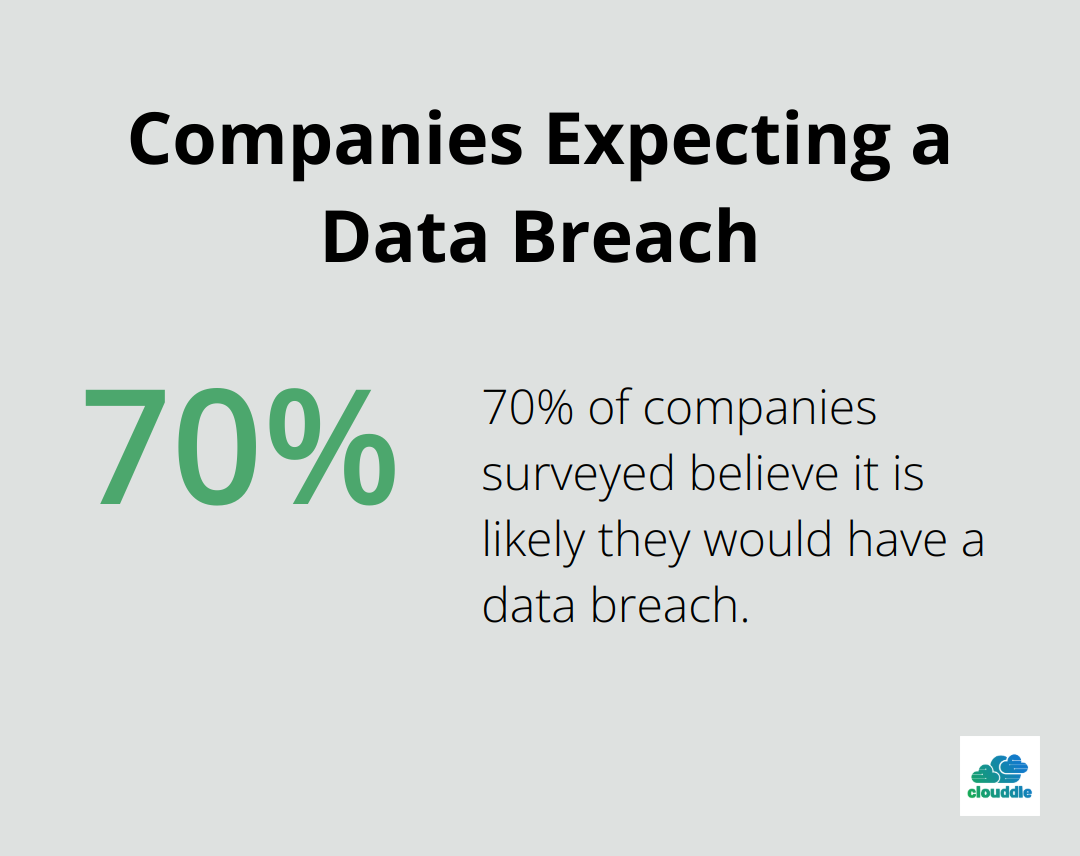
Before you select an IPS solution, conduct a comprehensive network assessment. This step identifies vulnerabilities and clarifies your specific security needs. A Ponemon Institute study found that 70 percent of companies surveyed believe it is likely their company would have a data breach.
Start by mapping your network topology, including all devices, applications, and data flows. Identify critical assets that require the highest level of protection. Use network scanning tools to detect potential vulnerabilities and misconfigurations. This assessment will guide your IPS selection and configuration process.
Choose the Right IPS Solution
Selecting the appropriate IPS solution is vital for effective network protection. Consider factors such as network size, industry-specific regulations, and integration capabilities with existing security tools.
For example, if you’re in the healthcare sector, prioritize IPS solutions with strong HIPAA compliance features. Financial institutions might focus on solutions with advanced fraud detection capabilities.
Look for IPS solutions that offer:
- High performance with low latency
- Customizable rule sets
- Regular threat intelligence updates
- Robust reporting and analytics features
According to Gartner, by 2027, more than 40% of AI-related data breaches will be caused by the improper use of generative AI (GenAI) across borders.
Fine-tune Your IPS Configuration
Proper configuration maximizes the effectiveness of your IPS. Start with a baseline configuration and gradually refine it based on your network’s specific requirements and traffic patterns.
Set up rules to block known malicious IP addresses and signatures. Configure the IPS to monitor for unusual patterns that might indicate zero-day attacks. Establish thresholds for triggering alerts and automated responses.
Be cautious of overly strict configurations that might lead to false positives and disrupt legitimate traffic. An ESG Research survey found that 45% of organizations struggle with high false positive rates in their security tools.
Regularly review and adjust your IPS configuration as your network evolves and new threats emerge. This ongoing process ensures your IPS remains effective against the latest security risks.
Maintain and Update Regularly
An IPS is not a set-it-and-forget-it solution. Regular maintenance and updates are essential for optimal performance and protection against emerging threats.
Keep your IPS software and signature databases up to date. Many vendors release updates weekly (or even daily). A Verizon report states that 99.9% of exploited vulnerabilities were compromised more than a year after the associated CVE was published, highlighting the importance of timely updates.
Perform regular performance checks to ensure your IPS operates efficiently. Monitor system logs for any signs of issues or unusual behavior. Try using automated update tools to streamline this process and reduce the risk of human error.
Invest in Staff Training
Even the most advanced IPS is only as effective as the team managing it. Invest in comprehensive training for your IT staff on IPS management and incident response.
Ensure your team understands how to interpret IPS alerts, investigate potential threats, and fine-tune the system. Regular tabletop exercises and simulated attacks can help staff practice their response to various security scenarios.
A CompTIA study found that organizations with well-trained IT security staff experience 60% fewer security breaches. Consider partnering with managed security service providers to augment your team’s capabilities and provide round-the-clock monitoring.
Final Thoughts
Intrusion Prevention Systems (IPS) revolutionize network security with real-time threat detection and automated incident response. These systems actively block malicious traffic before damage occurs, reducing the risk of successful cyberattacks. Modern IPS solutions adapt to emerging risks through machine learning capabilities, providing a dynamic defense mechanism against evolving threats.
Effective implementation of Network Security IPS requires careful planning, regular maintenance, and staff training. Organizations must select the right solution, fine-tune configurations, and keep systems updated to maximize their IPS investment. This proactive approach significantly enhances overall security posture in today’s fast-paced digital landscape.
We at Clouddle understand the critical role of robust network security in modern business environments. Our managed IT and security services help organizations implement and maintain effective security measures (including IPS solutions). Contact us today to learn how we can strengthen your network defenses and protect your valuable assets in an increasingly connected world.


